The corporate network of "Kaspersky Lab" could be attacked by the state structure
There are no risks for customers, says Evgeny Kaspersky
 The internal corporate network of Kaspersky Labs was attacked using an advanced platform and several previously unknown zero-day vulnerabilities, the head of the company said. The company called this attack Duqu 2.0. As stated in the statement, customer data and software products were not compromised.
The internal corporate network of Kaspersky Labs was attacked using an advanced platform and several previously unknown zero-day vulnerabilities, the head of the company said. The company called this attack Duqu 2.0. As stated in the statement, customer data and software products were not compromised.Kaspersky Lab claims that with the help of a prototype of its own Anti-APT (advanced persistent threat) solution in early spring of this year, a very advanced and well hidden product was found in the company's corporate network. The first infection occurred at the end of 2014. The development of this malware required the participation of highly skilled programmers and costly: "Conceptually, this platform is ahead of everything we have seen before, by an entire generation." The detected threat was named Duqu 2.0.
Code comparison Duqu and Duqu 2.0. Symantec concluded that the algorithms of the two products are similar.
The original Duqu computer worm was discovered on September 1, 2011 by the cryptography and system security laboratory of the Budapest University of Technology and Economics in Hungary. The worm received its name by the
~DQ prefix, which it added to the files being created. Symantec concluded that Duqu had some connection with the Stuxnet worm. The latter, according to some experts, was aimed at undermining the work of Iran’s nuclear program.')
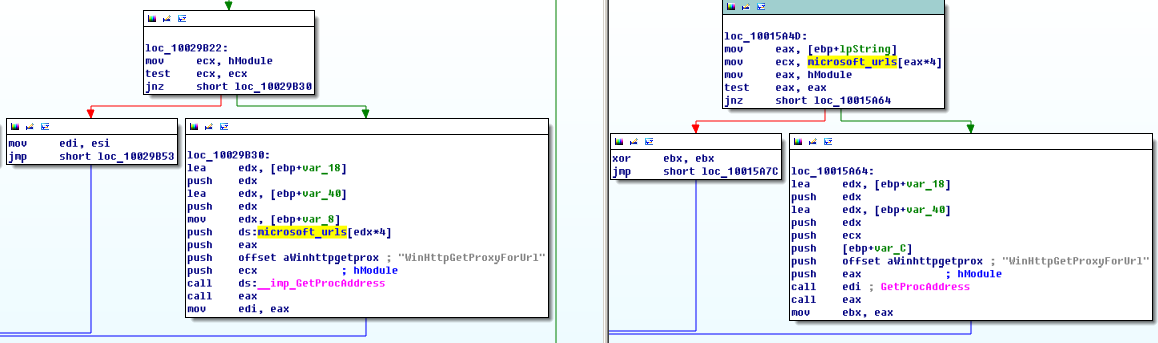
According to the preliminary report of Kaspersky Lab, Duqu 2.0 does not use any form of attachment to the system and is almost completely based in RAM. This indicates that the creators of the program expected to be able to maintain the platform even after rebooting the machine. If the Equation group uses the same encryption algorithm, then Duqu 2.0 always has different encryption and different algorithms.
The attackers showed interest in the company's intellectual property. They were interested in a secure operating system , financial transaction protection system , and the Kaspersky Security Network cloud. The attackers tried to find ways to avoid detection by Kaspersky Lab antivirus products, the head of the company said. In the LC, they believe that their corporate network was not the only goal. Other Duqu 2.0 victims are located in Western, Middle Eastern and Asian countries. Among the notable high-ranking goals are platforms for negotiations on the Iranian nuclear program of the “5 + 1 Group” and events dedicated to the 70th anniversary of the release of Auschwitz prisoners.

Duqu 2.0 workflow, Kaspersky Lab
In a statement, the company stated that the integrity of the source code of products and virus databases were not affected. LC traditionally refuses to indicate the country of origin of the attack. Time stamps and file paths have been tampered with . Kaspersky claims that the government structure is probably behind Duqu 2.0. This is evidenced by the use of numerous previously unknown zero-day vulnerabilities. According to experts of Kaspersky Lab, the cost of developing and supporting such a product can reach $ 50 million. Objectives to extract with the help of Duqu 2.0 financial benefits were not noticed.
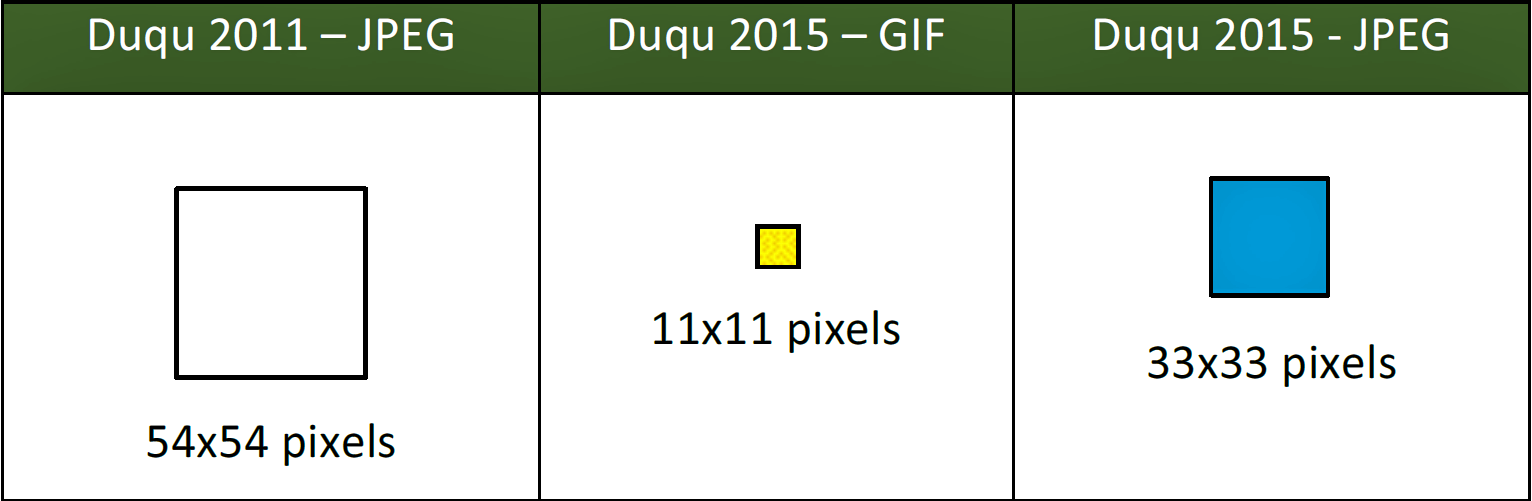
Like Duqu, Duqu 2.0 can store information in graphic images. The original was able to do this in JPEG files, in 2.0 the ability to operate with GIF files was added.
Microsoft fixed the exploited vulnerability thanks to the help of Kaspersky Lab. LK also initiated an investigation in law enforcement agencies of several countries. Antivirus software LC has already "taught" to identify Duqu 2.0. The company is still investigating.
Information about Duqu 2.0 on securelist.com
Duqu Bet Preliminary Report
Source: https://habr.com/ru/post/356778/
All Articles