What men pay for: continuation of the story Ashley Madison about burglary

Project of the failed application What's Your Wife Worth
Ashley Madison’s adult dating site hacking story, described in detail in a previous article , continues to grow into details. The second data archive, which has fallen across the network, contains both the correspondence of the Avid Life Media company management and the source codes of several of its sites. A well-known computer security expert told in his blog that he may have been on the trail of one of the hackers. Another researcher carefully calculated how many real women were registered on the site.
Sources of sites
From the same name of the hacker team Impact Team in file-sharing networks, a second file has appeared that is related to cracking of the site Ashley Madison. In the file with the volume of 18.5 Gb, you can find both the correspondence of the leaders of Avid Life Media, and the source codes of several company sites. In addition to Ashley Madison, this is the source code for CougarLife.com, EstablishedMen.com and others.
')
Naturally, such a leak hits the security of these resources. For lovers of hacking, it will be useful to study the source codes of the site and discover vulnerabilities there that can be used later for penetration purposes, for example, to steal user databases from there.
This leak confirms the fact that hackers initially gained access not so much to the Ashley Madison site, as to the company's corporate network. Investigating the materials available, TrustedSec specialists discovered an e-mail containing the Trojan program as an attachment. This is one of the most common ways to gain control over the victim's computer, and, most likely, this is how hackers penetrated first into one of the company's computers and then into its network.
Who is Tadeusz Zu
Brian Krebs is a renowned computer security enthusiast who runs the krebsonsecurity.com theme blog. It is popular enough for the hacking group Impact Team to send one of the first links to the archive with the leaked data via the feedback form.
Krebs studied the received material when he noticed a retweet from the user Thadeus Zu (@deuszu), which indicated the same link to the database that Krebs received from hackers. But this link by that time had not yet appeared in wide access to the Internet. Where did deuszu get it from?
Interested in this user, Krebs downloaded the entire history of his tweets. Over the five years of the account existence, dueszu has published hundreds and thousands of tweets per month, most of which were related to hacking. These were links to the routers they discovered, webcams, and printers that are not password protected or use default passwords. Also in tweets came across links to hacked sites.
On August 4, 2012, he hacked the website of a computer security company (KPN-CERT) and sent them a message about it, attributing that “next time it will be AC / DC Thunderstruck”.
The same kind of warning was sent to the hacking site of the Australian Parliament. And as we remember from the previous series, disgruntled employees of Avid Life Media discovered hacking, turning on their computers in the morning and hearing this particular song by Australian rockers.
Thoroughly surfing the Internet and digging out the user's Facebook page for Thadeus Zu, Krebs failed to reveal his identity, but concluded that even if this Mr. Zu is not a member of the hacker team, he definitely should know one of them.
Weak passwords
As was to be expected, one of the computer security researchers, Dean Pierce, successfully decrypted some of the passwords from the database, despite the fact that they were stored in a hash-bcrypt form. Of the 4,000 passwords received, more than half were banal common passwords that are on any list of the most popular (123456, password, and other similar passwords).
There was nobody to change
One enthusiast decided to check how many women actually registered on the ill-fated website who would be looking for entertainment on the side.
A direct calculation showed that out of about 37 million accounts, only 5.5 million were marked as female. But it is clear that these figures are too high - a few years ago, a former employee of ALM sued the company because of terrible working conditions.
She claimed to have undermined her health while working for the company. According to her, she was instructed to create a thousand fake female accounts in Portuguese to attract a Brazilian audience.
Almost all accounts marked as female were created and soon abandoned. Their owners have never entered into conversations with other users of the site. Continuing to dig up the data, taking into account the ip-addresses used by these supposedly female accounts, used to register emails, and other signs, the researcher came to the conclusion that 12,108 people were registered on the site.
It turns out that male users of the site are unlikely to have changed their wives as a result - they just paid for their sexual fantasies about adultery.
Wish your neighbor's wife
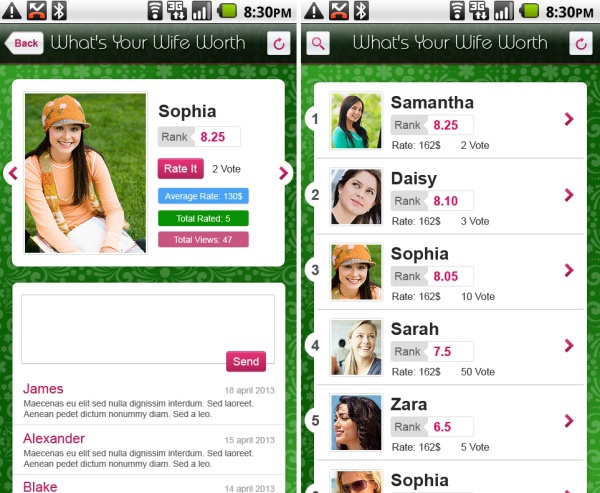
From the correspondence of the directors of ALM one more juicy detail of the company's activity became known. Her employees worked on the mobile app “What's Your Wife Worth” (What is your little wife worth)? Apparently, it was intended so that men could give ratings and characteristics to other people's wives - something like “likes” in social networks, but with a specialization.
Fortunately, this application never saw the light. Judging by the correspondence, it was conceived back in 2013, and in 2014 they came to the conclusion that it is not appropriate to release it.
There are a total of 200,000 emails from Noel Beiderman, the founder and head of ALM, all over the network. Who knows how much more interesting things can be found in them.
Source: https://habr.com/ru/post/356840/
All Articles