BugDrop operation. Overhearing more than 70 Ukrainian targets through the built-in microphones on the PC
Information security specialists from CyberX have revealed the details of a major intelligence operation that unknown persons have purposefully conducted in Ukraine. The operation involved installing the malware on the victims' computers and recording conversations through microphones on the PC. If the webcam is usually sealed with tape, then blocking the built-in microphone on the PC is almost impossible.
Technical analysis showed high qualifications of hackers. The complexity of the malware and the excellent coordination of the attack indicate that the attackers have a powerful organization with significant resources. Every day, several gigabytes of audio recordings were downloaded from the victims' computers. The processing of such a data array requires the work of numerous employees.
')
Audio recordings were copied to Dropbox, along with other confidential documents, screenshots, passwords for web services. Therefore, CyberX called this operation BugDrop.
At least 70 people from various fields of activity, including the management of critical infrastructure, the media, and research, have become victims of wiretapping. Most of the victims were in Ukraine (many in Donetsk and Lugansk), several people in Russia, Saudi Arabia and Austria.
Here are some examples of several interception targets:
- Development company of remote monitoring systems for oil and gas pipelines.
- An international organization that monitors human rights violations, is engaged in the fight against terrorism and is investigating cyber attacks on Ukraine’s critical infrastructure (for example, hacking into the electric network of Prykarpattyaoblenergo in December 2015 — an attack of the type BlackEnergy).
- Engineering company that designs electrical substations, gas pipelines, water supply facilities and equipment.
- Research Institute.
- Editors of Ukrainian newspapers.
CyberX experts point out some similarities between the BugDrop operation and another Groundbait intelligence operation, which was identified by ESET in May 2016. There are similarities in tactics, techniques and procedures that were used by hackers. Nevertheless, the BugDrop operation is much more cleverly organized using more complex techniques and procedures. In particular, attention is drawn to the use of DLL injection with reflection (Reflective DLL Injection) - an advanced attack technique that was also used during the BlackEnergy attack on the Ukrainian electrical network, and was also used by the US and Israeli intelligence services in the Stuxnet software uranium enrichment centrifuges.
DLL injection with reflection allows you to download malicious code without resorting to the usual Windows API. In this case, this technique was used to load into memory the encrypted (obfuscated) DLLs, which, due to the use of obfuscation, are not amenable to analysis by most conventional antiviruses and sandbox systems.
To collect data and control the Trojans, hackers used a public infrastructure - free hosting.
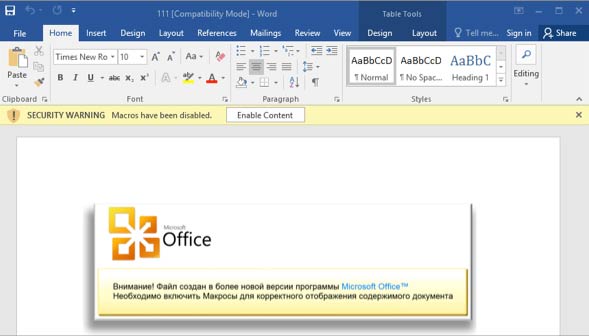
The initial infection of targets was carried out by sending targeted personal letters to each victim. Attached to the letter was a Microsoft Office document with a malicious macro. Hackers used social engineering tactics to convince victims to include macros in Microsoft Office (see screenshot).
The Vordov document itself contained a list of military personnel with personal data, such as date of birth and address.

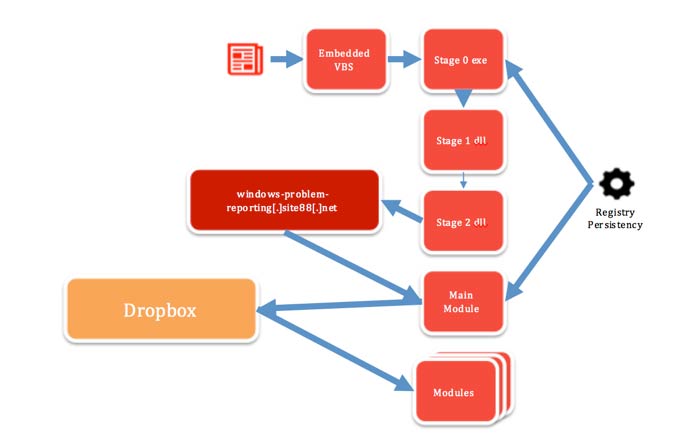
In the Word document, the VB script was triggered, which extracted the main loader to a temporary folder. The boot loader was detected only by 4 of 54 tested antiviruses. Interestingly, the icon for the EXE file with the loader was taken from the Russian-language forum - this is a meme with a joke on the Ukrainians.

Icon source:
The dropper resources were in a DLL, processed by XOR in such a way that the current XOR byte with the previous one is a much more efficient obfuscation technique than the usual XOR.
Libraries were retrieved into a temporary folder and inserted into memory using the Reflective DLL Injection method, and the libraries themselves were registered in the Windows registry.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\drvpath
RUNDLL32 “%USERPROFILE%\AppData\Roaming\Microsoft\VSA\klnihw22.nlp”, RUNNEROne of the libraries then downloaded the main module of the program from a free hosting service to the following address: windows-problem-reporting.site88.net (note: malware can spread to this address, so do not access it from your work computer).
Apparently, manual initiation from the operator’s side was required to initiate the transfer of the main module.
The main module downloaded various plug-ins for different methods of wiretapping and data collection on a computer (plug-ins for searching files on a disk and USB drives, collecting passwords and other data from a browser, recording sound through a microphone, collecting information about a PC). The program checked the security of work - the absence of a virtual environment, the absence of Wireshark, etc., and then also registered in the registry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\hlpAsist
RUNDLL32 “%USERPROFILE%\AppData\Roaming\Microsoft\MSDN\iodonk18.dll”, IDLEAn individual set of plug-ins was used for each victim.
The program sent the collected data to Dropbox via an account with the following credentials:
: P*****
: P********@mail.ruBefore sending to Dropbox, files were processed with the Blowfish cipher. The ID of a specific computer was used as the encryption key.
CyberX has published SHA-256 hashes for files used in the BugDrop operation.
Lure document with the names of military personnel
997841515222dbfa65d1aea79e9e6a89a0142819eaeec3467c31fa169e57076aDropper
f778ca5942d3b762367be1fd85cf7add557d26794fad187c4511b3318aff5cfdPlugins
Collection of screenshots:
7d97008b00756905195e9fc008bee7c1b398a940e00b0bd4c56920c875f28bfe
dc21527bd925a7dc95b84167c162747069feb2f4e2c1645661a27e63dff8c326
7e4b2edf01e577599d3a2022866512d7dd9d2da7846b8d3eb8cea7507fb6c92aKeylogger:
fc391f843b265e60de2f44f108b34e64c358f8362507a8c6e2e4c8c689fcdf67
943daa88fe4b5930cc627f14bf422def6bab6d738a4cafd3196f71f1b7c72539
bbe8394eb3b752741df0b30e1d1487eeda7e94e0223055771311939d27d52f78
6c479da2e2cc296c18f21ddecc787562f600088bd37cc2154c467b0af2621937
01aab8341e1ef1a8305cf458db714a0392016432c192332e1cd9f7479507027fFile collector
06dcf3dc4eab45c7bd5794aafe4d3f72bb75bcfb36bdbf2ba010a5d108b096dc
daf7d349b1b12d9cf2014384a70d5826ca3be6d05df13f7cb1af5b5f5db68d54
24f56ba4d779b913fefed80127e9243303307728ebec85bdb5a61adc50df9eb6
a65e79bdf971631d2097b18e43af9c25f007ae9c5baaa9bda1c470af20e1347cUSB file collector:
a47e6fab82ac654332f4e56efcc514cb2b45c5a126b9ffcd2c84a842fb0283a2
07c25eebdbd16f176d0907e656224d6a4091eb000419823f989b387b407bfd29
3c0f18157f30414bcfed7a138066bc25ef44a24c5f1e56abb0e2ab5617a91000Browser data collection:
fb836d9897f3e8b1a59ebc00f59486f4c7aec526a9e83b171fd3e8657aadd1a1
966804ac9bc376bede3e1432e5800dd2188decd22c358e6f913fbaaaa5a6114d
296c738805040b5b02eae3cc2b114c27b4fb73fa58bc877b12927492c038e27c
61244d5f47bb442a32c99c9370b53ff9fc2ecb200494c144e8b55069bc2fa166
cae95953c7c4c8219325074addc9432dee640023d18fa08341bf209a42352d7d
a0400125d98f63feecac6cb4c47ed2e0027bd89c111981ea702f767a6ce2ef75Microphone:
1f5e663882fa6c96eb6aa952b6fa45542c2151d6a9191c1d5d1deb9e814e5a50
912d54589b28ee822c0442b664b2a9f05055ea445c0ec28f3352b227dc6aa2db
691afe0547bd0ab6c955a8ec93febecc298e78342f78b3dd1c8242948c051de6Collection of information about the computer:
c9bf4443135c080fb81ab79910c9cfb2d36d1027c7bf3e29ee2b194168a463a7
5383e18c66271b210f93bee8cc145b823786637b2b8660bb32475dbe600be46e
d96e5a74da7f9b204f3dfad6d33d2ab29f860f77f5348487f4ef5276f4262311Source: https://habr.com/ru/post/357272/
All Articles