MIA contractor refuses to crack Tor
 The Central Scientific Research Institute for Economics, Informatics and Control Systems (TSNII EISU) is going to unilaterally terminate 4 state contracts with the establishment of “Special equipment and communication” (NPi STiS) of the Ministry of Internal Affairs, the Kommersant newspaper reports .
The Central Scientific Research Institute for Economics, Informatics and Control Systems (TSNII EISU) is going to unilaterally terminate 4 state contracts with the establishment of “Special equipment and communication” (NPi STiS) of the Ministry of Internal Affairs, the Kommersant newspaper reports .Data on contracts are closed, but according to the documentation, in 2013, the Central Research Institute EISU agreed with STiS on the implementation of works with the names “Uglyarka (Fleet)” and “Sakhalin-13 (Fleksura)”, and in 2014 - “Chameleon-2 (Fleet) "And" TOR (Fleet) ". The last job is the study of the de-anonymization of Tor users, which received the attention of the media and technical experts in the summer of 2014.
In the information on public procurement for the implementation of this work, initially there was the following title: “Performing R & D“ Investigating the possibility of obtaining technical information about users (user equipment) of the anonymous TOR network ”, code“ TOR (Fleet) ”. After receiving publicity in the media, the description was reduced to "Implementation of research work, code" TOR (Fleet) ". The original version can still be found in the screenshot in the post on "Habrahabr" . The maximum cost of work was estimated at 3.9 million rubles. The description of the Chameleon-2 tender with a maximum cost of 20 million rubles stated that it was “the creation of a hardware-software complex for conducting secret and hidden remote access to operatively significant information on the target electronic computer”. In this case, the description was also edited later.
At the moment, the Central Research Institute EISU has not yet abandoned the work, as reported by the newspaper Kommersant, citing a representative of the United Instrument-Making Corporation. The Central Research Institute at the end of May held a tender for the provision of legal services for termination. As a result, the law office of Pleshakov, Ushkalov and Partners was awarded a contract for 10 million rubles. Lawyers will help in the "preparation of a legal position on the procedure for termination" of four government contracts and will represent the Central Research Institute in court on several lawsuits of the Ministry of Defense. Vladimir Pleshakov does not comment on the situation, he only indicated that it is not yet clear whether the contract will be terminated.
')
Tor is an anonymous cryptographic network based on onion routing. Packages in Tor are encrypted in several layers. When transferring data, each of the network nodes decrypts the “onion” layer in order to obtain data on where the portion of data should be transferred. Then the onion packet is transmitted to the next node. Some network nodes provide an opportunity to exit through their channel to the external Internet. Due to this, users can bypass regional restrictions and locks. The protocol of “meeting points” allows you to implement a hidden network of resources on .onion-domains. It is impossible to establish both the identity of visitors to such .onion sites, and the real IP address and server location.
Regardless of the goals that were pursued during the creation of Tor, the network is often used to anonymize traffic, bypass the blocking of real Internet resources and access to a dark web with forbidden information (some types of pornography, drug trading). In this regard, the possibility of hacking the network and de-anonymizing its users are of increased importance.
If government agencies or any other intruders control more than one node on the data path, they can try to detect traffic detection. This will require analysis of timing and traffic paths, packet labels, and other methods that some studies have shown work against Tor. It is possible to listen to the unencrypted traffic of the output nodes. You can also establish the fact of using Tor, select a narrow group of users (users of one city, microdistrict or network segment) and search for suspects already from them.
To implement attacks, you often need to listen to many nodes in the path of a target, which is not always possible. Less expensive ways to hack the network get a close attention of technical publications.
Deputy Director General Zecurion notes that in the world there is no public data on the ways of hacking Tor. Security researchers, on the other hand, would hardly have published such information. Instead, they would prefer to sell it to the secret services. There is a possibility that the protocol has already been successfully listened to, but we will find out about it much later or not at all. Partner of the law firm Sirota & Partners Artem Sirota says that the very fact of organizing a tender to study Tor’s vulnerabilities is not a violation of the law. Problems may arise when employees of the Ministry of Internal Affairs monitor onion network nodes in order to identify IP addresses that may be considered personal data.
In Russia, Tor and other anonymizers proposed banning Leonid Levin. In February of this year, he spoke in favor of the pre-trial blocking of anonymizers, and the proposal of the deputy was supported by Roskomnadzor. The newspaper "Kommersant" Levin said that there is no ready draft law on this issue yet. Questions blocking anonymizer raised back in 2012.
Tor is popular in Russia. According to the number of users of the Russian Federation ranks third in the world after the United States and Germany. The website Tor Metrics claims that 173 thousand Tor users are estimated in Russia.
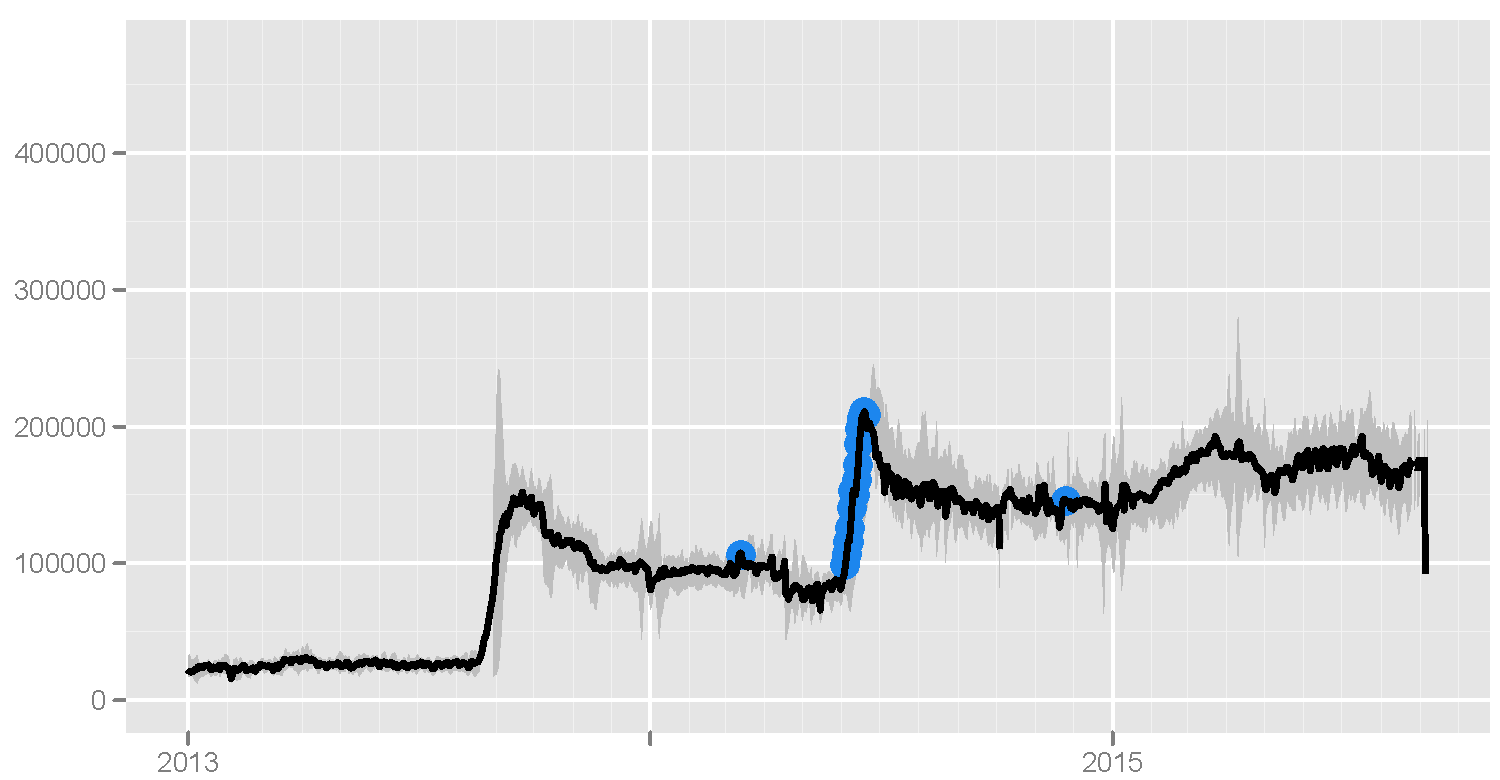
Graph of the number of Tor users in Russia. The blue highlights the events regarded from the Torproject point of view as censorship.
Over the past two years, the number of Tor users in Russia has greatly increased. The jumps in the graph above can be associated with website blocking by Roskomnadzor under the law on child protection and in accordance with federal law No. 187- to combat unlicensed content.
Source: https://habr.com/ru/post/356852/
All Articles