Spammers have a database of 1.37 billion email addresses because of a backup error.
On March 4, 2017, security specialist Chris Vickery of MacKeeper announced in advance that by Monday there would be details of a massive leak of 1.37 billion records in the personal database. He kept his promise. MacKeeper published the details of this leak yesterday. It turned out that her victim was not some normal company, but the spam company River City Media (RCM).
Under the leadership of well-known spammers Alvin Slocombe and Matt Ferris, this company claims to be a respectable marketing firm, while at the same time it brags in documents that it sends out more than a billion letters a day . And this is with a dozen employees.
')
Needless to say, with such a base, anyone can do "effective marketing."
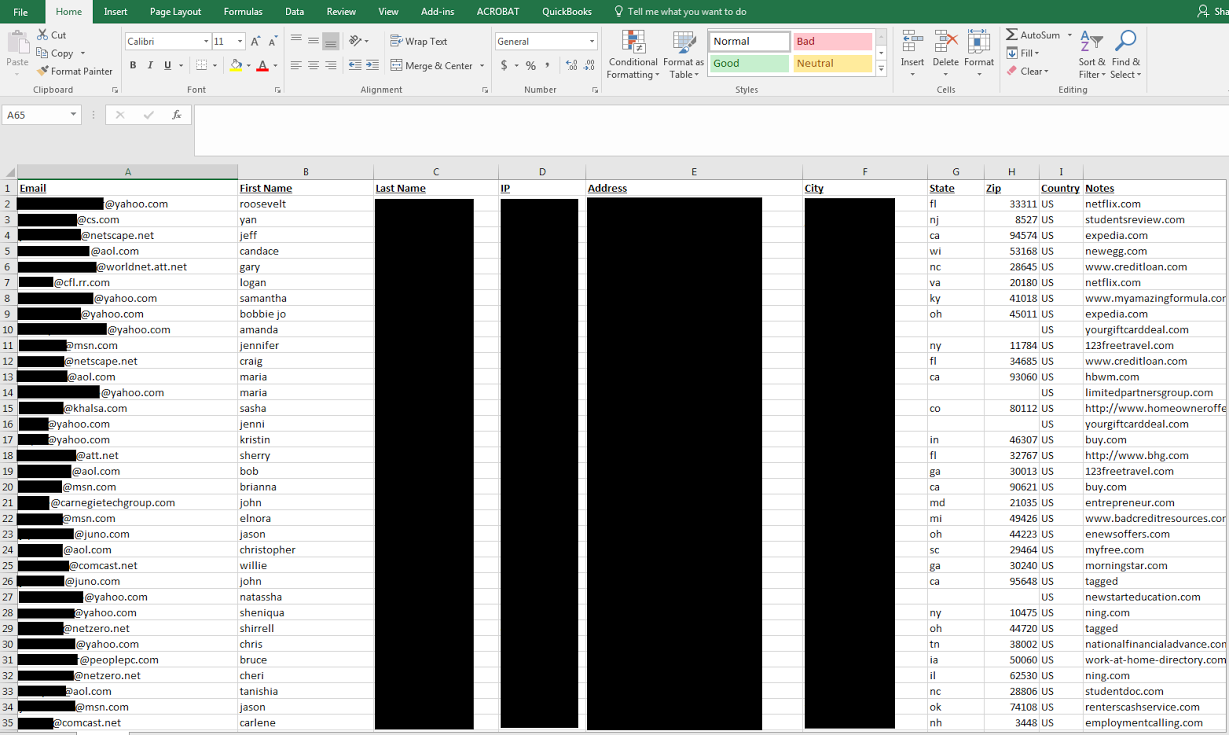
The database contains not only email addresses, but also real names, last names of users, IP addresses, and often physical addresses.
 In fact, such information can be useful not only to spammers, but also to other interested parties. Let's say it contains a huge amount of postal addresses in the .mil domain zone - with names and IP addresses. You understand what that means.
In fact, such information can be useful not only to spammers, but also to other interested parties. Let's say it contains a huge amount of postal addresses in the .mil domain zone - with names and IP addresses. You understand what that means.A sample base check showed that this is indeed real information.
The investigation against the spam giant RCM was conducted by experts from the MacKeeper Security Research Center, CSOOnline and Spamhaus. It all started with the fact that in January of this year, Chris Vickery came across in open access to a strange but suspicious set of files. As it turned out, the backup database belonged to River City Media. Files were not password protected. Chris Vickery has not yet told where exactly he “accidentally discovered” the files. Let's hope that the information security specialist has done nothing illegal.
The leak occurred due to misconfiguration of
rsync , a popular utility for backing up, synchronizing and mirroring data between servers.RCM backups have been in open access for more than a month. Some of the files are dated January 2017, and the other part - December 2016.
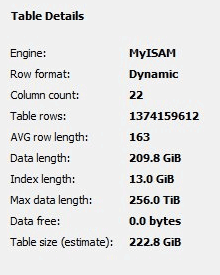
Among the files was a database of 222.8 GiB in size with email addresses. The total number of entries is 1,374,159,612.
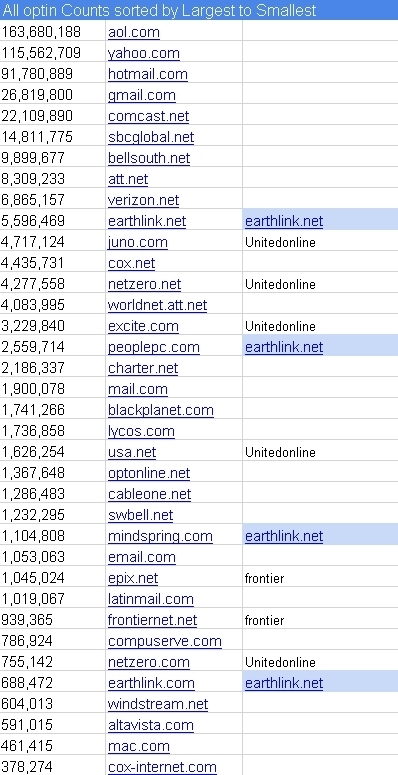
Judging by the statistics of postal services, spammers clearly focused on American users. Among the most popular there are no Russian postal domains. But, probably, almost all American users are present in the database.
The study of files showed that RCM is not just a spammer, but an agent who is very sophisticated in his business. For sending letters, they used automatic methods and some hacking techniques. For example, they checked mail servers for vulnerable configuration, and then used this information for mass mailings. This is evidenced by the presence of scripts and chat logs found in backups. Here is one snippet from these chats, where the technique is discussed, how to trick anti-spam filters of Gmail and fill up with letters to this mail server.

It explains that you need to raise the maximum number of connections with Gmail, but do not send anything, just keep the connections open for a long time. This is done by configuring your machine for maximum latency of response packets and in a fragmented manner, while opening up more and more connections. Well, and then, when Gmail is almost ready to break connections by timeout, bust sending letters to its fullest through all open connections, until Gmail chokes and disconnects them.
The technique of opening as many connections as possible between your machine and the victim's computer is, in fact, an attack like Slowloris , a kind of DoS. The trick here is that the spammer does not try to disable the victim’s computer, but tries to capture and use as much of its resources as possible. In this case, to give Gmail the maximum possible amount of spam mail.

The logs of the TierPoint provider that used RCM show problems with clogging AOL boxes
Details about different types of attacks with scripts are sent to Microsoft, Apple and other companies that were used by the spammer gang.
It is not known what methods River City Media used to collect this information. Surely in the near future, Alvin Slokombe and his accomplices will announce that they have not done anything illegal. Perhaps the base is collected through the so-called “co-registration”, when a person registers with some service, but does not notice a checkmark like “I allow sharing my information with third parties”. Owners of Internet services and programs collect databases of their users and can sell these databases to third parties.
Well, now RCM will find it much more difficult to use old methods. As of yesterday, Spamhaus has added the entire infrastructure of River City Media to its base.
Chris Vickery promises to publish a number of documents from the RCM backup in the near future, there are enough interesting spreadsheets, there are backups of hard drives, chat logs, etc. And the Salt Hash blog describes in detail some of the methods that RCM used for its dirty earnings on Internet advertising : fake search engine pages, sale of banner advertising on websites with its transfer to the body of the letter, etc. From all this nasty things, the company collected from October 2016 to January 2017 a considerable amount of $ 937,451.21 from various advertising networks, including AdDemand, W4, AD1 Media (Flex) and Union Square Media.
Source: https://habr.com/ru/post/357286/
All Articles