Hole in IE11 allows you to display popups even after the site is closed.
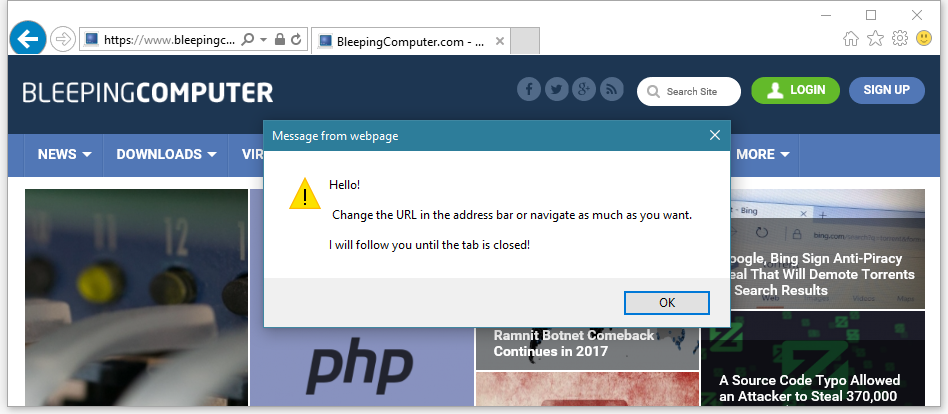
Vulnerability can be used to demonstrate "non-killed" popups.
Information Security Specialist Manuel Caballero from Argentina published the results of his vulnerability study in IE11 browser. The exploitation of this vulnerability allows the site owner with an embedded exploit to ensure that a site visitor starts to receive pop-up notifications. Their demonstration will continue even after the resource is closed. In addition, if desired, the site owner will be able to run his JavaScript code when a visitor to the malicious page has already left it and is visiting other resources.
Vulnerability, according to the specialist, is characteristic only for Internet Explorer 11, the Edge browser is devoid of this problem, as well as other developers' browsers. Now IE11 is the second most common browser, according to NetMarketShare statistics . Chrome 55 is now in first place with a market share of 37%, and IE11 is in second place with almost 11%. Thus, a vulnerability can be a threat to a large number of users.
The other day, Caballero demonstrated how a developer can make pop-ups appear in a user's browser, even if he left the site with a script added by the developer. And there is no limit in the number of popups. You can call them as follows.
')
for (var i = 0; i < 10; i++) { doc = new ActiveXObject("htmlFile"); win = doc.Script; // win is the window object of the ActiveXObject win.setTimeout("alert('Hello, world!')", i * 100); } The only way to get rid of this scourge is to close the tab, on which the site with the exploit was previously working and opening a new tab.
doc = new ActiveXObject("htmlFile"); win = doc.Script; // win is the window object of the ActiveXObject win.alert("Hello"); win.alert("2nd alert, no option to block me."); win.alert("3rd alert, and still no way out!"); 
A wide range of intruders can exploit this vulnerability for a variety of purposes. For example, it may be an ordinary advertisement. And maybe an attempt to deceive the user so that he downloaded malicious software onto his computer. Moreover, if popups appear while a user is working with authoritative resources like Google, Wikipedia, Bing, then suspicions about the emerging windows will be less than in any other case. It uses code with the window.open function.
doc = new ActiveXObject("htmlFile"); // Alert every 5 seconds doc.Script.setInterval("alert('Hello, world!')", 5000); // Save a self-reference doc.Script.doc = doc; // Use the open method. Nothing changes here, but now IE will not // destroy the previous reference and the script will continue running. window.open("","_self"); // "Does nothing", but this line is crucial. You can imagine how a user, working with Google search service, receives a message about the need to add a browser plugin to improve search performance.
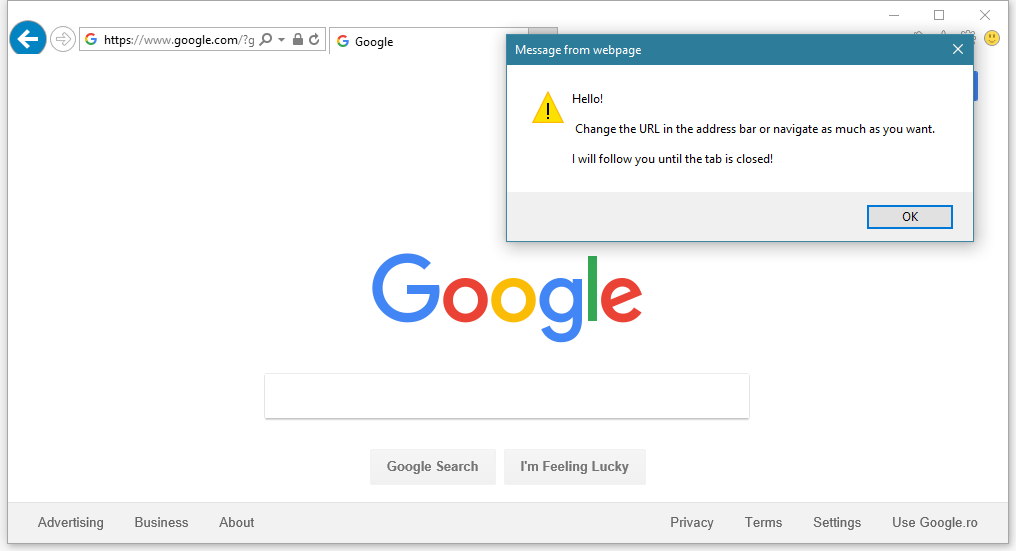
Or another example, when a user receives a notification about the need to install a new antivirus, and this notification appears on various sites, including the most authoritative ones. Until the tab is closed, in which the site with the embedded exploit originally appeared, the user cannot do anything with pop-up notifications. In a typical situation, IE11 allows you to block them in the browser, but if you wish, you can avoid this by closing the ignore button with another button with any text.
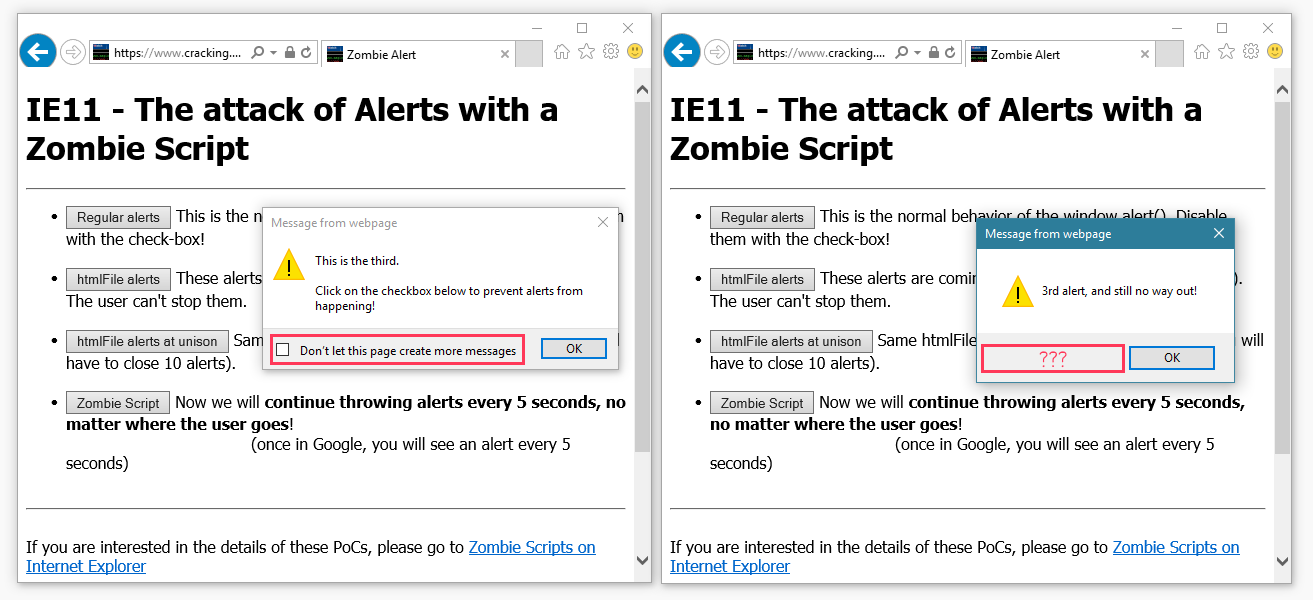
The popups themselves are a relatively minor issue . The fact is that instead of a pop-up notification code, you can add anything.
“For example, a new zero-day vulnerability has been discovered, and an attacker needs to download 5 MB using the victim’s browser. How can he be sure that there is enough time for this operation? And with the use of such a script, the attacker will have time for anything, ”says the Argentinian.
You can show fake ads, when you click on which the user will receive malicious software. You can download other exploits to the victim's browser, which, when combined with the detected Caballero vulnerability, will be even more effective. The vulnerability itself is based on the Universal Cross-Site Scripting (UXSS) bug, allowing an attacker to bypass the Same Origin Policy (SOP) through the htmlFile / ActiveXObject component.
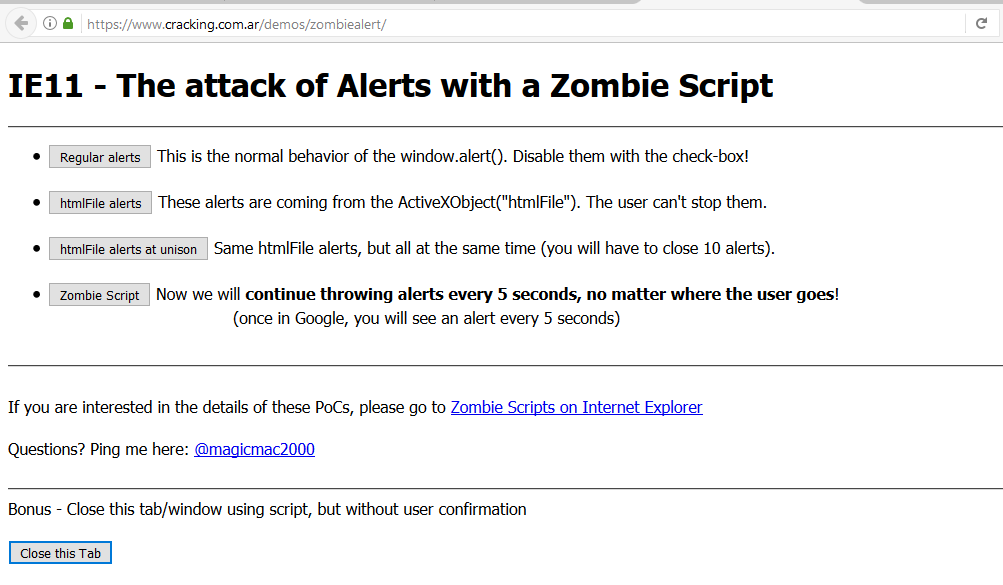
Unfortunately, to fix the problem is not yet possible. Caballero has recently stopped sending error messages to Microsoft, because the company has repeatedly ignored the information provided by the expert. But you can see the problem with your own eyes, it’s enough to go to the test page created by the Argentine. Let me remind you that only the IE11 browser is vulnerable, so the threat cannot be assessed with other browsers (in particular, only regular alerts from the author’s page work in Firefox).
Perhaps, after the publicity, Microsoft will still pay attention to this problem and eliminate it - this vulnerability is already too dangerous for IE11 users.
Source: https://habr.com/ru/post/357278/
All Articles