Russian hacker has published data to access the source codes of services Yota
 The Russian hacker, hiding under the nickname w0rm , has posted on his Twitter link to the company's internal JIRA (or rather, to the FishEye code change tracker) and data to access it.
The Russian hacker, hiding under the nickname w0rm , has posted on his Twitter link to the company's internal JIRA (or rather, to the FishEye code change tracker) and data to access it.Tweet screenshot (slightly edited, obscene language):
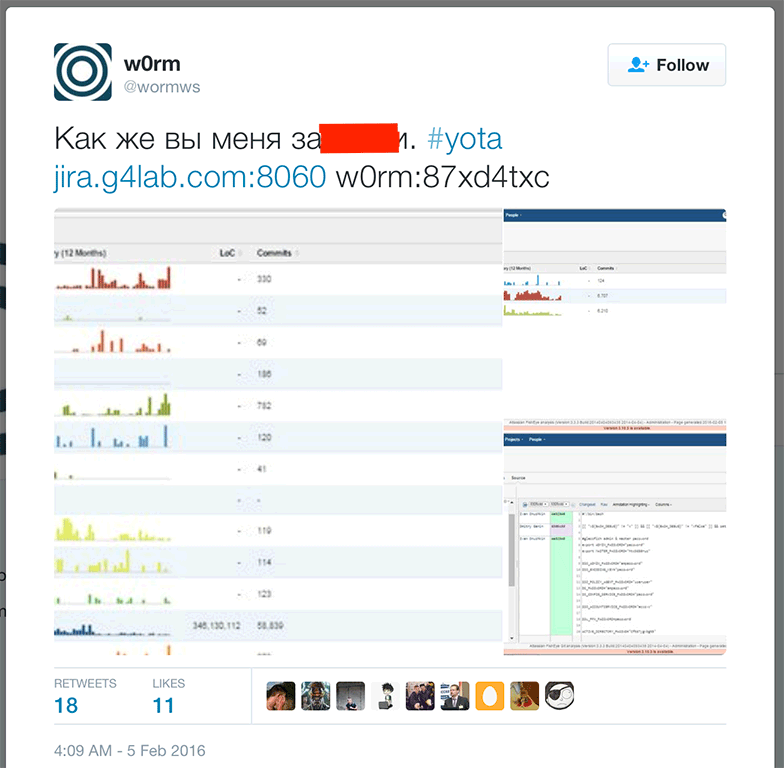
In addition, the screenshots attached to the tweet show that the source codes contain other accounts and passwords, from which services it has not yet been specifically identified.
According to the publisher TJournal , w0rm stated that "the administrator [Jira] just forgot to turn off the registration."
The data were publicly available for at least 2 hours; at the time of posting the record, the server with JIRA is not available. There are no source codes yet, but in the near future they will probably appear either in the public domain or in the black markets.
')
The official response of the company's PR director, Lina Udovenko:
Yota pays great attention to the safety and security of data. Judging from the published information, the w0rm account gained access to the test environment of auxiliary systems of the modem product. This system is in no way connected with billing, or with the personal data of Yota customers, or with any other data affecting the security and performance of the systems. And the user, despite his statements, did not make any changes to the code.
The changes made were made by the actual developer, while the w0rm account simply set the developer's name for himself to make a screen and give what he wanted to be true. At the moment, external access to the test environment is already closed. This forgery of information does not affect the business and safety of clients.
This is not the first time that hacker w0rm hacked services. In December 2015, they received administrative access to the AvtoVAZ website, and in August - to official data of MegaFon.
Source: https://habr.com/ru/post/356996/
All Articles