Android 5 can be unlocked using an arbitrary password of enormous length
The researcher found in the fifth version of the Android operating system a vulnerability that allows you to cause a system crash and unlock without entering the lock screen password. To do this, it only took to overload the password entry field with a large number of characters. The video above is 8 minutes 46 seconds long. This means that a person familiar with the sequence of actions can unlock the smartphone if you have physical access to it in about 10 minutes or less. Next, the attacker can perform any action, the rights to which were the owner of the smartphone.
The video above goes without comment what is happening. The content can be roughly divided into the following steps:
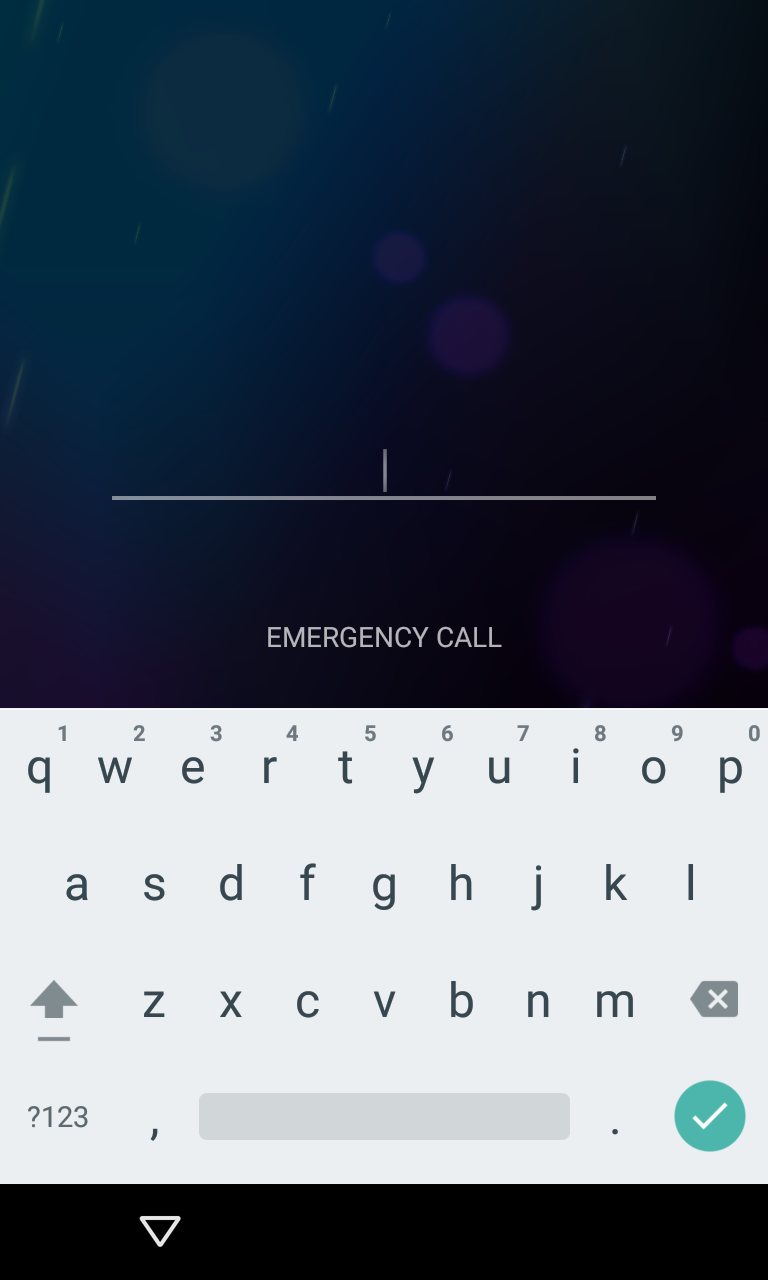 The emergency call screen opens on the lock screen.
The emergency call screen opens on the lock screen. Then any character is typed. In his example, the researcher used 10 stars. Two tapas on typed allow you to select them. The typed is copied and pasted again, which doubles the number of characters in the input field. The process of selecting all text, copying and re-pasting is repeated as long as the field responds to the selection. Usually, after 11 doublings, the field cannot be distinguished.
Then any character is typed. In his example, the researcher used 10 stars. Two tapas on typed allow you to select them. The typed is copied and pasted again, which doubles the number of characters in the input field. The process of selecting all text, copying and re-pasting is repeated as long as the field responds to the selection. Usually, after 11 doublings, the field cannot be distinguished.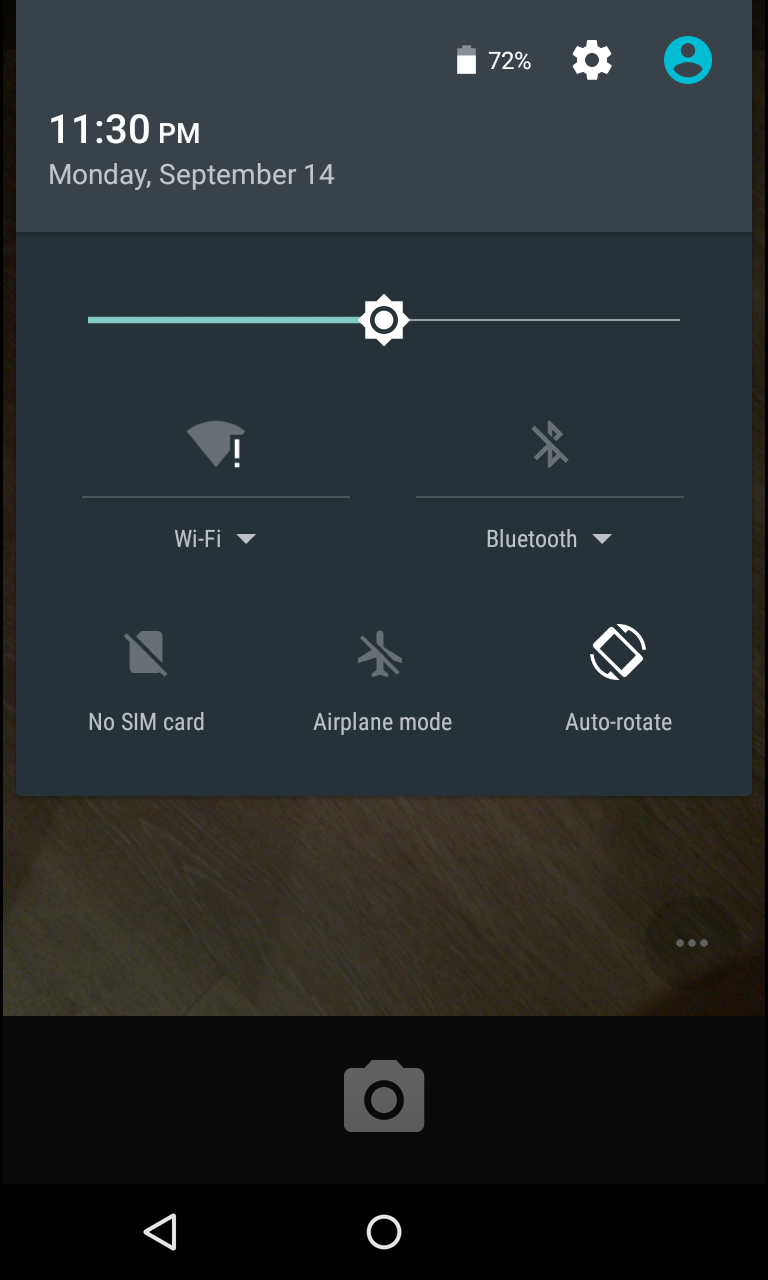 Then you need to return to the lock screen and open the camera. Top gets the notification zone. Attempting to open the settings leads to the suggestion to enter a password.
Then you need to return to the lock screen and open the camera. Top gets the notification zone. Attempting to open the settings leads to the suggestion to enter a password. A long tap in the password field will help insert the previously typed sequence into it. Then you need to continue this process: you need to insert characters as much as possible. The researcher recommends keeping the cursor at the end of the input field, since the insertion process can be complicated as the number of characters increases. At a certain moment, the GUI will “fall”, and the on-screen navigation buttons at the bottom will disappear, causing the camera to switch to full-screen mode.
A long tap in the password field will help insert the previously typed sequence into it. Then you need to continue this process: you need to insert characters as much as possible. The researcher recommends keeping the cursor at the end of the input field, since the insertion process can be complicated as the number of characters increases. At a certain moment, the GUI will “fall”, and the on-screen navigation buttons at the bottom will disappear, causing the camera to switch to full-screen mode.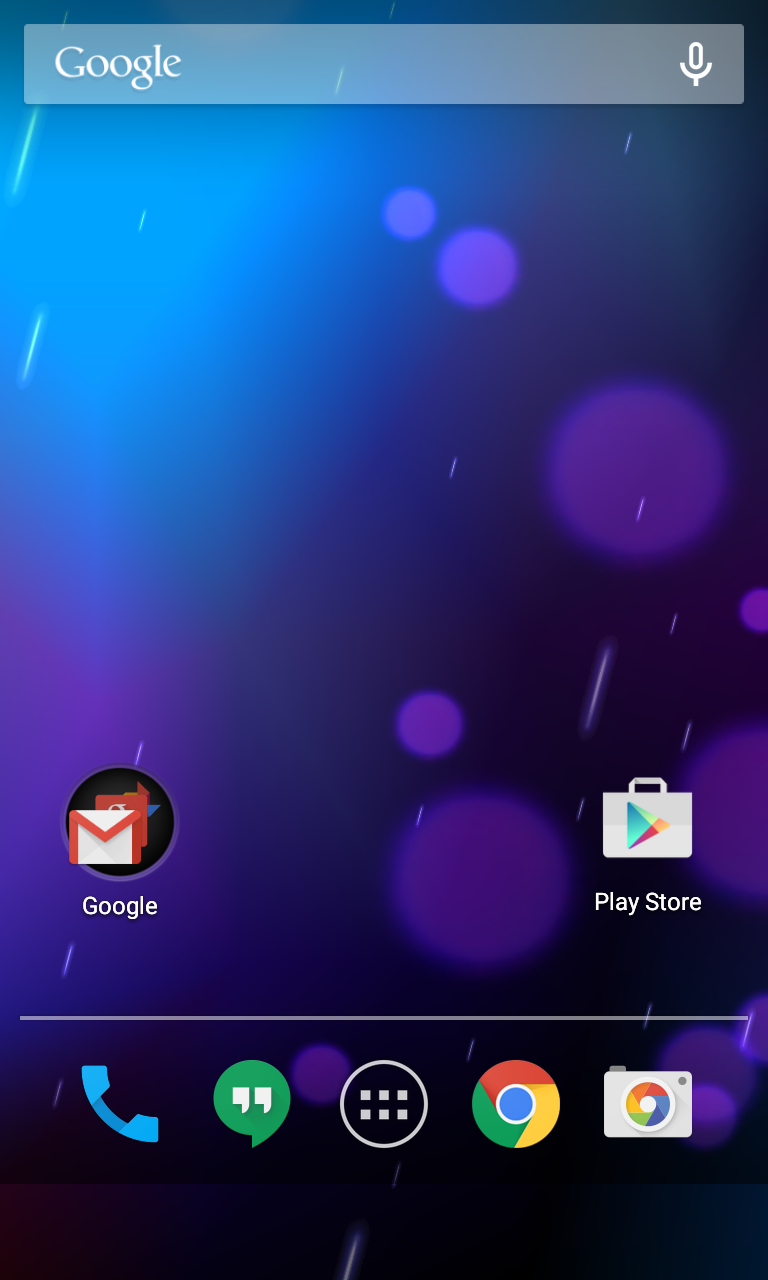 Then you need to wait until the camera app “crashes” and exposes the Android home screen. The time it takes to wait can vary considerably, but sooner or later the “fall” will happen. It will be possible to see that the camera lags slightly, trying to focus on new objects. Shooting with the buttons on the device can speed up the process, although it is optional. If the screen turns off due to inactivity, simply turn it on again and continue to wait. Sometimes the camera application falls on a full-fledged home screen, this happened in the video before kata. In another video, a researcher showed that a crash could occur on a partially rendered home screen.
Then you need to wait until the camera app “crashes” and exposes the Android home screen. The time it takes to wait can vary considerably, but sooner or later the “fall” will happen. It will be possible to see that the camera lags slightly, trying to focus on new objects. Shooting with the buttons on the device can speed up the process, although it is optional. If the screen turns off due to inactivity, simply turn it on again and continue to wait. Sometimes the camera application falls on a full-fledged home screen, this happened in the video before kata. In another video, a researcher showed that a crash could occur on a partially rendered home screen.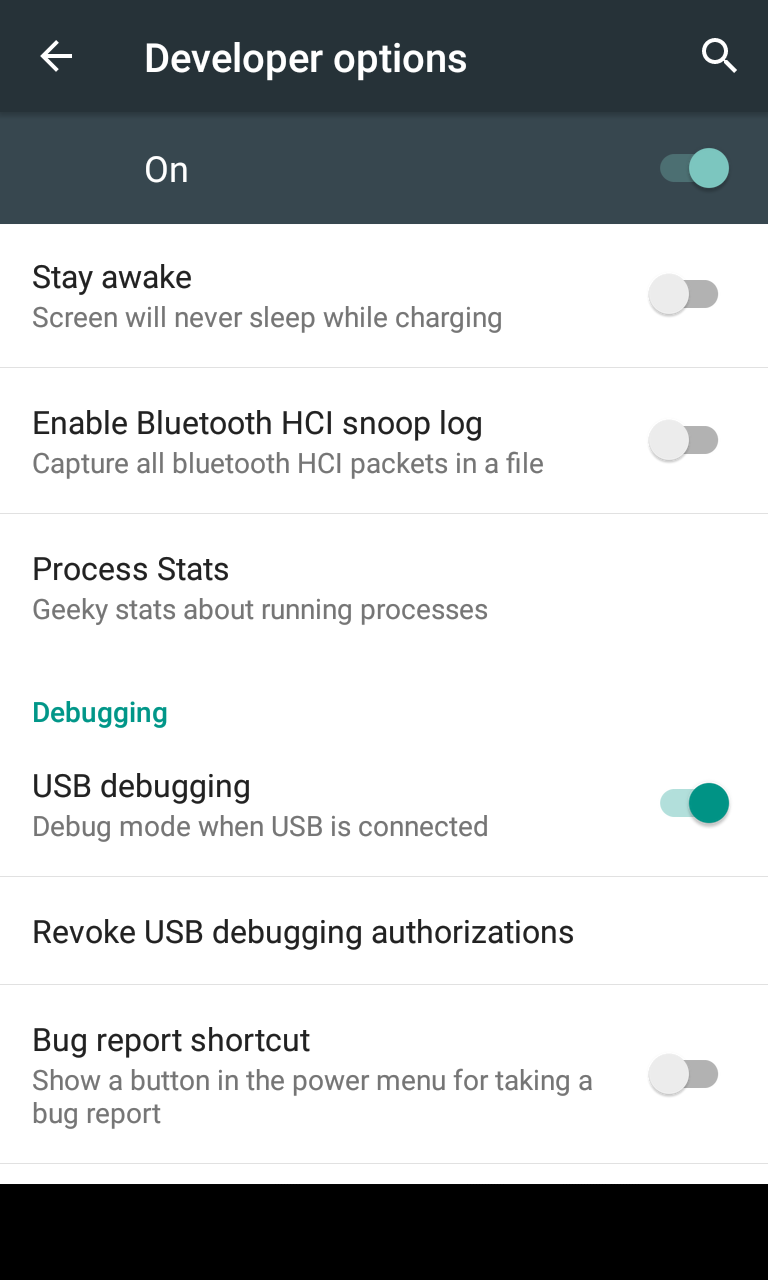 The process of bypassing the lock screen is complete. The researcher offers in any available way to get into the settings and enable USB debugging. To do this, you need to tap the build number 7 times to enter developer mode, click "Back", and enable USB debugging. Access to the device will be available via Android Debug Bridge. So you can send any commands, read and modify files with the level of access the owner of the smartphone.
The process of bypassing the lock screen is complete. The researcher offers in any available way to get into the settings and enable USB debugging. To do this, you need to tap the build number 7 times to enter developer mode, click "Back", and enable USB debugging. Access to the device will be available via Android Debug Bridge. So you can send any commands, read and modify files with the level of access the owner of the smartphone."Hole" was discovered a few months ago. On June 25th, she received information about her development team at Google. Already on July 1, the problem was assigned a low level of importance; in two weeks it was raised to medium. On September 9, Android 5.1.1 version LMY48M was released, in which this vulnerability has already been fixed. And on the 14th the information was open to everyone.
')
Vulnerability is easy to use to gain access to a stolen smartphone. For many, the greatest value is not the phone or tablet itself, but the privacy of personal data on it.
Due to the peculiarities of the smartphone market with the Android operating system, some devices will receive an update with a delay of weeks, months and even years. And the no longer supported smartphones and devices from unreliable manufacturers will never get a “patch”. Any Android 5 smartphones under version 5.1.1 of the LMY48M with stock applications are vulnerable, and only they . That is, 4.4 KitKat and earlier versions do not have this “hole”. This is a very good fact, because otherwise the number of affected devices would be much higher.
In the meantime, the manufacturer is preparing an update, you can try to change the way to enter the lock screen with a PIN code or enter with a pattern key. The latter are also vulnerable .
Source: https://habr.com/ru/post/356860/
All Articles