Let's Encrypt issued 14,766 certificates for phishing PayPal
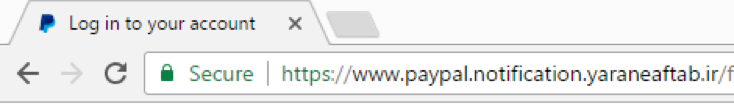
Free Let's Encrypt certificates have become so popular that this certification center from Mozilla and EFF has already become one of the largest certification authorities on the Internet. Unfortunately, the opportunity to get a free SSL certificate is used not only by regular sites, but also sites for phishing. For them, the presence of a green HTTPS badge is an important feature so that the difference with this site is not striking. Browsers mark such fakes as “secure sites”.
Security experts have previously noticed that Let's Encrypt issues too many certificates with the word “PayPal” in the domain name. SSL Store Expert Vincent Lynch (Vincent Lynch) even called on the certification authority to stop issuing such certificates , because they are more likely to be used for phishing. Evidence has now been gathered that phishing using Let's Encrypt certificates is a much more common occurrence than might have been supposed.
Vincent Lynch collected data using the search engine crt.sh (launched by Comodo) and the logs of the Certificate Transparency system, to which Let's Encrypt send information about all the issued certificates - all certificate authorities will soon do so. By default, the crt.sh search engine does not allow to process such an extensive request, so the researchers turned directly to the crt.sh developer Rob Stradling, who made the request directly to the database.
')
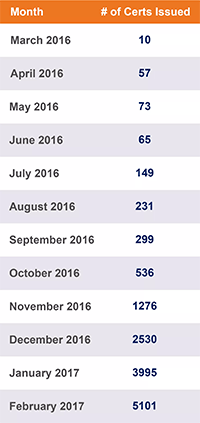 The specialist calculated that between January 1, 2016 and March 6, 2017, Let's Encrypt issued certificates for 15,720 domains with the word “PayPal” in the title, and the number of such certificates grows exponentially, increasing each month by 1.5-2 times.
The specialist calculated that between January 1, 2016 and March 6, 2017, Let's Encrypt issued certificates for 15,720 domains with the word “PayPal” in the title, and the number of such certificates grows exponentially, increasing each month by 1.5-2 times.As you can see, phishers took some time to master Let's Encrypt as the main certification authority - but then the process started. Let's Encrypt has become a regular working tool for scammers. Since December 2016, it has been issuing about 100 PayPal certificates each day, and in February 2017, more than 180 certificates per day.
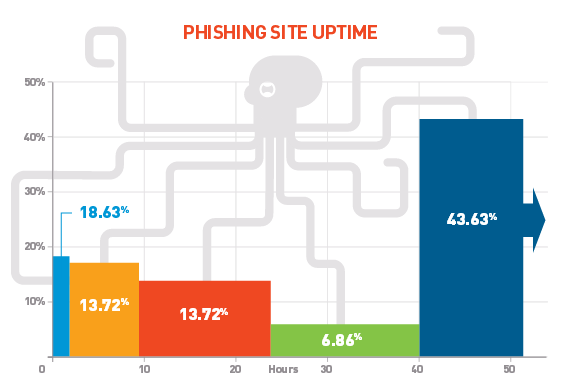
A conservative study of a random sample of thousands of sites showed that 96.7% of the issued certificates belong to domains that run phishing sites. This corresponds to 14,766 phishing domains from the entire sample of 15,720 certificates. Most phishing sites quickly fall into Safe Browsing service filters and soon go offline. As soon as a phishing site is marked as “dangerous” in the browser, it becomes useless. Therefore, fraudsters use such a large number of domains, constantly changing each other. According to a CYREN study , before marking in Safe Browsing or going offline, the average lifetime of a site is only about two days.
For March 2017 there are still incomplete data, but this month may be the first when the number of certificates issued for “PayPal” domains decreases.
The authors of the study say that they studied the situation only with the “PayPal” domains, because this is the most popular target for phishing, but the same situation is with the domains of various banks, Bank of America, Apple ID and Google. For example, here is a 1963 certificate with “applid” in the domain name.
The use of SSL certificates by fraudsters was one of the main concerns regarding the launch of a free certification authority at the end of 2015. In the old days with paid certificates, attackers could hardly afford the purchase of thousands of certificates, especially the issuance of each of them was accompanied by a certain bureaucratic procedure. Now certificates have become free, and their receipt and renewal can be automated.
According to experts, according to the current trend of Let's Encrypt, by the end of the year, another 20,000 certificates will be issued to PayPal phishing sites, so that the total number of issued certificates will reach 35,000.
The creators of Let's Encrypt believe that following cybercrime and catching fraudsters is not their business. They do not do moderation sites. This project is one of several initiatives aimed at “total encryption” of the Internet. The goal is to encrypt absolutely everything, and this implies encryption, including “bad” sites, which also switch to HTTPS.
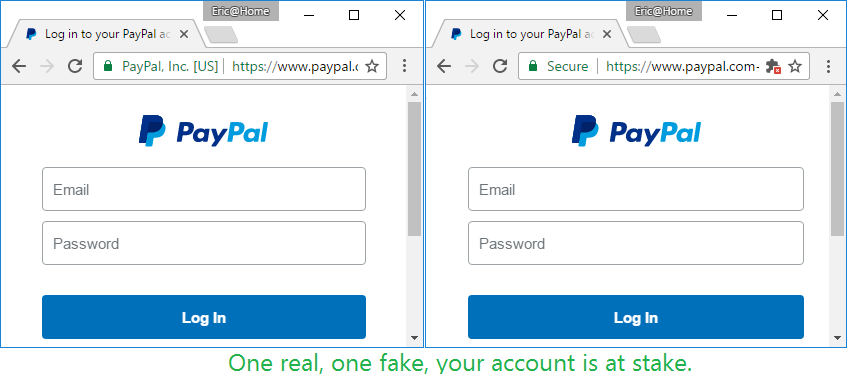
Over the years, security experts have taught users that a green HTTPS secure connection icon means security. The situation is worsened by the fact that even some browsers like Chrome, when connected via HTTPS to a phishing site, display a green dash with the words “Safe”.
Now we need to conduct additional explanatory work and explain that a “secure connection” can be with a malicious site, too. This is perfectly understandable to every specialist, but among users there is not always such an understanding, which is what fraudsters use. Part of the blame lies with the developers of UI browsers.
The security community used to ask whether malicious websites and software really use HTTPS. Now the answer is that in the phishing industry this is true.
Source: https://habr.com/ru/post/357308/
All Articles