In the browser Opera 50 implemented protection against mining

Setting up NoCoin in Opera 50 browser to protect against mining cryptocurrency
Opera 50 is approaching a stable release. A few days ago, the release candidate Opera 50 beta RC came out, using as an example all the new features that developers have added to the new version can be explored. Among the most interesting is the expanded support for playing spherical video VR360 for Oculus and Chromecast and the first among all browsers built-in protection against miners of cryptocurrency NoCoin.
The blacklist of NoCoin is published on GitHub , so you can load it into your ad blocker — and get the same functionality in any browser. For example, here's a text file for AdBlocker , but for the system hosts.txt .
As you know, lately, intruders get all the great popularity of mining cryptocurrency directly in the browser. The most popular of the services is the Coinhive affiliate program, there are other JavaScript miners. A person enters the site - and on his computer the load on the central processor dramatically increases. Some miners squeeze CPU resources by 100%, others act more carefully and covertly, so that the user does not suspect anything. Moreover, recently miner sites have learned to even hide the browser on users' computers . The trick is that despite the visible closing of the browser window, in fact, the browser does not close, but remains in memory. The malware opens an invisible pop-up window like pop-under. The coordinates of the pop-up window are chosen in such a way as to hide exactly behind the clock on the taskbar.
')
The coordinates of the window may vary slightly, depending on the screen resolution on the victim's computer, but it fits in behind the clock. True, there is one nuance. If the operating theme has a design theme with translucency, then the window is still slightly visible behind the panel.
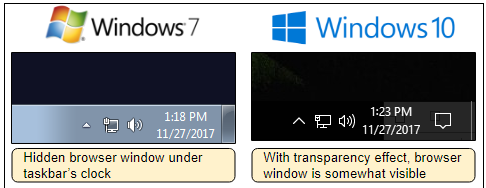
Browser window hid behind the clock
Typically, such scripts are not hosted by site owners, but by outsiders who hack sites. Attacks of this type are called cryptodikeking.
At one time, Opera was the first popular browser with a built-in ad blocker. Now the developers have updated the rules of the blocker - and added to the black list miners cryptocurrency. Thus, with the activated NoCoin function, mining scripts on the pages are blocked in the same way as regular banner ads.
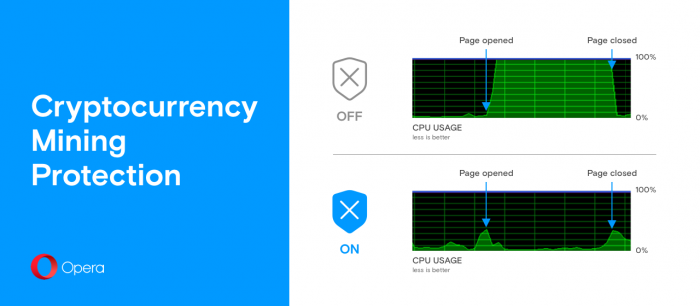
The screenshot shows how the load on the CPU changes when entering a site with a built-in miner with the mining protection option turned on (below) and off (above).
It is necessary to add that Opera is not the only browser sol with built-in ad blocker. There are other (little-known) browsers with this feature. For example, Brave Browser .
Links to install Opera 50 beta:
- Opera beta for Windows
- Opera beta for Windows (Portable version)
- Opera beta for macOS
- Opera beta for Linux - deb packages
- Opera beta for Linux - RPM packages
A previous study of crypto-miners on websites of online stores showed that the script of the most popular service for cryptodikeking Coinhive is installed on at least 2496 e-commerce sites . In 80% of cases, these sites have not only installed the Coinhive script, but also various malware for skimming - copying the details of bank payment cards of store customers. This is direct evidence that the sites have been hacked. The fact of hacking is also indicated by the fact that 85% of the scripts are associated with only two Coinhive identifiers. The remaining 15% is distributed among a large number of other IDs. However, in this entire group with different link IDs, the site name is the same. That is, it can be assumed that these 15% are also created by one person or group. In other words, all infections of online stores are made by three groups of intruders.
Mining cryptocurrency consumes a lot of electricity. Globally, it is already a significant part of global energy consumption . According to Trustwave, the average computer consumes 1212 Wh more electricity than usual per day for the Coinhive script. For a month out 36.36 kWh. At Moscow rates (5.38 rubles / kWh), 195 rubles 62 kopecks are obtained.
Source: https://habr.com/ru/post/355166/
All Articles