Search and seizure of electronic devices and storage media when crossing the US border
“The people's right to protect individuals, housing, papers and property from unreasonable searches and arrests should not be violated ...” - this is how the Fourth Amendment to the US Constitution begins.
Is it possible to conduct a search of electronic devices without court authorization? Will cryptographic tools help? What are the boundaries of privacy in the digital age, when crossing the US state border? If it is interesting to you, I ask under kat.
A brief history excursion
The history of legal protection from arbitrary searches and arrests originates from the English law of the beginning of the XVII century. In the case of Semayne's Case (1604), Sir Edward Kok laid down the principle:
')
For each his house is his fortress, both in terms of protection from violence and unlawful encroachment, and for his peace of mind.
Subsequently, this resulted in Knock-and-announce rules (a representative of the law should knock on the door, warn about a planned search and offer to open the door voluntarily) and astle doctrine (the principle “my home is my fortress” is the right of a person to use any means, including lethal, to protect oneself from unlawfully invading, avoiding subsequently liability for harm).
Summing up: the principle of common law " For each his house is his fortress " Edward Kok laid the foundation for the teaching of the inviolability of privacy and property, which we now observe in modern Constitutions of most states.

In colonial America, however, the British government acted more prosaically: it was issued by the General warrant (“Common warrant”), which gave the soldier or sheriff essentially unlimited power. In the general warrant it was not specified why the warrant was issued, for whom, the reasons for the search or arrest were absent, what was subject to seizure or arrest was also not listed.
After gaining independence from the British crown, the Founding Fathers realized that there was no place for “general warrants” in free America. At the level of legislations of individual states, relevant statutory legislation has been adopted.
Free Translation, Virginia Declaration of Rights (1776):
The practice of general warrants, when an officer or envoy may be authorized to search suspicious places without evidence of unlawful acts, or to arrest unnamed random individuals whose information on offenses is not supported by relevant evidence, is blatant and despotic and should not be turned into a life

All this led to the adoption of the Fourth Amendment to the US Constitution (ratified in 1791) according to which:
The right of the people to the protection of individuals, housing, papers and property from unreasonable searches and arrests should not be violated. No order shall be issued otherwise than if there is a sufficient basis , confirmed by oath or solemn declaration; the order must contain a detailed description of the place to be searched, the persons or objects to be arrested.
How does it work in ordinary life
If you are a US citizen or have a residence permit in this country and are in the United States, then you have the full range of rights provided for by the Fourth Amendment , that is:
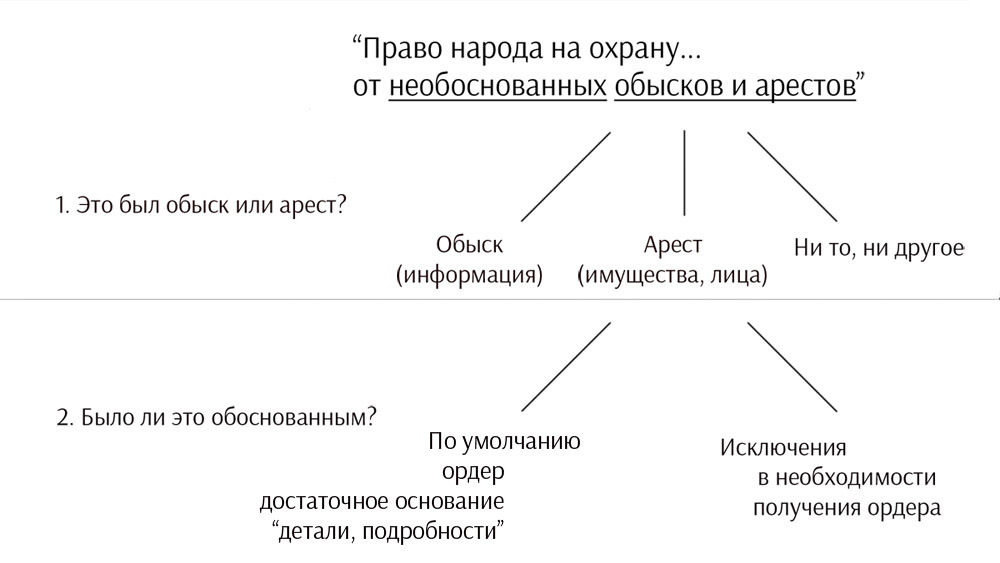
In order to conduct a search of your identity, home, papers and property, the representative of the executive branch must have sufficient reason to suspect you (according to the Probable cause standard), which is confirmed by a solemn statement ( Oath of affirmation ) and he must also list to the court what or who precisely subject to search or arrest . As a result, the judge decides whether or not to issue a warrant.
If the warrant was not received, and the search was conducted - in most cases, the search is considered illegal and all the evidence obtained cannot serve as evidence in the process. In the US, this is pretty strict. Competitiveness of the parties in all its glory. This principle is also enshrined in the criminal process of many civilized states.
And now about an interesting exception to the rule about the need to obtain a warrant.

(Human rights activists ironically call the 100-mile zone “the territory to which the Constitution does not apply.” Interestingly, almost 2/3 of the country's population, or 197.4 million people, live in this territory
Border search exception (“ Border search as an exception”) is a US criminal law doctrine that allows searches and arrests at the state border (including 100 miles from geographical borders), as well as its functional equivalent (for example, international airports in depth of the country), bypassing the procedure for obtaining a warrant and a sufficient reason.
The practice of searches is balanced between the rights of the "sovereign", i.e. a state that must protect national security and the rights of individuals to privacy. Based on this, searches at the state border automatically become justified and do not violate the provision of the Fourth Amendment on protection against unreasonable searches. These powers are vested in the US Border Guard Service (CBP), the US Immigration and Customs Police (ICE), the US Coast Guard (USCG), the US Department of Homeland Security (DHS)
What is most interesting, these searches do not require a sufficient basis or suspicion. That is, a search may be “off-barred” against any person carrying property, including its digital media and devices that qualify as a “closed container” . In practice, this happens in a random order, or according to "ethnic profiles."
Moreover, a search of electronic devices and storage media can be carried out both “on the spot” and by means of seizure (arrest) in a special laboratory. An arrest may last for months.

This branch of law is rather “unsettled” and there are still quite a few precedents, but the Court of Appeals for the Ninth Circuit of the United States (the largest district in the country) in United States v. Cotterman 709 F.3d 952, 956–57 (9th Cir. 2013) made the decision according to which the rule was fixed:
- " Manual search " (manual search) - no suspicion required
- " Forensic search " (Forensic search) - some suspicion is needed
The same Court of Appeal is already in another case - United States v. Arnold 2008 WL 1776525 (9th Cir. 2008). - to the statement of the party that:
a search of the traveler’s files on his laptop affects human dignity and privacy as well as searches of the traveler’s body
Objected and ruled that:
electronic media searches are legally equivalent to property searches
The US Supreme Court in one of its decisions touched upon the problem of “disorderless” searches or arrests of electronic media, and ruled that (loose quotation):
authorized customs officers may search any electronic media (including laptops, compact discs, MP3 players, cell phones and digital cameras) by accident, without suspicion and prohibitions. The first amendment to a search of this nature does not apply
Subtotal

When crossing the state border of the United States, your electronic devices and other information carriers may be searched, the data may be copied, and then on returning the devices themselves, the copies will be subjected to forensic examination. All this happens without the need for suspicion and without order (i.e. without a court order).
If you are lucky and you are in the jurisdiction of the Court of Appeal for the Ninth Circuit of the United States, then law enforcement officers will still need to some degree to substantiate the level of suspicion against you to conduct forensic research.
Concerning not a search, but an arrest
If you are unlucky, your electronic devices and storage media will be arrested and sent to the laboratory for more in-depth research. There are no exact regulatory deadlines, but I met the figure “up to 120 days”. That is, you should be ready to part with your devices for a long time, in an unfavorable scenario.
On August 1, 2008, the Washington Post published information that the internal regulations of the US Department of Homeland Security allowed federal agents
withdraw a laptop or other electronic device and transport it to external locations for an indefinite time , without any suspicion of an offense
and what is most interesting:
employees have the right to share data with other bodies or legal entities of private law for translation, decryption or other reasons
Wait, what about cryptography?
The presence of cryptographic information security tools you can only raise the degree of suspicion against you.
Of course, if you go to meet and decipher the device - it will be a plus. If you refuse, they can simply refuse you entry. Or withdraw your devices for forensic investigation. Most likely, even all at once. If you have already spent money on a ticket, the host country is waiting for you - playing a crypto-anarchist at customs is probably not the best way.
But do not blame much on the policy of the United States Because your refusal regarding the reproduction of the “key” that is in your head is completely legitimate. According to the Fifth Amendment - "should not be compelled to testify against itself." If the “key” is your fingerprint, as in the newest Apple smartphones, you can’t get out of here, there are other doctrines.
Probably you are already mentally cursing the US Constitution and all their Amendments, but let me point out that in the US there is indeed relative liberalism. Because such a progressive country as the United Kingdom can give you up to 5 years, if you can not make a decryption. Even if you do not have the key. In France - up to 3 years and a fine of 56,000 USD, in India up to 7 years, in South Africa up to 10 years and a fine of 180,000 USD. It is best to forget the keys in Australia: up to 6 months in prison.
Are you paranoid and want to talk about it?
Of course, all these rules, laws and court decisions worry human rights defenders, associations of professionals, information security specialists and ordinary travelers. For example, how do such “deprived” practices relate to law on attorney secrets ? Or about the protection of a trade secret, in the case when employees make business trips abroad? As long as these questions remain open, unresolved by a sufficient number of precedents and the practice of the Supreme Court, the executive branch can act “on the edge”. But public opinion, in the light of Snowden's revelations, is clearly not on their side, and it is quite possible that these practices will be settled in a more correct way.
I'm flying to the States tomorrow, what should I do?
With paranoia with experience, it is recommended to transport the device “OS-only”, although you should not forget that storing prohibited information (such as child pornography), even remotely (or in an unplaced area, as in United States v. Cotterman) is also offense.
In the thematic Reddit thread , some users say that:
When you make international trips, especially to the United States or China, take only a clean leptop with you. It should be installed only OS and basic applications. Access to all data only via VPN, Clouds or other more secure channels ...
Never transport corporate information or confidential information. individuals across the state border of the United States or China, because of the great likelihood of its compromise. This also applies to the United Kingdom and other states with “totalitarian surveillance” against their own citizens.
We have a similar corporate policy: if we travel to China, we can only carry a “clean” laptop. In addition, if the laptop is out of sight at border controls in the US, we must file a report with the security service in order for the latter to conduct a security audit
And after passing the border and customs control, leaving the 100-mile zone, you can already upload your data from the clouds or your VPN on the spot ... Oh wait, what about the mass surveillance programs for trunk communication channels? .. :)
Sources:
1. Stanford Law School - Surveillance Law - Border searches - also recommend the entire course on Coursera
2. Border search exception - Wikipedia
3. United States v. Cotterman 709 F.3d 952, 956–57 (9th Cir. 2013)
4. United States v. Arnold 2008 WL 1776525 (9th Cir. 2008)
5. Border searches of laptop computers after United States v. Arnold: implications for traveling professionals
6. The New York Times
7. Court curbs laptop searches at the US border - The Washington Times
PS If you like, unsubscribe in the comments, please. I have plans to turn this into a series of “Legislation on Snooping” articles.
Source: https://habr.com/ru/post/356620/
All Articles