The extortion program TorrentLocker earned 500 thousand euros only in Europe
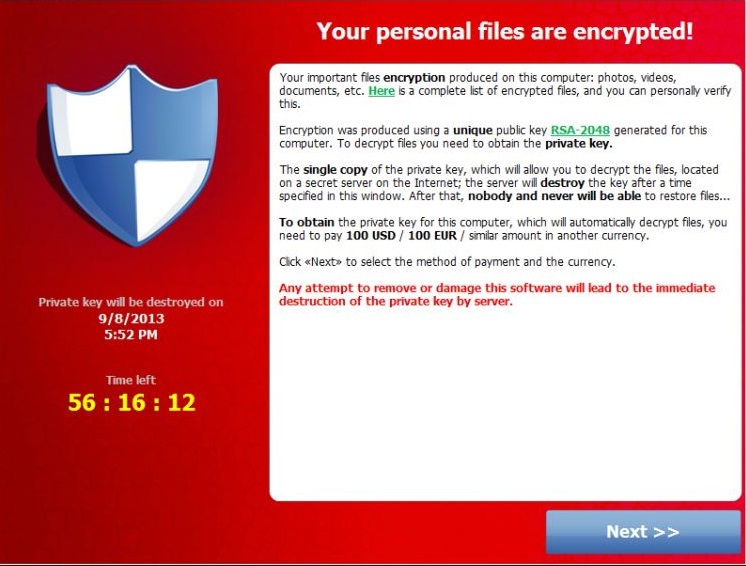
Ransomware many programs , but one of them, TorrentLocker, can be considered the leader of this “market”. For the first time, TorrentLocker appeared around February 2014, and since then the virus has managed to infect many thousands of computer systems. As a rule, the virus penetrates the victims' computers, which open suspicious attachments in e-mail messages (nothing changes here, as we see).
According to a study , about one and a half percent of owners of infected systems pay a bribe to extortionists - the creators of this virus. As you know, TorrentLocker requires you to pay in Bitcoin. At the current rate, the authors of the malware have already received more than 585 thousand US dollars.
')
TorrentLocker works in much the same way as other extortionists, with a slight difference. So, when getting into a new system, user files are encrypted with 256 AES encryption key (random generation). For a key that will allow the user to get their data back, the attackers require about 4 bitcoins (that's about one and a half thousand US dollars). The key itself is already encrypted with a 2048 RSA key, and is sent to the central server. After that, the AES-key is removed from the system. If the victim pays, the key is sent to the victim to recover the encrypted data.
At the moment, the malware has already encrypted about 280 million documents on a PC, mainly in Europe. Affected many in Canada, Australia and New Zealand.
The developers of the virus spread it in a completely normal way: sending spam, which refers to an unpaid invoice, a fine for speeding or tracking a package. In the message - either an application with a virus, or a link to the site. The site is quite presentable, the developers have tried to arrange it in the official style to make it look like a government resource or a reputable company site. There is even a CAPTCHA on this site, which appears when a user tries to download “unpaid invoice” data.
The virus is packed in a ZIP archive, or contained in a Word-based document with a macro that downloads and installs a virus. As before, the victim needs to run the .exe itself to start the virus. Messages are received by users of many countries, except, for some reason, the United States. It is unclear why the attackers do not send messages to the citizens of this country.
Experts from ESET believe that behind the creation of the virus is the same team that created the family of banking Trojans Hesperbot. Detailed research from ESET can be obtained at this link .
Source: https://habr.com/ru/post/356592/
All Articles