Chinese traffic routing error in Russia
In September last year, the third largest Russian mobile operator, Vimpelcom, and China Telecom signed an agreement on the direct connection of international and long-distance communication networks and interconnection, the amount of this contract was $ 2.2 million. The goal of this deal for the Russian side was to reach the Far East.
Over the past year, the Chinese telecom operator has tried several times to play Ivan Susanin. Doug Madori writes about this in detail in the DynResearch company blog.
')
Translated from the language of ordinary people into the language of specialists, the deal concluded means that the two companies have agreed to share information on dynamic routing using the BGP protocol. And as it often happens in such situations, one of the parties may issue routing data from other providers, which will put its communication lines in the path of the traffic of the second company. Specifically with these two companies, this has happened more than a dozen times over the past year. This phenomenon happens, but is poorly described in the BGP literature.
In general, BGP peering is a frequent occurrence in the world of large network providers, and this action has several meanings. Specifically, in this case, it means routing in such a way that traffic is exchanged freely, without paying one of the parties. Without a transit provider, you can save a lot, even if you spend money on servicing these peer-to-peer schemes.
In any case, the routing information received by one of the providers from another under the peering agreement usually remains within the network of this operator. In the example below, provider A sends information about the routing of its customers' data to provider B, as a result of which traffic from provider B’s clients goes through the peering connection to provider A.’s clients. This is normal operation.

Something can go wrong in several different ways. Provider B can take routes from provider A and send them to other providers, as shown below. Thus, provider B puts itself in the path of external traffic destined for provider A.
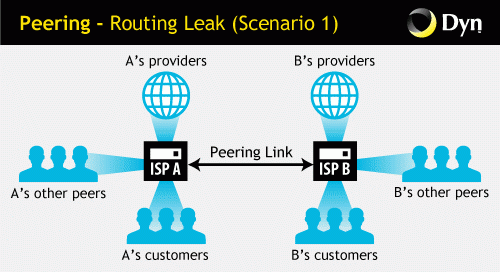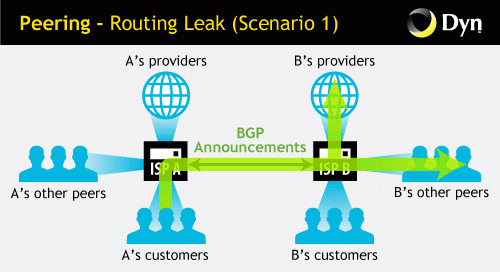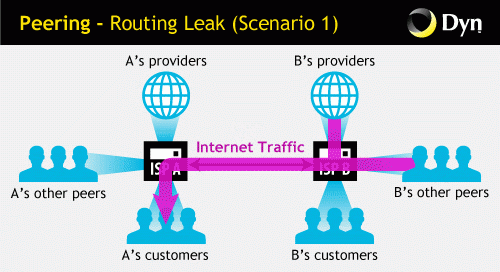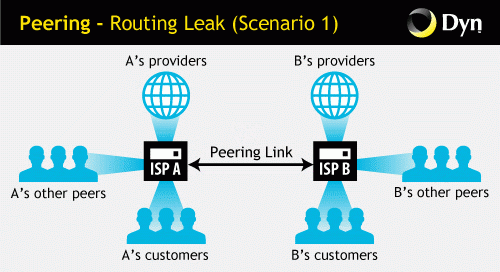
If provider B provides a route received from providers to which it has a connection, to provider A, then the latter’s traffic will follow these paths through provider B, even if it usually does not have to go through provider B.

Unlike other major and well-known incidents, the situations described above can occur often, and their appearance does not cause such a surge of attention. The response grows and packet routes change, and this is harder to notice than the complete lack of a network, so these problems may remain unresolved for a long time. In any case, the traffic is not going where it should, which negatively affects network performance and information security.
So, over the past year, incorrect information about the routing from China Telecom has hit the VimpelCom network several times. This happened, for example, on August 5 of this year, when China Telecom (AS4134) briefly submitted to VimpelCom almost its entire BGP table (326,622 entries), which resulted in a sharp increase in the response for users of Russian providers. Still, only about 120 ms are needed for traveling from Russia to China. Routing even within Russia was carried out through China Telecom networks.

This was the result of the traceroute: the information began its journey in Virginia (USA), then it was sent to California via NTT networks, where it was transmitted to China Telecom. From there she went to Shanghai, and then to Frankfurt and only later to Russia, to Omsk.
Hidden text
trace from Reston, VA to Omsk, Russia at 12:00 Aug 05, 20141 *2 129.250.204.153 (NTT America, Ashburn, US) 1.010ms3 129.250.4.40 (NTT America, Ashburn, US) 0.934ms4 *5 129.250.5.13 (NTT America, San Jose, US) 74.649ms6 129.250.8.6 xe-0.chinanet.snjsca04.us.bb.gin.ntt.net 70.909ms7 202.97.90.33 (China Telecom, San Jose, US) 71.451ms8 202.97.58.237 (China Telecom, Shanghai, CN) 341.819ms9 202.97.58.66 (China Telecom, Frankfurt, DE) 641.424ms10 118.85.204.58 (China Telecom, Frankfurt, DE) 608.965ms11 79.104.245.250 pe-r.Omsk.gldn.net 632.054ms12 195.239.162.178 (Vimpelcom, Omsk, RU) 687.536ms13 89.179.76.25 vpn2-gi0-0.omsk.corbina.net 682.153ms14 128.73.155.213 128-73-155-213.broadband.corbina.ru 707.525msFor a more visual illustration of the abnormality of this situation, let’s take a look at the VimpelCom traceroute to Germany. Traffic goes from VimpelCom networks to Frankfurt, then enters China Telecom networks, which deliver it to Shanghai before returning Chello Broadband, which has a peering agreement with China Telecom in Los Angeles. Then Chello Broadband takes him to New York, from there to Frankfurt again, and only then to Germany. For half a second traffic at least once rounds the globe.
Hidden text
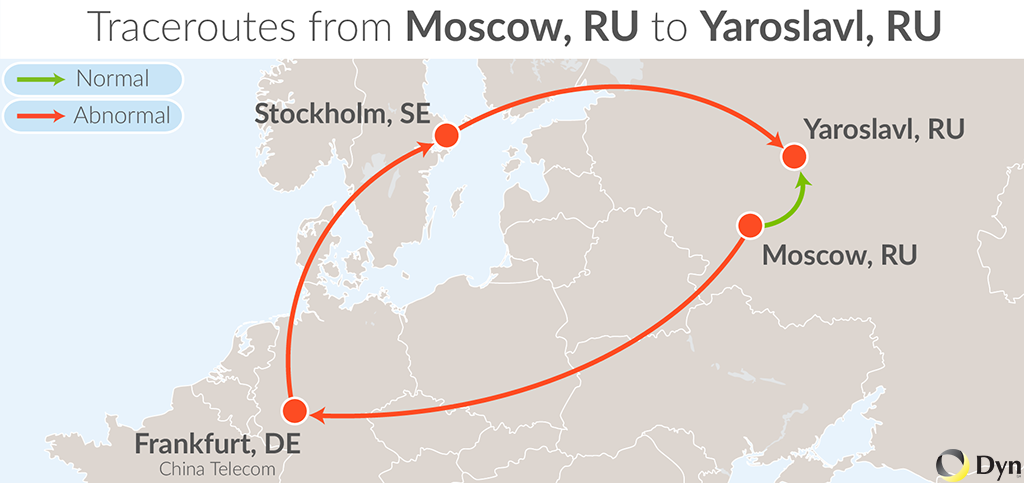
trace from Moscow, Russia to Marburg an der Lahn, Germany at 14:29 Aug 05, 20141 *2 194.154.89.125 (Vimpelcom, Moscow, RU) 0.908ms3 79.104.235.74 mx01.Frankfurt.gldn.net 40.695ms4 118.85.204.49 beeline-gw2.china-telecom.net 48.799ms5 202.97.58.61 (China Telecom, Shanghai, CN) 290.810ms6 202.97.58.202 (China Telecom, Los Angeles, US) 514.115ms7 202.97.90.62 (China Telecom, Los Angeles, US) 537.933ms8 213.46.190.217 213-46-190-217.aorta.net (New York) 414.365ms9 84.116.135.122 (UPC Austria GmbH, Vienna, AT) 420.591ms10 213.46.160.205 uk-lon02a-rd1-pos-4-0-0.aorta.net 421.530ms11 84.116.133.65 (UPC Austria GmbH, Frankfurt, DE) 421.557ms12 81.210.129.234 7111a-mx960-01-ae1.fra.unity-media.net 420.867ms13 80.69.107.214 7111a-mx960-02-ae0.fra.unity-media.net 418.427ms14 80.69.107.185 7211a-mx960-01-ae1.gie.unity-media.net 420.454ms15 88.152.128.0 (Unitymedia, Marburg an der Lahn, DE) 423.105msEven the internal Russian traffic, which usually goes to Moscow, went through the equipment of China Telecom. In the following example, traffic from Moscow is sent to Frankfurt, then China Telecom is processed there as well and only after it returns to Megafon networks. Thanks for the fact that not through Shanghai. (An illustration of this particular situation is shown on the map of Europe before the kata.)
Hidden text
trace from Moscow, Russia to Yaroslavl, Russia at 13:13 Aug 05, 20141 *2 194.154.89.125 (Vimpelcom, Moscow, RU) 0.542ms3 79.104.235.74 mx01.Frankfurt.gldn.net 37.006ms4 118.85.204.57 beeline-gw4.china-telecom.net 39.505ms5 213.248.84.185 ffm-b10-link.telia.net 41.481ms6 62.115.137.180 ffm-bb2-link.telia.net 42.227ms7 80.91.251.159 s-bb4-link.telia.net 42.894ms8 213.155.133.105 s-b2-link.telia.net 41.528ms9 80.239.128.234 megafon-ic-151430-s-b2.c.telia.net 42.707ms10 *11 78.25.73.42 (MegaFon, Volga,RU) 49.992ms12 213.187.127.98 ysu1-ccr1036-1.yar.ru 50.301ms13 213.187.117.230 (NETIS Telecom, Yaroslavl', RU) 54.769msOf course, when planning the network level of the organization of the Internet, its security was poorly thought out, and these peer-to-peer leaks can hardly be avoided. But this not only leads to performance problems, but also makes you very worried about security.
All this is somewhat amusing if we recall that several weeks ago it became officially known about the desire of the Russian government to have greater control over the security of the Russian Internet segment. Is it really impossible to deal with specific issues, because they constitute the security of our network segment?
Source: https://habr.com/ru/post/356560/
All Articles