Conference DEFCON 22. "DDOS attack cell phone for $ 2 per day: 70 calls per minute." Weston Hecker
The topic of my presentation today is the use of cell phones with a 2-dollar daily fee for DDOS attacks with an intensity of 70 calls per minute.
My name is Weston Hecker, I penetration tester, studied computer science and geophysics, have tons of certificates, wrote several user exploits and scripts for PMS Hotel real estate management software and Internet providers, created several ISP devices, like the one about which I will tell today , as well as a number of devices for software testing.

')
I have been testing devices and security for over 9 years. I am the creator of the Fake iPhone Park series of hacking products that are better than the USB Rubber Ducky hacker device.

This is how my park of fake “iPhones” using the Teensy 3.0 compact platform with Arduino support looks like.

Have any of you used Rubber Ducky when testing for penetration or other vulnerability tests? It can be combined with Teensy 3.0 and inserted into the iPhone, and I have a plan for you how to use it. These pieces are sold for $ 7 each, and they work much better than the classic "ducks" with USB.
I also developed the Phone Call Bomber “Call Bomber” hacker device based on a Samsung prepaid phone that runs on solar energy and can be hidden, for example, in lamps of public libraries.
I also came up with an RFID scanner that is mounted under a chair or chair. It uses the Arduino platform with a three-axis gyro sensor. When a person moves in a chair, the scanner scans the data of a bank card in its pocket or purse. It does not work incognito, because it confirms the successful reading of the data with a sound signal.
And now I will tell you what the difference between DDOS and TDoS attacks is.
DDOS attack is an attempt to make a computer or network inaccessible to users. Depending on the motives and goals, these attacks may differ in the way they are implemented, but in any case they are aimed at disabling the host that provides Internet services.
A TDoS (Telephony Denial of Service) attack, or telephone service failure, is a stream of unwanted malicious incoming calls. These calls attack call centers or other customer services to make voice calls more difficult or impossible. In fact, people are deprived of legal services to call someone and talk with him by phone. This has happened over the past few years and has often been a manifestation of activism.

Most people nowadays do not use traditional analog telephone communication, they make calls via the IP network using the SIP protocol, that is, in fact, telephone communication is carried out via the Internet.
Most often, I have come across cases of TDoS related to banking fraud. Now the theft of a physical card does not attract thieves, they act more on the network. Let me give an example: if I use my credit card to pay at some gas station in Texas, the banking company Wells Fargo will definitely try to call me. Therefore, fraudsters are trying to use TDoS to attack the phones of people who own premium bank cards. Most cases of banking fraud occur in Los Angeles and California, where attackers are embedded in the telephone connection between call centers and existing banks.
Using a fake CID Called ID was one of the reasons I ended up here. A couple of years ago in the morning, just before I went to Minneapolis, I received 3 phone calls. I had a new number, so I assumed that these were calls to the previous owner of the phone, who used the service for missed calls. But when I called this number, it turned out that it has a fake Caller ID. This phone belonged to an elderly man from somewhere in Delaware and he said that he received about 140 such calls per day. People say that they received a call from him and asked what he wanted from them, and because of this he was going to change his phone number. Then I first thought about TDoS attacks.
So these attacks apply:
I know dozens of government agencies that receive a huge number of anonymous calls that paralyze their activities. This is a manifestation of political activism.
And now I will talk about the existing methods of TDoS attacks.
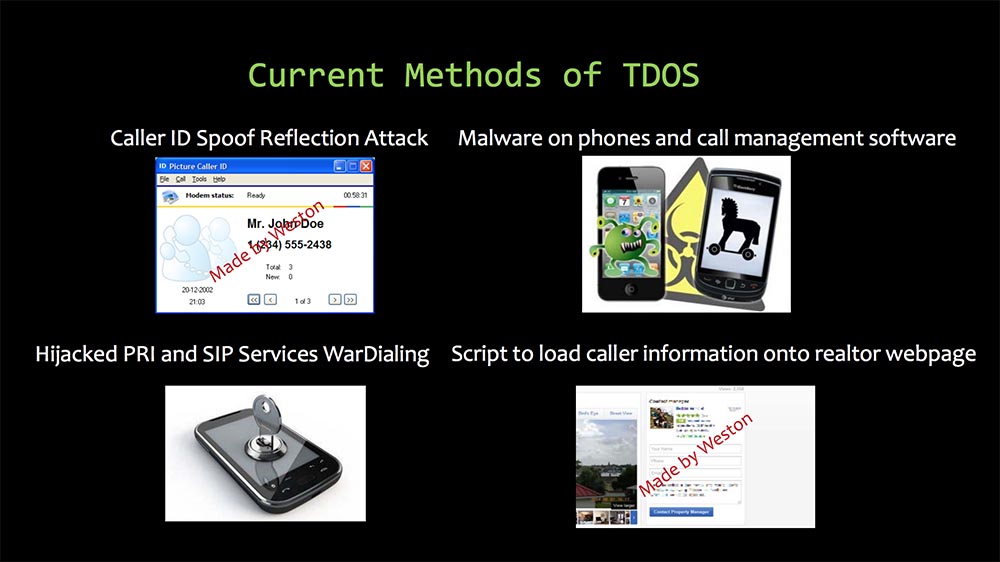
The first is called counter attack fake Caller ID, this is my own development, later I will tell about this in more detail. This is followed by malware on phones and call management software. I am sure that you have attended many DEFCON conferences where the use of malware for iOS and Android was discussed.
Then come PRI and SIP hacked services, which are used to make the so-called “War Calls”. War Dialing is an automatic scanning of the subscriber list and calling each number of the local telephone network to search for computers, BBS ad boards, faxes and modems.
My latest development is a script for uploading phone numbers of subscribers to existing web pages of realtors. It looks quite decent and does not require much effort.
Reflected attack fake Caller ID is to use a legitimate telephone service with fake information about the caller's phone number. Naturally, people who receive a call as if from this number, overwhelm the unsuspecting subscriber with thousands of callbacks, because they are sure that he was the one who called them. Using the application with a PRI server, we can generate 23 calls per minute to different subscribers who receive a fake caller's phone number. You can loop the list of phone numbers depending on which “dialer” is running on your computer. If you receive a message that the subscriber tried to call you 3-5 times, you call him back to find out what he wanted from you. In fact, you will call the phone number of a person who has not actually called you.
Today I will tell you how 15 phones could “collapse” 200 call centers.
Many people, including myself, do not call back to the specified number, because they believe that if someone could not get through to them, he would leave a voice message.
This is followed by a reception when real estate sellers are used to carry out a TDoS attack. To do this, use a script that places on the web pages of realtors fake customer information, automatically filling out the form on the page. About 76% of real estate sites use the same templates of the questionnaire without a “captcha”, so it is easy to fill out and submit such a form automatically. At the same time, the username and password required to fill out the form is generated very easily. Today, there are approximately 4,800 pages of realtors on the network, which the script can fill with fake information in 2 hours. For example, such: “I just sold my house in Nevada and am looking for something suitable in the area. Please, call me. John Doe.
As a result, a squall of calls from realtors falls on the phone indicated in the form.

There is also a botnet infected with smartphones. Smartphones, like computers, can serve as platforms for botnet networks. The increase in the number of "rutted" phones reduces their security and increases the risk of hacking.
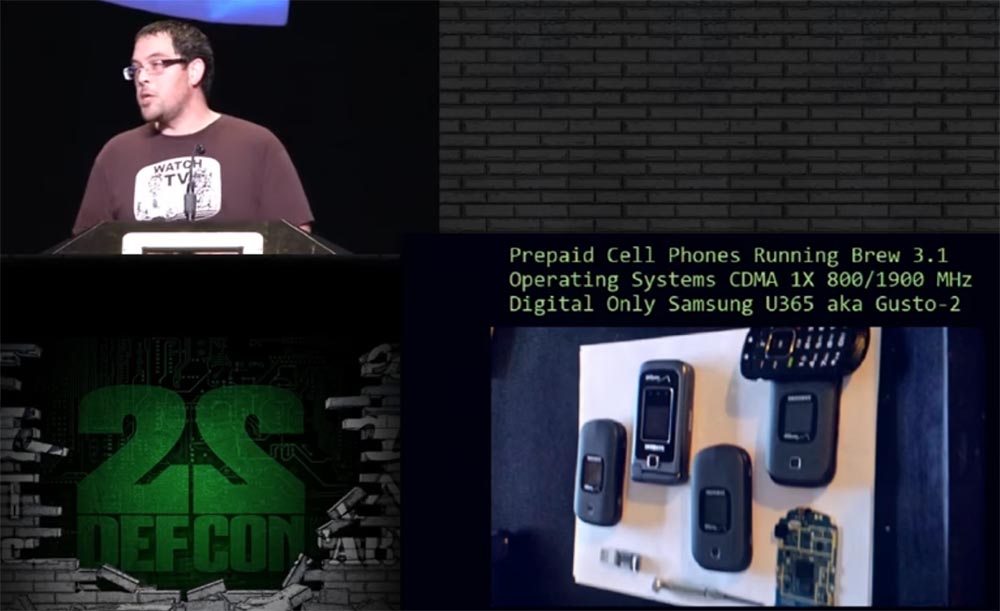
I want to tell you how I developed a “combat platform” based on OEM cell phones.
Prepaid cell phones use OS Brew 3.1, CDMA 1x 800/1900 MHz communication technology, and the Samsung U365 model, known as Gusto-2, also supports digital services. This is a very common model, surely many of you had such a “clamshell”. The mobile phone operator Verizon can buy this phone for $ 8-12.
Here is the chip installed in it with a Qualcomm QSC6055 processor with a frequency of 192 MHz. My "combat platform" is compatible with all processors of the QSC60xx series.
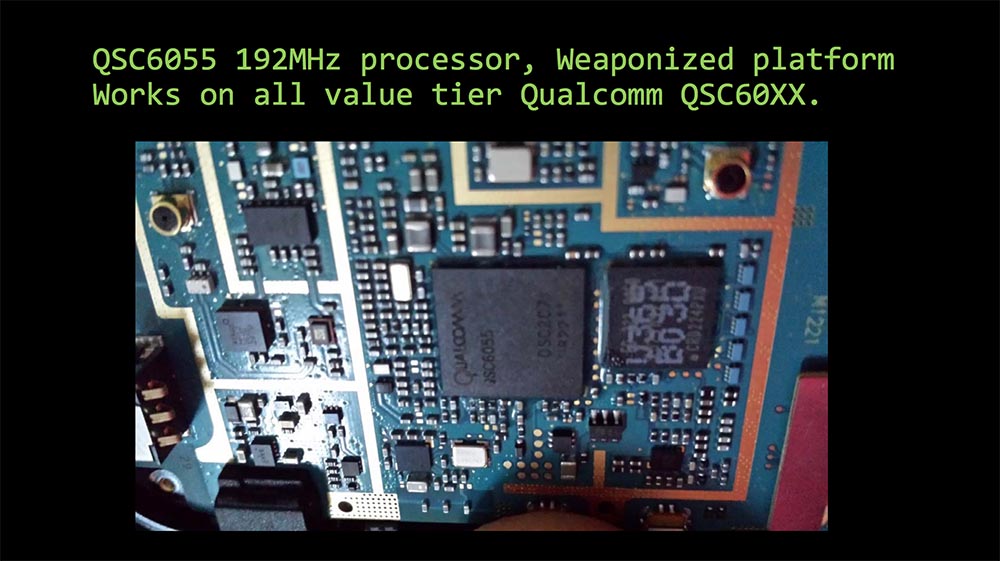
In 2014, I conducted a study on who exactly uses prepaid phones, and got the following result:
This chip has three security features built in: secure boot, secure boot, SEE and SFC. However, in the OEM version, that is, the version from the manufacturer, there is support for the normal boot mode of the phone, which unlocks the sets of functions, that is, makes it possible to get root-rights. In order to load my phone exploit, I created a pseudo-signature, with which the device “agreed” to work, as a result of which a recompiled operating system was loaded into the phone. The fact is that each manufacturer used its own OS, so I wrote a modified version of the OS that matched all phones with this chip.
This model is ideal for hacker experiments because of its price of $ 8, that is, it will not be a pity if, as a result of your manipulations, the phone turns into a “brick”. In addition, it allows you to use a large set of software from developers, which is written in C ++, so it is very easy to get the phone to work according to its own program.
Brew OS provides the ability to monitor voicemail and turn the device on or off using Brew applications. This feature exists by default if the user interface (UI) runs on top of Brew. The manufacturer provides the ability to change software parameters using the PST product support tool.
I used a lot of these phones to understand how it all works. I was lucky to find a team of talented Germans who eliminated my knowledge gaps and helped me to create an exploit for this phone. This is an amazing phone for someone who wants to learn how to hack cell phones.
It was designed in such a way that it is possible to use many additions and extensions for convenience. For example, you can use the battery saving mode, and then the screen of the phone while receiving calls will not light up. He has a very economical battery - when I was preparing for this performance, I often called the guys from DEFCON, and at the end of 7 days of use, there were 3 more bars on the battery charge indicator. You buy this phone from Verizon for $ 12-14, and it prepares calls for another $ 10, and then pay $ 2 every day for unlimited calls. This is a very convenient tariff plan.
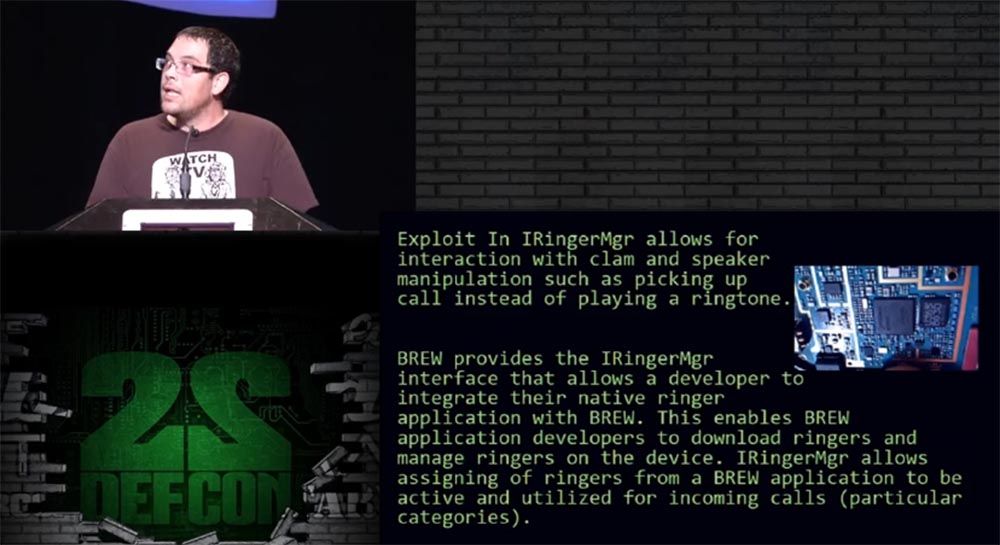
The introduction of the IRinger Mgr exploit allows you to carry out manipulations with the phone, such as silently receiving a call, that is, the phone receives an incoming call without activating the ringtone and without having to lift the top cover. This is a very convenient attack feature. Brew allows you to use the IRinger Mgr interface to implement your own calling program in the OS. Thus, the exploit uses the operating system of the phone, which receives and processes incoming calls in the mode we need.
Folding phones have certain functions that report on a flip cover. On these phones, by changing media files, for example, ringtones, you can “bypass” triggers and events triggered by hardware, depending on the specific user action. Thus, using the OEM version of the device with the “factory” OS and the application compiled by me, you can “bypass” any factory function and interact with the phone as you please.
You can write your own ringtone with the desired payload, consisting of "wrong" packages. Thus, you can interact with the phone using the wrong packet generator or by downloading already modified ringtone. It was a modified executive file that allowed me to download the necessary firmware to my phone. For the software of this phone, the certificate expired in 2012, it has operated since 2006, that is, the phone has not been used for several years. The modified executive file allowed to bypass the phone’s security functions through the “hole” in the certificate validity period. The next slide shows how I managed to install the phone’s firmware through the Samsung PC Studio 3 proprietary software, ignoring the Windows warning about expired certificate by simply choosing “Install this software anyway”.

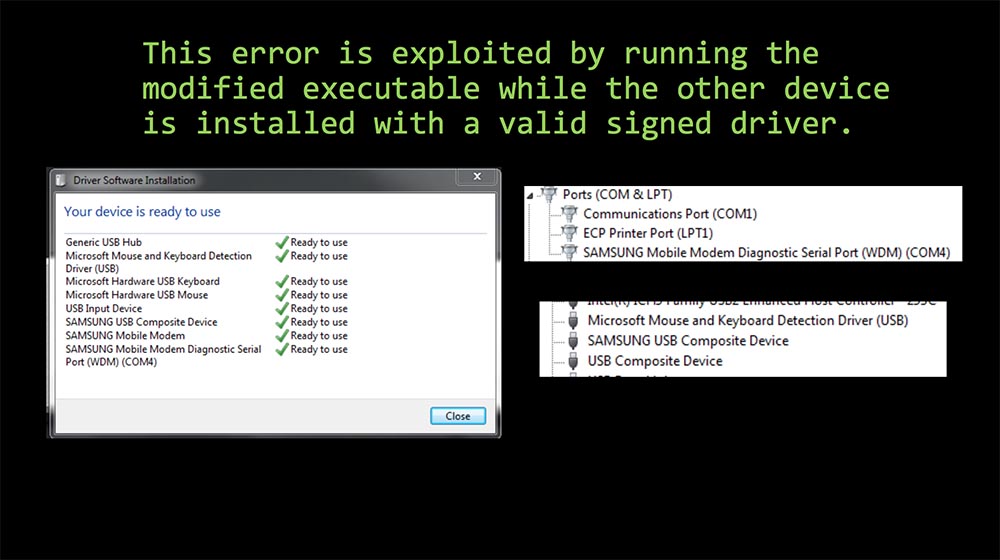
This error was used to launch a modified executable file, while other devices were installed with a driver that had a valid signature.
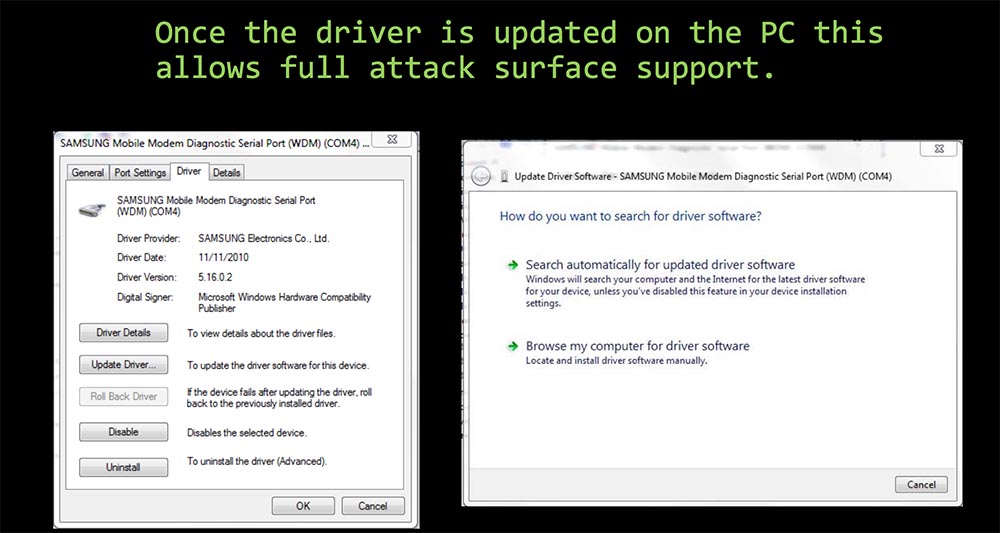
After updating the driver using a personal computer, it became possible to carry out a full-scale attack on the phone.
The next slide shows the certificate, which expired in 2012, which allowed me to bypass the settings of the security function.

Modified driver files allowed to modify all information about devices.
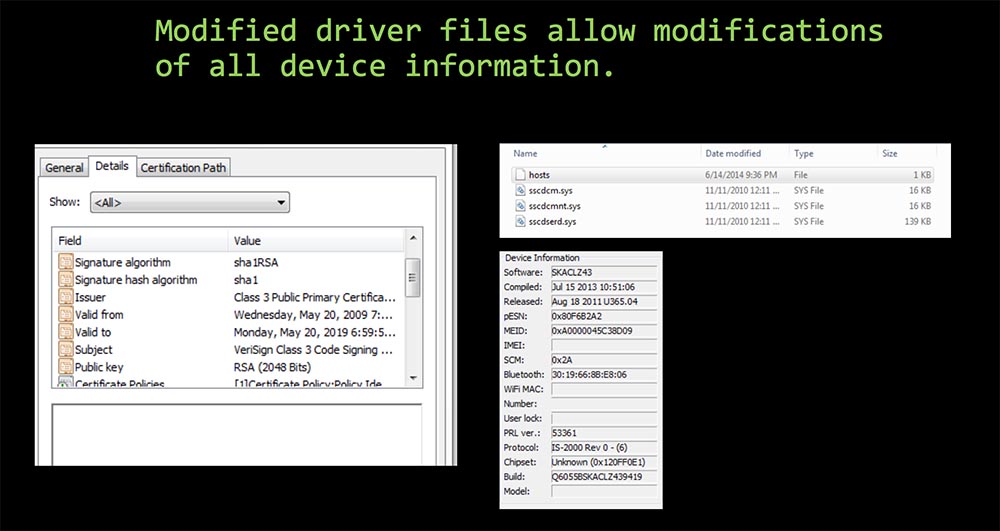
I note that I needed the drivers and the program for updating the firmware from the official Samsung website, where there were very outdated versions of this software. Perhaps this is one of the reasons why the phone is sold so cheaply. Again, I easily managed to do with this phone, everything I wanted.
Another remarkable feature of this "Samsung" is the formation of a preferred PRL roaming list, which determines which networks can use this CDMA phone. It shows which ranges and mobile networks should be scanned when turned on, and which of them should be given priority connection. He usually scans 12 cell towers, so he can use a triangulation method to determine the location of your house. You can fix 3 arbitrary towers and thus freeze the GPS position of the phone or disable position detection altogether, which will make it impossible to track the real location of the phone.
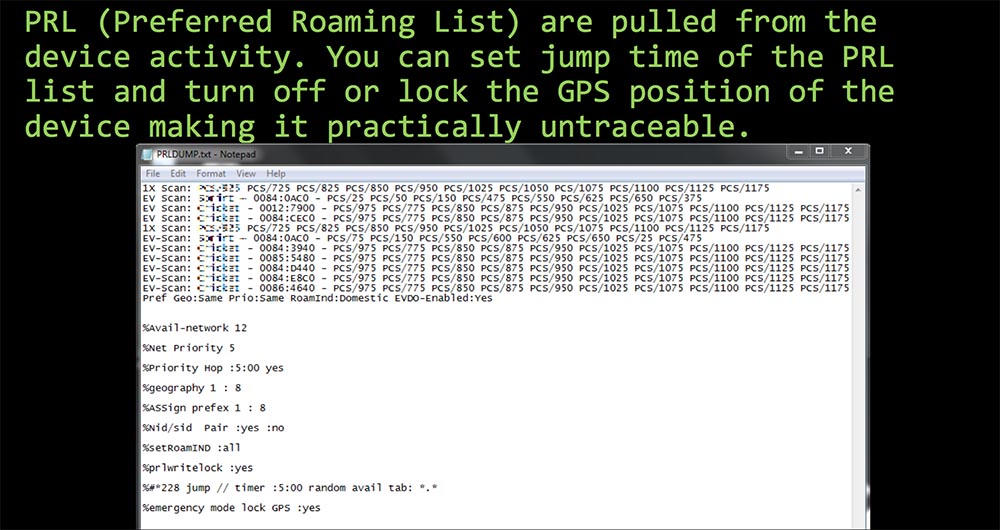
It is also necessary to modify the PRL for carrying out attacks, since with the GPS positioning function turned off, the attention of the cellular operator will not be attracted by the fact that someone needed to make 70 calls per minute from the same phone. Turning off the GPS function turned out to be very simple. I noticed that it is not fully restored until you make a call to 911. This looks like some kind of interaction with cell towers on an ongoing basis.
You can create an application for an attacking platform by emulating software using a platform emulator written by OEM hardware developers. That is, having a completely open "native" platform, you can create on its basis its own "combat" platform. At the same time, the application can be tested without even downloading it to the phone.
While testing my platform, I broke several phones. By the way, one of the reasons why I wrote my ringtone with a malicious package was the desire to break the phone with the help of a ringtone.
With the attack platform loaded onto the phone, you can gain complete control over its functions, such as TDoS or Brickmode. First you need to download a ringtone that carries a specific “payload”. Installing this ringtone, which I called Callbomb, as a ringtone for a call, launches the malicious functionality of the ringtone in relation to its associated event. That is, I installed this ringtone on my phone and sent it to the phone number I wanted to possess, and he started calling the numbers indicated in the text message with an intensity of 70 calls per minute. The calls continued until the battery was completely discharged. This is an extreme number of calls in the shortest amount of time that cannot be traced.
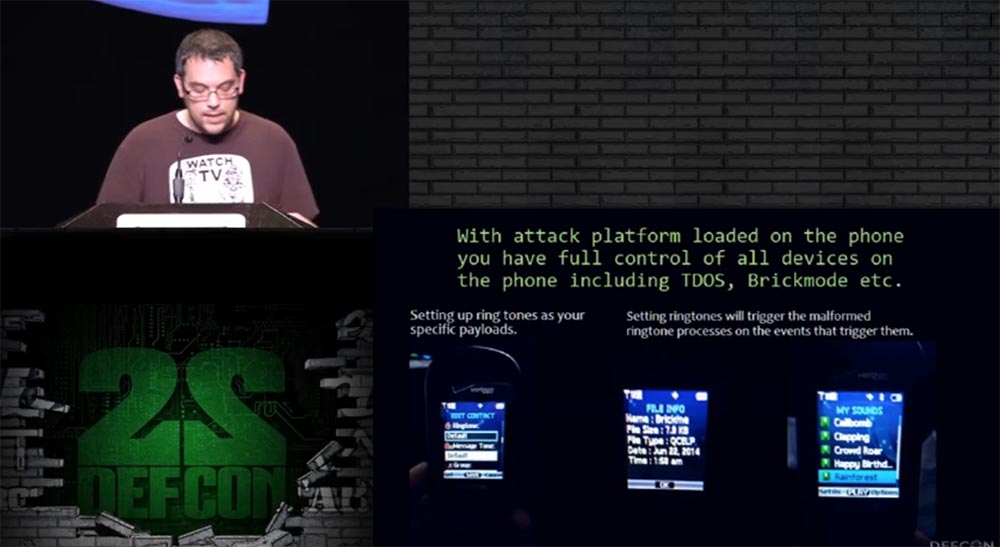
To complete the five-day cycle of "bombing calls," I set the alarm, and he disabled the phone. If someone was more experienced in programming and had more time, he could arrange something like a “flash” that would destroy the phone software so that it could not be restored. Thus, with the help of my technology, you received full access to the phone itself, its modules and interfaces.
Do any of you know what CheeseBox is? This is an "old school" term associated with bookmaking. For example, a bookmaker rented an unused apartment or store in which he installed several telephones and an electronic device called CheeseBox. The player called the number of one of these phones. When the phone took the call, CheeseBox automatically converted it to an outgoing call to the bookmaker’s phone, which was on a completely different line. Thus, the player never knew the real telephone number of the bookmaker. This technique is used by people who want their phone number to remain anonymous.

I wrote a ringtone pack that helped me deliver other ringtones. He provided a Bluetooth connection with other phones and made it possible to redirect the phone call. Suppose I made a call to the number I needed and after some random amount of time (it was possible to set the timer for 5-15 s), my phone "belonged" to another cell phone tower. It was possible to have at the same time 2 phones, each of which was tied to its tower. The technology was as follows:
Thus, the absolute anonymity of your phone was ensured. People may need it for a variety of reasons.
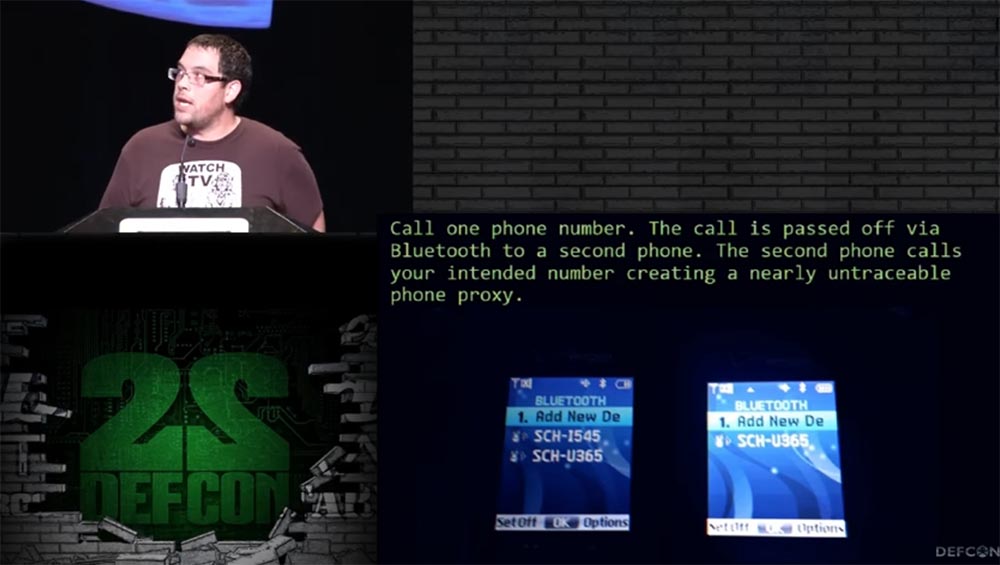
You can connect via Bluetooth up to 3 phones at the same time in order to make random outgoing calls.
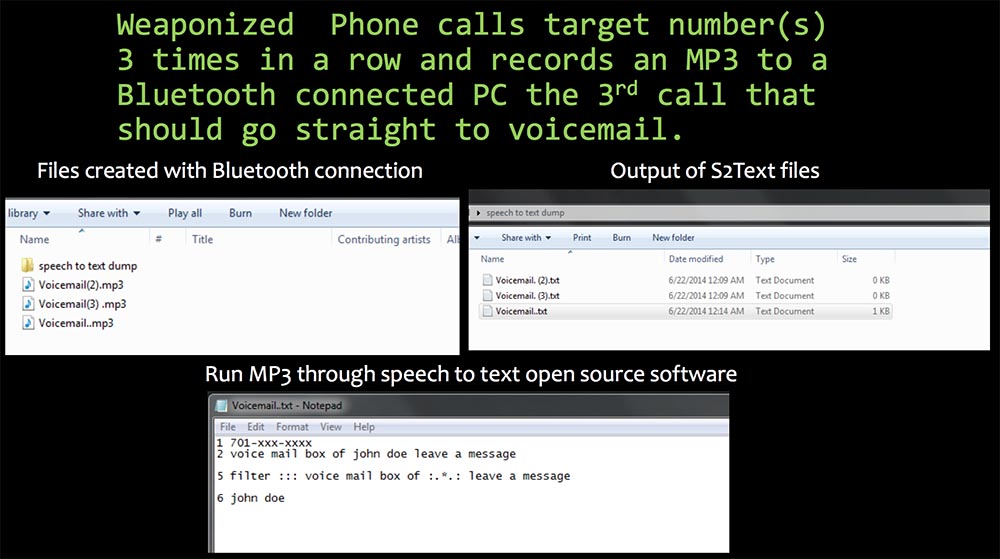
As I said, many people use War Dialing, for example, to determine the modem number and search for voice mail messages. My “charged” phone can also manage voice messages. He dials the target number or numbers 3 times in a row to activate voice mail, and writes a third ring .mp3 file to a computer that is connected via Bluetooth, so that this file is sent directly to voicemail.
The next slide on the left shows the call files created using Bluetooth connections, the right shows the S2Text text files that will be output, and below shows the process of turning the .mp3 file into an audio message using open text software.
Telephone script Program Bot will call and use the incoming information from the list to activate the corresponding service line.
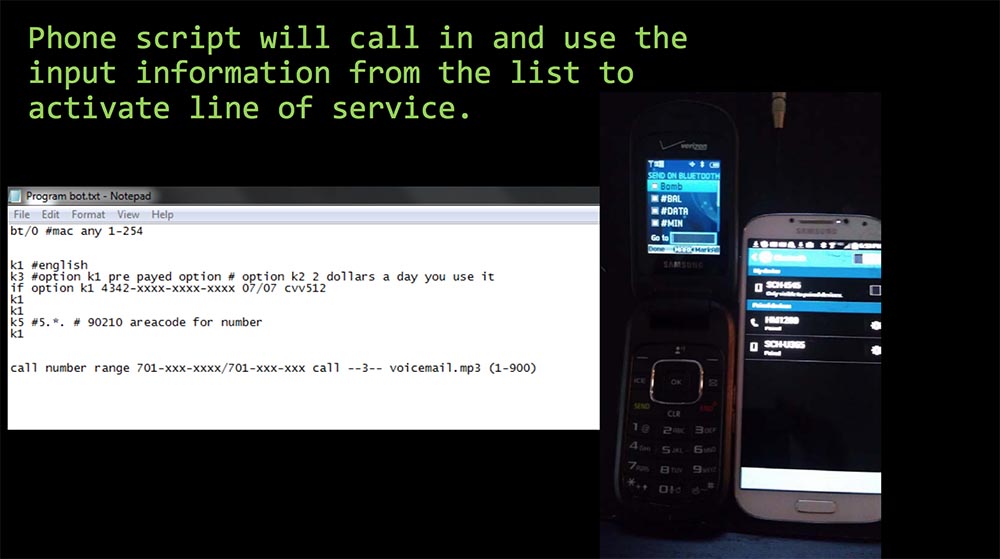
You can see that here you can use from 1 to 900 ringtones or up to 900 phone numbers to which you can call. The bottom line is not a program code, it's just my comment, which should not have been in the final slide for this presentation. The original version of this script looks like a spam letter from the Nigerian Mail. So if you need a current version of the slides, please contact me by email.
As a matter of fact, I added 2 possibilities to the program. The first is the ability to record anonymous .m3 messages for voicemail, the second is that for programming I can connect 5 phones to my computer at the same time and simply press a key to start the process. And this program provided my numbers with the prefixes of the state of Carolina phones, so that it could be used to send spam.

So, this prepaid cell phone, which prevents the reception of legal phone calls for 5 days, has the following properties:
The cost of the USB solar charger itself is only $ 6. The ringtone I wrote also ensured the minimum power consumption of the phone. The ability to “jump over” from the tower to the tower after a predetermined period of time ensured complete anonymity, in addition, I could forcibly fix the location and bind the phone, for example, to a cell phone tower in Las Vegas. The $ 2 daily plan for unlimited calls was for grandpas, and I don't know why Verizon changed it a month ago. However, you can use this tariff for "grandfathers" ESN numbers with other brands of Samsung cell phones having the same Brew OS, but the new version 1.151. It is very similar to the one with which I worked, but it has an updated security certificate. I think other methods of hacking such phones should be found, and my hacker set provides an excellent opportunity for this.
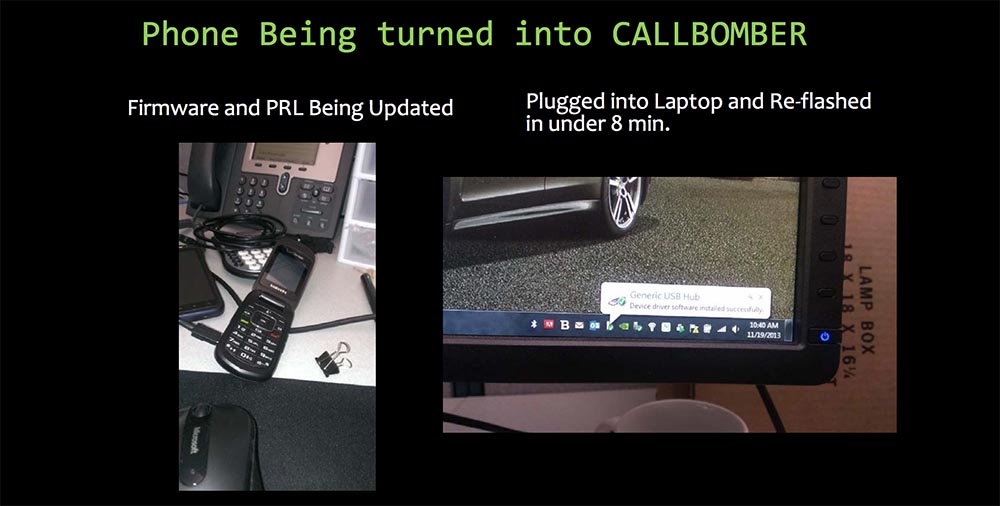
The next slide shows a phone that has been turned into a Callbomber Call Bomber. I updated its firmware and PRL using a special USB cable, connected it to the laptop and reprogrammed it in 8 minutes.
Next, the slide shows how I using the 10 phones with the “battle platform” brought down the virtual call center. The TDoS attack was carried out with an intensity of 12 calls per second over 210 lines of communication for 8 minutes and caused an overload of the processor and call center memory, which caused it to crash.
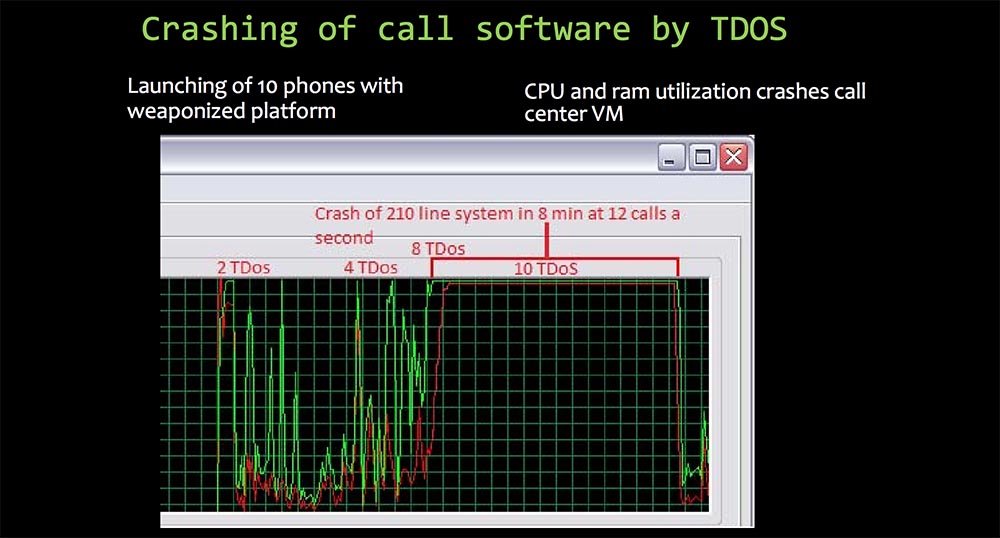
This is really a scary thing! I did this in order to attract the attention of people to this problem, because anyone can buy such a phone for $ 12, hack it and bring huge problems to others. It’s one thing when your web page crashes, and quite another when your call manager is blocked. These are different levels of problem. Many people do not think about it until the problem affects them personally.
Possible targets for TDoS attacks:
For the life support services of the population, TDoS attacks are a very serious problem. I live in a small state with about 600 thousand people, it “grew” a little because of the oil boom. And with us, blocking the 911 service can lead to dire consequences.
These attacks can hit stores, tax services, restaurants, taxi services, they can damage all existing US financial infrastructure. I’m afraid to imagine that someone will be able to release a wild beast TDoS, which can cause terrible damage for as little as $ 10.

And now I am ready to answer your questions.
Question:
- Do you have any ways to repel TDoS attacks by call centers?
Answer:
- Yes, I created plugins for Call Manager and Call Manager Express, they are designed to work with equipment and software CISCO, from which I, in fact, came. The plugin is designed so that after the third call it sends the captcha to the caller and does not accept the message until he dials this captcha on his softphone. Today I created 15 captcha.
Question:
- How about using new smartphones as a “battle platform”?
Answer:
- I don’t think that I would go for it, because they are not so cheap as to leave 10 smartphones in the public library and forget about them after they conduct a TDoS attack. I would not even have abandoned my old smartphone with Android, which passed into my ownership after a 2-year contract period. I actually used a “one-time” phone, primarily because of its cheapness. In addition, I needed the most compact platform with minimal power consumption. My phone could work up to 15 days without recharging in standby mode, so smartphones do not correspond to the tasks set for the “combat platform”.
Question:
- Why hasn't Verizon not attracted by the fact that some phone is trying to make 70 calls per minute?
Answer:
- Verizon Cell Towers do not exchange information with each other, so I don’t think there was a real opportunity to track such activity. But just in case, I made PRL allow the phone to periodically “jump over” from the tower to the tower in order to ensure anonymity and not attract the attention of the cellular operator.
Question:
- Have you tried to do this using text messages?
Answer:
- Yes, I completely unlocked the SMS function, so I could send the exploit not only using ringtones, but also completely anonymously via SMS. It is very cheap if you use the SMS sending service via a computer, so it’s realistic to create a “text bomber”. Text messages can be used not only for malicious attacks, but also in general for full control of the phone. I would be interested to see what the DEFCON community can do about it.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
My name is Weston Hecker, I penetration tester, studied computer science and geophysics, have tons of certificates, wrote several user exploits and scripts for PMS Hotel real estate management software and Internet providers, created several ISP devices, like the one about which I will tell today , as well as a number of devices for software testing.

')
I have been testing devices and security for over 9 years. I am the creator of the Fake iPhone Park series of hacking products that are better than the USB Rubber Ducky hacker device.

This is how my park of fake “iPhones” using the Teensy 3.0 compact platform with Arduino support looks like.

Have any of you used Rubber Ducky when testing for penetration or other vulnerability tests? It can be combined with Teensy 3.0 and inserted into the iPhone, and I have a plan for you how to use it. These pieces are sold for $ 7 each, and they work much better than the classic "ducks" with USB.
I also developed the Phone Call Bomber “Call Bomber” hacker device based on a Samsung prepaid phone that runs on solar energy and can be hidden, for example, in lamps of public libraries.
I also came up with an RFID scanner that is mounted under a chair or chair. It uses the Arduino platform with a three-axis gyro sensor. When a person moves in a chair, the scanner scans the data of a bank card in its pocket or purse. It does not work incognito, because it confirms the successful reading of the data with a sound signal.
And now I will tell you what the difference between DDOS and TDoS attacks is.
DDOS attack is an attempt to make a computer or network inaccessible to users. Depending on the motives and goals, these attacks may differ in the way they are implemented, but in any case they are aimed at disabling the host that provides Internet services.
A TDoS (Telephony Denial of Service) attack, or telephone service failure, is a stream of unwanted malicious incoming calls. These calls attack call centers or other customer services to make voice calls more difficult or impossible. In fact, people are deprived of legal services to call someone and talk with him by phone. This has happened over the past few years and has often been a manifestation of activism.

Most people nowadays do not use traditional analog telephone communication, they make calls via the IP network using the SIP protocol, that is, in fact, telephone communication is carried out via the Internet.
Most often, I have come across cases of TDoS related to banking fraud. Now the theft of a physical card does not attract thieves, they act more on the network. Let me give an example: if I use my credit card to pay at some gas station in Texas, the banking company Wells Fargo will definitely try to call me. Therefore, fraudsters are trying to use TDoS to attack the phones of people who own premium bank cards. Most cases of banking fraud occur in Los Angeles and California, where attackers are embedded in the telephone connection between call centers and existing banks.
Using a fake CID Called ID was one of the reasons I ended up here. A couple of years ago in the morning, just before I went to Minneapolis, I received 3 phone calls. I had a new number, so I assumed that these were calls to the previous owner of the phone, who used the service for missed calls. But when I called this number, it turned out that it has a fake Caller ID. This phone belonged to an elderly man from somewhere in Delaware and he said that he received about 140 such calls per day. People say that they received a call from him and asked what he wanted from them, and because of this he was going to change his phone number. Then I first thought about TDoS attacks.
So these attacks apply:
- fraudsters who carry out banking operations without physical cards on the principle of CNP;
- "Money mules", that is, fraudsters who transfer stolen money between different bank accounts or between different countries;
- using fake caller id CID;
- to attack call centers in order to prevent work with clients;
- in the form of protest activism to achieve political goals.
I know dozens of government agencies that receive a huge number of anonymous calls that paralyze their activities. This is a manifestation of political activism.
And now I will talk about the existing methods of TDoS attacks.

The first is called counter attack fake Caller ID, this is my own development, later I will tell about this in more detail. This is followed by malware on phones and call management software. I am sure that you have attended many DEFCON conferences where the use of malware for iOS and Android was discussed.
Then come PRI and SIP hacked services, which are used to make the so-called “War Calls”. War Dialing is an automatic scanning of the subscriber list and calling each number of the local telephone network to search for computers, BBS ad boards, faxes and modems.
My latest development is a script for uploading phone numbers of subscribers to existing web pages of realtors. It looks quite decent and does not require much effort.
Reflected attack fake Caller ID is to use a legitimate telephone service with fake information about the caller's phone number. Naturally, people who receive a call as if from this number, overwhelm the unsuspecting subscriber with thousands of callbacks, because they are sure that he was the one who called them. Using the application with a PRI server, we can generate 23 calls per minute to different subscribers who receive a fake caller's phone number. You can loop the list of phone numbers depending on which “dialer” is running on your computer. If you receive a message that the subscriber tried to call you 3-5 times, you call him back to find out what he wanted from you. In fact, you will call the phone number of a person who has not actually called you.

Today I will tell you how 15 phones could “collapse” 200 call centers.
Many people, including myself, do not call back to the specified number, because they believe that if someone could not get through to them, he would leave a voice message.
This is followed by a reception when real estate sellers are used to carry out a TDoS attack. To do this, use a script that places on the web pages of realtors fake customer information, automatically filling out the form on the page. About 76% of real estate sites use the same templates of the questionnaire without a “captcha”, so it is easy to fill out and submit such a form automatically. At the same time, the username and password required to fill out the form is generated very easily. Today, there are approximately 4,800 pages of realtors on the network, which the script can fill with fake information in 2 hours. For example, such: “I just sold my house in Nevada and am looking for something suitable in the area. Please, call me. John Doe.
As a result, a squall of calls from realtors falls on the phone indicated in the form.

There is also a botnet infected with smartphones. Smartphones, like computers, can serve as platforms for botnet networks. The increase in the number of "rutted" phones reduces their security and increases the risk of hacking.

I want to tell you how I developed a “combat platform” based on OEM cell phones.
Prepaid cell phones use OS Brew 3.1, CDMA 1x 800/1900 MHz communication technology, and the Samsung U365 model, known as Gusto-2, also supports digital services. This is a very common model, surely many of you had such a “clamshell”. The mobile phone operator Verizon can buy this phone for $ 8-12.

Here is the chip installed in it with a Qualcomm QSC6055 processor with a frequency of 192 MHz. My "combat platform" is compatible with all processors of the QSC60xx series.

In 2014, I conducted a study on who exactly uses prepaid phones, and got the following result:
- 60% of elderly parents;
- 30% of drug dealers;
- 8% of inept users;
- 2% of paranoid professionals in the field of security networks from DEFCON.
This chip has three security features built in: secure boot, secure boot, SEE and SFC. However, in the OEM version, that is, the version from the manufacturer, there is support for the normal boot mode of the phone, which unlocks the sets of functions, that is, makes it possible to get root-rights. In order to load my phone exploit, I created a pseudo-signature, with which the device “agreed” to work, as a result of which a recompiled operating system was loaded into the phone. The fact is that each manufacturer used its own OS, so I wrote a modified version of the OS that matched all phones with this chip.
This model is ideal for hacker experiments because of its price of $ 8, that is, it will not be a pity if, as a result of your manipulations, the phone turns into a “brick”. In addition, it allows you to use a large set of software from developers, which is written in C ++, so it is very easy to get the phone to work according to its own program.
Brew OS provides the ability to monitor voicemail and turn the device on or off using Brew applications. This feature exists by default if the user interface (UI) runs on top of Brew. The manufacturer provides the ability to change software parameters using the PST product support tool.
I used a lot of these phones to understand how it all works. I was lucky to find a team of talented Germans who eliminated my knowledge gaps and helped me to create an exploit for this phone. This is an amazing phone for someone who wants to learn how to hack cell phones.

It was designed in such a way that it is possible to use many additions and extensions for convenience. For example, you can use the battery saving mode, and then the screen of the phone while receiving calls will not light up. He has a very economical battery - when I was preparing for this performance, I often called the guys from DEFCON, and at the end of 7 days of use, there were 3 more bars on the battery charge indicator. You buy this phone from Verizon for $ 12-14, and it prepares calls for another $ 10, and then pay $ 2 every day for unlimited calls. This is a very convenient tariff plan.
The introduction of the IRinger Mgr exploit allows you to carry out manipulations with the phone, such as silently receiving a call, that is, the phone receives an incoming call without activating the ringtone and without having to lift the top cover. This is a very convenient attack feature. Brew allows you to use the IRinger Mgr interface to implement your own calling program in the OS. Thus, the exploit uses the operating system of the phone, which receives and processes incoming calls in the mode we need.
Folding phones have certain functions that report on a flip cover. On these phones, by changing media files, for example, ringtones, you can “bypass” triggers and events triggered by hardware, depending on the specific user action. Thus, using the OEM version of the device with the “factory” OS and the application compiled by me, you can “bypass” any factory function and interact with the phone as you please.
You can write your own ringtone with the desired payload, consisting of "wrong" packages. Thus, you can interact with the phone using the wrong packet generator or by downloading already modified ringtone. It was a modified executive file that allowed me to download the necessary firmware to my phone. For the software of this phone, the certificate expired in 2012, it has operated since 2006, that is, the phone has not been used for several years. The modified executive file allowed to bypass the phone’s security functions through the “hole” in the certificate validity period. The next slide shows how I managed to install the phone’s firmware through the Samsung PC Studio 3 proprietary software, ignoring the Windows warning about expired certificate by simply choosing “Install this software anyway”.

This error was used to launch a modified executable file, while other devices were installed with a driver that had a valid signature.

After updating the driver using a personal computer, it became possible to carry out a full-scale attack on the phone.

The next slide shows the certificate, which expired in 2012, which allowed me to bypass the settings of the security function.

Modified driver files allowed to modify all information about devices.

I note that I needed the drivers and the program for updating the firmware from the official Samsung website, where there were very outdated versions of this software. Perhaps this is one of the reasons why the phone is sold so cheaply. Again, I easily managed to do with this phone, everything I wanted.
Another remarkable feature of this "Samsung" is the formation of a preferred PRL roaming list, which determines which networks can use this CDMA phone. It shows which ranges and mobile networks should be scanned when turned on, and which of them should be given priority connection. He usually scans 12 cell towers, so he can use a triangulation method to determine the location of your house. You can fix 3 arbitrary towers and thus freeze the GPS position of the phone or disable position detection altogether, which will make it impossible to track the real location of the phone.

It is also necessary to modify the PRL for carrying out attacks, since with the GPS positioning function turned off, the attention of the cellular operator will not be attracted by the fact that someone needed to make 70 calls per minute from the same phone. Turning off the GPS function turned out to be very simple. I noticed that it is not fully restored until you make a call to 911. This looks like some kind of interaction with cell towers on an ongoing basis.
You can create an application for an attacking platform by emulating software using a platform emulator written by OEM hardware developers. That is, having a completely open "native" platform, you can create on its basis its own "combat" platform. At the same time, the application can be tested without even downloading it to the phone.

While testing my platform, I broke several phones. By the way, one of the reasons why I wrote my ringtone with a malicious package was the desire to break the phone with the help of a ringtone.
With the attack platform loaded onto the phone, you can gain complete control over its functions, such as TDoS or Brickmode. First you need to download a ringtone that carries a specific “payload”. Installing this ringtone, which I called Callbomb, as a ringtone for a call, launches the malicious functionality of the ringtone in relation to its associated event. That is, I installed this ringtone on my phone and sent it to the phone number I wanted to possess, and he started calling the numbers indicated in the text message with an intensity of 70 calls per minute. The calls continued until the battery was completely discharged. This is an extreme number of calls in the shortest amount of time that cannot be traced.

To complete the five-day cycle of "bombing calls," I set the alarm, and he disabled the phone. If someone was more experienced in programming and had more time, he could arrange something like a “flash” that would destroy the phone software so that it could not be restored. Thus, with the help of my technology, you received full access to the phone itself, its modules and interfaces.
Do any of you know what CheeseBox is? This is an "old school" term associated with bookmaking. For example, a bookmaker rented an unused apartment or store in which he installed several telephones and an electronic device called CheeseBox. The player called the number of one of these phones. When the phone took the call, CheeseBox automatically converted it to an outgoing call to the bookmaker’s phone, which was on a completely different line. Thus, the player never knew the real telephone number of the bookmaker. This technique is used by people who want their phone number to remain anonymous.

I wrote a ringtone pack that helped me deliver other ringtones. He provided a Bluetooth connection with other phones and made it possible to redirect the phone call. Suppose I made a call to the number I needed and after some random amount of time (it was possible to set the timer for 5-15 s), my phone "belonged" to another cell phone tower. It was possible to have at the same time 2 phones, each of which was tied to its tower. The technology was as follows:
- you call one number;
- Your call arrives on the second phone via Bluetooth;
- The second phone dials the number you need, creating the nearest untraceable proxy.
Thus, the absolute anonymity of your phone was ensured. People may need it for a variety of reasons.

You can connect via Bluetooth up to 3 phones at the same time in order to make random outgoing calls.
As I said, many people use War Dialing, for example, to determine the modem number and search for voice mail messages. My “charged” phone can also manage voice messages. He dials the target number or numbers 3 times in a row to activate voice mail, and writes a third ring .mp3 file to a computer that is connected via Bluetooth, so that this file is sent directly to voicemail.
The next slide on the left shows the call files created using Bluetooth connections, the right shows the S2Text text files that will be output, and below shows the process of turning the .mp3 file into an audio message using open text software.

Telephone script Program Bot will call and use the incoming information from the list to activate the corresponding service line.

You can see that here you can use from 1 to 900 ringtones or up to 900 phone numbers to which you can call. The bottom line is not a program code, it's just my comment, which should not have been in the final slide for this presentation. The original version of this script looks like a spam letter from the Nigerian Mail. So if you need a current version of the slides, please contact me by email.
As a matter of fact, I added 2 possibilities to the program. The first is the ability to record anonymous .m3 messages for voicemail, the second is that for programming I can connect 5 phones to my computer at the same time and simply press a key to start the process. And this program provided my numbers with the prefixes of the state of Carolina phones, so that it could be used to send spam.

So, this prepaid cell phone, which prevents the reception of legal phone calls for 5 days, has the following properties:
- This is an anonymous purchase.
- using this phone costs $ 2 per day;
- it can not be traced;
- It can be charged using a solar charger;
- it can generate random PRL lists showing the false location of the phone;
- hides easily inside lighting fixtures in public places and is recharged from light bulbs;
- The total cost of providing a 5-day TDoS attack when using solar charging is $ 20.
The cost of the USB solar charger itself is only $ 6. The ringtone I wrote also ensured the minimum power consumption of the phone. The ability to “jump over” from the tower to the tower after a predetermined period of time ensured complete anonymity, in addition, I could forcibly fix the location and bind the phone, for example, to a cell phone tower in Las Vegas. The $ 2 daily plan for unlimited calls was for grandpas, and I don't know why Verizon changed it a month ago. However, you can use this tariff for "grandfathers" ESN numbers with other brands of Samsung cell phones having the same Brew OS, but the new version 1.151. It is very similar to the one with which I worked, but it has an updated security certificate. I think other methods of hacking such phones should be found, and my hacker set provides an excellent opportunity for this.
The next slide shows a phone that has been turned into a Callbomber Call Bomber. I updated its firmware and PRL using a special USB cable, connected it to the laptop and reprogrammed it in 8 minutes.

Next, the slide shows how I using the 10 phones with the “battle platform” brought down the virtual call center. The TDoS attack was carried out with an intensity of 12 calls per second over 210 lines of communication for 8 minutes and caused an overload of the processor and call center memory, which caused it to crash.

This is really a scary thing! I did this in order to attract the attention of people to this problem, because anyone can buy such a phone for $ 12, hack it and bring huge problems to others. It’s one thing when your web page crashes, and quite another when your call manager is blocked. These are different levels of problem. Many people do not think about it until the problem affects them personally.
Possible targets for TDoS attacks:
- 911 service lock;
- block incoming emergency calls;
- federal agencies during terrorist attacks;
- shops during the holiday sales season;
- any person or organization that you don’t like.
For the life support services of the population, TDoS attacks are a very serious problem. I live in a small state with about 600 thousand people, it “grew” a little because of the oil boom. And with us, blocking the 911 service can lead to dire consequences.
These attacks can hit stores, tax services, restaurants, taxi services, they can damage all existing US financial infrastructure. I’m afraid to imagine that someone will be able to release a wild beast TDoS, which can cause terrible damage for as little as $ 10.

And now I am ready to answer your questions.
Question:
- Do you have any ways to repel TDoS attacks by call centers?
Answer:
- Yes, I created plugins for Call Manager and Call Manager Express, they are designed to work with equipment and software CISCO, from which I, in fact, came. The plugin is designed so that after the third call it sends the captcha to the caller and does not accept the message until he dials this captcha on his softphone. Today I created 15 captcha.
Question:
- How about using new smartphones as a “battle platform”?
Answer:
- I don’t think that I would go for it, because they are not so cheap as to leave 10 smartphones in the public library and forget about them after they conduct a TDoS attack. I would not even have abandoned my old smartphone with Android, which passed into my ownership after a 2-year contract period. I actually used a “one-time” phone, primarily because of its cheapness. In addition, I needed the most compact platform with minimal power consumption. My phone could work up to 15 days without recharging in standby mode, so smartphones do not correspond to the tasks set for the “combat platform”.
Question:
- Why hasn't Verizon not attracted by the fact that some phone is trying to make 70 calls per minute?
Answer:
- Verizon Cell Towers do not exchange information with each other, so I don’t think there was a real opportunity to track such activity. But just in case, I made PRL allow the phone to periodically “jump over” from the tower to the tower in order to ensure anonymity and not attract the attention of the cellular operator.
Question:
- Have you tried to do this using text messages?
Answer:
- Yes, I completely unlocked the SMS function, so I could send the exploit not only using ringtones, but also completely anonymously via SMS. It is very cheap if you use the SMS sending service via a computer, so it’s realistic to create a “text bomber”. Text messages can be used not only for malicious attacks, but also in general for full control of the phone. I would be interested to see what the DEFCON community can do about it.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/354858/
All Articles