HSTS Supercuts for spying on users
HTTPS implementation features allow you to distinguish a particular user
 For many years now, there is a feature in all major browsers due to which any website owner can follow a visitor. There is a considerable amount of irony in the fact that the function exploited by this is designed to provide security.
For many years now, there is a feature in all major browsers due to which any website owner can follow a visitor. There is a considerable amount of irony in the fact that the function exploited by this is designed to provide security.A software consultant from the British company RadicalResearch recently drew attention to the problem . In fact, Sam Greenhal discovered America: a description of this protocol vulnerability appeared in the HSTS draft itself (see clause 14.9 of the Creative Manipulation of HSTS Policy Store).
But Greenhal clearly showed how this function can be used to their advantage. In some browsers, not only cleaning cookies, but even incognito mode does not help.
The mechanism is called HTTP Strict Transport Security, and it is very important to ensure a reliable connection between the user and the server.
')
After installing a special flag in the header, the user's browser will always request the encrypted HTTPS version of the site. This protects users from eavesdropping: an attacker between network nodes will not be able to slip HTTP versions of pages available for interception.
The data that the specific domain has been set the HSTS flag is stored in the user's browser, it is a logical variable (true / false). These are not cookies, but security information, which is why browsers treat it differently. HSTS flags can be difficult to remove.
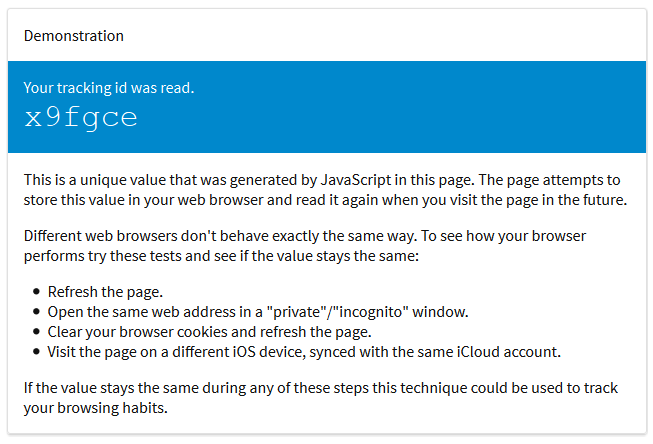
A concept called HSTS Super Cookies uses this data to identify the user in the same way that ordinary cookies do. The site will “recognize” the user if he has already visited the resource. In this case, you can read HSTS Super Cookies from any domain name.
HSTS saves only binary values - either it is enabled or not. Therefore, Greenhalou had to customize 32 domains in a special way, this volume is enough to store information about more than two billion users. To improve perception, the number is translated to base36 : instead of 71009647, the user sees 169ze7, 1307145327 - lm8nsf, and so on.
C HSTS Super Cookies can be found on the project page .
After visiting the page, the value identifier is set, which can be read from any domain. Traditional cookies can only be read from the domain that installed them.
Most users can feel at ease: clearing cookies in Chrome, Firefox and Opera also means deleting HSTS data.
But this is not true for all browsers. The researchers were concerned about the behavior of Safari, the popular browser of all Apple devices: the HSTS user’s flags are not only not removed, they even sync with iCloud, keeping an imprint forever.
The latest version of Firefox 34.0.5 has some protection against this potential threat to privacy: in incognito mode, the HSTS values cannot be set. Greenhal said that in version 33 under Windows HSTS Super Cookies still works.
Chrome developers, in turn, believe that the vulnerability is inherent in the architecture of the web, so there is no point in doing something.
Superkuki do not work in Internet Explorer: there is no support for HSTS, although they are going to add it.
When HTTP Strict Transport Security was created, the problem was thought of. But it was decided that it was very important to prevent attacks with a decrease in the level of security, even if it is necessary to compromise and leave the opportunity to follow the user through these "prints".
There is no particular cause for concern, and without HSTS, monitoring user behavior is easier than it seems. As the EFF demonstrates , there are many other ways to distinguish the user from the rest without the use of cookies: the configuration of our computers (OS, language pack, resolution and screen color depth, system fonts, time zone) and browsers (language, installed extensions, plug-ins, version ) most often quite unique for these purposes.
Source: https://habr.com/ru/post/356616/
All Articles