Tor and new anonymity alternatives

Good day, readers GeekTimes! I offer you my translation of the material published earlier by the publication ArsTechnica. In the first part of the publication, the author briefly analyzes the disadvantages and advantages of the Tor network in the light of the events of the past few years, draws conclusions about the possibility of replacing it with alternatives. The second part discusses several modern developments in this area that can compete with Tor or strengthen and supplement it. If you are interested, then under the cut you will find a translation directly.
Since 3 years ago, Edward Snowden left the number one Hong Kong hotel under camera lenses to share with the world the shocking information about mass state surveillance, the popularity of the anonymous Tor network has grown many times. Journalists and activists are willing to use Tor tools to avoid mass surveillance, under which we all live now, and residents of countries where the Internet is subject to censorship, such as Turkey or Saudi Arabia, have turned to Tor in order to bypass state “firewalls”. Law enforcement agencies reacted to the situation with less enthusiasm, expressing concern that online anonymity also contributes to the growth of criminal activity.
')
The growth in the number of network users has not gone unnoticed, and now the “onion router” is under constant pressure from a considerable number of people who want to identify its faceless users. The data released by Snowden indicate that the United States National Security Agency (NSA) and the UK Government Communications Center (CPS) have studied Tor with a view to finding a way to de-anonymize it throughout the past decade. In 2014, the US government paid Carnegie Mellon University for introducing a series of dummy nodes to de-anonymize network users. Also in the past years there was a released scientific work, in general terms, describing a method that allowed, in some circumstances, to conduct an effective attack on the hidden services of Tor. In addition, the presence of 110 hidden fake hidden services was recently discovered that collected information about .onion sites in order to detect vulnerabilities, in a possible attempt to de-anonymize both the servers and their visitors.

An unforgettable and already classic slide “Thor stinks ...” from the collection of documents transferred to the public by Snowden.
The first weaknesses have already been found. A study conducted in 2013 by the US Navy Research Laboratory, initially, by providing support for the development of Tor, concluded that in just half a year, "80% of all types of network users can be relatively easily deanonymized by an attacker who uses infected nodes."
Despite this conclusion, Aaron Johnson, the chief author of the study, the Naval Naval Research Laboratory, thinks that talking about a certain Tor hacking is irrelevant here: the essence of the problem lies in the fact that the project was never intended to be able to withstand the attacks of the world's strongest intruders.
“The threat models may have changed, and these tools are no longer suitable for the goals set several years ago,” he explains. - Tor hasn't changed. The world around has changed.
New threats
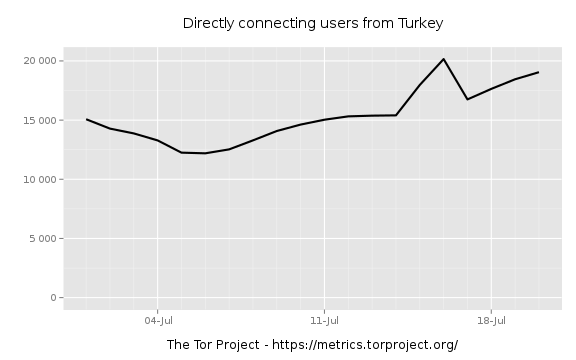
A graph illustrating the dramatic increase in the use of Tor in Turkey during the recent repression of opponents of the authorities
Tor's weakness in analyzing attacks is well known. The original project documentation indicates the vulnerability of the system to a “global passive attacker” capable of listening to all traffic, both entering the Tor network and leaving it. By comparing the two traffic streams, a similar attacker can de-anonymize each user.
However, as co-founder of the Tor project Nick Mathewson explained, the main problem of the network is not at all this.
“No attacker can afford to act truly globally. He, however, does not need such omnipresence, says Matthewson. - To eavesdrop on a large amount of traffic, just a few computers connected to the network will suffice, along with a selective DOS attack that allows artificially redirecting traffic to them. And the organization of such an attack will require only about 10 thousand dollars. "
At the simplest level, an adversary that exploits two malicious nodes — one input and one output — can analyze the traffic and thereby identify a tiny percentage of the least successful users whose data flow went through both these nodes. Currently, of the 7 thousand available Tor nodes, about 2 thousand are input nodes and about a thousand are weekends. Therefore, the probability of such an event is approximately 1 to 2 million (1/2000 x 1/1000).
However, as Professor Brian Ford, who heads the laboratory of decentralized and distributed systems at the Swiss Federal Polytechnic School of Lausanne, explains: “If an attacker can add a sufficient number of input and output nodes, increasing their number, say, so that they start processing up to 10 percent of the global input and output network bandwidth, then he will be able to deanonymize about one percent of all Tor-connections ”.
“As a rule, during a normal browser session, users tend to open multiple connections to different remote websites and HTTP servers at the same time. At the same time, the longer the session lasts, the more connections you open at one time, he adds. “This means that if you use Tor often enough to browse web pages, over time you have several hundred different connections accumulating and you can almost certainly be sure that the owner of the front nodes can easily de-anonymize at least one of your Tor- compound".
For a dissident or journalist concerned about a visit by a secret police, such a disclosure of identity on the network may mean arrest, torture or death.
The hype around Tor and the public discovery of its weak points eventually led to academic research aimed at finding ways to strengthen the network, as well as developing alternative anonymity systems. The priority for most researchers was to find the best ways to prevent traffic analysis. Hypothetically, the new anonymity system may be just as vulnerable to the practice of operating unreliable nodes as Tor. However, any improvement in protection against traffic analysis will make listening sites much less useful for their owners and significantly increase the cost of disclosing the identity of users.
So what’s the biggest obstacle for us to move forward in this area? Firstly, despite all the nuances mentioned above, Tor still remains one of the best solutions for ensuring online anonymity. Secondly, over the many years of its existence, around Tor has grown a strong community consisting of developers and volunteers engaged in the ongoing maintenance of the network. Therefore, if someone succeeds in making a successful attempt to deploy and scale an improved analogue of Tor in the real world, and not just in the lab, then this event in itself will be a very significant achievement.
Reasons for the success of Tor
Tor was designed as a general-purpose anonymity network, optimized to work exclusively with TCP traffic with low network latency. Web browsing was and remains the most important way to use it, as evidenced by the popularity of the Tor Browser Bundle. This popularity has served a good service for those who want to hide their presence on the network, because the more people use Tor, the more difficult it becomes to make passive identification of its individual users.
However, such an architecture also has its costs: browsing web pages using Tor is possible only with low latency indicators (delays in the transmission of information). Naturally, the more time a web page takes to load, the fewer users will wait for it to happen. Therefore, the Tor developers sacrificed a certain degree of anonymity in order to achieve a web browsing speed convenient for most users. At the same time, the scaling of the system leads to the complication of its de-anonymization. The authors of the Tor concept judged that the anonymity that is strong and at the same time accessible to many would be better than ideal, but too slow to solve the problems of most people.
“There are quite a few projects that allow for a greater degree of anonymity by reducing the delay requirements and bandwidth of the Internet channel,” says Matthewson. - The main issue in this area of research is to find the "golden mean". "
“Is it possible to consider a 20-second delay as normal for a chat? - he asks. - Is the use of email acceptable when the delay is five minutes? How many users will agree to work with such a system? ”
According to Matthewson, he is very enthusiastic about some of the other anonymity systems that are emerging today, but at the same time, he urges caution in using them, since they are all at the stage of academic research and are still not prepared for full-scale downloading and application. end users.
Ford agrees with him: “The problem is to take the next big step forward, to go beyond the limits marked Tor. Today we have already come to understand that a significantly higher level of security is quite achievable, but we have to do a lot of work to turn modern developments into a usable product. ”
Can I replace Tor?
The experience of many leaders in the field of ensuring anonymity shows that Tor will not leave the scene soon. According to the most likely scenario, in the future Tor will remain a “good, but not perfect” anonymous public network. As for the new analogs, they will be optimized for specific applications, such as anonymization of the exchange of messages or files, microblogging or voice over IP.
And of course, the Tor Project will not stand still. As not without pleasure Matthewson notes, Tor in its modern form is very different from the first public release, which occurred more than ten years ago. And this evolution will continue.
“I always anticipated that Tor, which we will use in five years, will look very different from the version we use today,” he says. - Whether the project will continue to be called Tor depends largely on who will work on it and release releases. We do not back down from innovation. I always wanted our hands to have better and more practical solutions for protecting the right of people to privacy. ”
Next, we will tell you about five projects dedicated to innovative developments in the field of security. Here is a summary of new creative ideas in this area, from which you will learn about the current status of each project and the assessment of their readiness for full application.
Herd: signal without metadata
Let's start with the twins Aqua and Herd, characterized by the greatest readiness to launch in "combat conditions". Aqua (short for Anonymous Quanta) is an anonymous file sharing network project, and Herd is based on Aqua and has similar parameters, an anonymous voice over IP network. Project leader Stevens Le Blon, a research scientist at the Max Planck Society for Software Systems Institute in Germany, also described Herd as a “signal without metadata” transmission system.
Le Blon said that his team has already implemented a working Herd prototype in its native institute and, along with its colleagues from Northeastern University in the USA, recently received funding for half a million dollars from the US National Science Foundation for the actual deployment of Herd, Aqua and other systems ensure anonymity on the Internet over the next three years. With funding in hand, Le Blon hopes to see the first Herd nodes launched and fully operational by users in 2017.
The work of both Herd and Aqua is based on traffic “stuffing” - random noise, which makes the data diagrams of two different network users indistinguishable. Unlike Tor, which, with certain difficulties, is able to cope with voice over IP in the manner of a shortwave radio , Herd promises to provide practical, secure and anonymous VoIP calls.
“Aqua and Herd try to combine practicality and anonymity by designing, developing, and implementing low-latency and / or high-capacity networks without having to sacrifice some degree of anonymity,” says Le Blon.
Ford believes that, of all modern projects, Herd and Aqua personify the most tangible progress in the development of anonymity technology. “I can well assume that developments such as Aqua or Herd could replace Tor in the future,” he says.
Vuvuzela / Alpenhorn: free metadata chat
Vuvuzela is a project named after a noisy horn, popular with football fans in Africa and Latin America, and its second iteration, Alpenhorn , offers anonymous, metadata-free chat to its users. The best of these available chats today is considered Ricochet . Previously, the Pond project, which is now frozen, also gave high hopes. However, according to project leader David Lazar, Alpenhorn will offer enhanced safeguards to protect privacy.
“Pond and Ricochet rely on Tor, which is known to be vulnerable to traffic analysis attacks,” says Lazar. “Vuvuzela is a new project that protects its users from such attacks and has formalized guarantees of the integrity of transmitted data.”
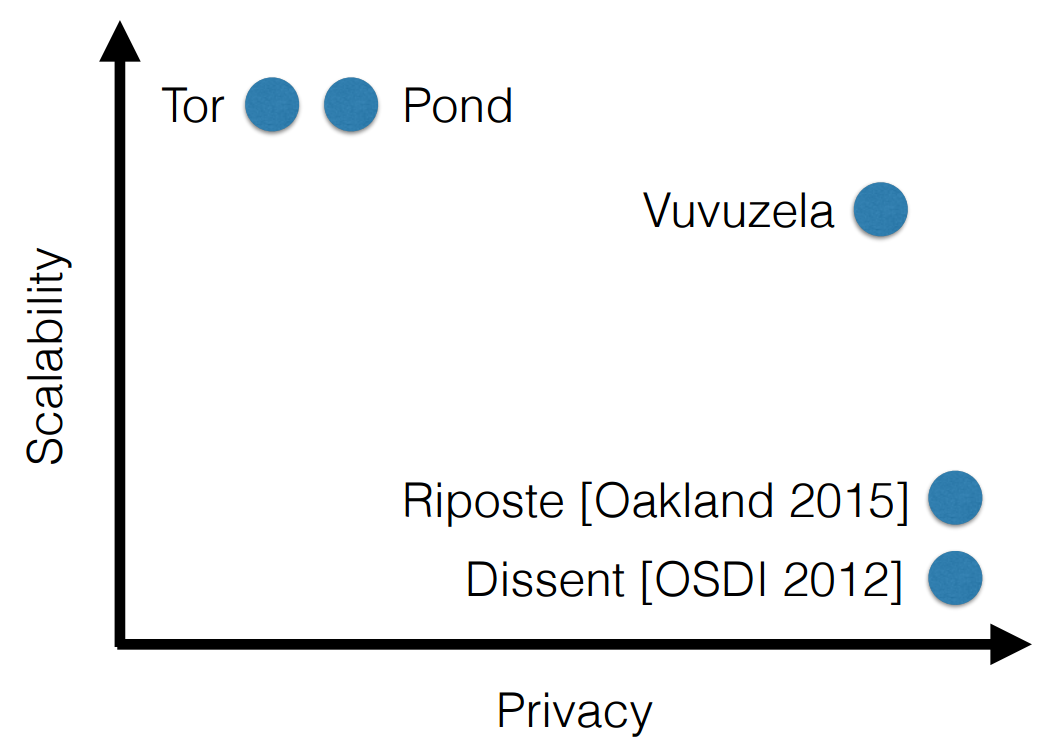
So the creators of Vuvuzela / Alpenhorn see their work in comparison with similar projects.
“Our experiments show that Vuvuzela and Alpenhorn can be scaled to a million users,” he adds. “And now we are working on launching an open beta test.”
The anonymity of the chat is provided by encrypting the metadata, with the addition of noise to those of them that are not subject to encryption and using the method of differential privacy to analyze the degree of anonymity that this noise provides.
Written on Go, the Alpenhorn code fits into only 3 thousand lines . As for scaling, with parallel activity of 1 million users who exchange information with a throughput of 60 thousand messages per second, the network has a delay of 37 messages to send 1 message.
Where is the noise, and where is the discussion of a grandmother's recipe?
The application is developed by a team of researchers from the laboratory of computer science and artificial intelligence MIT. The results of their research, scientists will present at the November event Usenix Symposium 2016.
“At the moment we are working on the final version of the project documentation and are preparing the Vuvuzela and Alpenhorn code for release in production,” says Lazar. “In the meantime, users who want to follow the development of the project can subscribe to our e-newsletter .”
Dissent: squeezing the most out of modern theory
Increased anonymity is always associated with increased requirements for the delay and bandwidth of the Internet channel. The Brian Ford project called Dissent created a sensation a few years ago, promising to provide safety by 11 points on a 10-point scale. The exponential test version of Dissent provided cryptographically confirmed anonymity, noting, however, serious limitations in terms of scalability and practicality.
In contrast to the Tor onion routing model, Dissent’s work is based on the use of a dining cryptographer algorithm, or rather, the so-called DC networks, capable of applying this algorithm for practical purposes. In addition, Dissent also combines DC networks with a scheduled messaging algorithm. As a result of combining these and other technologies, an architecture has emerged, offering almost or not the highest degree of anonymity that can be achieved today.
High network latency and low bandwidth when working with a network will not prevent true dissidents and opposition members to appreciate its capabilities. The optimal scenario of the project application is the group broadcasting of messages that does not require real-time interaction, which is well suited for such activities as blogging and microblogging or even IRC.
DC networks are designed so that when one client wants to send a message to a group of other recipients, their clients must also send a message in the same size to the group. This significantly overloads the channel, with the result that now Dissent can simultaneously support up to several thousand users. However, according to Ford, his team is already working on optimizing the algorithm.
Dissent can also be useful for organizing PriFi — as Ford called integrating his product into a corporate Wi-Fi or campus network. This combination could provide a demonstrably anonymous web browsing within people in the building. That is, a certain passive observer, of course, will be able to learn that someone on campus has been browsing a certain website, but he cannot identify the identity of a particular user. PriFi traffic sent to the Tor network will allow an even higher level of anonymity.
The Dissent team is now redesigning the project and rewriting it for Go, and some of the new components, according to Ford, are already available on Github , but are parts of a whole and are therefore not yet ready for use.
“Unfortunately, this code is not yet ready for use by users who want to“ play around ”with a complete anonymity system,” says Ford. “However, we are pleased to welcome all lovers to delve into the code who want to help us further develop these parts or link them together in a working application.”
Dissent has become something of a cornerstone in the field of anonymity research. The creators of the next two projects drew their inspiration, both from it and from the desire to create a more efficient anonymity system, while preserving the main characteristics of Dissent.
Riffle: anonymous file sharing
Like Aqua, the main use of Riffle is anonymous file sharing. Contrary to some reports that this new development could replace Tor, in fact, Riffle, in the event of its successful launch, can not only complement Tor, but perhaps even speed it up by providing a more secure alternative for anonymous sharing of large files.
“Riffle should not be seen as a replacement for Tor, but as its complement,” says MIT undergraduate and lead investigator for the Albert Kwon project. “We have a completely different goal: we want to achieve the highest possible level of anonymity, without the need to sacrifice practicality.”
As Kwon explained to us, his interest in developing an anonymous file-sharing system has nothing to do with copyright infringement. It's all about wanting to help journalists anonymously send large files and simplify the process of transferring large sets of documents from the whistleblowers to the publishers.
“In Tor, attempts to transfer a very large file in a short amount of time are significantly different from the usual file transfer in an open segment of the Internet,” says Kwon. - Moreover, such a person can give some characteristic signs that can be traced. I would like to create such a file sharing group that will allow everyone to maintain their anonymity. Many journalists would like to be able to work with something like that. ”
Riffle served as a source of inspiration for Dissent, and like him, Riffle uses a message-passing algorithm on a schedule, abandoning, however, the spartan simplicity of DC-network algorithms for general efficiency gains. According to Kwon, the program can also be used for anonymous microblogging, but the academic prototype is not suitable for ordinary users. The next semester is a young researcher planning to devote an open alpha version.
Riposte: anonymous Twitter
Like Riffle, Riposte got its inspiration from the ideas of Dissent, but its architecture was optimized for one single application: microblogging.
“This is an example that any developer who wants to adapt the system design for a specific application can achieve a higher level of performance,” said Henry Corrigan-Gibbs, a graduate student from the Stanford Applied Cryptography Group and lead researcher Riposte. “You can't solve all the problems at the same time.”
Riposte maintains strong anonymity parameters for DC networks, including their resistance to traffic analysis and attacks from malicious clients causing network disruptions. At the same time, the number of simultaneous network users can reach one million people. A side effect is again an increased delay. However, according to Corrigan-Gibbs, such costs are quite acceptable for services operating on the principle of Twitter.
“Anonymity combined with low latency has a congenital disadvantage, which lies in the attacker's ability to see large, or most interesting parts of the network,” he explains.
Riposte now exists as an academic prototype. The Corrigan-Gibbs team is working to improve anonymity and security settings. The project leader himself hopes that at least some of the ideas applied in Riposte will be integrated into existing communication platforms for users concerned with privacy issues.
The Riposte team does not plan to deploy a network on its own, at least for now. “I came up with an architecture and developed a prototype system to show that it works,” explains the researcher. “In order to create something truly serious, a completely different set of important skills is required. The scale of the Tor Project is impressive, as is the ability of its participants to keep afloat a distributed system of such enormous size with relatively little funding. ”
From research to reality
The gap between academic research and practical implementation is a challenge for researchers who want to scale up their prototypes of next-generation anonymity technologies and run them in the real world. Academicians who want to build a career as professors are faced with a system that encourages the publication of scientific ideas and the development of proof of concepts. When it comes to the development of a practical product, its distribution and user engagement, the academic community is not interested in these processes.
In addition, as the researchers themselves admit, the set of skills required for full-scale practical implementation of the software is in no way connected with their main research activities. “Most of the work on the development of next-generation anonymous networks is done in the research community, and this is usually not the best option in terms of getting full-fledged, applicable products in the real world,” says Ford. “In my group at the Federal Polytechnic School of Lausanne, I try to change this situation at least at the local level.”
Mathewson is sympathetic to this, since Tor began its existence as a research paper, the practical results of which he, he said, wanted to observe for several years, subsequently transferring the project to someone else. More than 10 years later, the Tor Project participants gained deep experience in maintaining the network's performance, which has become a vital infrastructure for many dissenters and the only barrier between the unwanted regime of tweeting or a blog post and the visit of the secret police.
Mathujon gives researchers the following advice: try your products on yourself.
“I have already talked about this before. „ , “, — . — — Tor , , ».
« , , , , — . — , . , , , ».
, , , -, WhatsApp Signal.
« , , , , , , , , — , Speech, Privacy, and Technology ».
« , . , , -, , , — . — , , , , , ».
Source: https://habr.com/ru/post/357186/
All Articles