Go into Flash: Top 10 vulnerabilities exploited by attackers

The company Recorded Future analyzed more than 100 exploit kits (exploit kits, EC), examining the vulnerabilities that these EKs target. As it turned out, Adobe Flash Player is a software product that is most often cracked. There are quite a few vulnerabilities in Flash, and attackers quite often use these vulnerabilities for their own purposes.
From January 1, 2015 to September 30, 2015, the Adobe Flash Player contains 8 of the 10 most known vulnerabilities exploited by hackers. The remaining vulnerabilities are Microsoft Internet Explorer 10 and 11 (CVE-2015-2419) plus other Microsoft products, including Silverlight (CVE-2015-1671).
Exploit kits are an exploit package immediately for several programs (versions) and / or for various vulnerabilities in them. In the latest versions of bundles, an exploit is selected specifically for a specific user program. In most cases, exploit kits are used during client-side attacks, when malicious code gets to the victim through a browser, and then it is executed. The main bundle of exploits in bundles is aimed specifically at vulnerabilities in browsers, Java, Flash, and PDF.
')
Often the sets are used as a service when a client provides software that needs to be downloaded to the victim’s PC or server, and the owner of the “service” tries to install this software on the maximum number of machines. In this case, the client pays for each successful installation.
On the computers of users of the software gets in different ways, including compromised web pages. Understanding what vulnerabilities are exploited by cybercriminals helps to better protect against hacking.
Angler Exploit Kit
Angler is one of the most popular and well-known exploits of whales, it was used to carry out the most successful campaigns for distributing cryptographers. It first appeared in 2013, and quickly became popular due to its ability to go unnoticed by the overwhelming number of anti-virus products. Angler helps distribute software such as Cryptowall, AlphaCrypt, Necurs, and Bedep.

In October, Cisco discovered a large number of proxy servers related to Angler. The network, which was discovered by Cisco, was responsible for 50% of the activity of the exploit of the whale. The infrastructure infected about 90 thousand systems per day, and brought about $ 30 million per year to its creators.
Methodology
The company Recorded Future has analyzed thousands of sources throughout the Web, including .onion websites, crackers forums and social media. In addition to Angler, the work of such popular exploit services as Neutrino, Nuclear Pack was also studied.
The company did not perform reverse engineering of the software mentioned; instead, information available from blogs on information security, posts on blogs, and so on was studied.
results
Using these methods, the company was able to identify the most popular vulnerabilities among attackers. As mentioned above, the majority refers to the Adobe Flash Player.
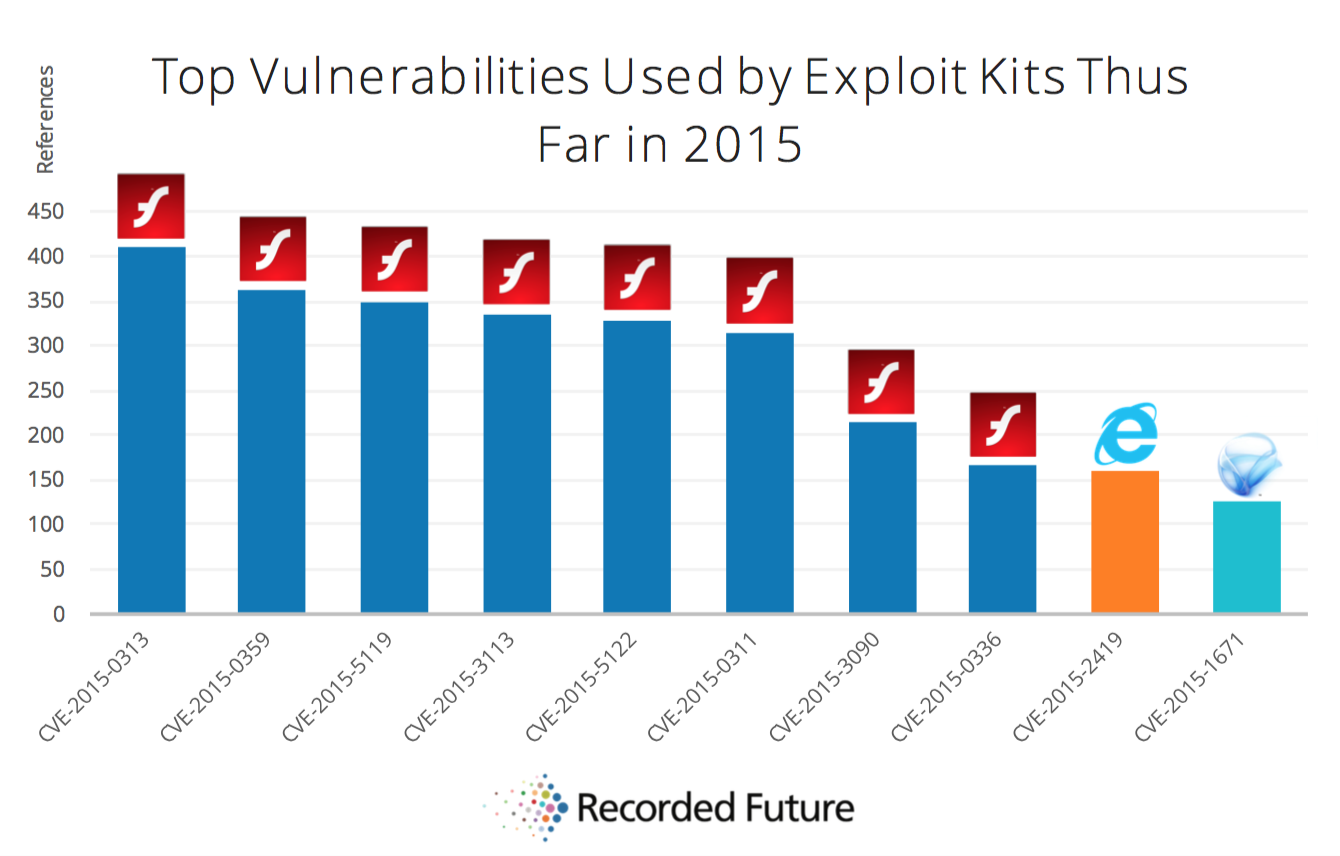
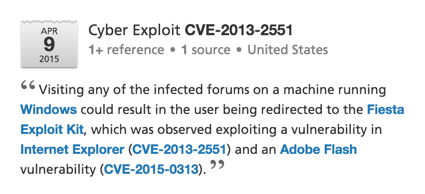
The most common vulnerability CVE 2015-0313 - uses Flash Player 16.0.0.296, it is identified by Adobe as critical, and was fixed in February 2015. This vulnerability is contained in the database Hanjuan, Angler and Fiesta EKs.
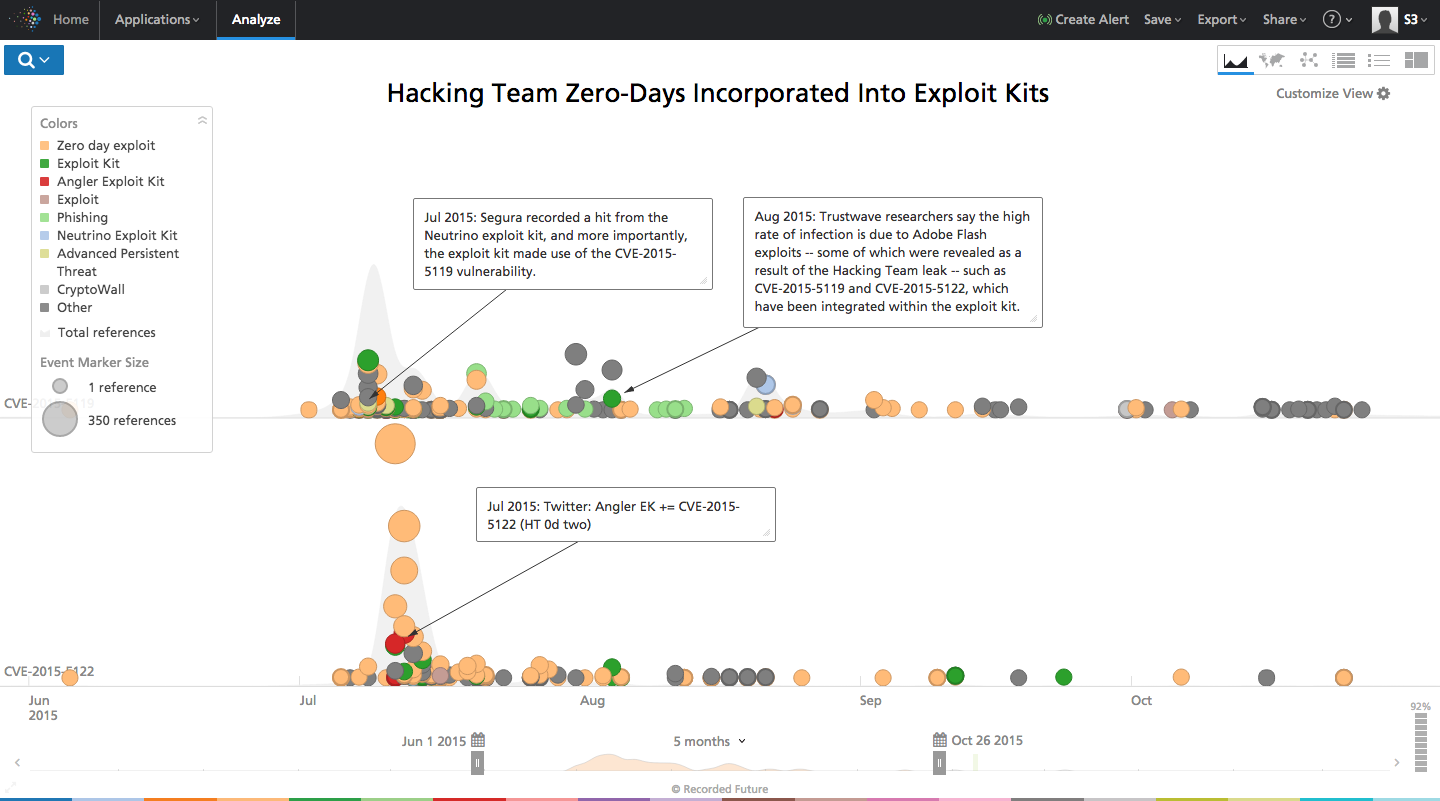
Several other vulnerabilities (CVE-2015-5119, CVE-2015-5122) were immediately added by the EK authors immediately after these problems became known "due to" the leakage of July 2015 Hacking Team .
Effects
Since the Adobe Flash Player package is multiplatform, plus there are a lot of vulnerabilities in it, it is very popular among hackers. In fact, there are so many “holes” in Adobe Flash Player that this product can hardly be called a safe operating environment.
Flash versions older than 19.0.0.226 cannot be run on Apple OS X.
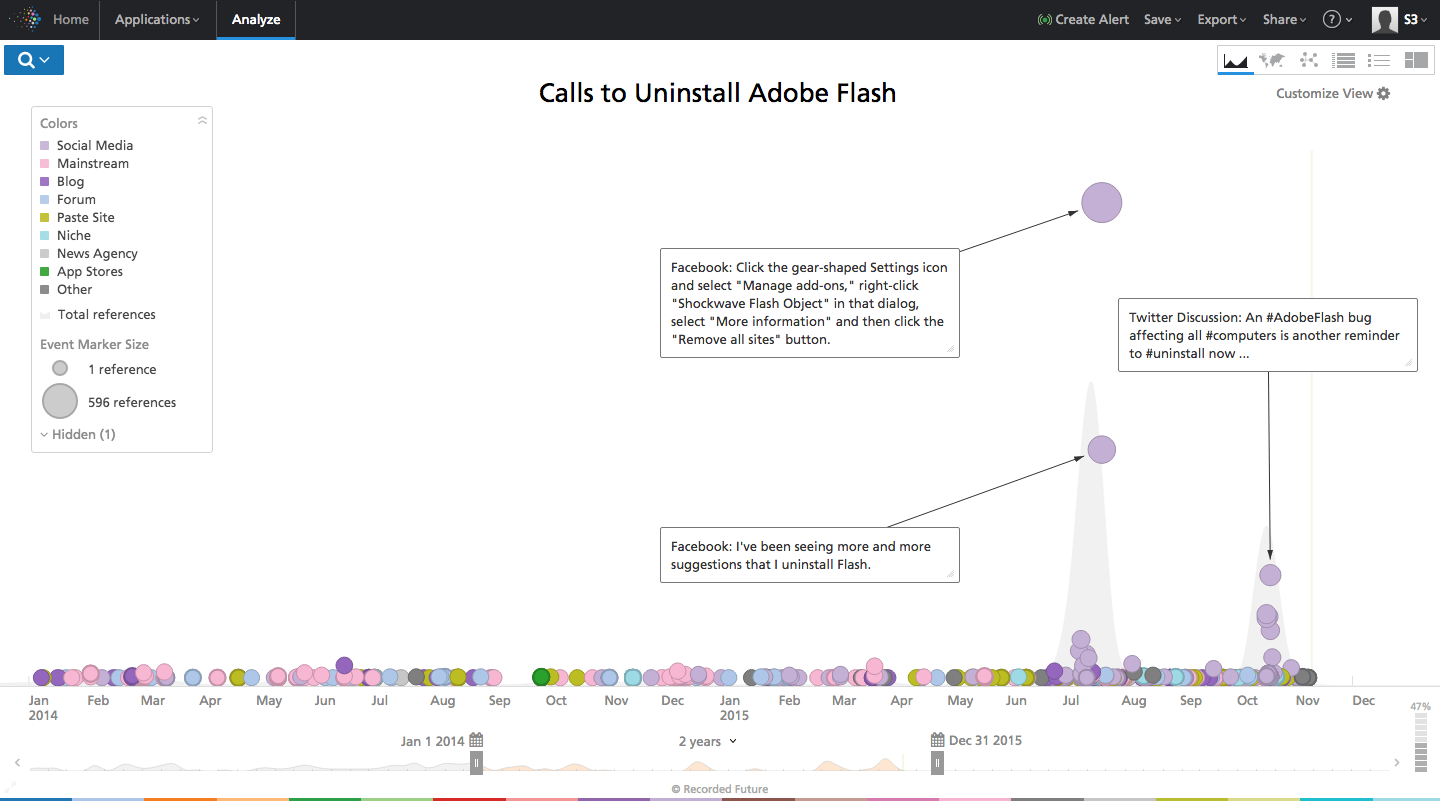
It is clear that each organization and user must decide whether to use Flash in their work or not. But one thing is for sure - if the package is already in use, it needs to be updated on time. Plus, you should use “Click to Play” , which helps to test the work of Flash in an unfamiliar environment.
Source: https://habr.com/ru/post/356908/
All Articles