New algorithm for checking the reliability of passwords
Many sites try to help users set more complex passwords. To do this, establish basic rules that usually require you to specify at least one uppercase letter, one lowercase letter, one number, and so on. The rules are usually primitive like these :
Unfortunately, such simple rules mean that the
Some experts say that this is not the best option.
In reality,
')
Here are the first two passwords.

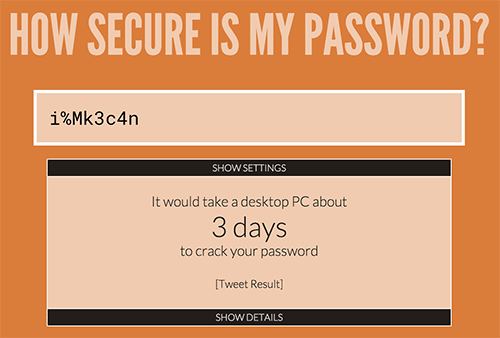
But two passwords that do not pass the test for reliability.
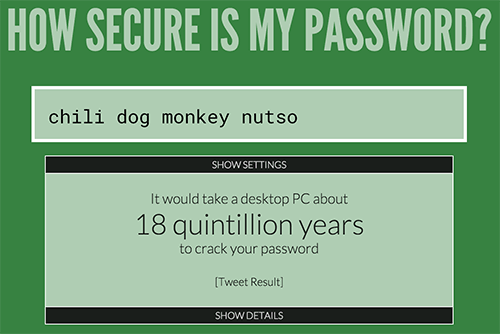
What to do? Maybe you should not force the use of special characters and introduce new rules, such as a ban on repeating several characters in a row, using not one, but two or three special characters and numbers, increasing the minimum password length, and so forth.
Instead, it’s enough to do a simple thing - just set a limit on the minimum password entropy , and that’s all! You can use a ready-made evaluator zxcvbn for this.
There are other solutions besides zxcvbn. Just last week, the ACM Computer and Communications Security security conference featured a scientific paper ( pdf ) of security specialists from the research division of Symantec Research and the French research institute Eurecom. They have developed a new program to verify the reliability of passwords, which estimates the approximate number of brute-force attempts required using the Monte-Carlo method . The proposed method differs in that it requires a minimum amount of computing resources on the server, is suitable for a large number of probabilistic models and at the same time is quite accurate. The method was tested on passwords from the base of 10 million Xato passwords that are in the public domain ( copy on Archive.org ) - it showed a good result. True, this study by Symantec Research and Eurecom is more of a theoretical nature, at least they have not laid out their program in open access in any acceptable form. Nevertheless, the meaning of the work is clear: instead of heuristic rules for checking passwords, it is desirable for websites to implement a test for entropy.
'password' => [ 'required', 'confirmed', 'min:8', 'regex:/^(?=\S*[az])(?=\S*[AZ])(?=\S*[\d])\S*$/', ]; Unfortunately, such simple rules mean that the
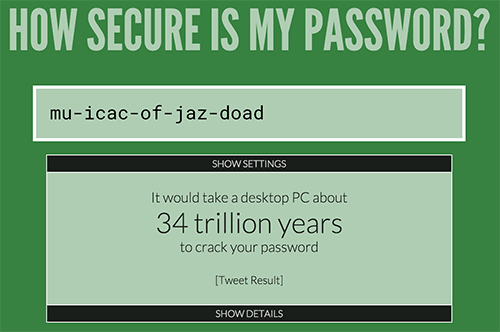
Abcd1234 password will be recognized as good and of high quality, just like Password1 . On the other hand, the password mu-icac-of-jaz-doad will not pass validation.Some experts say that this is not the best option.
In reality,
Abcd1234 and Password1 are bad passwords, and mu-icac-of-jaz-doad is a good password. This is easy to verify .')
Here are the first two passwords.


But two passwords that do not pass the test for reliability.


What to do? Maybe you should not force the use of special characters and introduce new rules, such as a ban on repeating several characters in a row, using not one, but two or three special characters and numbers, increasing the minimum password length, and so forth.
Instead, it’s enough to do a simple thing - just set a limit on the minimum password entropy , and that’s all! You can use a ready-made evaluator zxcvbn for this.
There are other solutions besides zxcvbn. Just last week, the ACM Computer and Communications Security security conference featured a scientific paper ( pdf ) of security specialists from the research division of Symantec Research and the French research institute Eurecom. They have developed a new program to verify the reliability of passwords, which estimates the approximate number of brute-force attempts required using the Monte-Carlo method . The proposed method differs in that it requires a minimum amount of computing resources on the server, is suitable for a large number of probabilistic models and at the same time is quite accurate. The method was tested on passwords from the base of 10 million Xato passwords that are in the public domain ( copy on Archive.org ) - it showed a good result. True, this study by Symantec Research and Eurecom is more of a theoretical nature, at least they have not laid out their program in open access in any acceptable form. Nevertheless, the meaning of the work is clear: instead of heuristic rules for checking passwords, it is desirable for websites to implement a test for entropy.
Source: https://habr.com/ru/post/356892/
All Articles