The Shadow Brokers Group has published new NSA exploits
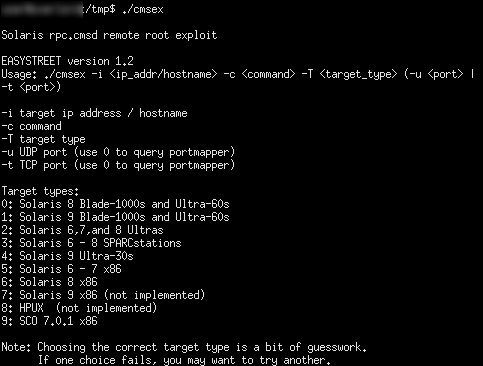
EASYSTREET (rpc.cmsd): remote root for Solaris, one of the published exploits
In August 2016, a group of hackers The Shadow Brokers laid out the first batch of exploits, which belong to the Equation Group - a well-known hacker group, which with a high probability had a hand in the creation of known types of cyber weapons, including, Stuxnet, Flame, Duqu, Regin, EquationLaser, etc. To all signs , this highly qualified group is associated with the NSA (hackers from the GReAT subdivision at Kaspersky Lab are studying in detail their activities).
The second part of the exploit kit stolen from the Equation Group was set up for auction by hackers. But over the past time, they have not been able to collect a considerable amount of money on their Bitcoin wallet. Therefore now decided to publish all other ekslpoyty in open access (links under a cat).
In a published statement , The Shadow Brokers group members expressed extreme dissatisfaction with the policies of Donald Trump, whom they voted for and supported. According to hackers, he does not meet the expectations of his electorate. The Shadow Brokers group responded to those who link their activities with Russia. They said that it is not. But at the same time, they believe that Americans have more in common with the Russians than with the Chinese, globalists and socialists. Therefore, the principle here is that the enemy of your enemy is your friend.
')
In their statement, the hackers also published a password for the encrypted file eqgrp-auction-file.tar.xz.gpg , which was put up for auction in August 2016. This is the
CrDj"(;Va.*NdlnzB9M?@K2)#>deB7mN password CrDj"(;Va.*NdlnzB9M?@K2)#>deB7mN .Security expert x0rz thinks that an exploit can be of some interest for breaking into a certain target in the .gov.ru domain (stoicsurgeon_ctrl__v__1.5.13.5_x86-freebsd-5.3-sassyninja-mail.aprf.gov.ru, although we could not find it among files, and the link to it in the repository also does not work ) and the default password list from /Linux/etc/.oprc.
Of course, this is not all interesting, which can be found in the archive, which is now open to all. There are tools for remote code execution for Solaris, NetScape Server, FTP servers (RHEL 7.3 + / Linux, CVE-2011-4130, and probably CVE-2001-0550). Among other exploits include:
- ESMARKCONANT for phpBB (<2.0.11),
- EL scoop for SquirrelMail 1.4.0-1.4.7,
- ELITEHAMMER for RedFlag Webmail 4,
- ENVISIONCOLLISION for phpBB,
- EPICHERO for Avaya Media Server,
- EARLYSHOVEL for RHL7 using sendmail,
- ECHOWRECKER / sambal for samba 2.2 and 3.0.2a-3.0.12-5 (with DWARF symbols), for FreeBSD, OpenBSD 3.1, OpenBSD 3.2 and Linux. Probably using vulnerability CVE-2003-0201. There is a version for Solaris.
- ELECTRICSLIDE (heap overflow) in Squid, probably for Chinese purposes,
- EMBERSNOUT for httpd-2.0.40-21 in Red Hat 9.0,
- ENGAGENAUGHTY / apache-ssl-linux for Apache2 mod-ssl (2008), SSLv2,
- ENTERSEED for Postfix 2.0.8-2.1.5,
- ERRGENTLE / xp-exim-3-remote-linux , root for Exim, probably using CVE-2001-0690, Exim 3.22-3.35,
- EXPOSITTRAG for pcnfsd 2.x,
- KWIKEMART (km binary) for SSH1 padding crc32, (https://packetstormsecurity.com/files/24347/ssh1.crc32.txt.html),
- slugger : remote code execution in various printers, probably using the CVE-1999-0078 vulnerability,
- statdx for Redhat Linux 6.0 / 6.1 / 6.2 rpc.statd,
- telex : an exploit for Telnetd, probably in RHEL, possibly through vulnerability CVE-1999-0192,
- toffeehammer for cgimail’s cgiecho module, fprintf exploit,
- VS-VIOLET for Solaris 2.6 - 2.9, something related to XDMCP,
- SKIMCOUNTRY to copy mobile phone logs,
- EMPTYBOWL RCE for MailCenter Gateway (mcgate) - an application that comes bundled with the Asia Info Message Center mail server.
Plus backdoors and shells for HP-UX, Linux, SunOS, FreeBSD, JunOS, an implant for AIX 5.1-5.2, tools for elevating privileges, including evolvingstrategy, probably for Kaspersky Anti-Virus (/ sbin / keepup2date).
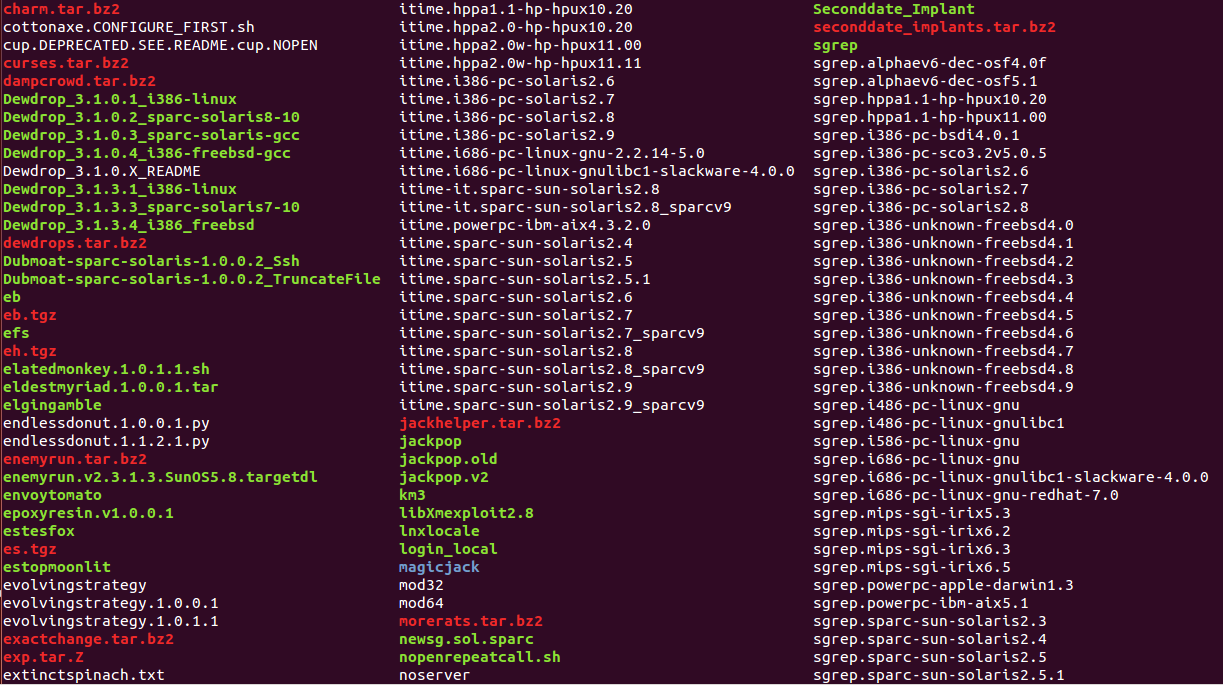
Experts are still exploring exposites, but it seems that many of them are designed for outdated systems. Edward Snowden expressed the opinion that the volume of published data is already enough for the NSA to determine the source of the leak.
Links to the archive with encrypted files (published on August 13, 2016):
magnet:? xt = urn: btih: 40a5f1514514fb67943f137f7fde0a7b5e991f76 & tr = http: //diftracker.i2p/announce.php
https://mega.nz/#!zEAU1AQL!oWJ63n-D6lCuCQ4AY0Cv_405hX8kn7MEsa1iLH5UjKU
https://app.box.com/s/amgkpu1d9ttijyeyw2m4lso3egb4sola
https://www.dropbox.com/s/g8kvfl4xtj2vr24/EQGRP-Auction-Files.zip
https://ln.sync.com/dl/5bd1916d0#eet5ufvg-tjijei4j-vtadjk6b-imyg2qkd
https://yadi.sk/d/QY6smCgTtoNz6
Password to decrypt eqgrp-free-file.tar.xz.gpg (published on August 13, 2016):
theequationgroupPassword to decrypt eqgrp-auction-file.tar.xz.gpg (published on April 8, 2017):
CrDj"(;Va.*NdlnzB9M?@K2)#>deB7mNTo decrypt the archive on Windows, you need the gpg2 tool from the Gpg4win package.
Mirror (with decrypted files)
dfiles.ru/files/8ojjgfdze
The contents of the archive eqgrp-auction-file.tar.xz.gpg on Github (published April 8, 2017):
github.com/x0rz/EQGRP
(The owner of the x0rz repository says that some binaries may be missing because the antivirus has deleted them)
Source: https://habr.com/ru/post/357312/
All Articles