At the Defcon conference, you can crack Tesla electric car
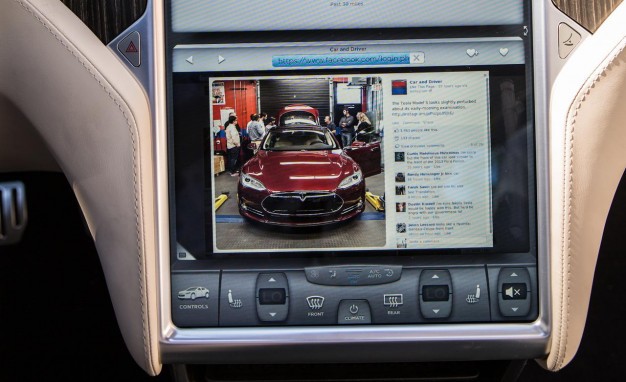
In the summer of this year, at the Defcon hacker conference, they will bring one of the Tesla electric car models, and anyone can try to hack it. Naturally, not physically hack, knocking doors or windows, and through the built-in computer system.
“The benefit for Tesla will be twofold,” analysts say . “They will find out about bugs in the car and find out those hackers worth hiring.” We add that there is a third potential benefit: if no vulnerabilities are found, then Tesla can use this fact to advertise.
Last year, representatives of Tesla Motors came to Defcon to search for potential candidates for employment. According to rumors , the company was going to recruit up to 30 hackers in the state to check the reliability of the car’s computer.
')
Tesla held the same competition for hacking a car at the SyScan hacker conference in Beijing (July 16-17, 2014). Directly in the showroom put a copy of Model S and several computers.
Independent experts have repeatedly said that from such contests more harm than good . This is more like a show. How many people will take part in the competition? Only a few who come to the conference. In case they do not find vulnerabilities, the manufacturing company will make a false assumption that its product is safe to use. Even if they find something, the manufacturer will report the removal of the bug and, again, make a false assumption that there are no more vulnerabilities in the product.
In fact, it can be even easier to connect to the Tesla Model S than to other machines, because here the internal electronics is integrated into an Ethernet local network , and the car computer works under Ubuntu.
A 100 Mbit / s full duplex network in the Tesla Model S connects three devices with IP addresses in the 192.168.90.0 segment. This is the main console, screen / navigation bar and another unknown device.
Some of the ports and services used are:
- 22 (ssh)
- 23 (telnet)
- 53 (DNS)
- 80 (HTTP)
- 111 (rpcbind)
- 2049 (NFS)
- 6000 (X11)
A modified version of Ubuntu with the ext3 file system is running on the car's computer.
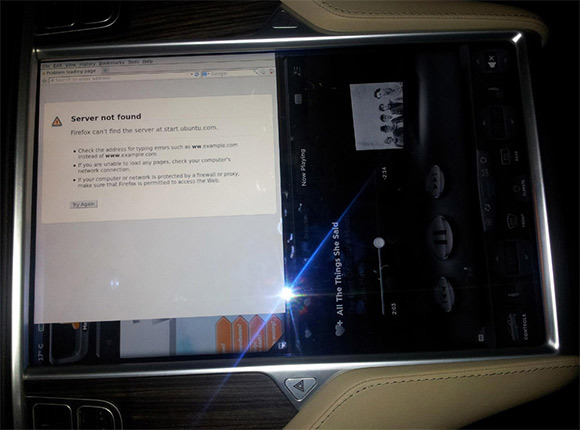
It was possible to connect to the Tesla Model S car computer via Ethernet
That is, these are not some kind of exotic proprietary protocols, but standard well-studied software. Let's see what can be done to visitors Defcon.
Source: https://habr.com/ru/post/356728/
All Articles