The effect of the cobra. Keylogger on eBay and ban on copy-paste password

During the British Empire, the British had a small problem on the Indian subcontinent - the cobra. It turned out that there are a hell of a lot of these reptiles everywhere. And it turned out that they are poisonous. The colonists did not like it, some of them died. Therefore, the British authorities have come up with an excellent way out. For each killed cobra, the natives began to pay a small reward. It would seem that the problem is solved.
Unfortunately, the Indians have differently interpreted the terms of remuneration. They considered this an excellent reason to breed poisonous snakes and donate them for money. Realizing the problem in the original logic, the British authorities canceled the payment of rewards. Well, the Indians had no choice but to release a huge number of cobras to freedom. As a result, their number in Indian forests has grown many times.
')
From there went the expression of the effect of the cobra . A situation where the decision taken to correct a problem does not correct this problem, but leads to the opposite result.
The effect of the cobra has to be remembered, looking at some of the security measures that are implemented to protect users on individual sites. For example, websites are forced to use passwords with special characters and numbers, thereby cutting off the most reliable passphrases of 40-50 characters with the highest entropy. Or even a stranger "security measure" - a ban on copy-paste in the password entry field .
The ban on copy-paste in the password field
Apparently, in this way the site is protected from hackers who copy-paste paste someone else's passwords from the database with stolen passwords.
The explanation is ridiculous, but in reality many sites have already banned copy-paste in the password field. For example, on GE Capital sites it is impossible to copy the password in the input field during authorization. Of course, this is done for safety . But users are not explained the reasons. No “For your safety” messages or the like. The password just disappears.
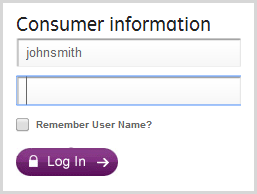
On PayPal, a similar blocking is valid on the password change page (by the way, along with draconian and completely unnecessary restrictions on the password length of 20 characters).
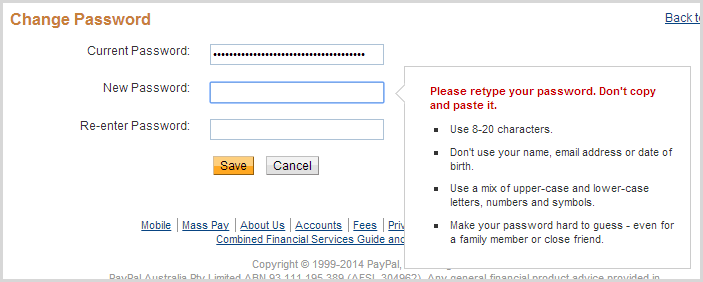
Well, at least here they explain why everything is started.
The most interesting thing is that blocking the input of a password is often implemented using onpaste - a nonstandard event that Microsoft once invented for its Internet Explorer browser.
<input type="password" name="j_password" class="DataPasive" maxlength="14" size="23" onkeypress="return logonWithEnter(event)" autocomplete="off" onpaste="return false"> Surprisingly, this non-standard event still works, not only in Internet Explorer, but also in Chrome, and in Safari, and in Firefox. And if it didn’t work, there are other bright ideas on how to “hack” the functionality of Ctrl + V (Shift + Ins) in browsers.
Such “protection against hackers” is simply absurd, says well-known security specialist Troy Hunt (because the only truly secure password is one that you cannot remember (without taking into account long passphrases that are already blocked by others). password restrictions). Accordingly, to generate a password with maximum entropy, it is better to use specialized password generators and password managers like 1Password , KeePass or LastPass . The point is that you delegate the function of “remembering” the password to your password manager, and you will store dozens of generated unique passwords in a secure place protected by a single master password.
By blocking password copy-paste, sites actually try to prevent the use of password managers, that is, de facto they reduce the level of user security (although some password managers can bypass such copy-paste blocking).
Ebay keylogger
Another interesting example of how sites care about the security of their users is the keylogger function in the form of resetting a password on the eBay website.
In the browser console, you can make sure that when entering a password, the browser sends dozens of POST requests to eBay servers.
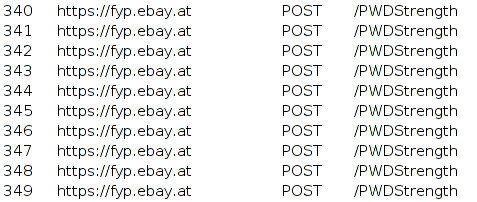
It's good that the keylogger works on HTTPS.
Each time you press a key in the password entry window, a request is sent. Judging by the fact that they go to / PWDStrength , it can be assumed that the password strength verification module works in a peculiar way, which evaluates its entropy and informs the user of the result: its password is “good” or “bad”.
In principle, this JavaScript module usually works on the client side, and then the need for such a keylogger and POST requests for each keystroke would disappear.
What is completely incomprehensible is why with each POST request for each keystroke a username and an email address are added to the POST body.
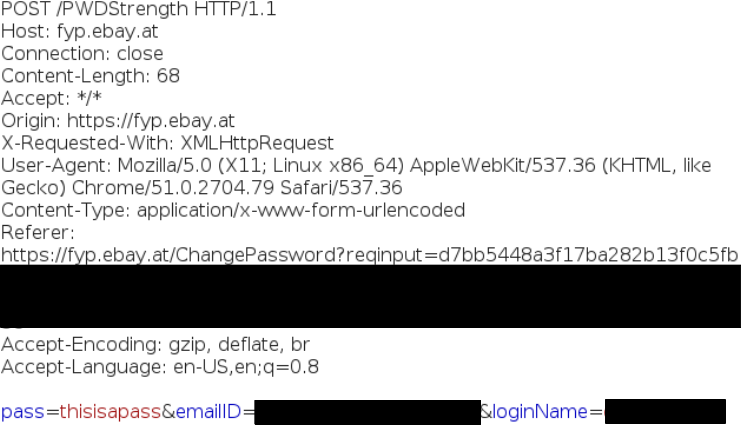
In principle, such a keylogger is not very dangerous, because all information is sent over a secure HTTPS connection, although it is somehow strange to feel that with each click a request is sent with your email address and username.
EBay has a rewards program for the vulnerabilities found. When one of the hackers reported a bug, an employee of the company sent an official response :
Hello David!
Thanks for your letter. There are some reasons why the current implementation works, but I will not be able to provide you with additional information about this.
Thank,
eBay Security Research
We can only guess about the reasons why with each character to send an email address.
But it is fine. Another thing is worse: in some other places on the eBay website, when the password is changed, the keylogger sends not POST requests, but GET requests for each keystroke.

Although there is no email address and username in the request body, this is already more dangerous , because GET requests can be cached on proxy servers and stored in logs.
In general, developers always want to remember the experience of the British colonialists in India - they also wanted the best ...
Source: https://habr.com/ru/post/357132/
All Articles