June situation with unavailability of resources due to website blocking
All Internet providers in Russia are forced to block links made to the Unified Register of Banned Sites. It represents a huge dump of links (including those that do not meet the standards ), domains and IP addresses. There is no general method of blocking, there are only abstract recommendations from Roskomnadzor, therefore each provider blocks sites in his own way, to the best of understanding of the registry, his technical advancement and budget.
The overwhelming majority of providers use some kind of traffic analysis system to block specific URLs, not IP addresses: DPI hardware systems, DPI-open Linux, transparent proxy servers. This is quite enough to block links in HTTP, but not all systems support domain analysis (SNI parameter) in HTTPS traffic, which is why providers with such systems have to block HTTPS registry links by IP address.
Also in the registry there are sites entered by the domain, without specifying the protocol. Some providers block such records by IP-address, others - only HTTP and HTTPS-protocol in these domains. In order not to buy expensive DPI configurations that can analyze the entire huge flow of traffic, providers passed through DPI only known IP addresses of blocked sites, and were less expensive to configure.
Each entry in the registry, whether it is a domain or a link, has its own list of IP addresses. Until the end of January of this year, providers blocking partially or completely by IP addresses, it was enough to filter access only to IP addresses from the registry. At the end of January, the Auditor software was updated - a system that checks how well the provider blocks websites. If earlier “Revizor” tried to open the site to a single IP address from DNS, like any regular browser or program, after updating it makes requests to all IP addresses both from the DNS response and from the registry. At the same time, providers began to penalize the opened sites, there were no concessions and the allowable threshold of suddenly opened sites.
')
In order not to be fined, providers started constantly checking whether new IP addresses appeared on the domain and adding them to the lists blocked and passed through DPI.

This was followed by the partial inoperability of Telegram and some other sites.
Under special circumstances, if the resource IP address was added to a domain entered without a URL, or to a URL with HTTPS, and traffic to the site came through a provider that implements blocking for transit traffic, the site became unavailable immediately from everywhere, globally for everyone.
Transit locks mainly affected resources passing through Rostelecom and TTC:
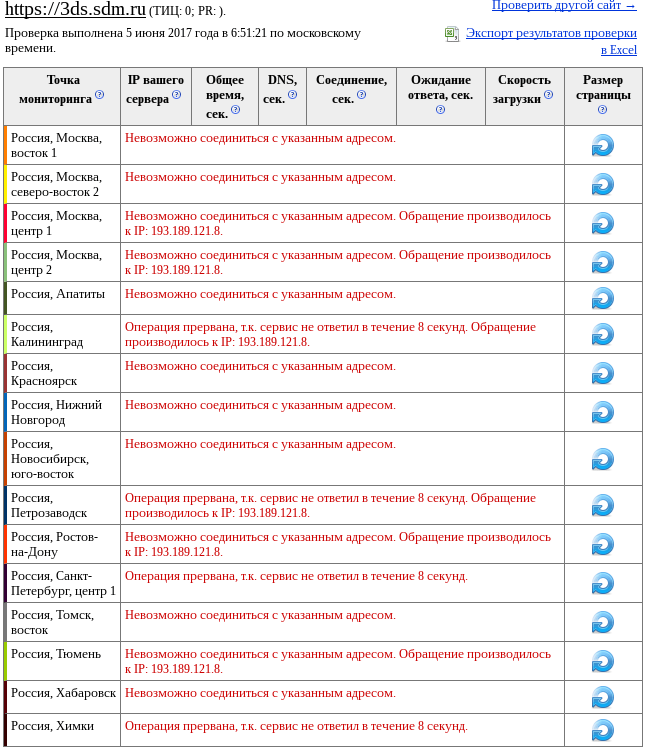
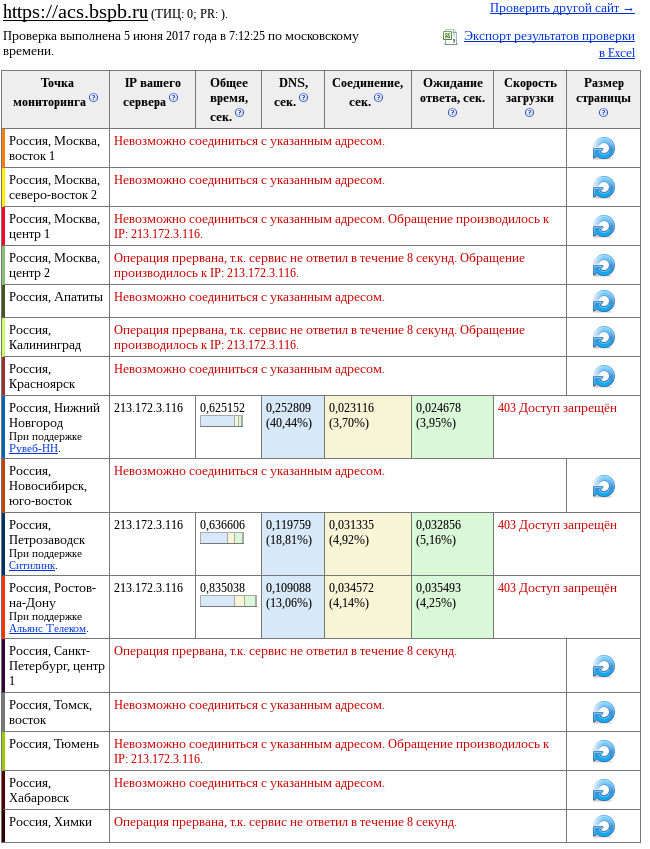
Nag and NTV lay for a long time, half a day, or so. The inability of the last two domains, which provide 3-D Secure (SMS confirmation of an online transaction on the card) of banks St. Petersburg and SDM, was not announced either by the media or by the banks themselves.
For a long time anti-ban has an anomaly detection system to exclude the IP addresses of popular resources from the proxy list, if the owner of the blocked domain has set the A-record to this IP address. The list of IP addresses for defining anomalies was made up by itself, popular world and Russian sites got to it, root DNS and DNS of common domain zones, technical bank domains .
Waking up on Monday morning, I found a large number of anomalies, was surprised, and decided to check the availability of some services ping-admin.ru - the result in the screenshot above. I do not know how long they held out and on what domain they were installed, since the script was run every 6 hours and gave only a list of IP addresses (now I have already modified it). In the subsequent unloading of these IP was no longer.
On June 7, in inept attempts to rectify the situation, Roskomnadzor compiled and sent a “white” list of sites to providers , with IP addresses and domains, which it would be better not to block.

Roskomnadzor combined the cells in the XLS document so that every second record was not visible, and many tried to understand for a long time why, for example, some root DNS servers entered it, and others did not. Everything became clear when someone thought of setting the height of all cells to the same value.
Funny entertainers began to leave a message in the DNS records to Roskomnadzor and providers (there is even from a 14-year-old boy ), and also made their own service blocking arbitrary IP addresses!
Later, the main providers woke up. Realizing that things are not being done this way, Transtelecom first began to proxy all requests to blocked sites in transit (literally, through squid, with the outgoing IP address changed), and then began to disable blocking transit traffic, forcing small providers to filter sites independently.
The last anomaly is as follows:
ping-admin.ru, , , meduza.io tjournal.ru.
, ! , -, , , , ? , ? , .
(, , ).
.
The overwhelming majority of providers use some kind of traffic analysis system to block specific URLs, not IP addresses: DPI hardware systems, DPI-open Linux, transparent proxy servers. This is quite enough to block links in HTTP, but not all systems support domain analysis (SNI parameter) in HTTPS traffic, which is why providers with such systems have to block HTTPS registry links by IP address.
Also in the registry there are sites entered by the domain, without specifying the protocol. Some providers block such records by IP-address, others - only HTTP and HTTPS-protocol in these domains. In order not to buy expensive DPI configurations that can analyze the entire huge flow of traffic, providers passed through DPI only known IP addresses of blocked sites, and were less expensive to configure.
Each entry in the registry, whether it is a domain or a link, has its own list of IP addresses. Until the end of January of this year, providers blocking partially or completely by IP addresses, it was enough to filter access only to IP addresses from the registry. At the end of January, the Auditor software was updated - a system that checks how well the provider blocks websites. If earlier “Revizor” tried to open the site to a single IP address from DNS, like any regular browser or program, after updating it makes requests to all IP addresses both from the DNS response and from the registry. At the same time, providers began to penalize the opened sites, there were no concessions and the allowable threshold of suddenly opened sites.
')
In order not to be fined, providers started constantly checking whether new IP addresses appeared on the domain and adding them to the lists blocked and passed through DPI.
The fun begins ...
Starting from May 29, people began to slowly buy the divided domains from the registry, which were added in 2014-2016, and set A-records on them to IP addresses of popular resources. Providers resolved these domains, added IP-addresses to the list of blocked, access to resources was lost. The first pranksters added Vkontakte and Yandex entries, which is why some providers blocked access to them. Roskomnadzor sent the following notice:
This was followed by the partial inoperability of Telegram and some other sites.
Under special circumstances, if the resource IP address was added to a domain entered without a URL, or to a URL with HTTPS, and traffic to the site came through a provider that implements blocking for transit traffic, the site became unavailable immediately from everywhere, globally for everyone.
Transit locks mainly affected resources passing through Rostelecom and TTC:
- Root DNS
- ntv.ru
- nag.ru
- avito.ru
- 3ds.sdm.ru
- acs.bspb.ru
Nag and NTV lay for a long time, half a day, or so. The inability of the last two domains, which provide 3-D Secure (SMS confirmation of an online transaction on the card) of banks St. Petersburg and SDM, was not announced either by the media or by the banks themselves.


For a long time anti-ban has an anomaly detection system to exclude the IP addresses of popular resources from the proxy list, if the owner of the blocked domain has set the A-record to this IP address. The list of IP addresses for defining anomalies was made up by itself, popular world and Russian sites got to it, root DNS and DNS of common domain zones, technical bank domains .
Waking up on Monday morning, I found a large number of anomalies, was surprised, and decided to check the availability of some services ping-admin.ru - the result in the screenshot above. I do not know how long they held out and on what domain they were installed, since the script was run every 6 hours and gave only a list of IP addresses (now I have already modified it). In the subsequent unloading of these IP was no longer.
... and continues
On June 7, in inept attempts to rectify the situation, Roskomnadzor compiled and sent a “white” list of sites to providers , with IP addresses and domains, which it would be better not to block.

Roskomnadzor combined the cells in the XLS document so that every second record was not visible, and many tried to understand for a long time why, for example, some root DNS servers entered it, and others did not. Everything became clear when someone thought of setting the height of all cells to the same value.
Funny entertainers began to leave a message in the DNS records to Roskomnadzor and providers (there is even from a 14-year-old boy ), and also made their own service blocking arbitrary IP addresses!
Later, the main providers woke up. Realizing that things are not being done this way, Transtelecom first began to proxy all requests to blocked sites in transit (literally, through squid, with the outgoing IP address changed), and then began to disable blocking transit traffic, forcing small providers to filter sites independently.
The last anomaly is as follows:
104.244.42.129 nudism.ga. # twitter
104.244.42.193 nudism.ga. # twitter
109.207.1.97 nudism.ga. # gosuslugi.ru
163.172.11.143 zenitbet44.com. # meduza.io
163.172.11.149 zenitbet44.com. # meduza.io
163.172.180.25 zenitbet44.com. # meduza.io
163.172.40.199 zenitbet44.com. # meduza.io
163.172.73.23 zenitbet44.com. # meduza.io
163.172.74.46 zenitbet44.com. # meduza.io
194.54.14.159 nudism.ga. # sberbank
194.67.29.100 www.segodel.com. # securepay.rsb.ru
216.146.46.10 www.10sport10it.com. # travel.s7.ru
216.146.46.10 www.betrallyru.com. # travel.s7.ru
216.146.46.11 www.10sport10it.com. # travel.s7.ru
216.146.46.11 www.betrallyru.com. # travel.s7.ru
50.112.196.159 nudism.ga. # twitch
52.36.196.57 nudism.ga. # twitch
52.41.96.17 nudism.ga. # twitch
5.255.255.88 bethaze.ru. # yandex
5.255.255.88 dabet.ru. # yandex
5.255.255.88 zerkalo-tv.ru. # yandex
77.88.8.88 www.segodel.com. # yandex
88.212.240.172 zenitbet44.com. # meduza.io
88.212.244.68 zenitbet44.com. # meduza.io
91.227.34.40 zenitbet44.com. # meduza.io
95.167.27.74 www.segodel.com. # DNS Rostelecom
95.213.255.15 www.rutinadew.com. # tjournal.ruping-admin.ru, , , meduza.io tjournal.ru.
, ! , -, , , , ? , ? , .
(, , ).
.
Source: https://habr.com/ru/post/356174/
All Articles