Information leaks on most VPN providers: is there any reason to sound the alarm?
The results of the VPN security research
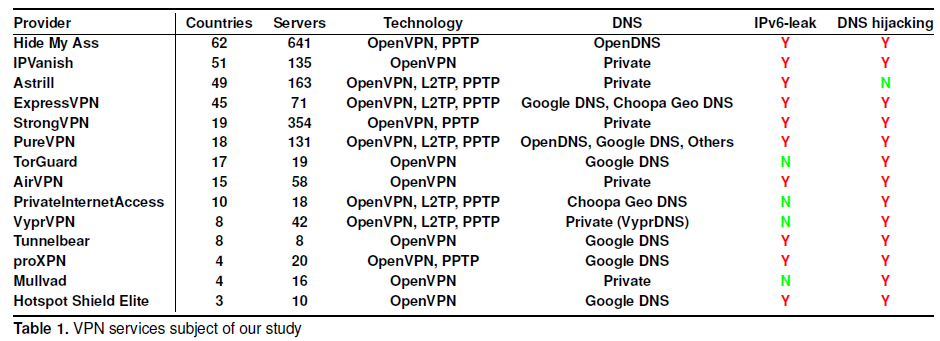
On June 30, a team of researchers from Italy and the UK specializing in computer security presented contradictory work at a symposium on privacy . The paper argues that the VPN connection technology of most of the 14 popular VPN providers permits information leakage through IPv6 and / or by using DNS spoofing.
The authors of the work report that they used a specially configured Wi-Fi access point, as a hacker would have done somewhere in a cafe, and through it, they listened to traffic from a computer connected via VPN.
')
The researchers claim that they were able to obtain various information about the user's activity through the leakage of IPv6, ranging from the sites they visited and even ending with the comments that they leave on social networks. This information turned out to track only on sites that did not use HTTPS. At the same time, they managed to get the browsing history even for those sites that do not support IPv6.
Problems, according to bezopasnik, are connected with various aspects of work of VPN and operating systems. For example, most providers use outdated technologies like PPTP with MS-CHAPv2. In addition, routing tables are processed by operating systems that do not take into account the security settings of VPN clients.
Regarding such serious allegations, TorrentFreak turned to several well-known VPN providers.
PureVPN reported that their experts are studying the work and, if necessary, will take appropriate measures.
In AirVPN, they responded that they received this job from Bezopasnik a few months ago - they deliberately sent out the survey results to all providers so that they could take action. As a result, AirVPN took action, and information about them simply did not have time to change in the report.
TorGuard reported that they released on July 1 a new software that protects against information leaks through IPv6 by forcibly sending such traffic through the tunnel. Regarding DNS substitution, they said that such a situation could theoretically arise only if you get into the network through a compromised router - and in this case, you will have much more problems.
Private Internet Access criticized the work itself and the methods of collecting information, calling it "inaccurate" and "incorrect." They reported that their DNS system was securely configured to prevent any information leaks.
In any case, users who are concerned about privacy and security can check their connection for leaks on the ipleak.net website, and / or completely disable IPv6 support in their operating system ( Windows , Linux , Mac ).
Source: https://habr.com/ru/post/356800/
All Articles