Hacking a “smart” sniper rifle over Wi-Fi

Photo Wired
Information security specialists Runa Sendvik (Runa Sandvik) and Michael Auger (Michael Auger) at the Black Hat conference, which will be held in August, will show how to hack the TrackingPoint 750 smart sniper rifle. The manipulation can be divided into two parts: getting access to a computer rifle via Wi-Fi and control of the rifle API from a third-party device so that the shooter can easily not notice the interference, while all shots will, for example, end in a miss.
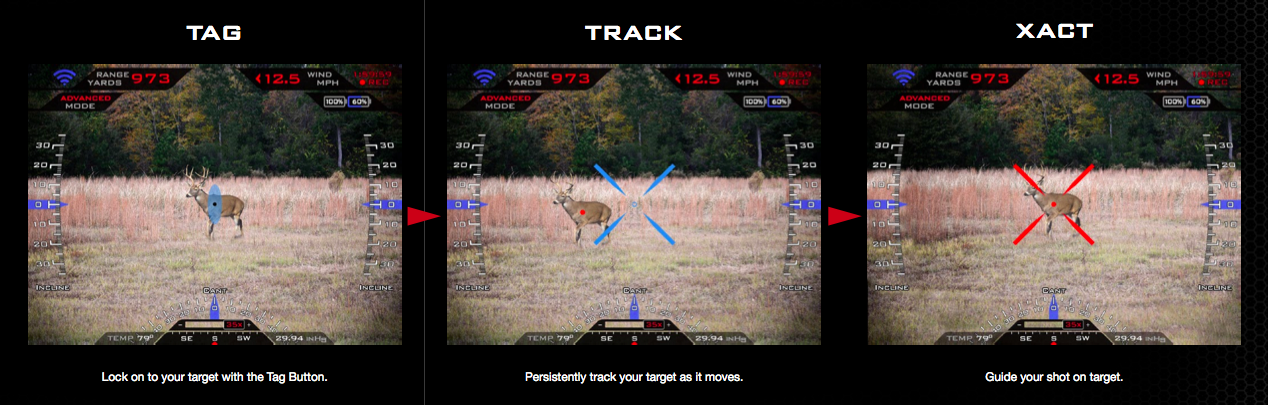
At the disposal of the runes and Michael, who are spouses, there were two TP 750 rifles, each of which costs $ 13,000. The peculiarity of the weapon is that it has a special computerized optical sight, with which the target is captured, it is tracked, corrections for wind and temperature are calculated, and other auxiliary actions are performed. The mechanics of firing look like this: the rifle captures the target, the shooter pulls the trigger, and the actual shot occurs at the moment when the rifle’s pointing system believes that the target is at the crosshair and can be successfully hit.
The photo below shows this process: the shooter points at the target (blue ellipse), presses a special button next to the trigger (the rifle begins to track the target, marking it with a red circle), and finally, the moment of the shot - the reticle of the sight changes color from blue to red:
')
Arstechnica Photos
One of the possibilities of the rifle is to transmit the video image from the sight to another device (computer, phone, tablet) via Wi-Fi in real time to control shooting. By default, this "feature" is disabled, but the enabled network password, which the rifle "distributes", turned out to be factory, which allowed anyone to connect to the weapon. What password is set in the rifle and whether the instruction to change it before use is not quite clear. Since the weapon was obtained by researchers in a legal manner, it can be assumed that they specifically modeled many familiar situations when, on the home wireless router, its owners do not change the default password. Thus, this part of the "hacking" is trivial.
The next part of the research consisted in reverse-engineering of the printed circuit board installed in the rifle in order to restore its API. With this task, the hacker couple successfully coped. Thus, the essence of the manipulations, which it was possible to remotely carry out with a rifle, is that it is possible for the shooter to change the calculated parameters of the shot, simply by connecting to the rifle from the laptop. In the end, you can organize everything so that the weapon will constantly “smear” regardless of the skill of the sniper. In addition, you can simply perform various destructive actions with a rifle, such as turning off the sight, but then the fact of unauthorized intervention will already be obvious.

Photo Wired
The creators of the rifle initially laid a precaution in it: a shot is physically possible only when the trigger is pulled. The researchers did not succeed in circumventing this ban and achieving spontaneous shooting from “smart” weapons.
You can watch the shooting from the “hacked” TrackingPoint on the video below: first, Runa easily hits the target from 46 meters, and Michael (a former developer of Tor), after interfering with a rifle, cannot hit the target.
Source: https://habr.com/ru/post/356816/
All Articles