How to open sites blocked by the provider and hidden onion-services in the main browser (Firefox)
And at the same time support the Tor project at no extra cost
I am a longtime fan of the Tor network and the features it provides. I prefer to visit sites without supervision from above, without restrictions imposed by certain individuals trying to control my life. And I like the presence of hidden services, although I practically do not use them, but the fact that it is possible to launch such a service pleases an internal cryptanarchist.
Therefore, I have always launched a set of experts , which I set up to work as an intermediate node - so I make a modest contribution to supporting the Tor network. In the settings of the site, you can limit the maximum traffic that will be eaten off for the needs of the network.
Of course, the highest privacy is ensured by the use of the Whonix system, and to whom it is inconvenient - at least go through the sites through the Tor Browser. But I read the criminal code, and I don’t have a reason to hide so much - sometimes I just want to go to the site to which my provider denied access, or to open a service with the .onion domain
')
Since I don’t use the Tor Browser for this purpose every time, I don’t use Opera and Yandex browsers, but for some reason I didn’t work with the common anti-blocking solutions (friGate and so on) - I developed my own system allowing you to open as blocked sites and hidden services.
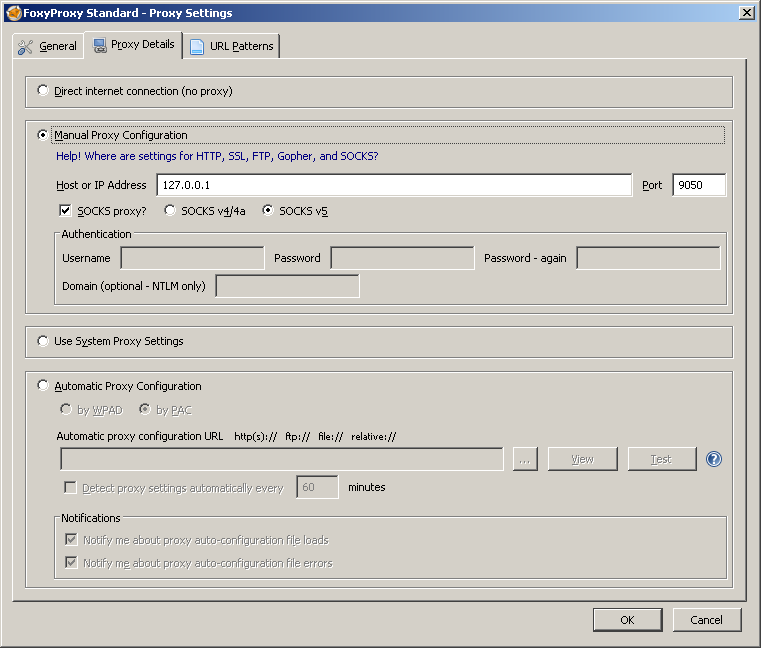
I use the Firefox browser, and for the operation of the system I need to install only one plugin - FoxyProxy. If the Tor node is already up and running, then by default it will provide a proxy service at 127.0.0.1: 9050. Using this proxy, you can go to blocked sites and to the .onion domains.
To use a proxy only in these cases, you need to configure the FoxyProxy plugin. It is intended for selective use of rule-based proxy servers. In our case, the rules will be simple - the inclusion of a proxy on the domain mask.

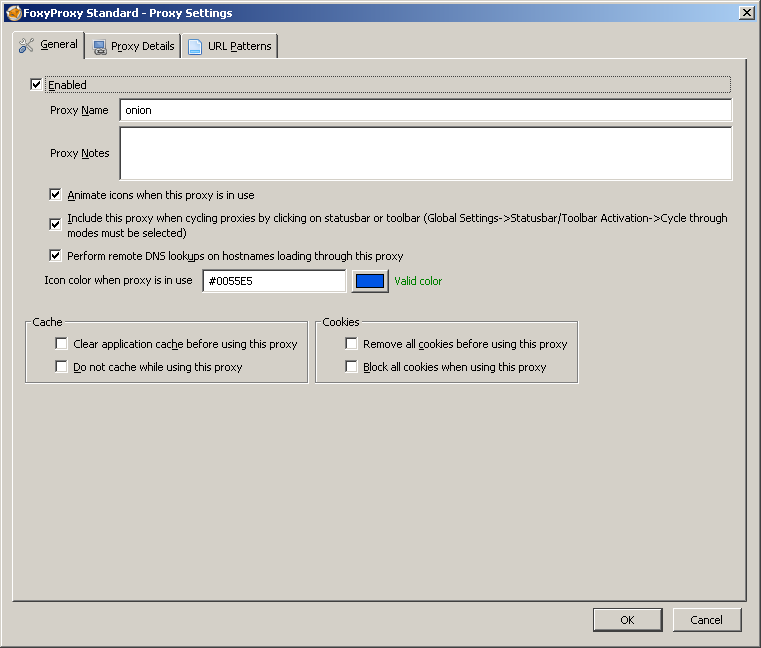
In the main window of the plugin you need to add a new proxy. In the add window in the first tab, you only need to come up with a name (I chose “onion”), in the second, select the manual configuration and set the ip-address and port (127.0.0.1: 9050), as well as tick SOCKS.
In the third, we will add a few rules, subject to which this proxy will be included, sending requests through the Tor network.
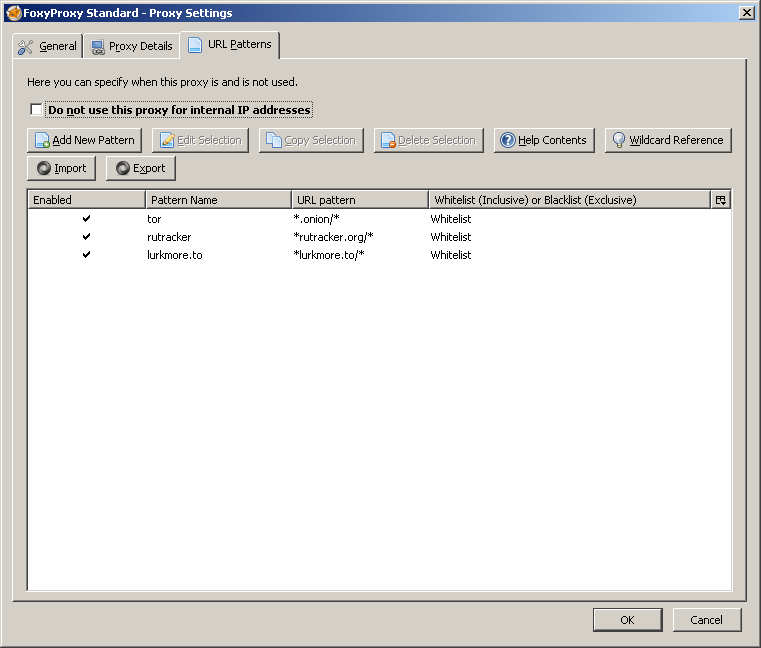
To create a rule, you need to create a domain name and mask for it. For hidden sites, Tor mask looks like
*.onion/* . After the rule is saved, all sites with the .onion domain will open via proxy 127.0.0.1: 9050 - that is, via the Tor network.
Similarly, sites are added, the entrance to which is blocked by the provider (example:
*lurkmore.to/* ).No further action is required - when executing any of the rules, FoxyProxy forces Firefox to send requests via the Tor network. If you need high-quality privacy, it is better to use the Tor browser - it takes into account most of the holes in Firefox. Of course, the best solution remains Whonix with embedded virtual machines - but this is already a choice of hackers, unscrupulous people and heavy paranoids.
Source: https://habr.com/ru/post/357100/
All Articles