General Motors launched its own Bug Bounty program, but without rewards
Another shot in the leg
 Concern General Motors has launched its own program to search for bugs and vulnerabilities for "reward", reports securityledger.com . The highlight of the new BB is that the concern will not pay for the found vulnerabilities.
Concern General Motors has launched its own program to search for bugs and vulnerabilities for "reward", reports securityledger.com . The highlight of the new BB is that the concern will not pay for the found vulnerabilities.The program is designed for “White hat” hackers and information security specialists, with whom GM will provide access to its software. Bug Bounty was launched in order to increase the interest of White hat hackers and other experts to work on the company's internal software. The actual “reward” for participation will be the absence of lawsuits to specialists who have found vulnerabilities.
This “attraction of unprecedented generosity” was launched on January 5, 2016 on the Hackerone website with promises of “eternal glory” for specialists who will take part in it and transmit data about the security vulnerabilities of General Motors software. About cash rewards, as is usually the case when launching BB programs, is not mentioned on the site. But it is proposed to be the first to "cover itself with eternal glory." General Motors is not the first "old capitalist giant" who comes to the IT community with similar proposals.
')
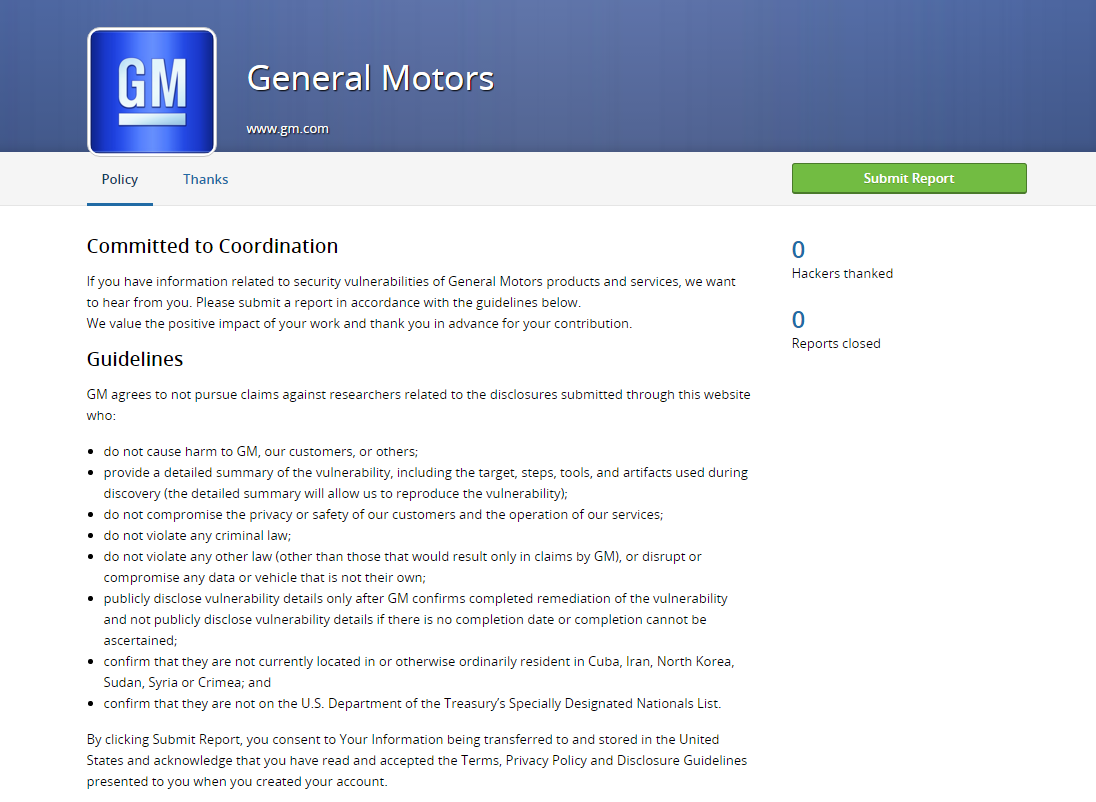
Meanwhile, in order not to receive a multimillion claim from the auto concern, a security specialist or a hacker will need to fulfill, for example, the following requirements:
- Do not harm GM or their customers;
- Provide a detailed report on their work on their software;
- Do not endanger the life or safety of customers of the company or its services;
- Do not violate the laws;
- Required to provide details of the location of the vulnerability for its elimination by GM;
- Specialists from Cuba, Iran, North Korea, Sudan, Syria and the Crimea are prohibited from participating in the program.
Full description of GM BB-program in the screenshot below:
For a week, no one was willing to participate.
Considering GM's market capitalization of $ 47 billion, the lack of information on remuneration looks at least strange. Bounty Bug-programs have become a serious source of income for talented hackers and information security specialists and allow them to earn hundreds of thousands of dollars a year, at the same time improving the quality of software produced by large companies and software giants. Companies such as Yahoo, PayPal, Twitter, Facebook, Microsoft and others actively use the services of "freelance" security personnel.
Source: https://habr.com/ru/post/356986/
All Articles