The war of legislation and programmers: anonymity and the secret of correspondence in 2016
The first half of 2016 is almost over, there are only two months left. It would seem that only recently the laws on “blacklists” and bloggers were passed in the last reading, the legislation on non-cash payments has been tightened - but four years have passed since the introduction of the first of these laws to the parliament. And over the past four years, the arms race, legislation against technical means of anonymizing and ensuring the privacy of correspondence, was hotter than ever. One of the most striking episodes of this struggle was, of course, the disclosure of the surveillance program of the US National Security Agency, NSA.

However, we are living in Russia, and recently the situation continues to deteriorate - if in other countries a civilian request for greater openness of government agencies is able to stop statesmen in their endeavors (for example, you can take the same SIPA , which the guys from Fight For The Future ), then, alas, we are not so rosy. Of the latest “good” news on this front, another tightening of legislation in the field of data storage by telecom operators, held under the guise of “anti-terrorist amendments”; development of commercial tools for listening to calls in mobile networks - for example, the same InfoWatch Natalia Kaspersky. Do not forget about the recent loud hacking of accounts in the Telegram , carried out, apparently, with the direct assistance of the mobile operator.
')
In connection with all this, the demand for technical means to bypass site locks, preserve the privacy of correspondence and anonymize the web is extremely high - so let's see how things are going on for the main projects on this front, namely Tor, I2P and Tox.
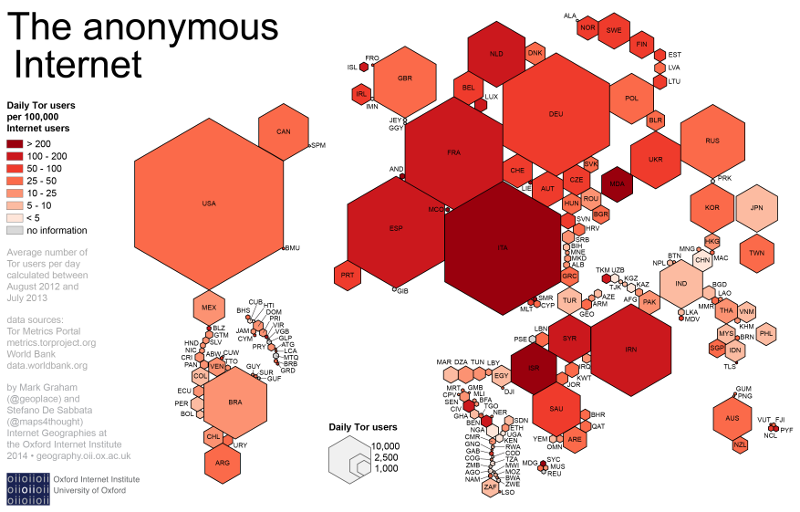
Tor, the “oldest” of all the projects that will be mentioned today, continues to bloom and smell. Being originally developed by the US Navy in conjunction with DARPA, from the end of zero to the present day, the project has evolved from a marginal project for a few technically knowledgeable users to the absolutely necessary tool today that ordinary people have finally begun to use. As of February 2016, there were more than seven thousand weekend nodes in the network, and the total number of participants in the network exceeded two million - and already in 2014, Russia ranked third in the world in the number of users.
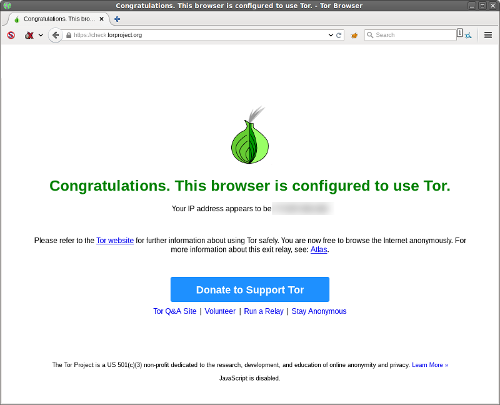
A very large increase in the user base was achieved, among other things, thanks to the active development of the Tor Browser bundle, which is now the “flagship”, to some extent, product of the project - previously this was the package consisting of the Tor daemon and the Vidalia graphic panel but the user was offered to choose the browser himself. Being based on the Firefox ESR (Firefox edition of "extended support", the closest analogue is the Ubuntu LTS editions), due to the mass of custom patches aimed at minimizing user information leaks, and also due to the fact that must-have extensions like NoScript, AdBlock and HTTPS Everywhere, Tor Browser is currently the simplest and safest “single-click” solution for the end user.
Tor is currently available in one form or another on absolutely all platforms, including mobile. Also in 2014, several projects of hardware routers appeared on Kickstarter, the application case of which meant the transparent passage of all network traffic connected to them via Tor. Most of these projects were canceled - in particular, the administration of Kickstarter stopped collecting funds for the German project Anonabox due to the fact that the developers were not completely honest with the backers regarding the hardware and software of the project. At the same time, the amount collected by backups on Anonbox exceeded half a million dollars (with an initial goal of $ 7,500), which clearly shows how important anonymity is for users around the world.
If Tor is intended to access the familiar to all of us Internet, the main idea of I2P is to create an overlay network that uses the Internet purely as a transport network, completely distributed, and in no way dependent on it, in which all information is multi-level encrypted. Having started its development in 2003, the network came to the more or less familiar look of the network closer to the beginning of the tenth years of this century, just to the beginning of the end of the free Internet era.
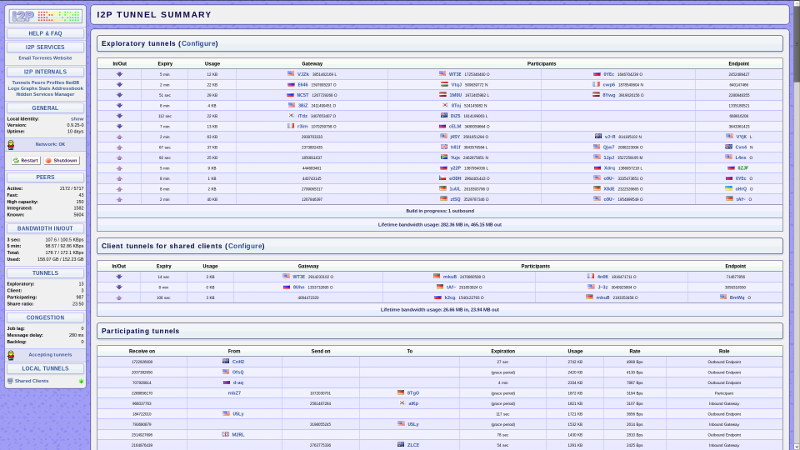
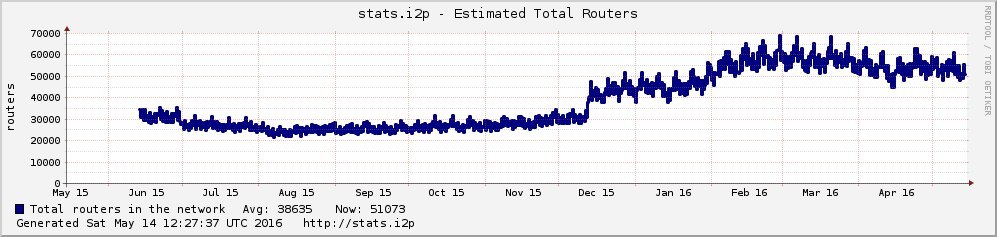
Most of the “Habrakhabra” audience and related resources are certainly aware of the basic I2P functionality, and therefore we limit ourselves to news. The network continues to grow rapidly, and at the moment Russia is the second number in terms of the number of nodes (routers), and their total number is close to 70 thousand. Every day, 300-400 new routers come to the network, of which up to half remain active on average. About ten thousand nodes play the role of floodfills, i.e. they deal exclusively with passing someone’s traffic to neighboring nodes.
In the past couple of years, the project has been actively developing the mobile version of the router, which is currently available for Android end users, including on Google Play and F-Droid. Despite the fact that due to the network structure, mobile devices cannot be considered as a sufficiently secure environment, and the quality of communication is not sufficient to pass other people's traffic through the router, the current implementation is quite enough to access sites on the network. In addition, work is underway to improve the anonymity of I2P mobile users - the draft of the mobile router is in the state of active development.
In addition to working on the network itself, the I2P Project is also involved in educational activities: in December 2015, project representatives took part in the 32nd Chaos Communication Congress conference held in Hamburg (Germany).
If Tor and I2P are aimed at a wide range of services that can work in them, and are general-purpose networks, then Tox was created exclusively as a protected messenger. The starting point was the release of information about NSA surveillance programs by Edward Snowden. After mentioning Microsoft's mass collaboration with state agencies, as well as details of listening operations on Skype, a thread appeared on one of the world's largest imageboard, 4chan, dedicated to the creation of a secure messenger that would be completely “closed” from wiretapping, functionally not inferior to Skype, and was fairly simple to use for the average user. This was the beginning of the development of Tox.

Since the first public alpha client builds appeared in February 2014, much of the promise was fulfilled: Tox clients exist for almost all popular platforms, including Android and iOS (don't forget about the protocol plug-ins for Pidgin and Miranda NG ) The majority of desktop clients support audio and video calls. The network of bootstrap nodes needed by customers to find each other grows by leaps and bounds: at the moment there are almost fifty of them, eleven of which are in Russia. The kernel also continues to grow rapidly, and one of the key developers, irungentoo, has recently successfully completed the collection of funds for the development of documentation on the core and protocol.
Not without problems: Last summer, Sean Qureshi was expelled from the project, who served as CFO of the Tox Foundation, an organization established as the official representative of the project. In July 2015, irungentoo announced on Reddit that Qureshi had appropriated about three thousand dollars from the Tox Foundation funds. Later it was stated that Qureshi "took a loan for personal purposes not connected with the project, on the security of the Tox Foundation and all the funds of the fund." According to irungentoo, most of the funds appropriated consisted of prize payments received by the project for participation in the Google Summer of Code; a small proportion were also user donations. In September 2015, Shawn himself stated that he had spent all the money to pay for the growing infrastructure of the project (server rental, channels, etc), and even promised to provide evidence in the form of checks — but even by December month he didn’t confirm his words. has provided.
Despite the fact that due to these events, Tox's reputation has suffered some damage (not to mention the fact that the project had to move to new servers again, change the domain, and even the form of organization), the development does not stop: in February this year, the Tox stand He worked at SCaLE (Southern California Linux Expo, one of the largest open-air exhibitions in the States), the project plans to take part in Google Summer of Code 2016, and the next year, if everything goes well, the project code audit is scheduled to begin.
The “information is power” principle that has been beaten for decades, has acquired a new, and by no means the most friendly, color in this decade. If earlier, users were afraid that they were being watched by Microsoft and Google in order to display more relevant and “personal” advertising, today the security agencies are not even trying to hide our fact that they are following us, justifying their absolutely unlimited authority by fighting terrorism, care for minors - all that is intended to make you feel guilty when you try to object. But we should not forget that the legislation of most countries guarantees citizens the right to privacy of correspondence - and when this right is infinitely consistently violated, there is nothing reprehensible in using things like Tox or Tor to preserve anonymity.
Currently, many countries are trying to change the legislation by tightening regulation on the use of anonymizers and end-to-end encryption tools - for example, in Russia, parliamentarians have repeatedly raised the issue of banning Tor or imposing criminal penalties for its use. In Belarus, as in China, the use of Tor and other anonymizers for circumventing locks is prohibited , and in Britain and the United States for refusing to provide a PGP key to decrypt a file or hard disk, it is quite possible to go to jail . That is why it is so important to disseminate as widely as possible information about simple and affordable means of protecting your own privacy. Even if your main secret is how many cats live with you.
- The Tor Project website
- I2P project website
- Site Tox Project
- Twister , a P2P microblogging project
- “I2P Bulletin” : all “for” and “against” distributed networks, detailed educational program, I2P use cases

However, we are living in Russia, and recently the situation continues to deteriorate - if in other countries a civilian request for greater openness of government agencies is able to stop statesmen in their endeavors (for example, you can take the same SIPA , which the guys from Fight For The Future ), then, alas, we are not so rosy. Of the latest “good” news on this front, another tightening of legislation in the field of data storage by telecom operators, held under the guise of “anti-terrorist amendments”; development of commercial tools for listening to calls in mobile networks - for example, the same InfoWatch Natalia Kaspersky. Do not forget about the recent loud hacking of accounts in the Telegram , carried out, apparently, with the direct assistance of the mobile operator.
')
In connection with all this, the demand for technical means to bypass site locks, preserve the privacy of correspondence and anonymize the web is extremely high - so let's see how things are going on for the main projects on this front, namely Tor, I2P and Tox.
The tor project
Tor, the “oldest” of all the projects that will be mentioned today, continues to bloom and smell. Being originally developed by the US Navy in conjunction with DARPA, from the end of zero to the present day, the project has evolved from a marginal project for a few technically knowledgeable users to the absolutely necessary tool today that ordinary people have finally begun to use. As of February 2016, there were more than seven thousand weekend nodes in the network, and the total number of participants in the network exceeded two million - and already in 2014, Russia ranked third in the world in the number of users.

A very large increase in the user base was achieved, among other things, thanks to the active development of the Tor Browser bundle, which is now the “flagship”, to some extent, product of the project - previously this was the package consisting of the Tor daemon and the Vidalia graphic panel but the user was offered to choose the browser himself. Being based on the Firefox ESR (Firefox edition of "extended support", the closest analogue is the Ubuntu LTS editions), due to the mass of custom patches aimed at minimizing user information leaks, and also due to the fact that must-have extensions like NoScript, AdBlock and HTTPS Everywhere, Tor Browser is currently the simplest and safest “single-click” solution for the end user.

Tor is currently available in one form or another on absolutely all platforms, including mobile. Also in 2014, several projects of hardware routers appeared on Kickstarter, the application case of which meant the transparent passage of all network traffic connected to them via Tor. Most of these projects were canceled - in particular, the administration of Kickstarter stopped collecting funds for the German project Anonabox due to the fact that the developers were not completely honest with the backers regarding the hardware and software of the project. At the same time, the amount collected by backups on Anonbox exceeded half a million dollars (with an initial goal of $ 7,500), which clearly shows how important anonymity is for users around the world.
I2P: Invisible Internet Project
If Tor is intended to access the familiar to all of us Internet, the main idea of I2P is to create an overlay network that uses the Internet purely as a transport network, completely distributed, and in no way dependent on it, in which all information is multi-level encrypted. Having started its development in 2003, the network came to the more or less familiar look of the network closer to the beginning of the tenth years of this century, just to the beginning of the end of the free Internet era.

Most of the “Habrakhabra” audience and related resources are certainly aware of the basic I2P functionality, and therefore we limit ourselves to news. The network continues to grow rapidly, and at the moment Russia is the second number in terms of the number of nodes (routers), and their total number is close to 70 thousand. Every day, 300-400 new routers come to the network, of which up to half remain active on average. About ten thousand nodes play the role of floodfills, i.e. they deal exclusively with passing someone’s traffic to neighboring nodes.

In the past couple of years, the project has been actively developing the mobile version of the router, which is currently available for Android end users, including on Google Play and F-Droid. Despite the fact that due to the network structure, mobile devices cannot be considered as a sufficiently secure environment, and the quality of communication is not sufficient to pass other people's traffic through the router, the current implementation is quite enough to access sites on the network. In addition, work is underway to improve the anonymity of I2P mobile users - the draft of the mobile router is in the state of active development.
In addition to working on the network itself, the I2P Project is also involved in educational activities: in December 2015, project representatives took part in the 32nd Chaos Communication Congress conference held in Hamburg (Germany).
Tox project
If Tor and I2P are aimed at a wide range of services that can work in them, and are general-purpose networks, then Tox was created exclusively as a protected messenger. The starting point was the release of information about NSA surveillance programs by Edward Snowden. After mentioning Microsoft's mass collaboration with state agencies, as well as details of listening operations on Skype, a thread appeared on one of the world's largest imageboard, 4chan, dedicated to the creation of a secure messenger that would be completely “closed” from wiretapping, functionally not inferior to Skype, and was fairly simple to use for the average user. This was the beginning of the development of Tox.

Since the first public alpha client builds appeared in February 2014, much of the promise was fulfilled: Tox clients exist for almost all popular platforms, including Android and iOS (don't forget about the protocol plug-ins for Pidgin and Miranda NG ) The majority of desktop clients support audio and video calls. The network of bootstrap nodes needed by customers to find each other grows by leaps and bounds: at the moment there are almost fifty of them, eleven of which are in Russia. The kernel also continues to grow rapidly, and one of the key developers, irungentoo, has recently successfully completed the collection of funds for the development of documentation on the core and protocol.

Not without problems: Last summer, Sean Qureshi was expelled from the project, who served as CFO of the Tox Foundation, an organization established as the official representative of the project. In July 2015, irungentoo announced on Reddit that Qureshi had appropriated about three thousand dollars from the Tox Foundation funds. Later it was stated that Qureshi "took a loan for personal purposes not connected with the project, on the security of the Tox Foundation and all the funds of the fund." According to irungentoo, most of the funds appropriated consisted of prize payments received by the project for participation in the Google Summer of Code; a small proportion were also user donations. In September 2015, Shawn himself stated that he had spent all the money to pay for the growing infrastructure of the project (server rental, channels, etc), and even promised to provide evidence in the form of checks — but even by December month he didn’t confirm his words. has provided.
Despite the fact that due to these events, Tox's reputation has suffered some damage (not to mention the fact that the project had to move to new servers again, change the domain, and even the form of organization), the development does not stop: in February this year, the Tox stand He worked at SCaLE (Southern California Linux Expo, one of the largest open-air exhibitions in the States), the project plans to take part in Google Summer of Code 2016, and the next year, if everything goes well, the project code audit is scheduled to begin.
Instead of conclusion
The “information is power” principle that has been beaten for decades, has acquired a new, and by no means the most friendly, color in this decade. If earlier, users were afraid that they were being watched by Microsoft and Google in order to display more relevant and “personal” advertising, today the security agencies are not even trying to hide our fact that they are following us, justifying their absolutely unlimited authority by fighting terrorism, care for minors - all that is intended to make you feel guilty when you try to object. But we should not forget that the legislation of most countries guarantees citizens the right to privacy of correspondence - and when this right is infinitely consistently violated, there is nothing reprehensible in using things like Tox or Tor to preserve anonymity.
Currently, many countries are trying to change the legislation by tightening regulation on the use of anonymizers and end-to-end encryption tools - for example, in Russia, parliamentarians have repeatedly raised the issue of banning Tor or imposing criminal penalties for its use. In Belarus, as in China, the use of Tor and other anonymizers for circumventing locks is prohibited , and in Britain and the United States for refusing to provide a PGP key to decrypt a file or hard disk, it is quite possible to go to jail . That is why it is so important to disseminate as widely as possible information about simple and affordable means of protecting your own privacy. Even if your main secret is how many cats live with you.
Useful links, or "what else can I read?"
- The Tor Project website
- I2P project website
- Site Tox Project
- Twister , a P2P microblogging project
- “I2P Bulletin” : all “for” and “against” distributed networks, detailed educational program, I2P use cases
Source: https://habr.com/ru/post/357078/
All Articles