CIA hacker tools collection published
On March 7, 2017, the Wikileaks website began publishing the Vault collection of 7 secret documents from the Central Intelligence Agency. The first part of the Year Zero collection contains 8761 files, including a list of various malware, viruses, Trojans, dozens of 0day exploits and payloads for them, remote control systems (now instead of file folders there are pdf with a list of files, after checking the files themselves appear ) and related documentation. All in all parts of the collection - hundreds of millions of lines of code. According to Wikileaks activists, after such a leak, the CIA loses control over most of its hacker arsenal.
Files obtained from a network with a high degree of protection at the CIA Cyber Intelligence Center , located in Langley, pc. Virginia.
The hacking division of the Center for Cyber Intelligence of the CIA employs more than 5,000 people (judging by the number of registered users in the system). They even say that the CIA's hacking resources outnumber their “competitors” from the NSA. Possessing powerful intellectual resources, this division has developed a wide arsenal of computer programs for computer surveillance and espionage.
')
The EDG (Engineering Development Group) department, which is part of the Directorate for Digital Innovation (DDI), was directly involved in the development, testing, and maintenance of the software; see the CIA organizational chart .
In terms of the volume of published documents, the first part of Vault 7 (Year Zero) already exceeds the volume of all NSA documents received from Edward Snowden and published over three years.
Who hacked into the CIA network is unknown. Perhaps it was not a hack, but an insider job or a “gift” of one of the former employees. “The archive seems to have circulated among hackers who worked in the past for the US government and contractors in an unauthorized manner, one of whom provided Wikileaks with parts of the archive,” said Wikileaks in a press release . However, it should be noted that in recent months a number of representatives of the intelligence community have been arrested in the United States. Their names are mostly unknown., Except for a certain Harold Martin III (Harold T. Martin III), who on February 8, 2017 was charged with federal charges for 20 cases of “misuse” of secret information. About 50 terabytes of information he received from the secret programs of the NSA and the CIA, including the source code of numerous hacking tools, were taken from his computers.
The CIA's unique exploits target a range of popular products, including iOS, Android, and Windows; there is even one for Samsung TVs (with built-in microphones). The latest exploit was created by the development department for embedded systems Embedded Development Branch (EDB). Documents and department files are on this page . An exploit for Samsung TVs called Weeping Angel was developed jointly with British intelligence MI5 / BTSS. The program adds the TV mode 'Fake-Off', when the TV looks off, but at the same time records conversations in the room and sends them via the Internet to the CIA server.
Separate documents indicate an attempt by the CIA to develop programs for installation in car control systems. Probably, including for the inconspicuous killing of people, so that everything looks like an accident.
The exploits for smartphones were developed by the Mobile Devices Branch (MDB) mobile device department. At the end of 2016, the division released 24 Android exploits with various 0day vulnerabilities, some of which were acquired from colleagues from the NSA, GCHQ and third-party contractors. Designed tools allowed whatsApp, Signal, Telegram, Wiebo, Confide and Cloackman messages to intercept before the application encrypts them.
Many of the Windows exploits have been developed by the Automated Implant Branch (AIB) department. Among the many malicious programs for this OS are operating programs with 0day-vulnerabilities with local or remote installation, viruses for transferring information from computers disconnected from the network (air gap) like Hummer Drill (integrated into the Nero program for recording CD / DVD and transferred from computer to computer together with disks), USB flash drives infector , code for hiding information inside image files (steganography) and into hidden disk areas ( Brutal Kangaroo ).
Network Devices Branch Network Devices Branch (NDB) attacks against Internet infrastructure and web servers.
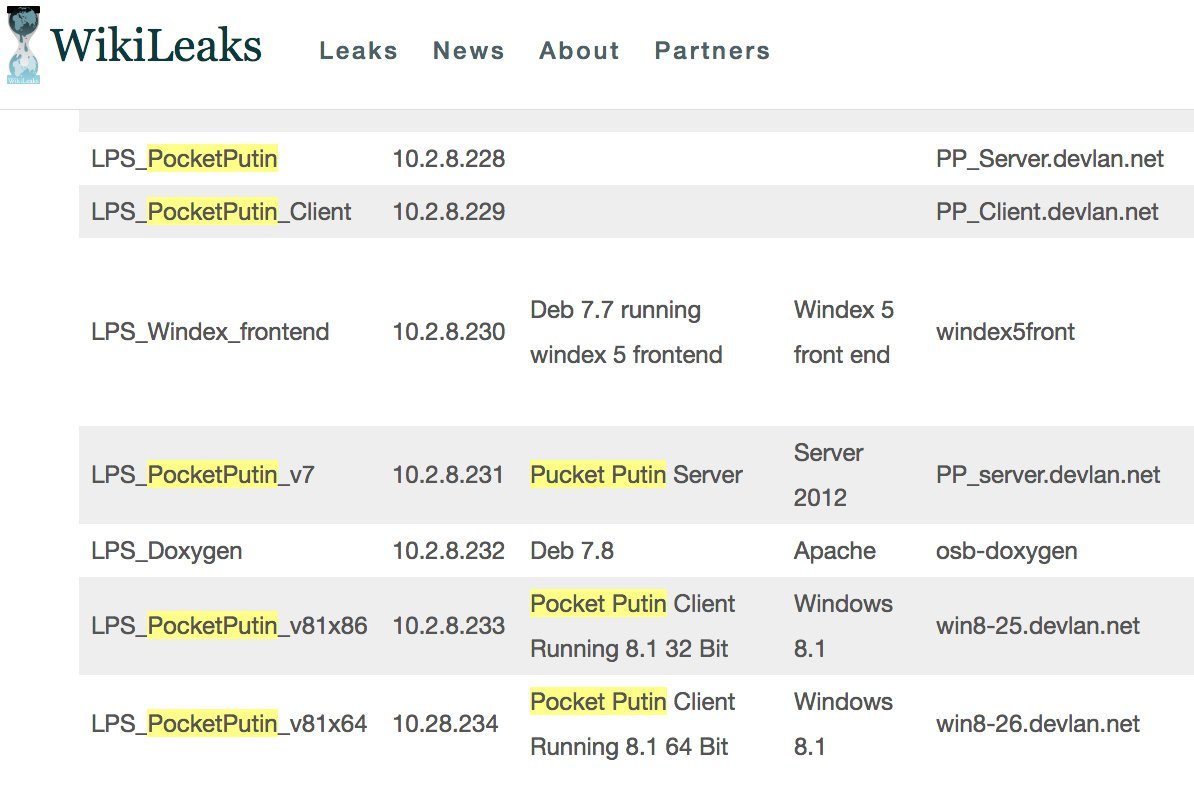
Published user guide and developer guide for HIVE cross-platform malware, which includes specialized bookmarks for Windows, OS X, Solaris, MikroTik (used in routers) and Linux, and also describes the service infrastructure Listening Post (LP) / Command and Control ( C2) to communicate with these bookmarks. For each of them, a separate domain is allocated, which is resolved to the public commercial provider VPS. An open server receives traffic from HTTPS from the bookmark and redirects it via VPN to a specialized server (Blot), which verifies the client certificate and redirects the connection to the Honeycomb server — it communicates with the bookmark. If the certificate is invalid, then the traffic is sent to a secret server that loads a harmless site.
CIA programmers not only developed their own exploits, but also tried to borrow the most valuable tools used by government hackers from other countries. Borrowed components are listed on this page : there are keyloggers, password collectors, modules for capturing images and sound from a webcam, destroying information on a disk, elevating privileges, bypassing antiviruses, etc.
Among the documents of the CIA, there are those that are not directly related to hacking and intelligence. For example, tips and tricks for working with Git . Pretty funny reading.
The CIA archive convincingly proves that this particular intelligence agency is violating the requirement of former President Obama to government agencies to disclose the 0day-vulnerability that they have become aware of. To this end, a special procedure was approved by the Vulnerability Equities Process (VEP) and a commission led by the National Security Council (NSC) with representatives of other agencies. It is possible that the guide for programmers to conceal traces is designed not only to disguise from external enemies, but also from their own American officials who "interfere with normal work" and demand compliance with the Constitution.
Thanks to the leakage of the CIA’s extensive hacking arsenal, now anyone can now have the same capabilities that only American specialists used to have, including other states, computer criminals, and just teenagers. But it is temporary. Most importantly, software developers and device manufacturers were able to learn about exploited vulnerabilities — and close them. This will certainly increase the overall security of all users.
All Year Zero torrent files:
file.wikileaks.org/torrent/WikiLeaks-Year-Zero-2017-v1.7z.torrent
Archive password: SplinterItIntoAThousandPiecesAndScatterItIntoTheWinds
( mirror , archive without password)
Source: https://habr.com/ru/post/357288/
All Articles