WikiLeaks uncovered the method used by the CIA to conceal the country of origin of spyware malware
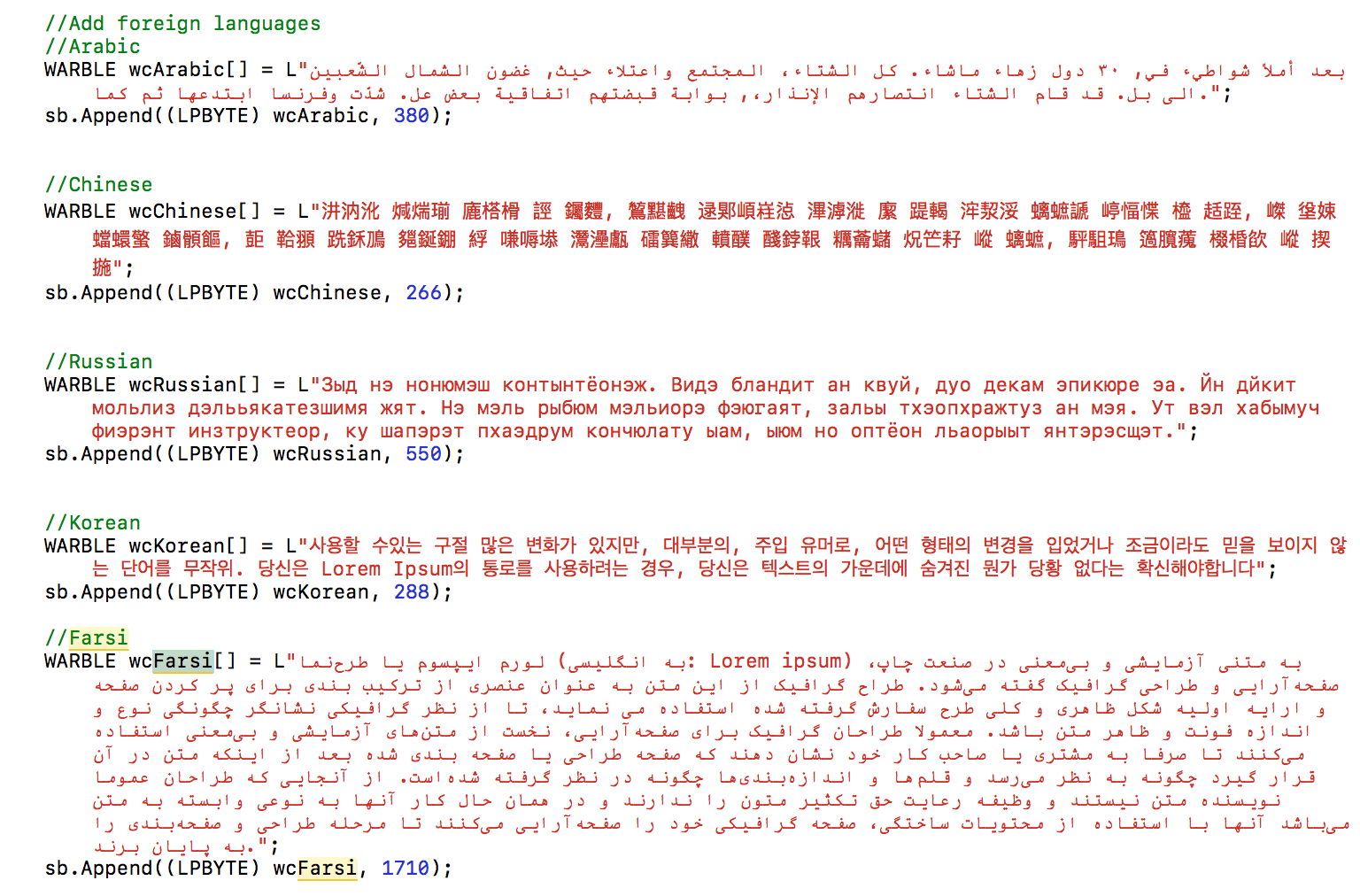
Pay attention to the place with the supposedly "Russian" text.
Up until now, only technical documentation has been published on WikiLeaks describing the capabilities of the software tools of the Central Intelligence Agency of the United States. Vault 7 documents are of great interest to information security specialists, telecommunications companies and, of course, hackers. Now the editors of the resource have decided to start publishing the source code of some programs, which makes it possible to get a more detailed idea of the software possibilities from the CIA.
This is the release of the “Marble Framework” toolkit, designed to obfuscate code. This package of tools was used by the CIA officers to complicate the process of reverse engineering of various programs used by the intelligence agency to obtain various kinds of confidential information. Marble is a C ++ application that obfusts the code and comments on it in various ways. WikiLeaks believes that Marble software was used by the CIA back in 2016.
According to representatives of the University of California at Berkeley, this information is one of the most “malicious” on the part of Wikileaks, because it jeopardizes the successful conduct of operations conducted by the CIA.
')
As for obfuscation methods, the introduction of snippets in various languages of the world is used here, including Farsi, Chinese, and “Russian” (as illustrated in the announcement). The set of characters is continuous gibberish, there is no sense in these texts (as for the supposed “Russian” language, there is no sense here, not only in the texts, but also the words themselves. It is Cyrillic, yes, but hardly anyone would think that it is Russian tongue). According to experts, what was used is akin to “Lorem ipsum”, the types of text that is used to fill out website templates and documents. These snippets, according to the developers, should have misled specialists who would have attempted to reverse-engineer software from the CIA toolkit.
Snippets, in particular, had to convince those who would disassemble a randomly discovered CIA software tool that non-Americans, but representatives of other countries took part in the development of the software. According to experts, this software itself is written by highly qualified specialists and is perfectly documented.
Experts say that by itself, publishing information about the methods used by the CIA to obfuscate its software is not dangerous. In general, everything that intelligence programmers use is known to other specialists. But now, using text snippets, you can now search, which allows you to identify malicious software from American intelligence officers. The texts disclosed by WikiLeaks, along with other “digital fingerprints”, allow identifying spyware, which, of course, will complicate further work of the CIA in cyber-defense.
Almost immediately after the announcement of WikiLeaks information on the Web, user comments appeared that managed to find traces of the CIA's presence. “Saying 'hacked me' is one thing. But “the CIA hacked me,” is quite another, ” said Jake Williams, the founder of information security company Rendition InfoSec, about his case. “I believe that all this may affect the country's foreign policy in the future.” He believes that if this obfuscation software was used by the CIA during most operations, then the work of the CIA could be destroyed.

The CIA has already responded to the actions of WikiLeaks. “Dictators and terrorists have no friend closer than Julian Assange, because it is he who protects their privacy,” said Dean Boyd, the CIA spokesman. “The American public should be deeply concerned about any disclosures by Wikileaks of information that interferes with the ability of intelligence officers to protect America from terrorists and other threats. All this not only puts at risk employees from the United States and various operations, but also puts into the hands of our enemies weapons and information that can harm us. ”
Anyway, but in the Vault 7 information package provided by Wikileaks (information about Marble is already the third piece of data on the CIA tools), there is no too obvious “cover breaking”. Yes, a lot of information is interesting, but most of the disclosed software vulnerabilities are already outdated - software developers that are mentioned in Wikileaks leaks, including Google, Microsoft, Firefox, have already fixed the vulnerabilities, and in most cases before the leak.
Now representatives of the FBI are investigating the situation, trying to understand how the files that got to WikiLeaks leaked from the CIA.
Source: https://habr.com/ru/post/357310/
All Articles