Study: sound attack on accelerometers replaces readings

A study by a group of scientists from the University of Michigan and the University of South Carolina calls into question the long-held belief that software can automatically trust hardware sensors that provide autonomous systems with the information they need to make decisions.
According to the results of scientific work, sound waves can be used to crack important sensors in a wide range of technological devices, including smartphones, cars, medical equipment and the Internet of things.
')
This study studied inertial sensors - capacitive MEMS accelerometers, which measure the change in the velocity of an object in three dimensions. A team of researchers used finely tuned acoustic signals to trick down 20 different accelerometers that capture motion. This approach made it possible to detect a backdoor with which it was possible to control other elements of the system.
The fundamentals of hardware physics allowed scientists to trick sensors and force them to pass false information into a microprocessor. Capacitive MEMS accelerometers for measuring acceleration register the deviation of the inertial mass. Under the influence of force, the inertial mass changes, causing a change in capacitance, which is converted into an analog signal.
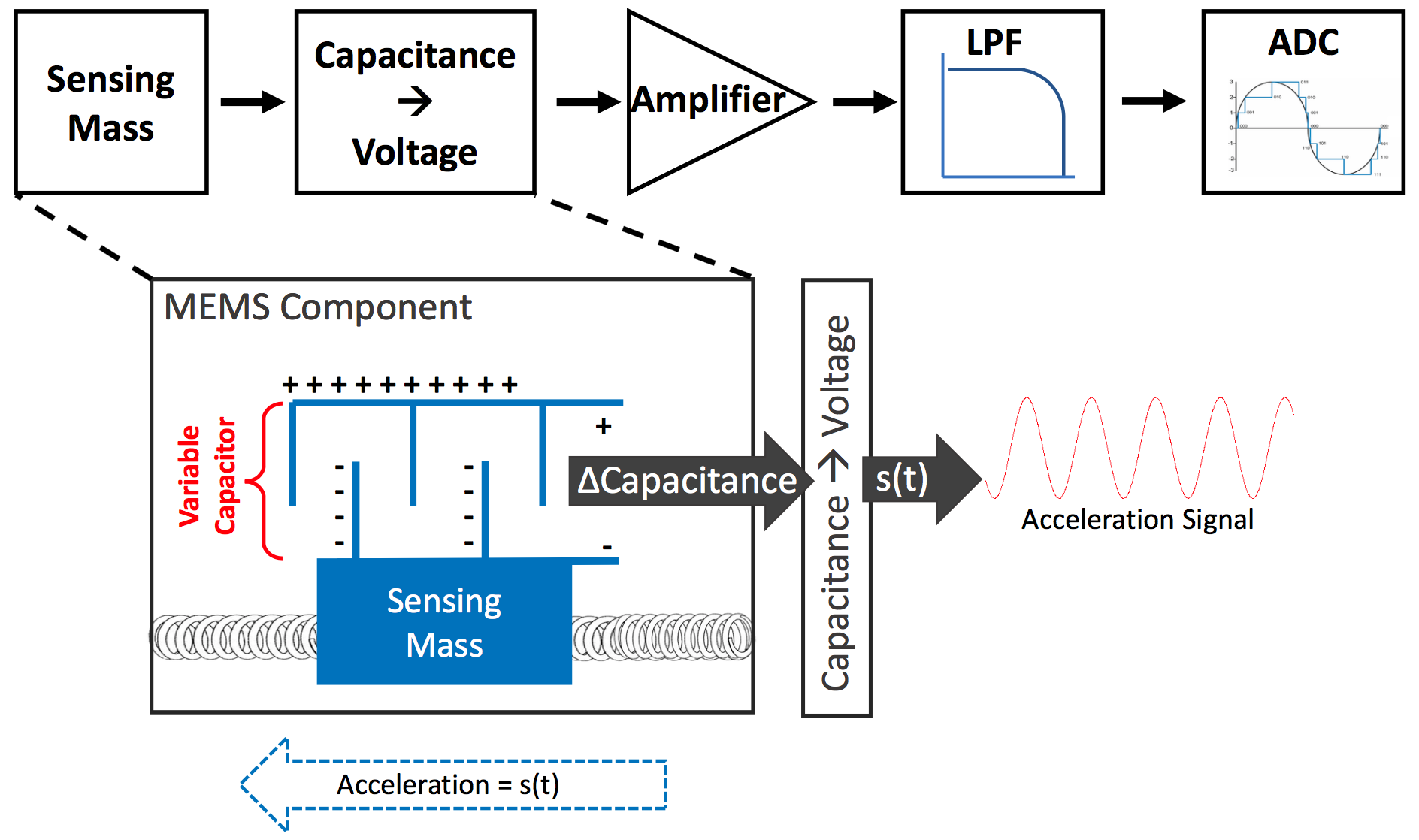
The effect of sound pressure on a sensitive spring-mass system can displace it, thereby creating false acceleration signals. These fake acceleration signals correlate with the acoustic noise signal.
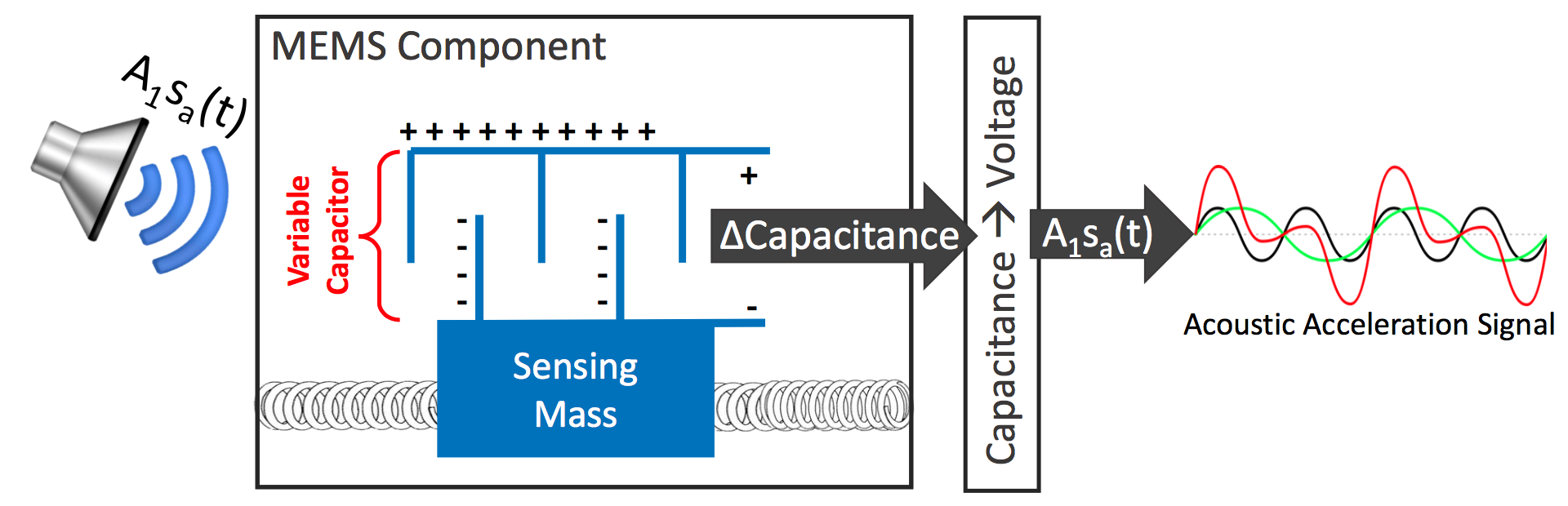
It is important to note that the resonant frequency of the spring-mass system is a characteristic of how it was designed on the physical level, and for successful deception the frequency of acoustic noise must correspond to it.
The researchers conducted several demonstration demonstrations: an audio signal from a simple $ 5 speaker caused the Fitbit bracelet to show thousands of fake steps. In another case, a malicious music file was turned on on the smartphone, and the speaker controlled the accelerometer of another smartphone, on which the Android application “twisted the steering wheel” of a toy car. Another music track disabled the accelerometer of the Samsung Galaxy S5, which instead of the graph of readings displayed the word WALNUT (walnut).
The research team also notes that it is possible to disrupt the accelerometer's behavior even in combination with video and music, which are automatically reproduced from websites, email attachments, receiving notifications and so on.
MEMS accelerometers are already installed in thousands of devices and home appliances. Autonomous systems, such as unmanned aerial vehicles and autopilot cars, make decisions based on what their sensors suggest. If autonomous systems cannot trust their sensor senses, their safety and reliability is at risk. When a system or device uses a vulnerable MEMS sensor to make decisions, attackers can use them as an attack vector.
To achieve this effect, the researchers determined the resonant frequencies of 20 different accelerometers from five manufacturers. In their experiments, they did not use noise below 110 dB, but note that lower amplitudes may also adversely affect various sensors.
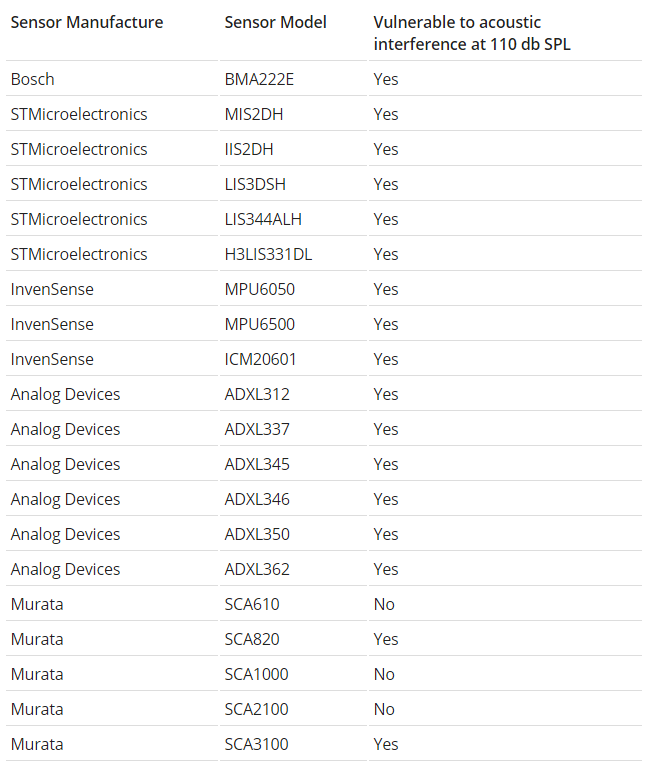
Other MEMS sensors, including gyros, are also potentially susceptible to sound attack. In the course of their experiments, scientists discovered additional vulnerabilities. For example, the development of digital low-pass filters that filter out the highest frequencies, as well as amplifiers, did not take into account safety concerns.
To protect sensors from sound attack, you must use a combination of different methods, however, there are two main approaches:
- Position MEMS sensors in such a way as to limit the effects of sound interference. For example, surround it with soundproof material.
- Deploy data processing algorithms that reject abnormally accelerated signals, especially with frequencies close to the resonant frequency of the MEMS sensor.
In addition, researchers have developed several software solutions that could minimize vulnerabilities, and reported this to manufacturers.
The research team leader and lead author Kevin Fu (Kevin Fu) has previously researched the cybersecurity risks of medical technology, including the potential threat of transmitting fatal heart rhythms to a pacemaker over a wireless network.
According to him, to conduct a study aimed at studying the effect of acoustic signals on equipment, they were inspired by the case when quadrocopters were disabled with the help of music. He added that the earlier work of scientists demonstrated the success of DoS-attacks, in which sound is used to turn off accelerometers.
This is not the only study where the safety of using accelerometers is questioned. In 2014, security researchers at Stanford University demonstrated how the sensor can be secretly used as a primitive microphone. Even earlier, in 2011, a group from the Massachusetts Institute of Technology and the Georgia Institute of Technology showed how using an accelerometer in a smartphone, you can decipher approximately 80% of all words typed on a computer keyboard.
Source: https://habr.com/ru/post/357296/
All Articles