DoS attack on the MikroTik line of equipment and virtual RouterOS
In MikroTik, they did not have time to patch the vulnerability voiced in the article from the CIA hack tools, as the possibility of performing Denial Of Service on remote equipment running on RouterOS was discovered (all versions of OS are pre-attack).
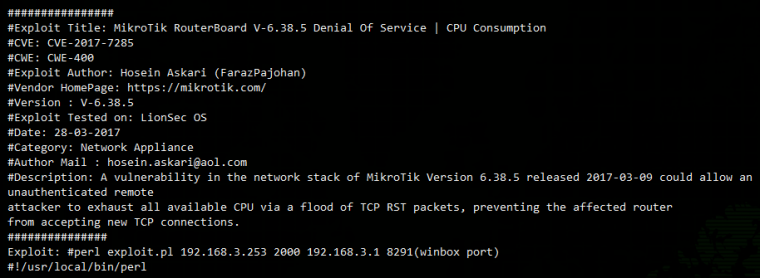
The vulnerability allows you to load the RouterOS CPU 100% by sending a heap of TCP RST packets to port 8291 which is used by default by Winbox. By default, access to this port is closed by the firewall, but if you opened it to control your tics via the Internet, you should at least change the default port, and at best, register permission to access the winbox only for certain ip (although not the fact that it will save):
According to the discussion on the off. Site vulnerabilities are subject to both hardware devices (tested on: RB751, hEX lite, RB951, RB2011, CCR1036 and even RB3011) and virtual CHR (tested for 8x Xeon).
An example of a working exploit is in the public domain .
')
The official representative of MikroTik advises to disable all services in the Ip service menu (be careful), change the standard ports, use a router, restrict access to these services only from the internal network via vpn on a third-party device, or buy a more productive router. And in general it is from his words “normal situation” that the CPU performance is not enough to handle such a number of packets ...
The vulnerability allows you to load the RouterOS CPU 100% by sending a heap of TCP RST packets to port 8291 which is used by default by Winbox. By default, access to this port is closed by the firewall, but if you opened it to control your tics via the Internet, you should at least change the default port, and at best, register permission to access the winbox only for certain ip (although not the fact that it will save):
ip firewall filter add chain=input action=accept protocol=tcp src-address=ADMIN_IP dst-port=8291 comment=Allow_Winbox According to the discussion on the off. Site vulnerabilities are subject to both hardware devices (tested on: RB751, hEX lite, RB951, RB2011, CCR1036 and even RB3011) and virtual CHR (tested for 8x Xeon).
An example of a working exploit is in the public domain .
')

The official representative of MikroTik advises to disable all services in the Ip service menu (be careful), change the standard ports, use a router, restrict access to these services only from the internal network via vpn on a third-party device, or buy a more productive router. And in general it is from his words “normal situation” that the CPU performance is not enough to handle such a number of packets ...
Source: https://habr.com/ru/post/357318/
All Articles