Time attack on HSTS Sniffly shows which sites the user went to
 Modern browsers support HTTP Strict Transport Security (HSTS). The HSTS flag indicates that it is necessary to request an encrypted HTTPS version from a specific domain — even if the transition is carried out via HTTP, and not HTTPS. The mechanism is needed to provide an additional level of security: the browser could request an HTTP version of a page that is easy to listen to or replace. This way you can avoid some attacks by lowering the level of protection and intercepting cookies.
Modern browsers support HTTP Strict Transport Security (HSTS). The HSTS flag indicates that it is necessary to request an encrypted HTTPS version from a specific domain — even if the transition is carried out via HTTP, and not HTTPS. The mechanism is needed to provide an additional level of security: the browser could request an HTTP version of a page that is easy to listen to or replace. This way you can avoid some attacks by lowering the level of protection and intercepting cookies.The data that a particular domain had the HSTS flag set are stored in the user's browser. This is a boolean variable (true / false). These are not cookies, but security information, which is why browsers treat it differently. About cookie tracking is well known. The user can enter the browser settings and delete those cookies that he does not like. There are separate add-ons that prohibit the acceptance of cookies from the domains of marketing companies. Clearing the HSTS settings is not so transparent - in browsers you can only remove all flags for all sites at once. In January, Sam Greenhal demonstrated that using HSTS you can create superkuki that are not so easy to remove.
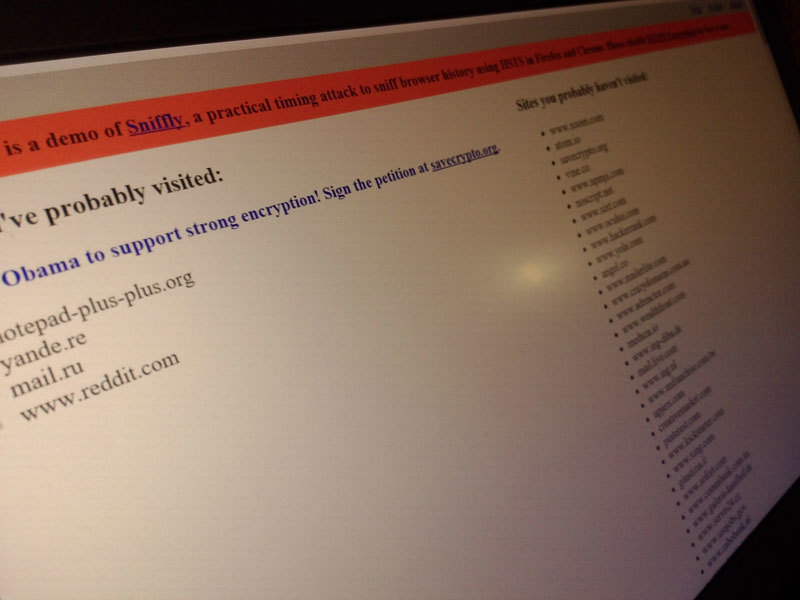
Last month, Yan Zhu showed up at Sniffly's ToorCon conference in San Diego. The project uses HSTS and Content Security Policy to determine which sites from the list the user has already visited.
Sniffly looks like a regular web page . After switching to it, Sniffly will check a number of sites and show which resources the user probably was on, and which resources they probably did not. In some cases, Sniffly produces data with large errors. Before visiting it is recommended to disable HTTPS Everywhere, if this add-on is installed. Sniffly works only in the main browsers, and does not show the correct results in Chrome for iOS, Internet Explorer and Safari.
')
How it works?
The principle of operation of Sniffly is simple and briefly described in the presentation for ToorCon. If the owner of sneaky.com knows that example.com uses HSTS, then he can embed any element of example.com into his sneaky.com page. Then, each time you visit sneaky.com, the user will request this item, which means a request to example.com.
If the user has already visited example.com, then his browser already stores HSTS data, so an internal redirect to the HTTPS version of the example.com page will occur. This redirect happens almost instantly. If the user has never been to example.com, then a full-fledged network request will be made with an HTTP 301 or 302 code — that is, a redirect to the HTTPS version. This query will take much longer. Measurement of time will allow to make a timing attack and establish the fact of visiting a particular resource with HSTS.
But you need to measure time. For this, the abuse of Content Security Policy is used. It's funny that, like HSTS, it is also a security tool. The standard is designed to prevent content downloads, which is designed to get rid of XSS attacks. All sneaky.com needs in order to conduct its attack is the prohibition of downloading pictures via HTTPS. When you try to upload a picture via HTTPS, an error occurs that is registered by the JavaScript code. If the user was on example.com and has the HSTS flag, the error arrives within a millisecond order. If a complete request is made, then the error comes in a hundred milliseconds or more.
Sniffly applies the principles outlined above to several hundred HSTS resources that were selected from the first million Alexa.com rankings. Sniffly may work worse with newer browsers, with HTTPS Everywhere add-ons or in the Tor browser. The author claims that, in principle, you can try to track with the help of timing not only the fact of visiting the resource, but also the presence of the file in the cache.
Easy to find application for this tool. These are not only different systems for exploring the tastes of a user with the goal of selling him relevant advertising. It also leaks important personal information. You can set the range of interests of the user, his views and preferences.
You can resist the attack. Modern browsers have a built-in list of domains that can only be accessed via HTTPS. It is enough to get the domain name of the resource to the HSTS Preload list of popular browsers, and it will be impossible to establish the fact of its visit.
Sniffly
GitHub page
Source: https://habr.com/ru/post/356912/
All Articles