"Hunter for sysadmines" from the NSA contacted
Network Engineer resigned from the NSA Electronic Intelligence Department and was interviewed

There are thousands of system administrators around the world. They set up computer networks, maintain servers in working condition, even without suspecting that they are one of the priority targets of special services.
In March 2014, Edward Snowden provided a number of NSA secret documents for publication - screenshots from the internal platform for communication of agency staff (screenshots under the cut). One of the participants of the discussion describes in some detail his professional duties in several messages, one of which is entitled “I hunt for sysadmins”.
')
The author used specific slang (pwn, skillz, zomg, internetz) and naughty emoji, which is rather unusual for an NSA operative.
The hacker explains that the sysadmins themselves are not a target for SIGINT operations, but for the NSA it is extremely important to have access to their computers and own their credentials, which may be needed in the future to access the local infrastructure. Therefore, the NSA hacks the work and personal computers of system administrators who work for foreign Internet providers and telecom operators to monitor traffic in the internal networks of these companies.
The hunt for sysadmines in the NSA was put on stream. The agency sought to compile a comprehensive database - an international "list of targets" of sysadmins that may be useful. That is, those who need to hack. At the same time, the documents explicitly state that the system administrators from the list do not necessarily have to be noticed in any criminal activity, they are entered into the list solely because they have access to the networks of interest to the NSA.
The documents list specific data that should be collected from personal and work computers of system administrators. These are maps of network routing, user lists, working mail correspondence and, the author jokes, “pictures of cats in funny poses with funny signatures”. If no joke, then in the database entered the IP-addresses of computers system administrators, their mailboxes and accounts in social networks, if such could be found. The author wrote that the NSA uses QUANTUM hacking techniques to install “implants” on the computers of system administrators who logged in to Facebook. About this hacker wrote with his characteristic expression.
The Intercept organization, which published the documents received from Snowden, at one time hid the name of the NSA employee, who published messages about the “sysadmin hunt” with naughty emoticons. But she noted at the same time that the guy is a network engineer in the Electronic Intelligence Agency of the NSA (Signals Intelligence Directorate). He is also the author of the scandalous NSA presentations, which caused a lot of noise in the press, about the de-anonymization of Tor users : presentation 1 , presentation 2, presentation 3 . In short, the algorithm is to monitor several Tor nodes, as well as to recognize (fingerprinting) Tor clients in the place where traffic goes from a Tor node to a specific site, for example, Google. Such requests are intercepted by means of hidden servers of the NSA on the main communication channels. Then, on Tor users' computers, the FoxAcid exploit pack is applied, containing exploits for Firefox 10.0 ESR 0day vulnerabilities (this browser was used in the Tor Browser Bundle client software bundle at the time of the NSA presentations).
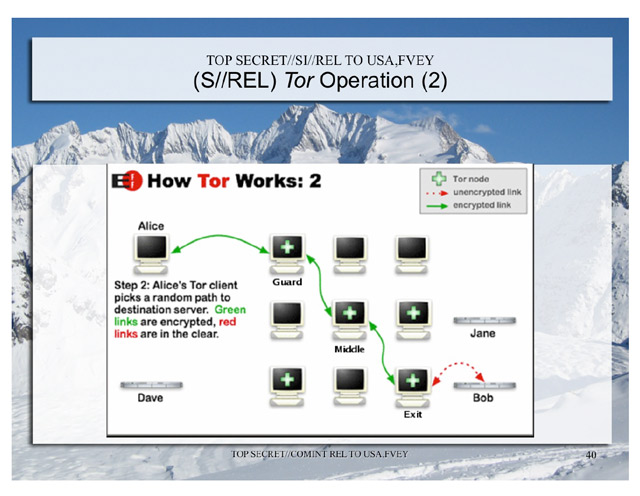
Slide from NSA presentation on de-anonymization of Tor users
It was reported that the network engineer used to work in a private company, a contractor for the NSA, and then moved to the intelligence department. In one of the messages, he is indignant because of the poor quality of presentations at hacker conferences Blackhat / Defcon, that is, the guy often visited these conferences and considered himself one of the elite hackers (most likely, not without reason).
Two years after the publication of those documents, much water has flowed. It turned out that the mischievous hacker quit the NSA and went to work in the private sector, in one of the companies in the field of information security. He even agreed to talk with The Intercept project staff . An employee of the project writes that during the three-hour video chat, they discussed many topics, from ethical issues of surveillance of the population to the difficulties of home repairs and ways to secure the laptop as much as possible.
A hacker sat in front of a computer in a black sweatshirt with the name of one of his favorite heavy metal bands Lamb of God . With a thick beard and tattoos, he looked like a typical representative of the underground, and not at all like a former employee of a government agency.
At home, behind a man, you could see a cat scratcher and beautiful wooden ceilings on the ceiling. Workers carried out repairs in the house, constantly drilled, sawed and pounded. The hacker came off to talk on the phone with his wife, and the interview was periodically interrupted by dog bark: “I apologize, the cats again mock my dog,” the former NSA officer apologized. Later this dog jumped on the desktop and began to lick his face.
As it was possible to assume, the employees of the most powerful special services in the world are quite ordinary people, with their own weaknesses and everyday problems. A certain stereotype has emerged in society about asocial hackers, but in reality, if you take a survey between the two, it turns out that most of them actually have official work and retirement savings, The Intercept writes, stressing that this is the merit of state special services, who were able to lure many hackers into their ranks (the FSB in Russia does the same, not without success).
Reportedly, the state’s strategy was to toughly fight independent hackers and award them maximum prison sentences, while at the same time softly offering to help their homeland (the carrot and stick method). By the way, such a strategy was used in the notorious history of the Ukrainian hacker Maxim Popov, who was recruited by the FBI .
It is known from declassified documents that the real hacker culture flourishes in the NSA: geeks, nerds and hackers work side by side, and at hacker conferences like Defcon they feel completely at ease with like-minded people. In 2012, the director of the NSA, General Keith Alexander (Keith Alexander) even visited Defcon in jeans and a black T-shirt EFF (it was a good attempt, but the NSA leadership tried not to appear there anymore).

At the same time, a page was launched on the NSA website , where the NSA welcomed Defcon visitors and invited them to work.
In general, the “sysadmin hunter” belongs to the same hacker subculture that the National Security Agency tried to attract. Talking about the past, he recalls how he began to be interested in information security: he was just interested in finding out everything, he spent hours studying the packages at Wireshark, trying to understand what computers are transmitting to each other, reading literature. After his appointment to the NSA, he was able to learn a lot from agency veterans, experienced computer scientists.
Ethics issues are constantly discussed in the NSA. Employees are trying to determine how ethically it is to track the personal communications of the same sysadmins, their personal mail, accounts in social networks.
During the interview, The Intercept journalist asked, what would he feel on the site of the sysadmin of a foreign company if someone purposefully led him to hunt and try to hack. He smiled: “There is no real security anywhere. Whatever you do on the Internet, this is part of the attack in one form or another, you have to live with it. Every time I go online and do something, this thought remains in my head. From an inexperienced script kiddie to a random hacker or foreign intelligence — what can they do to me? ”This must always be remembered.
A former NSA official says most people scorn for Internet security. Their attitude is approximately like this: “I will just quickly leave naked from home, no one will look at me . ”
The engineer believes that it is not the fault of the intelligence community that people do not want to use Tor, Signal and other tools to ensure their security.
At the same time, he believes that absolute security cannot be achieved. Like in the joke that the only safe computer is the one that was turned off and buried in the ground. In reality, those who want to find holes, invest enough resources in it, can always achieve their goal. Everything can be hacked, it is only a matter of time and money.
As part of the project The Intercept previously published articles about some other interesting employees of the NSA. For example, about the former writer and linguist who writes the ethics column for the corporate newspaper of the NSA, as well as the middle manager under the nickname Zelda, who leads the Ask Zelda! Question and answer heading in the corporate newspaper. There she answers everyday questions of NSA office workers. For example, what to do if a colleague smells badly or he falls asleep at work, what to do if the boss does not respond to e-mails and who steals soda from the common fridge (for example, “Ask Zelda!” Column ).

There are thousands of system administrators around the world. They set up computer networks, maintain servers in working condition, even without suspecting that they are one of the priority targets of special services.
In March 2014, Edward Snowden provided a number of NSA secret documents for publication - screenshots from the internal platform for communication of agency staff (screenshots under the cut). One of the participants of the discussion describes in some detail his professional duties in several messages, one of which is entitled “I hunt for sysadmins”.
')
The author used specific slang (pwn, skillz, zomg, internetz) and naughty emoji, which is rather unusual for an NSA operative.
The hacker explains that the sysadmins themselves are not a target for SIGINT operations, but for the NSA it is extremely important to have access to their computers and own their credentials, which may be needed in the future to access the local infrastructure. Therefore, the NSA hacks the work and personal computers of system administrators who work for foreign Internet providers and telecom operators to monitor traffic in the internal networks of these companies.
Screenshots from the NSA internal server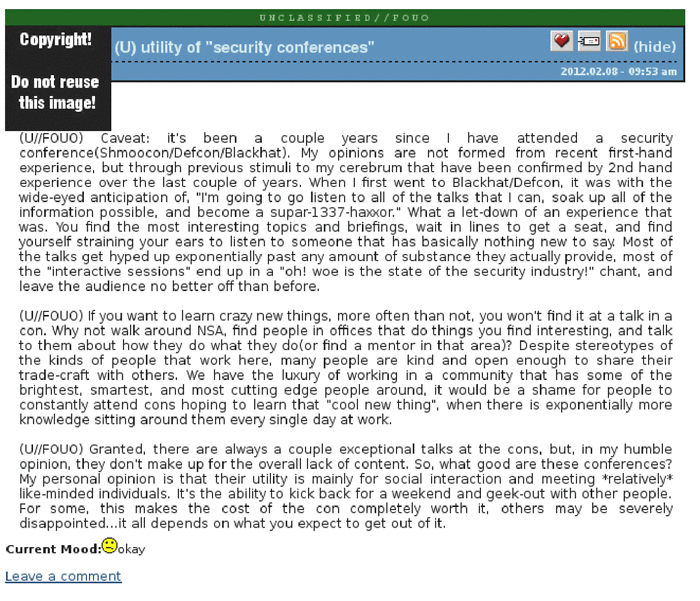
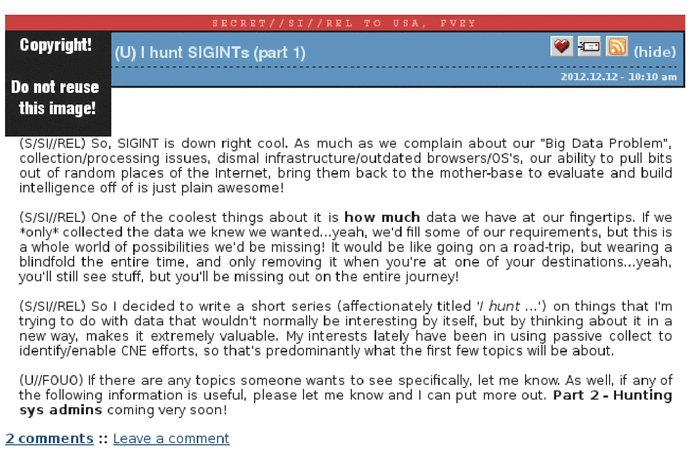

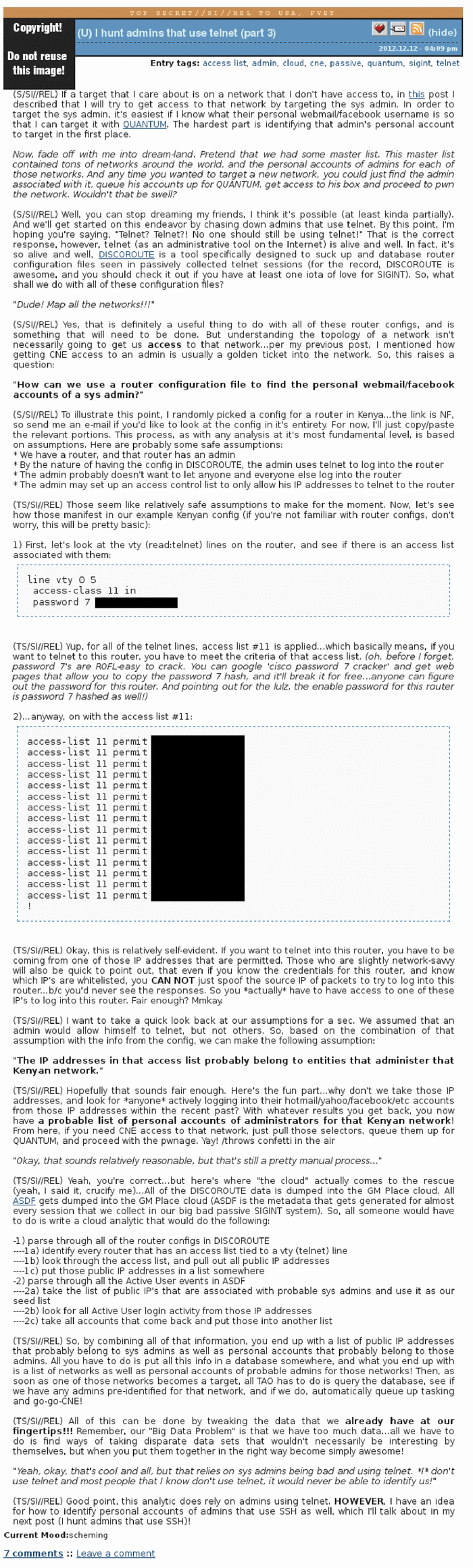

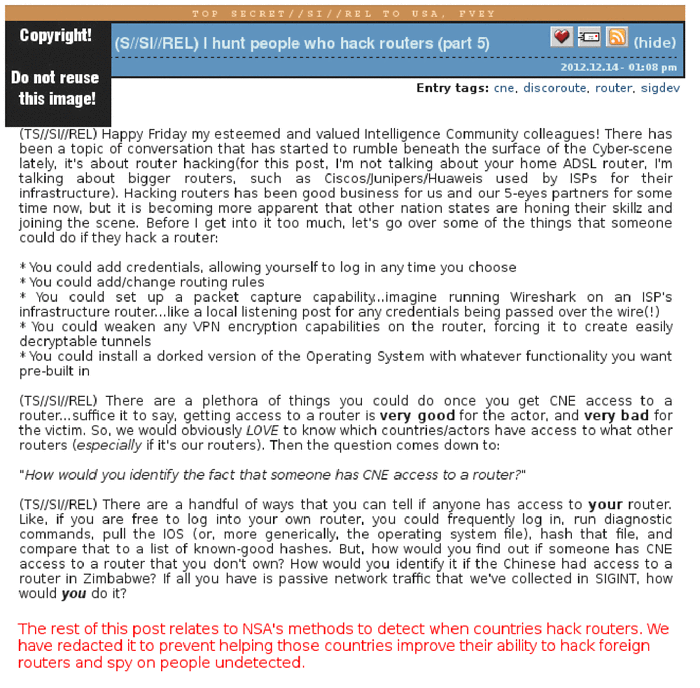






The hunt for sysadmines in the NSA was put on stream. The agency sought to compile a comprehensive database - an international "list of targets" of sysadmins that may be useful. That is, those who need to hack. At the same time, the documents explicitly state that the system administrators from the list do not necessarily have to be noticed in any criminal activity, they are entered into the list solely because they have access to the networks of interest to the NSA.
The documents list specific data that should be collected from personal and work computers of system administrators. These are maps of network routing, user lists, working mail correspondence and, the author jokes, “pictures of cats in funny poses with funny signatures”. If no joke, then in the database entered the IP-addresses of computers system administrators, their mailboxes and accounts in social networks, if such could be found. The author wrote that the NSA uses QUANTUM hacking techniques to install “implants” on the computers of system administrators who logged in to Facebook. About this hacker wrote with his characteristic expression.
Just pull those selectors, make them up for QUANTUM, and proceed with the pwnage. Yay! / throws confetti in the air.
The Intercept organization, which published the documents received from Snowden, at one time hid the name of the NSA employee, who published messages about the “sysadmin hunt” with naughty emoticons. But she noted at the same time that the guy is a network engineer in the Electronic Intelligence Agency of the NSA (Signals Intelligence Directorate). He is also the author of the scandalous NSA presentations, which caused a lot of noise in the press, about the de-anonymization of Tor users : presentation 1 , presentation 2, presentation 3 . In short, the algorithm is to monitor several Tor nodes, as well as to recognize (fingerprinting) Tor clients in the place where traffic goes from a Tor node to a specific site, for example, Google. Such requests are intercepted by means of hidden servers of the NSA on the main communication channels. Then, on Tor users' computers, the FoxAcid exploit pack is applied, containing exploits for Firefox 10.0 ESR 0day vulnerabilities (this browser was used in the Tor Browser Bundle client software bundle at the time of the NSA presentations).

Slide from NSA presentation on de-anonymization of Tor users
It was reported that the network engineer used to work in a private company, a contractor for the NSA, and then moved to the intelligence department. In one of the messages, he is indignant because of the poor quality of presentations at hacker conferences Blackhat / Defcon, that is, the guy often visited these conferences and considered himself one of the elite hackers (most likely, not without reason).
Two years after the publication of those documents, much water has flowed. It turned out that the mischievous hacker quit the NSA and went to work in the private sector, in one of the companies in the field of information security. He even agreed to talk with The Intercept project staff . An employee of the project writes that during the three-hour video chat, they discussed many topics, from ethical issues of surveillance of the population to the difficulties of home repairs and ways to secure the laptop as much as possible.
A hacker sat in front of a computer in a black sweatshirt with the name of one of his favorite heavy metal bands Lamb of God . With a thick beard and tattoos, he looked like a typical representative of the underground, and not at all like a former employee of a government agency.
At home, behind a man, you could see a cat scratcher and beautiful wooden ceilings on the ceiling. Workers carried out repairs in the house, constantly drilled, sawed and pounded. The hacker came off to talk on the phone with his wife, and the interview was periodically interrupted by dog bark: “I apologize, the cats again mock my dog,” the former NSA officer apologized. Later this dog jumped on the desktop and began to lick his face.
As it was possible to assume, the employees of the most powerful special services in the world are quite ordinary people, with their own weaknesses and everyday problems. A certain stereotype has emerged in society about asocial hackers, but in reality, if you take a survey between the two, it turns out that most of them actually have official work and retirement savings, The Intercept writes, stressing that this is the merit of state special services, who were able to lure many hackers into their ranks (the FSB in Russia does the same, not without success).
Reportedly, the state’s strategy was to toughly fight independent hackers and award them maximum prison sentences, while at the same time softly offering to help their homeland (the carrot and stick method). By the way, such a strategy was used in the notorious history of the Ukrainian hacker Maxim Popov, who was recruited by the FBI .
It is known from declassified documents that the real hacker culture flourishes in the NSA: geeks, nerds and hackers work side by side, and at hacker conferences like Defcon they feel completely at ease with like-minded people. In 2012, the director of the NSA, General Keith Alexander (Keith Alexander) even visited Defcon in jeans and a black T-shirt EFF (it was a good attempt, but the NSA leadership tried not to appear there anymore).

At the same time, a page was launched on the NSA website , where the NSA welcomed Defcon visitors and invited them to work.
In general, the “sysadmin hunter” belongs to the same hacker subculture that the National Security Agency tried to attract. Talking about the past, he recalls how he began to be interested in information security: he was just interested in finding out everything, he spent hours studying the packages at Wireshark, trying to understand what computers are transmitting to each other, reading literature. After his appointment to the NSA, he was able to learn a lot from agency veterans, experienced computer scientists.
Ethics issues are constantly discussed in the NSA. Employees are trying to determine how ethically it is to track the personal communications of the same sysadmins, their personal mail, accounts in social networks.
During the interview, The Intercept journalist asked, what would he feel on the site of the sysadmin of a foreign company if someone purposefully led him to hunt and try to hack. He smiled: “There is no real security anywhere. Whatever you do on the Internet, this is part of the attack in one form or another, you have to live with it. Every time I go online and do something, this thought remains in my head. From an inexperienced script kiddie to a random hacker or foreign intelligence — what can they do to me? ”This must always be remembered.

A former NSA official says most people scorn for Internet security. Their attitude is approximately like this: “I will just quickly leave naked from home, no one will look at me . ”
The engineer believes that it is not the fault of the intelligence community that people do not want to use Tor, Signal and other tools to ensure their security.
At the same time, he believes that absolute security cannot be achieved. Like in the joke that the only safe computer is the one that was turned off and buried in the ground. In reality, those who want to find holes, invest enough resources in it, can always achieve their goal. Everything can be hacked, it is only a matter of time and money.
As part of the project The Intercept previously published articles about some other interesting employees of the NSA. For example, about the former writer and linguist who writes the ethics column for the corporate newspaper of the NSA, as well as the middle manager under the nickname Zelda, who leads the Ask Zelda! Question and answer heading in the corporate newspaper. There she answers everyday questions of NSA office workers. For example, what to do if a colleague smells badly or he falls asleep at work, what to do if the boss does not respond to e-mails and who steals soda from the common fridge (for example, “Ask Zelda!” Column ).
Source: https://habr.com/ru/post/357136/
All Articles