Hacker groups crack satellite channels to cover their tracks
Poorly protected satellite communication channels are used by Russian-speaking hacker groups to disguise command servers during targeted attacks on the most valuable victims, according to an investigation by Kaspersky Lab. We are talking about the most advanced hacker groups that allegedly fulfill the orders of state special services.
Specialists found three different groups using satellite access channels to disguise their campaigns. “LK” considers the most interesting and unusual of them is the Turla group, which is also called Snake or Uroburos (after the name of its first-class rootkit). She has been involved in cyber espionage for over eight years.
“At first, we could not understand whether attackers were renting commercial satellite Internet channels or hacking Internet providers and conducting MitM attacks at the router level to intercept the flow,” LK specialists admit. “We analyzed these mechanisms and came to a striking conclusion: the method used by the Turla group is incredibly simple and straightforward. At the same time, it provides anonymity, very cheap implementation and management. ”
“The way to get the command server to the range of IP addresses of satellite Internet is interception of network traffic between the victim and the satellite operator and the introduction of their packages. To do this, it will be necessary to exploit the vulnerabilities of the satellite operator or another Internet provider on the route, ”experts explain.
')
These methods of hacking have already been encountered earlier and in November 2013 were described in the Renesys blog .
From the Renesys blog: “The BGP routes of various providers were hacked, with the result that some of their Internet traffic was misdirected through Belarusian and Icelandic Internet providers. We have BGP routing data at our disposal, which show the development of 21 events in Belarus in February and May 2013 and 17 events in Iceland in July-August 2013 in seconds. ”
In a later post on Dyn's 2015 blog, researchers note: “For security professionals analyzing alert logs, it is important to understand that IP addresses identified as sources of incidents can be changed and replaced regularly. For example, an attack allegedly being carried out from the Comcast IP address in New Jersey may actually be a burglar from Eastern Europe who briefly captured the Comcast IP address space. It is interesting to note that in all six cases examined, attacks were conducted from Europe or Russia. ”
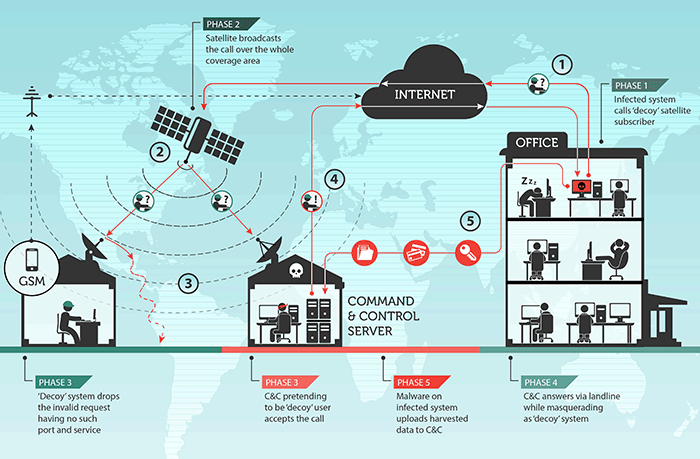
Here's how the attack happens: “Plates of legitimate users and intruders are aimed at a specific satellite transmitting traffic. Attackers use the fact that the packets are not encrypted. After determining the IP address to which traffic is routed through the downlink satellite channel, attackers begin to listen to the network, waiting for packets transmitted via the Internet to this IP address. When such a packet is detected (for example, TCP / IP SYN), they identify the source and send it a spoofed response packet (for example, SYN ACK) via the normal Internet line. At the same time, the legitimate user of the channel simply ignores this packet, since it arrives at the closed port (for example, 80 or 10080). Here an important note should be made: usually when a packet arrives at a closed port, the source is answered with an RST or FIN packet, making it clear that the packet is not expected. However, for slow links, it is recommended to use firewalls that simply drop packets destined for closed ports. This creates an opportunity for malicious use. ”
Initial investment in the implementation of this method of attack is less than a thousand dollars, Kaspersky Lab estimates, and the cost of ongoing maintenance is less than a thousand dollars a year.
Turla is not the only APT group using satellite Internet channels. On the IP addresses of satellite Internet, the command servers of the HackingTeam and Xumuxu groupings, and more recently the APT grouping of Rocket Kitten, were noticed.
Specialists found three different groups using satellite access channels to disguise their campaigns. “LK” considers the most interesting and unusual of them is the Turla group, which is also called Snake or Uroburos (after the name of its first-class rootkit). She has been involved in cyber espionage for over eight years.
“At first, we could not understand whether attackers were renting commercial satellite Internet channels or hacking Internet providers and conducting MitM attacks at the router level to intercept the flow,” LK specialists admit. “We analyzed these mechanisms and came to a striking conclusion: the method used by the Turla group is incredibly simple and straightforward. At the same time, it provides anonymity, very cheap implementation and management. ”
“The way to get the command server to the range of IP addresses of satellite Internet is interception of network traffic between the victim and the satellite operator and the introduction of their packages. To do this, it will be necessary to exploit the vulnerabilities of the satellite operator or another Internet provider on the route, ”experts explain.
')
These methods of hacking have already been encountered earlier and in November 2013 were described in the Renesys blog .
From the Renesys blog: “The BGP routes of various providers were hacked, with the result that some of their Internet traffic was misdirected through Belarusian and Icelandic Internet providers. We have BGP routing data at our disposal, which show the development of 21 events in Belarus in February and May 2013 and 17 events in Iceland in July-August 2013 in seconds. ”
In a later post on Dyn's 2015 blog, researchers note: “For security professionals analyzing alert logs, it is important to understand that IP addresses identified as sources of incidents can be changed and replaced regularly. For example, an attack allegedly being carried out from the Comcast IP address in New Jersey may actually be a burglar from Eastern Europe who briefly captured the Comcast IP address space. It is interesting to note that in all six cases examined, attacks were conducted from Europe or Russia. ”

Here's how the attack happens: “Plates of legitimate users and intruders are aimed at a specific satellite transmitting traffic. Attackers use the fact that the packets are not encrypted. After determining the IP address to which traffic is routed through the downlink satellite channel, attackers begin to listen to the network, waiting for packets transmitted via the Internet to this IP address. When such a packet is detected (for example, TCP / IP SYN), they identify the source and send it a spoofed response packet (for example, SYN ACK) via the normal Internet line. At the same time, the legitimate user of the channel simply ignores this packet, since it arrives at the closed port (for example, 80 or 10080). Here an important note should be made: usually when a packet arrives at a closed port, the source is answered with an RST or FIN packet, making it clear that the packet is not expected. However, for slow links, it is recommended to use firewalls that simply drop packets destined for closed ports. This creates an opportunity for malicious use. ”
Initial investment in the implementation of this method of attack is less than a thousand dollars, Kaspersky Lab estimates, and the cost of ongoing maintenance is less than a thousand dollars a year.
Turla is not the only APT group using satellite Internet channels. On the IP addresses of satellite Internet, the command servers of the HackingTeam and Xumuxu groupings, and more recently the APT grouping of Rocket Kitten, were noticed.
Source: https://habr.com/ru/post/356854/
All Articles