Too many cooks, or hacking the Internet with TR-069
Shahar Tal: let's take a quick vote - which of you saw the series “Too many cooks?”. A good percentage for such an audience. So, let's begin.

The screensaver of the film is shown on the screen, then portraits of speakers appear.
')

Further in the credits are indicated:
Denis DeVito - as an affordable IPv4 toaster, Arnold Schwarzenegger - as a TP-Link TD-W8961ND router, and others ...
So, for those of you who have not seen the movie “Too Many Cooks,” which was shown a few months ago, we advise you to watch it, we really liked it. If you watched it, you could appreciate our “funny pictures” that we used for the presentation.
So, we are researchers of malware and vulnerabilities and work in the company - the developer of programs in the field of IT-security CheckPoint, located in Tel Aviv. The slogan of our company - "We protect the Internet." Our task is to find the vulnerability of the equipment, tell the manufacturer about it and share information with the public.
Today we will talk about the following:
So, TR-069 is the specification No. 69 describing the CPE WAN control protocol (CPE is the equipment installed at the customer’s premises, your home router, the WAN is an extensive Internet network with a large number of computers). Version 1.0 of this specification first appeared in 2004 on the Broadband Forum from a group of companies developing broadband standards. There were several revisions of this specification, but remember that it was developed almost 10 years ago. Version 1.4 (Amendment 5) appeared in 2013, it is possible that the 6th amendment of this specification will be released in 2015.
This is what ISPs use:
The next slide shows how the work session for this specification looks like.
The CPE user equipment is located on the right — your home router with the TR-069 client, on the left is the TR-069 server, also called the ACS automatic configuration server. They “talk” to each other using SOAP RPS using XML over HTTP.
A session is always initiated by a router; this is a single IP connection by which the computer connects to the network. ASC uses the connection request and sends the command “get the parameter values” and “set parameter values” to the router.
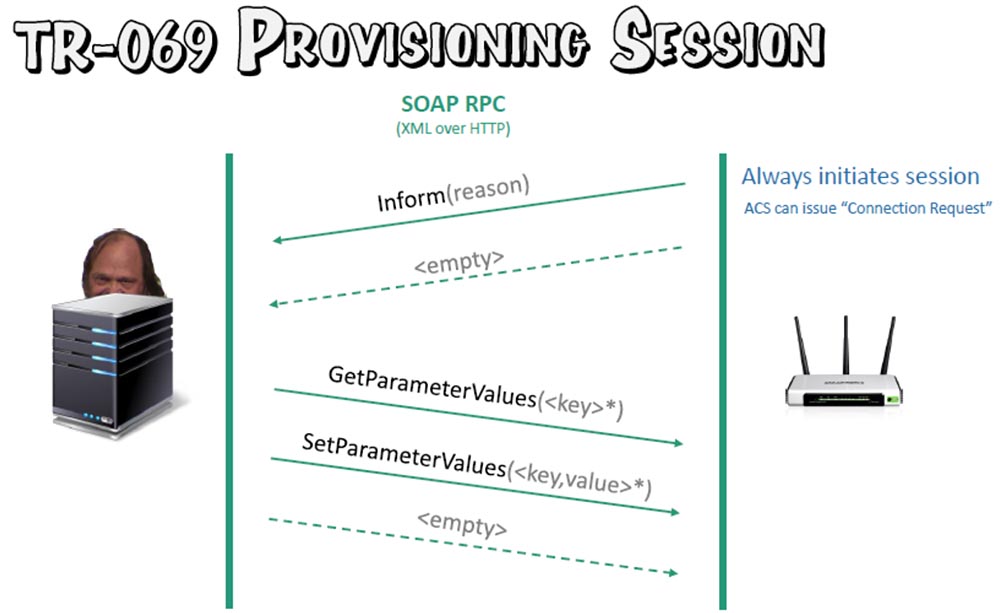
As you can see, this is quite simple. A double authentication mechanism is involved here. The CPE must ensure that it is communicating with your trusted ASC, and the ASC only allows an authorized user to session.
At DEFCON 22, we talked about what we found in the process. Our study found deficiencies in the implementation and configuration produced by many ACS servers of network providers (ISPs):
Here is an excerpt from the TR-069 specification regarding the Connection Request: “ACS can at any time request that the CPE initiate a connection with it using the notification mechanism of the connection request. Support for this mechanism is mandatory for the CPE. ” In fact, this means that all TR-069 clients all over the world are also the connection request server on the port that we request, and for all TR-069 this is the same port 7547, it is used by default.
Last year, the Dead Map guys did a very interesting study, it was Zachary Rumrich and his friends from the University of Michigan. They scanned 2 million random addresses on each of the nearly 10,000 ports, and determined that the CWMP 7547 — the default port for TR-069 — is the second most popular open port in the world. The percentage of its use of the Hit Rate for the Internet is 1.12%. Let me remind you that this protocol was created 10 years ago - think about it! Approximately 45 million devices use this port to communicate with the Internet, and they can be “listened” through this open port.
We will conduct a brief overview of the most popular ports in the world, which various devices use to communicate with the Internet.

Approximately 70 million devices use port 80, half for connecting to the web servers of the global Internet. Most of them are Apache servers, followed by nginx servers, IIS 8, and others. The second half of the devices uses port 80 for the Internet of Things. These devices are routers, webcams, VoIP phones and toasters.
Now people are finally beginning to realize that open access to these things is simply dangerous. Therefore, they are looking for as many devices as possible that use only port 80 for local networks.
Consider that the open port 7547 is used not only by ordinary users, its use is provided by the software of the servers of the providers interacting with the devices of the users. And all 45 million devices using TR-069 are the Internet of things.
All these devices go online using the Connection Request.
We decided to investigate security issues and find the number of people affected by this vulnerability. We had to stop guessing and move on to the facts. Last month (November 2014) we scanned ports 7547 several times around the entire IPv4 address space with the help of our friends Rapid 7 and the guys from the University of Michigan. As a result, after a simple “slash” input (/) via port 7547, we received 1.18% of all public Internet devices, the total number of which was 46,093,733 worldwide. That is, it is not one country in which these ports are open, it’s 189 countries around the world.
If you remember, there is a requirement in the TR-069 specification that this port is open for ASC requests. So, last year another 0.06% of new devices appeared that met this requirement, and that’s as much as 2.2 million! That is, the growth trend is evident.
We dealt with the problem of implementing the TR-069 on the client side and what statistics we received.
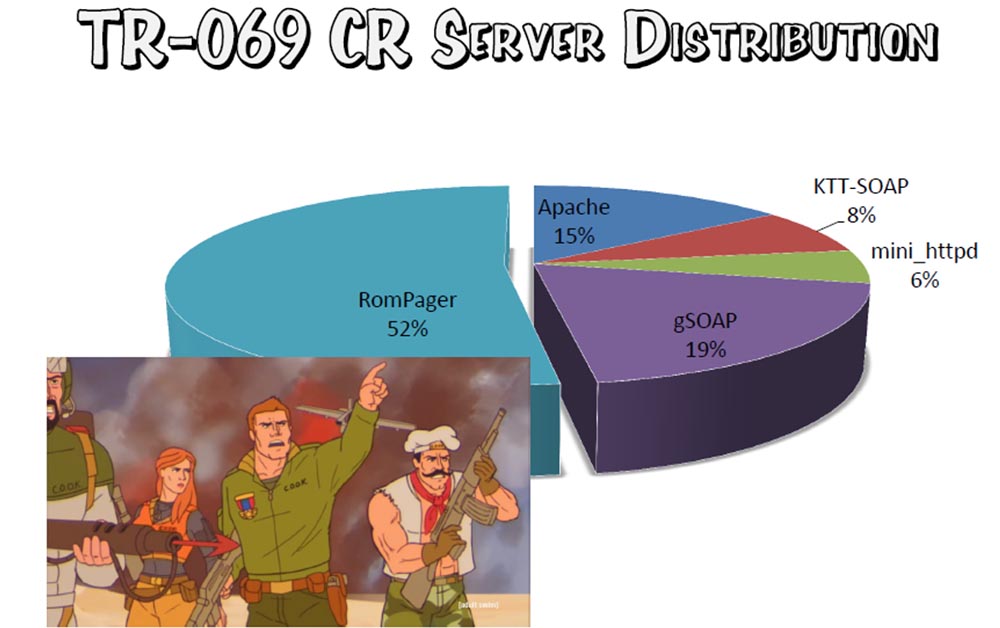
We have 5 main types of servers using the connection request. More than half fell on a piece called RomPager. This is a built-in HTTP server from Allegro Software, a Massachusetts-based company that is included in the firmware of most routers. It is optimized for minimum requirements - binary codes, minimum memory - and was first introduced in 1996. Since then there have been many versions, the latest is 5.4. We decided to focus on it and found that the client’s equipment uses four versions of RomPager.
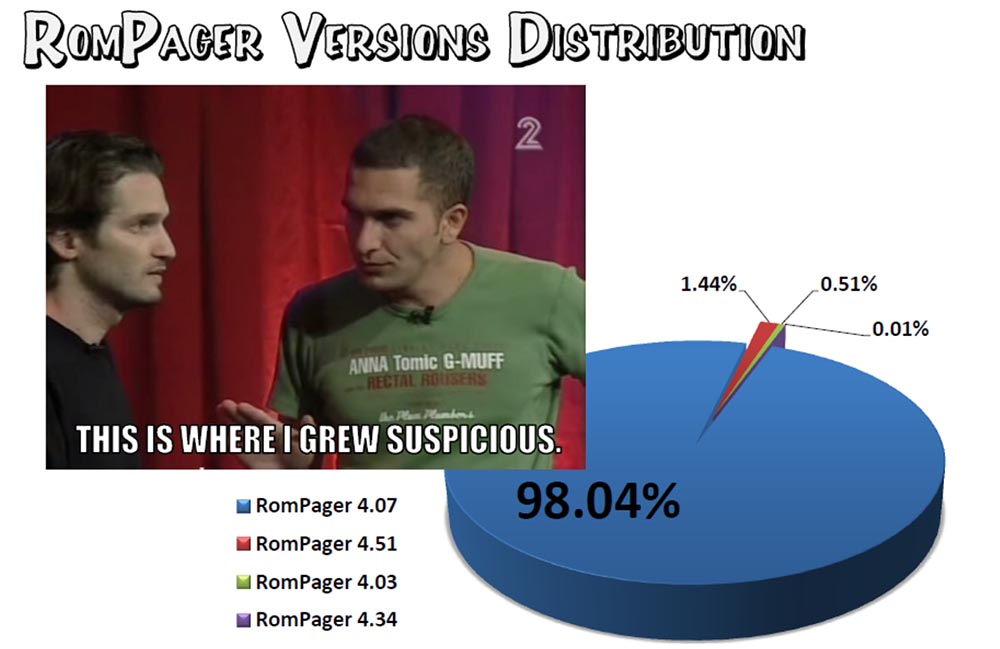
As a result, we found that 98.04% of devices use the outdated version 4.07, 1.44% use version 4.51, 0.51% - 4.03 and 0.01% 4.34. As stated in the series, “after that I became suspicious.” What explains the incredible popularity of the only version of RomPager?
We bought a new TP Link router, unpacked it and connected it to the network. It was installed RomPager 4.07. We thought that maybe this is an old router with outdated firmware and downloaded the new firmware of 2014 from the TP Link site, updated the router and restarted it, and as a result got version 4.07 again.
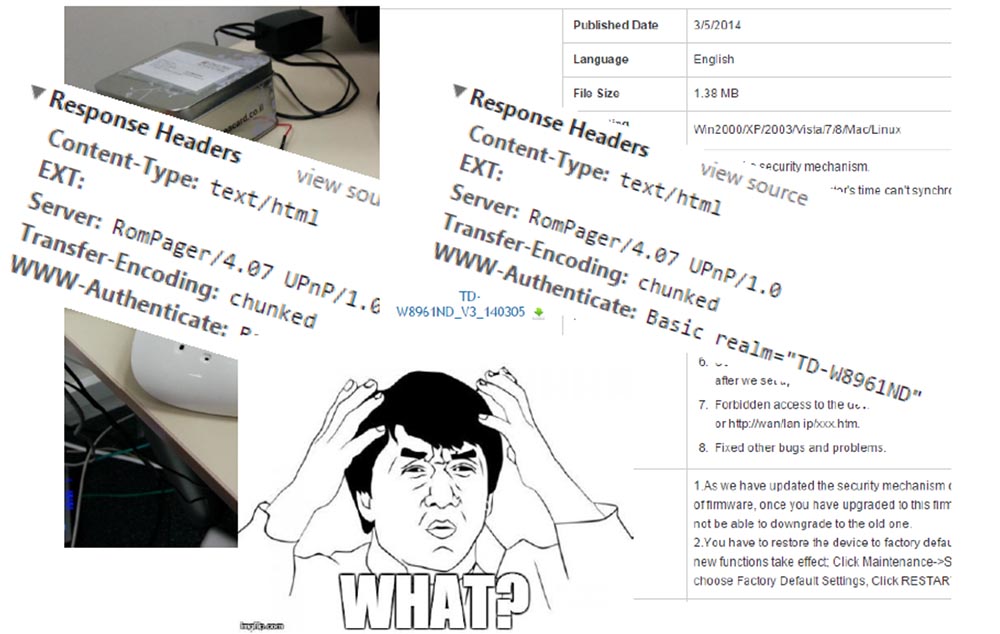
Thus, we received an explanation of the popularity of the old version - it was the only latest version of the firmware, located on the websites of the manufacturers of routers.
Who is present here has an unpacked new router? It can not be that good luck!
The guy from the hall passes the box with the router, and the speaker puts it on the table.
I assure you, this man does not work for me! We will deal with this box later.
We decided to explore what RomPager version 4.07 is. It was released in 2002 and has appeared in a variety of modern devices:
The study involved 200 different device models of more than 50 different brands. So, more than 11 million routers use an extremely outdated version of the built-in server, released in 2002, for the modern Internet. This is an excellent candidate for researching equipment vulnerability.
A very important point is that the most popular versions of the specifications are available on the Internet in the public domain.
And now let Lior continue - he will tell about how we analyzed this firmware.

Good day! My name is Lior and I analyzed how RomPager version 4.07 works and found interesting results. We had a proprietary firmware downloaded from the manufacturer of the TP Link router manufacturer. It looked like a compressed array of data, so we used Binwalk, a tool to search for files and executable code in this binary image. It is used to hack the archive and extract packed files.
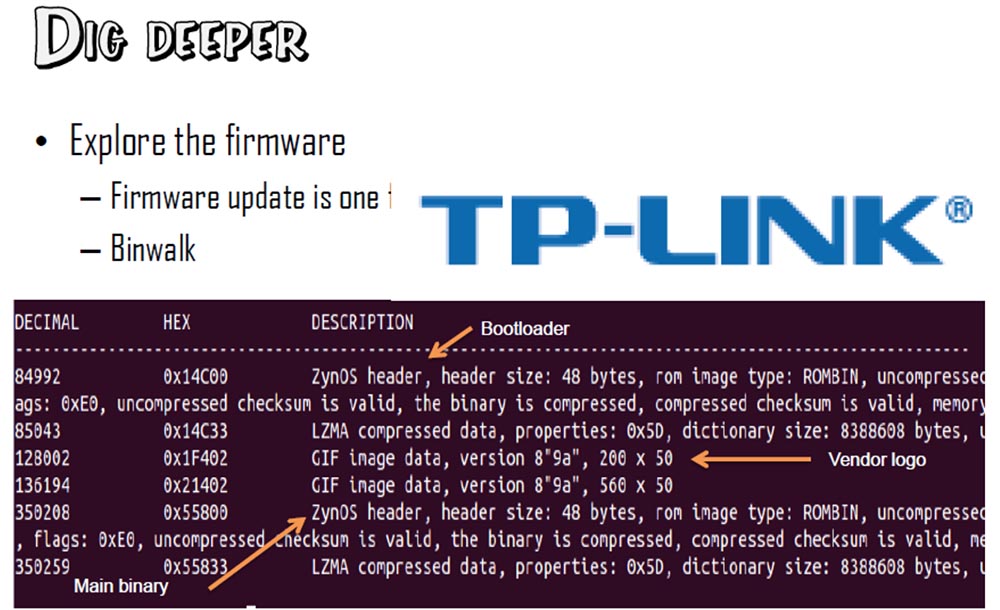
So, inside the firmware, we found the Bootloader loader, the manufacturer's logo in .gif image format and the main binary code Main binary.
For a more objective analysis, I decided to download all the RomPager firmware version 4.07, which I could find on the Internet, and found that they all contained the ZyNOS (mipsb32) header - an operating system that uses ZyXEL network devices. I could not understand why devices from different manufacturers had the same firmware. I began to study what ZyNOS is.
This is the main real-time operating system - Real Time OS, RTOS, without any file system and special permissions, it consists of one large binary file designed to meet any requirements.
This system has the known rom-0 vulnerability (VE-2014-4019). As of May 2014, 1,219,985 devices worldwide had this vulnerability. This vulnerability allows an attacker to take control of the router by simply downloading the configuration file from it without any authorization, directly from the web browser panel through port 80. As a result, the attacker will simply receive the password and username. And this vulnerability affects 1.2 million devices worldwide.
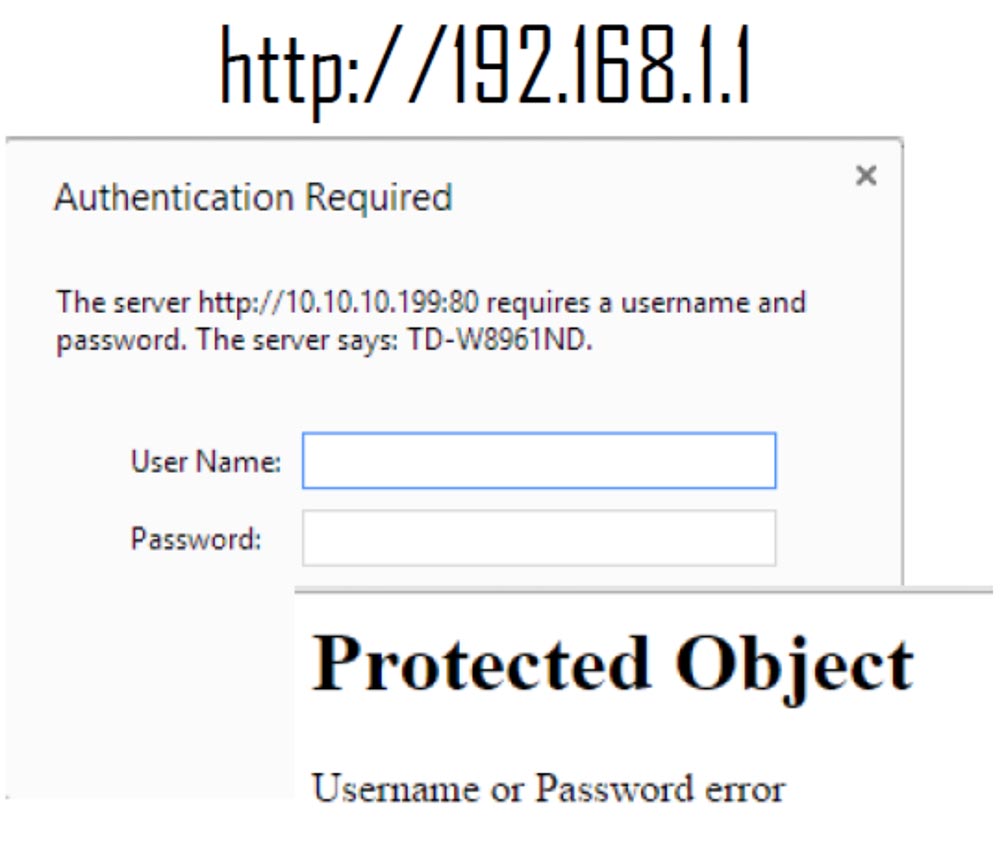
Consider what the interface of the attack through port 80 looks like. We received an authorization request, and since we did not know the username and password, we tried to enter through port 7547.
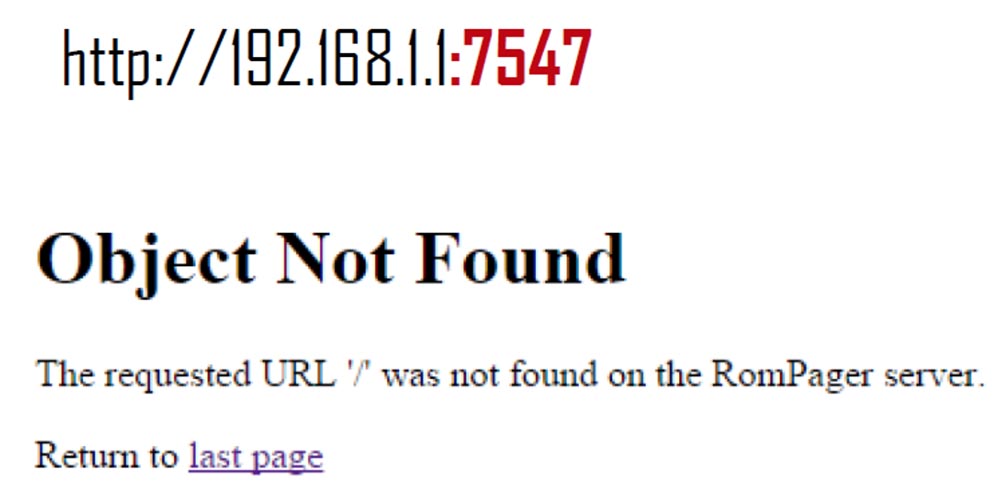
Here we received a message that at the given address “Object not found” for any path other than the correct address.
I decided to find the correct address, that is, to send a request on the right path. Before starting to deal with the code, I decided to perform manual testing via HTTP headers, and suddenly I managed to hack the router by sending the user's digest name with the overflow of the digest authentication header with the value of 'a' # 600.

This led me to the first vulnerability. To understand why this happens, let's look at the structure of the RomPager code. Each line here consists of an HTTP header and its manufacturer’s function to process this header.
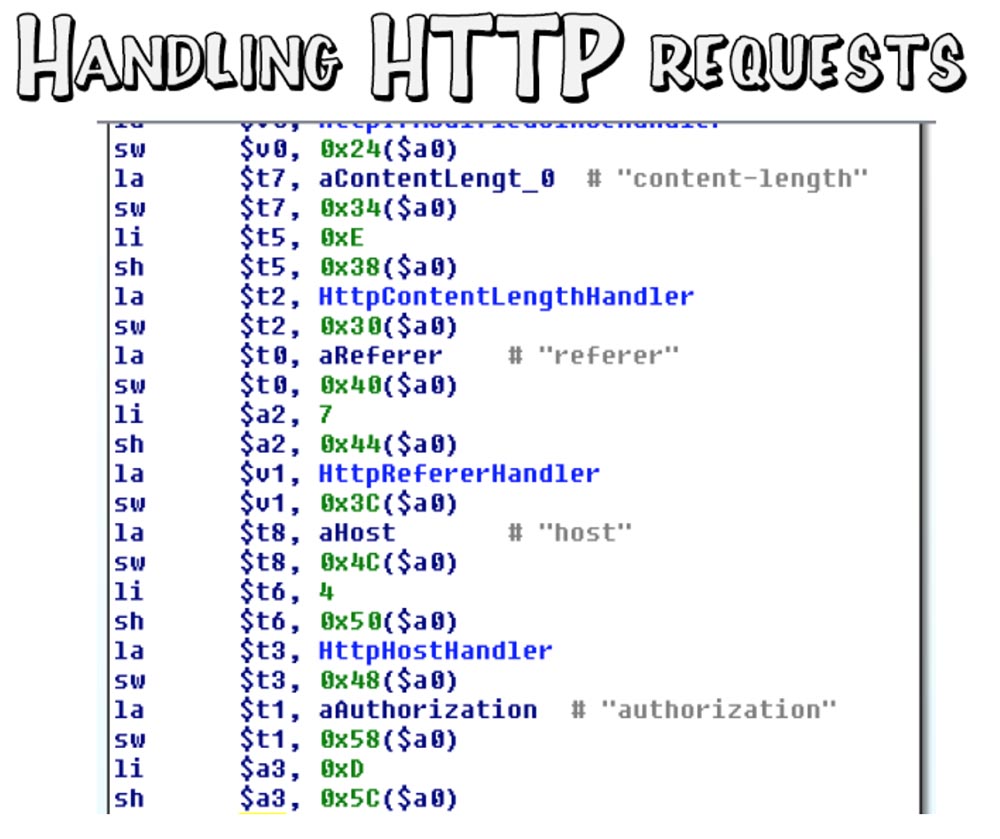
Consider the function that is responsible for the username.
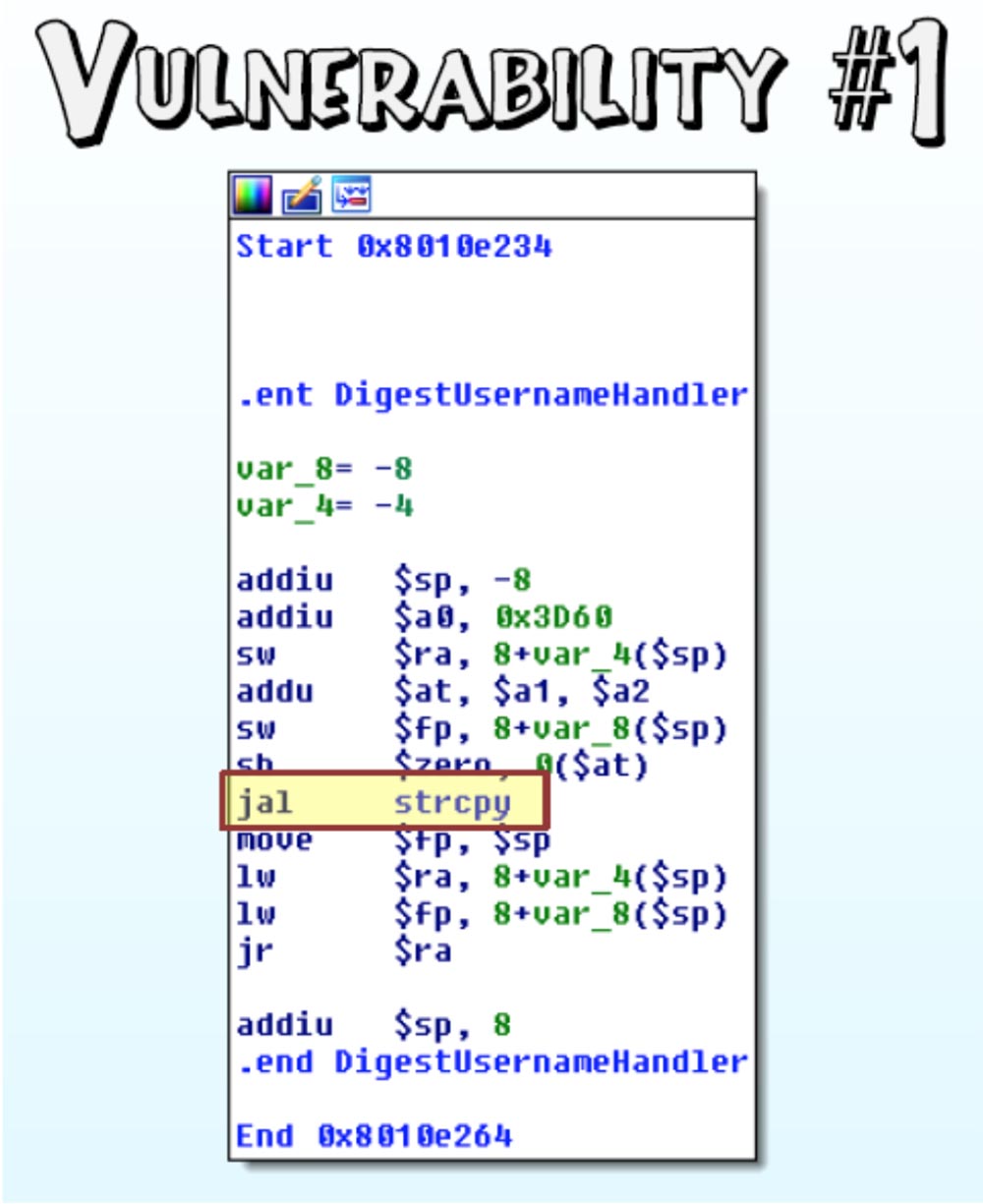
You can see what causes this vulnerability - this is unprotected strcpy, a standard library function for copying a null-terminated string (including a null-terminator) to a buffer. But what really leads to the possibility of hacking a router is the lack of symbols and the possibility of dynamic analysis. It is very difficult to understand.
I opened the router and began to look for JTAG. For those who do not know what it is, I will explain: JTAG is an interface for debugging and testing firmware. But when I took off the case, I didn’t find any JTAG connectors there, but I found something that looked like a U-ART serial port on a separate chip - a connector designed to communicate with other digital devices.
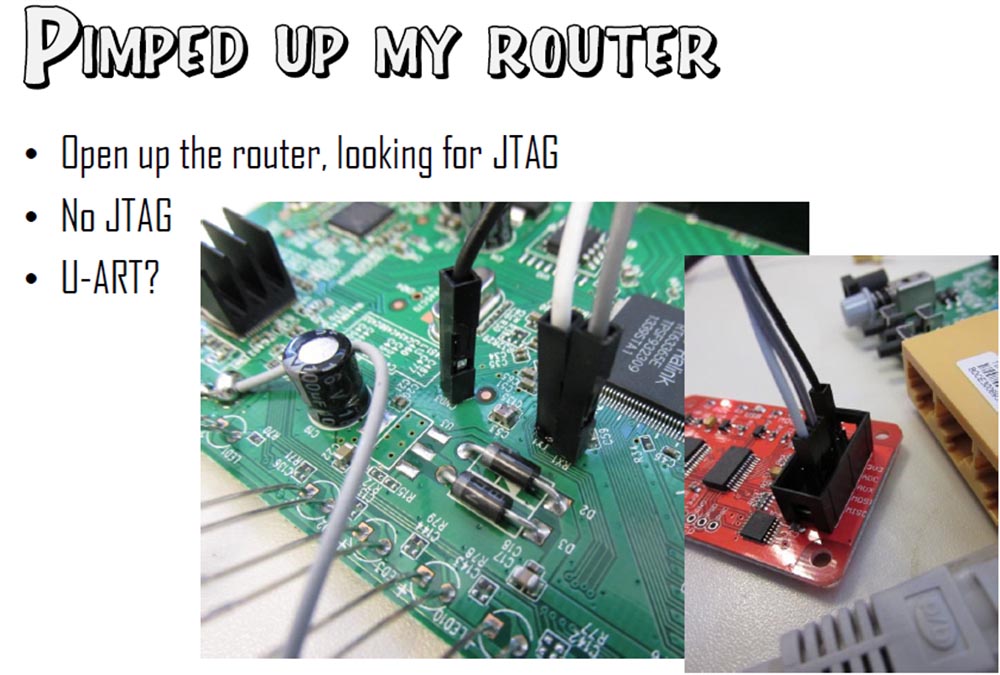
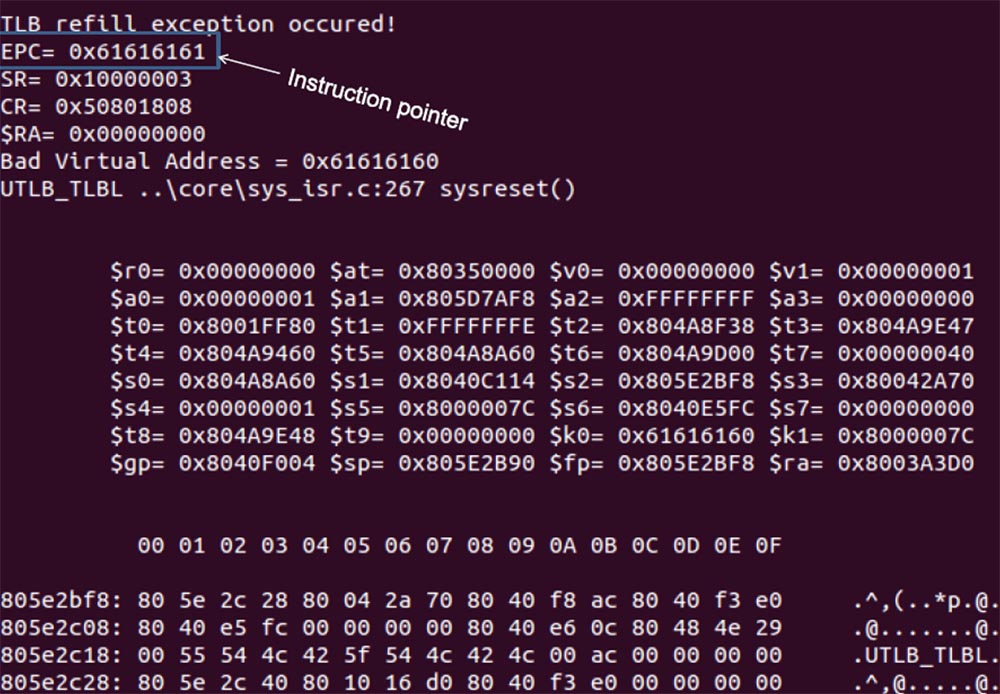
I went in for soldering and connected it to the router itself, and then through the USB adapter I connected this U-ART to my computer. When I loaded the router, I found a very good opportunity to debug the router. I'll show you what I got after hacking the router - this is a very nice crash dump with all registers and stacks, indicating the cause of the emergency recording - “TLB overflow”. At the top is a line of EPS - a pointer to the instructions for the MIPS microprocessor. As you can see, it is rewritten by me, and this means that I control the router. Further analysis of the crash dump made it possible to fully determine the cause of the vulnerability.
So, unprotected strcpy allows you to completely rewrite the EPC, which consists of 584 hexadecimal bytes, conveniently located after the user name, so hacking the router is very easy.
This is the number 1 exploit:
The difficulty of this method of hacking is as follows:
Theoretically, these problems can be circumvented by attempting to inject shellcode through another router information leakage vulnerability. Let's see how it works.
Since I did not have full debugging capabilities, I used the debugging option for the “beggars”, using the primitive debugging capabilities built into the RomPager itself, via the serial port. This made it possible to patch the firmware before downloading it, which was quite convenient, but very tiring.
After several reboots, I found the hidden feature of the ZyNOS operating system, which allowed access to the memory of the router via the Internet. This is ZynOs Remote Debugger, or ZORDON. This feature allows you to create control points, view and edit memory, read and rewrite registers online.
Let's look at vulnerability # 2.
If you remember, there is no dynamic allocation of memory, so each incoming HTTP request fills in a pre-allocated “request structure”.
RomPager 4.07 handles up to 3 parallel requests (3 pre-allocated structures).
When sending 3 consecutive requests, one of them can rewrite the HTTP structure that we saw earlier. This also became possible due to the unprotected strcpy, and we again took control of the EPC.
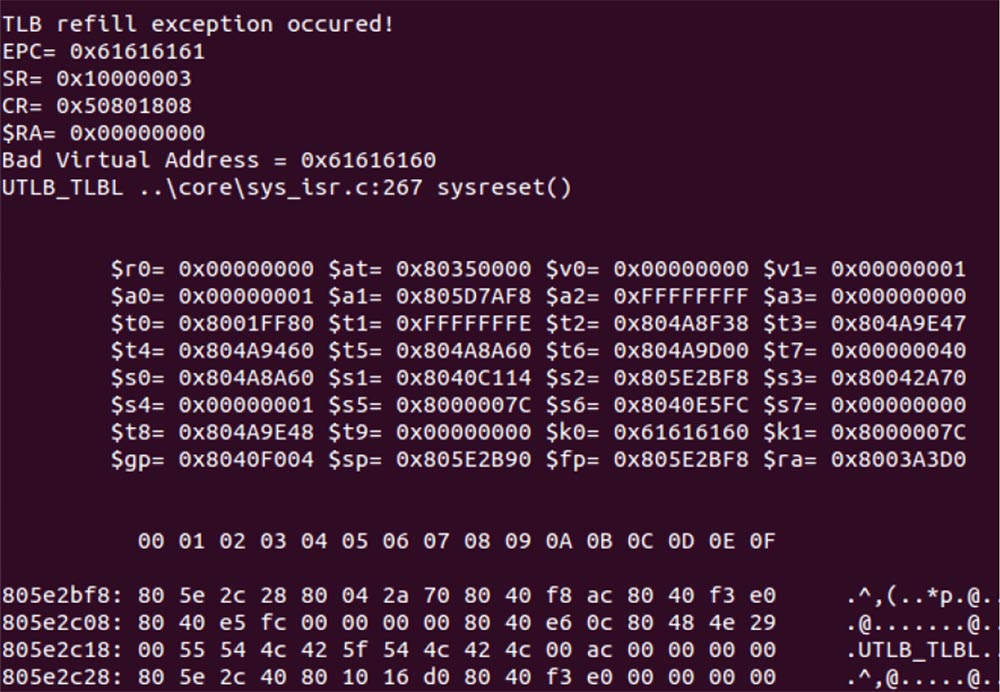
So, what is the exploit number 2?
Move to vulnerability number 3.
RomPager supports cookies. As you remember, there is no dynamic memory allocation, so there is a preliminary memory allocation for each array of cookies, a total of 10 pieces, each 40 bytes long. The names of cookies are constant - from 0, 1, 2 ... 9. The next slide shows what C0 looks like.

Let's see how RomPager steals cookies, that is, it processes cookies. At the top of the slide, you can see that he first checks the name of the cookie with a capital letter at the beginning. If so, it converts the rest of the name "cookies" into an integer and uses it as an index for the array "cookies".
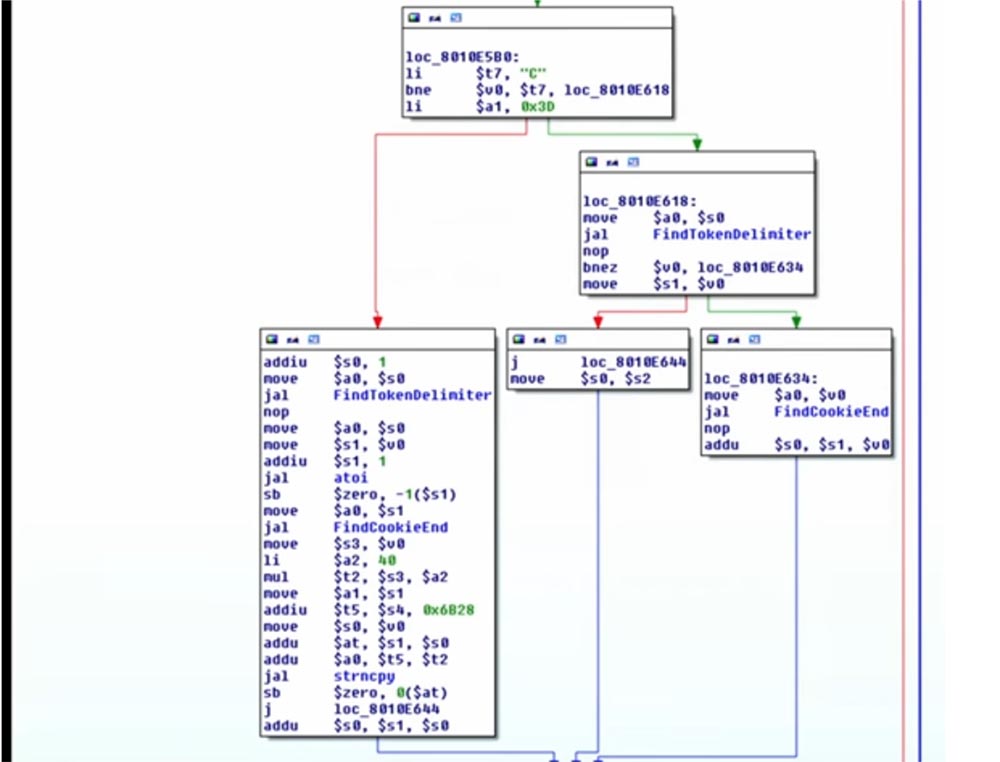
Next, it loads it, multiplying by s3, it will be an index for 40, and uses it at the strncpy destination.
Thus, vulnerability # 3 is as follows.
By performing an arbitrary write to the memory of a fixed point in the internal management structure of the RomPager, we gain control over everything that the RomPager does. At the same time, an additional bonus is the ability to overflow the 32-bit integer value in order to adversely affect the infrastructure.
If we send any “cookies” instead of C0, C1 and so on, we get the following answer:
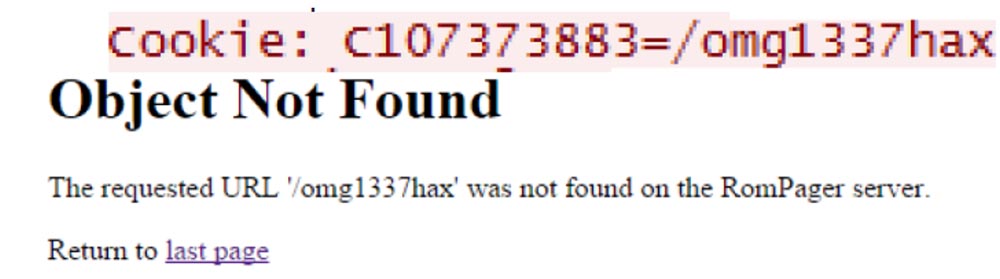
This technique works on any model of routers of any brand, to which we have obtained legal access. Thus, exploit # 3 is as follows: using several magic cookies added to your request, you bypass any authentication and view the configuration interface as an administrator through any open port.
Let's see a demonstration of what has been said - we have a video of our actions. We start the Internet browser and in the address bar enter the IP address of our router and the request for authorization. If you register in the line: 7547, then we get the message shown earlier.
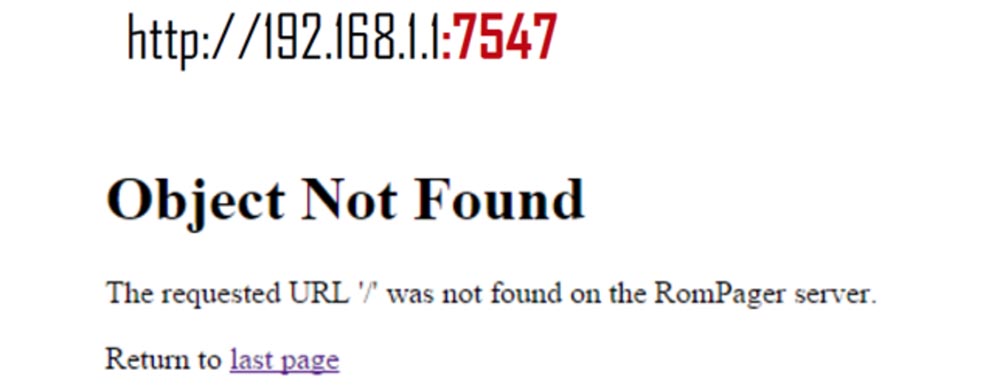
Therefore, we use “our” Chrome browser plugin, that is, the exploit we have built in, its icon is located to the right of the browser’s address bar (the plugin is called “Take all these things!”).
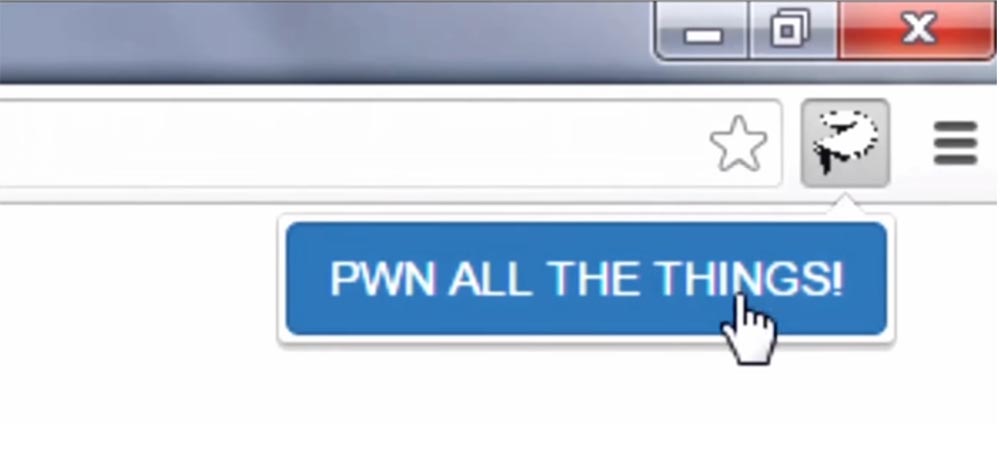
Click on the icon to activate this plugin.
It takes literally a second, and the TP-Link router settings window opens in front of us. We bypassed the authorization process!
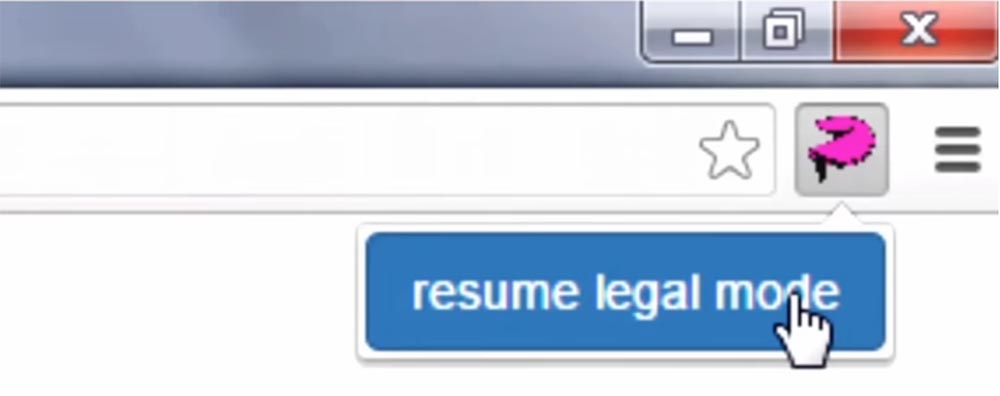
Then you can click on the plugin again to restore the legal mode.
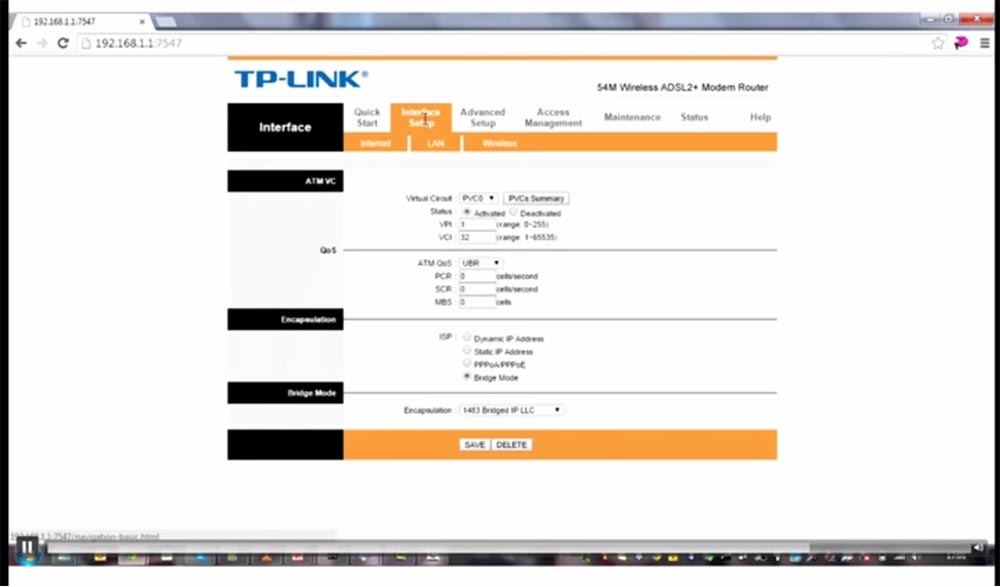
Let me show you again how it works: enter the IP address of the router 192.168.1.1 into the line, refresh the page when the plug-in is connected ... it did not work ... try updating again - that's it! We went to the settings page of the router without any authentication request, the window for entering the user name and password did not appear at all.
I repeat once again: we now have a new router connected from the manufacturer, right out of the box, released in 2014, and it is subject to the same vulnerability that was discovered and described more than 10 years ago.
Let's return to our presentation. We placed on this slide a link to the site where the information on the essence of the problem described by us is posted.

This map shows which countries are affected by this vulnerability. These are 189 countries worldwide and over 52% of all IP addresses.
I know what you just thought: you need to immediately abandon the use of port 7547 on your devices to access the Internet. But even if you try to deactivate the CWMP function in the settings of the router, port 7547 will still remain open.
You can counter this as follows:

Consider how the process of production of routers.
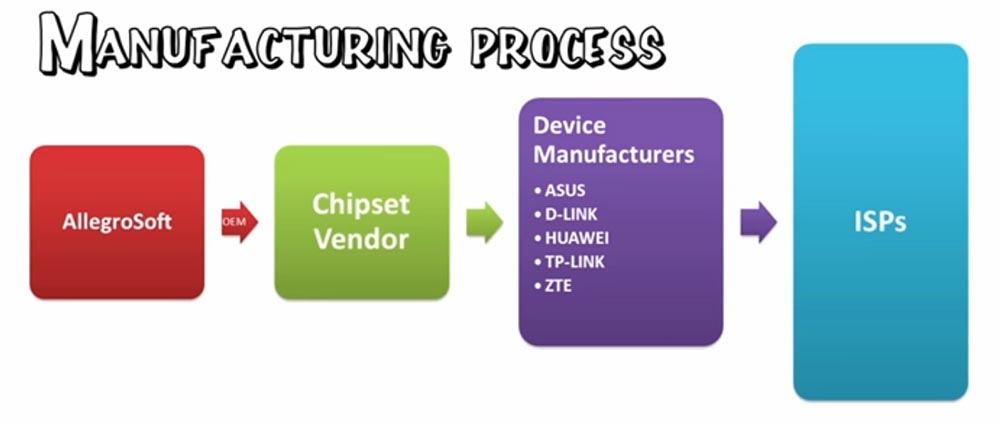
Allegro Soft supplies RomPager to the chipset manufacturer, which is sent to the manufacturers of ASUS, D-Link, Huawei, TP-Link, ZTE routers. Those adapt the software to different models, insert their logo into the firmware and sell the ready routers to the end user of the equipment.
Consider how slowly the security system is updated in such a production chain.
Allegro Soft delivers a fixed version of RomPager to the chip manufacturer, which should include it in the SDK and transfer to the router manufacturer. After that, you need to recompile the firmware for each product line and each model, and if you also perform a regular update, it will become a real nightmare for the manufacturer.
In this case, we say: “Too many cooks do spoil the broth”, that is, “Seven nannies have a child without an eye” (literal translation from English: “Too many cooks spoil the broth”).
I note that most people never update the firmware of their routers. This is one of the reasons why such vulnerabilities are not fixed for months or even years.
Consider the issue of cooperation with manufacturers. We contacted Allegro Soft and the most influential manufacturers of routers, presented them with a complete description of the vulnerability and offered non-destructive “patches” of the operating system (POS) to fix it. Despite our broken English, the majority heeded our recommendations and released firmware updates based on our recommendations, for example, Huawei.
But Allegro Soft replied that “we cannot force manufacturers to upgrade to the latest version”, despite the fact that they presented the latest updated version in 2005! Think about the fact that if the 2005 update has not yet passed through this whole chain, then something is clearly wrong with this.
And now we will answer frequently asked questions:
Is it true that RomPager is so bad?
— , , , «», , .
, « » ?
– , .
?
– , !
, IP- ?
– 80 7547 ISP TR-069, , .
: IPv4, IP, .
, !
, .
Question:
— D-Link GSL 320, Linux, , ?
Answer:
— , , , , , , .
Question:
— , ZoneAlarm. , , ?
Answer:
— , , , , .
Question:
— , , , , , , ? , ISP.
Answer:
— DSL , , .
, , , , . – , , .
Question:
— gSOAP ?
Answer:
— SDK, , .
Question:
— , ?
Answer:
— , !
Question:
— , 7547?
Answer:
— - , , , IP, WAN. IP LAN, , . .
Question:
— , , , ACS ?
Answer:
— , , , , .
Question:
— ?
Answer:
— , .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

The screensaver of the film is shown on the screen, then portraits of speakers appear.
')

Further in the credits are indicated:
Denis DeVito - as an affordable IPv4 toaster, Arnold Schwarzenegger - as a TP-Link TD-W8961ND router, and others ...
So, for those of you who have not seen the movie “Too Many Cooks,” which was shown a few months ago, we advise you to watch it, we really liked it. If you watched it, you could appreciate our “funny pictures” that we used for the presentation.
So, we are researchers of malware and vulnerabilities and work in the company - the developer of programs in the field of IT-security CheckPoint, located in Tel Aviv. The slogan of our company - "We protect the Internet." Our task is to find the vulnerability of the equipment, tell the manufacturer about it and share information with the public.
Today we will talk about the following:
- we will conduct a quick review of the CWMP TR-069 protocol specification, a kind of squeeze out of our speech at the DEFCON conference;
- about the motivation of our research;
- about the latest edition of TR-069 from 2014, which will provide you with interesting information about our research and its technical details;
- actually about our research;
- about mass users;
- about a pessimistic view of things.
So, TR-069 is the specification No. 69 describing the CPE WAN control protocol (CPE is the equipment installed at the customer’s premises, your home router, the WAN is an extensive Internet network with a large number of computers). Version 1.0 of this specification first appeared in 2004 on the Broadband Forum from a group of companies developing broadband standards. There were several revisions of this specification, but remember that it was developed almost 10 years ago. Version 1.4 (Amendment 5) appeared in 2013, it is possible that the 6th amendment of this specification will be released in 2015.
This is what ISPs use:
- for initial installation (the so-called zero configuration);
- to monitor your device for faults and malicious activity;
- to set up your home router, including assigning it a MAC address, assigning host names for your network;
- to create additional WI-Fi networks;
- to update the firmware;
- and more for many additional operations.
The next slide shows how the work session for this specification looks like.
The CPE user equipment is located on the right — your home router with the TR-069 client, on the left is the TR-069 server, also called the ACS automatic configuration server. They “talk” to each other using SOAP RPS using XML over HTTP.
A session is always initiated by a router; this is a single IP connection by which the computer connects to the network. ASC uses the connection request and sends the command “get the parameter values” and “set parameter values” to the router.

As you can see, this is quite simple. A double authentication mechanism is involved here. The CPE must ensure that it is communicating with your trusted ASC, and the ASC only allows an authorized user to session.
At DEFCON 22, we talked about what we found in the process. Our study found deficiencies in the implementation and configuration produced by many ACS servers of network providers (ISPs):
- ACS is the only point of “ownership” of the Internet in modern ISP infrastructure;
- Many implementations of the provisions of TR-069 are simply not serious enough - we have found vulnerabilities in several products that lead to the seizure of user routers by attackers.
Here is an excerpt from the TR-069 specification regarding the Connection Request: “ACS can at any time request that the CPE initiate a connection with it using the notification mechanism of the connection request. Support for this mechanism is mandatory for the CPE. ” In fact, this means that all TR-069 clients all over the world are also the connection request server on the port that we request, and for all TR-069 this is the same port 7547, it is used by default.
Last year, the Dead Map guys did a very interesting study, it was Zachary Rumrich and his friends from the University of Michigan. They scanned 2 million random addresses on each of the nearly 10,000 ports, and determined that the CWMP 7547 — the default port for TR-069 — is the second most popular open port in the world. The percentage of its use of the Hit Rate for the Internet is 1.12%. Let me remind you that this protocol was created 10 years ago - think about it! Approximately 45 million devices use this port to communicate with the Internet, and they can be “listened” through this open port.
We will conduct a brief overview of the most popular ports in the world, which various devices use to communicate with the Internet.

Approximately 70 million devices use port 80, half for connecting to the web servers of the global Internet. Most of them are Apache servers, followed by nginx servers, IIS 8, and others. The second half of the devices uses port 80 for the Internet of Things. These devices are routers, webcams, VoIP phones and toasters.
Now people are finally beginning to realize that open access to these things is simply dangerous. Therefore, they are looking for as many devices as possible that use only port 80 for local networks.
Consider that the open port 7547 is used not only by ordinary users, its use is provided by the software of the servers of the providers interacting with the devices of the users. And all 45 million devices using TR-069 are the Internet of things.

All these devices go online using the Connection Request.
We decided to investigate security issues and find the number of people affected by this vulnerability. We had to stop guessing and move on to the facts. Last month (November 2014) we scanned ports 7547 several times around the entire IPv4 address space with the help of our friends Rapid 7 and the guys from the University of Michigan. As a result, after a simple “slash” input (/) via port 7547, we received 1.18% of all public Internet devices, the total number of which was 46,093,733 worldwide. That is, it is not one country in which these ports are open, it’s 189 countries around the world.
If you remember, there is a requirement in the TR-069 specification that this port is open for ASC requests. So, last year another 0.06% of new devices appeared that met this requirement, and that’s as much as 2.2 million! That is, the growth trend is evident.
We dealt with the problem of implementing the TR-069 on the client side and what statistics we received.

We have 5 main types of servers using the connection request. More than half fell on a piece called RomPager. This is a built-in HTTP server from Allegro Software, a Massachusetts-based company that is included in the firmware of most routers. It is optimized for minimum requirements - binary codes, minimum memory - and was first introduced in 1996. Since then there have been many versions, the latest is 5.4. We decided to focus on it and found that the client’s equipment uses four versions of RomPager.
As a result, we found that 98.04% of devices use the outdated version 4.07, 1.44% use version 4.51, 0.51% - 4.03 and 0.01% 4.34. As stated in the series, “after that I became suspicious.” What explains the incredible popularity of the only version of RomPager?

We bought a new TP Link router, unpacked it and connected it to the network. It was installed RomPager 4.07. We thought that maybe this is an old router with outdated firmware and downloaded the new firmware of 2014 from the TP Link site, updated the router and restarted it, and as a result got version 4.07 again.

Thus, we received an explanation of the popularity of the old version - it was the only latest version of the firmware, located on the websites of the manufacturers of routers.
Who is present here has an unpacked new router? It can not be that good luck!
The guy from the hall passes the box with the router, and the speaker puts it on the table.
I assure you, this man does not work for me! We will deal with this box later.
We decided to explore what RomPager version 4.07 is. It was released in 2002 and has appeared in a variety of modern devices:
- 2,249,187 devices used it through port 80;
- 11,328,029 devices used it through port 7547.
The study involved 200 different device models of more than 50 different brands. So, more than 11 million routers use an extremely outdated version of the built-in server, released in 2002, for the modern Internet. This is an excellent candidate for researching equipment vulnerability.
A very important point is that the most popular versions of the specifications are available on the Internet in the public domain.
And now let Lior continue - he will tell about how we analyzed this firmware.

Good day! My name is Lior and I analyzed how RomPager version 4.07 works and found interesting results. We had a proprietary firmware downloaded from the manufacturer of the TP Link router manufacturer. It looked like a compressed array of data, so we used Binwalk, a tool to search for files and executable code in this binary image. It is used to hack the archive and extract packed files.

So, inside the firmware, we found the Bootloader loader, the manufacturer's logo in .gif image format and the main binary code Main binary.
For a more objective analysis, I decided to download all the RomPager firmware version 4.07, which I could find on the Internet, and found that they all contained the ZyNOS (mipsb32) header - an operating system that uses ZyXEL network devices. I could not understand why devices from different manufacturers had the same firmware. I began to study what ZyNOS is.
This is the main real-time operating system - Real Time OS, RTOS, without any file system and special permissions, it consists of one large binary file designed to meet any requirements.
This system has the known rom-0 vulnerability (VE-2014-4019). As of May 2014, 1,219,985 devices worldwide had this vulnerability. This vulnerability allows an attacker to take control of the router by simply downloading the configuration file from it without any authorization, directly from the web browser panel through port 80. As a result, the attacker will simply receive the password and username. And this vulnerability affects 1.2 million devices worldwide.
Consider what the interface of the attack through port 80 looks like. We received an authorization request, and since we did not know the username and password, we tried to enter through port 7547.

Here we received a message that at the given address “Object not found” for any path other than the correct address.

I decided to find the correct address, that is, to send a request on the right path. Before starting to deal with the code, I decided to perform manual testing via HTTP headers, and suddenly I managed to hack the router by sending the user's digest name with the overflow of the digest authentication header with the value of 'a' # 600.

This led me to the first vulnerability. To understand why this happens, let's look at the structure of the RomPager code. Each line here consists of an HTTP header and its manufacturer’s function to process this header.

Consider the function that is responsible for the username.

You can see what causes this vulnerability - this is unprotected strcpy, a standard library function for copying a null-terminated string (including a null-terminator) to a buffer. But what really leads to the possibility of hacking a router is the lack of symbols and the possibility of dynamic analysis. It is very difficult to understand.
I opened the router and began to look for JTAG. For those who do not know what it is, I will explain: JTAG is an interface for debugging and testing firmware. But when I took off the case, I didn’t find any JTAG connectors there, but I found something that looked like a U-ART serial port on a separate chip - a connector designed to communicate with other digital devices.

I went in for soldering and connected it to the router itself, and then through the USB adapter I connected this U-ART to my computer. When I loaded the router, I found a very good opportunity to debug the router. I'll show you what I got after hacking the router - this is a very nice crash dump with all registers and stacks, indicating the cause of the emergency recording - “TLB overflow”. At the top is a line of EPS - a pointer to the instructions for the MIPS microprocessor. As you can see, it is rewritten by me, and this means that I control the router. Further analysis of the crash dump made it possible to fully determine the cause of the vulnerability.
So, unprotected strcpy allows you to completely rewrite the EPC, which consists of 584 hexadecimal bytes, conveniently located after the user name, so hacking the router is very easy.
This is the number 1 exploit:
- need to send a long username;
- rewrite the instruction pointer with your shellcode — the binary executable code for the main processor;
- get the ability to remotely control the router!

The difficulty of this method of hacking is as follows:
- Each device and each firmware version has a different location of the Nature's ASLR address space, that is, it is not known what exactly the value of the instruction pointer needs to be rewritten.
- If you know where the memory is located in a specific firmware file, then you can easily run the code needed to hack the victim's router;
- the hacker has only one chance for a successful attack, because after “crashing” the router will receive a new IP address, because here there is a dynamic allocation of IP addresses.
Theoretically, these problems can be circumvented by attempting to inject shellcode through another router information leakage vulnerability. Let's see how it works.
Since I did not have full debugging capabilities, I used the debugging option for the “beggars”, using the primitive debugging capabilities built into the RomPager itself, via the serial port. This made it possible to patch the firmware before downloading it, which was quite convenient, but very tiring.
After several reboots, I found the hidden feature of the ZyNOS operating system, which allowed access to the memory of the router via the Internet. This is ZynOs Remote Debugger, or ZORDON. This feature allows you to create control points, view and edit memory, read and rewrite registers online.
Let's look at vulnerability # 2.
If you remember, there is no dynamic allocation of memory, so each incoming HTTP request fills in a pre-allocated “request structure”.
RomPager 4.07 handles up to 3 parallel requests (3 pre-allocated structures).
When sending 3 consecutive requests, one of them can rewrite the HTTP structure that we saw earlier. This also became possible due to the unprotected strcpy, and we again took control of the EPC.

So, what is the exploit number 2?
- Blindly reading memory by replacing the HTTP header line.
- Problem: this technique only works with port 80, which also has the rom-0 vulnerability.
Move to vulnerability number 3.
RomPager supports cookies. As you remember, there is no dynamic memory allocation, so there is a preliminary memory allocation for each array of cookies, a total of 10 pieces, each 40 bytes long. The names of cookies are constant - from 0, 1, 2 ... 9. The next slide shows what C0 looks like.

Let's see how RomPager steals cookies, that is, it processes cookies. At the top of the slide, you can see that he first checks the name of the cookie with a capital letter at the beginning. If so, it converts the rest of the name "cookies" into an integer and uses it as an index for the array "cookies".

Next, it loads it, multiplying by s3, it will be an index for 40, and uses it at the strncpy destination.
Thus, vulnerability # 3 is as follows.
By performing an arbitrary write to the memory of a fixed point in the internal management structure of the RomPager, we gain control over everything that the RomPager does. At the same time, an additional bonus is the ability to overflow the 32-bit integer value in order to adversely affect the infrastructure.
If we send any “cookies” instead of C0, C1 and so on, we get the following answer:

This technique works on any model of routers of any brand, to which we have obtained legal access. Thus, exploit # 3 is as follows: using several magic cookies added to your request, you bypass any authentication and view the configuration interface as an administrator through any open port.
Let's see a demonstration of what has been said - we have a video of our actions. We start the Internet browser and in the address bar enter the IP address of our router and the request for authorization. If you register in the line: 7547, then we get the message shown earlier.

Therefore, we use “our” Chrome browser plugin, that is, the exploit we have built in, its icon is located to the right of the browser’s address bar (the plugin is called “Take all these things!”).

Click on the icon to activate this plugin.

It takes literally a second, and the TP-Link router settings window opens in front of us. We bypassed the authorization process!

Then you can click on the plugin again to restore the legal mode.

Let me show you again how it works: enter the IP address of the router 192.168.1.1 into the line, refresh the page when the plug-in is connected ... it did not work ... try updating again - that's it! We went to the settings page of the router without any authentication request, the window for entering the user name and password did not appear at all.
I repeat once again: we now have a new router connected from the manufacturer, right out of the box, released in 2014, and it is subject to the same vulnerability that was discovered and described more than 10 years ago.
Let's return to our presentation. We placed on this slide a link to the site where the information on the essence of the problem described by us is posted.

This map shows which countries are affected by this vulnerability. These are 189 countries worldwide and over 52% of all IP addresses.
I know what you just thought: you need to immediately abandon the use of port 7547 on your devices to access the Internet. But even if you try to deactivate the CWMP function in the settings of the router, port 7547 will still remain open.

You can counter this as follows:
- refuse to use the Internet at all;
- use alternative router firmware;
- Do not buy these models of routers until they eliminate the vulnerability - here is a link to our site with a list of mis.fortunecook.ie/misfortune-cookie-suspected-vulnerable.pdf , we are constantly updating it.

Consider how the process of production of routers.

Allegro Soft supplies RomPager to the chipset manufacturer, which is sent to the manufacturers of ASUS, D-Link, Huawei, TP-Link, ZTE routers. Those adapt the software to different models, insert their logo into the firmware and sell the ready routers to the end user of the equipment.
Consider how slowly the security system is updated in such a production chain.
Allegro Soft delivers a fixed version of RomPager to the chip manufacturer, which should include it in the SDK and transfer to the router manufacturer. After that, you need to recompile the firmware for each product line and each model, and if you also perform a regular update, it will become a real nightmare for the manufacturer.
In this case, we say: “Too many cooks do spoil the broth”, that is, “Seven nannies have a child without an eye” (literal translation from English: “Too many cooks spoil the broth”).
I note that most people never update the firmware of their routers. This is one of the reasons why such vulnerabilities are not fixed for months or even years.
Consider the issue of cooperation with manufacturers. We contacted Allegro Soft and the most influential manufacturers of routers, presented them with a complete description of the vulnerability and offered non-destructive “patches” of the operating system (POS) to fix it. Despite our broken English, the majority heeded our recommendations and released firmware updates based on our recommendations, for example, Huawei.
But Allegro Soft replied that “we cannot force manufacturers to upgrade to the latest version”, despite the fact that they presented the latest updated version in 2005! Think about the fact that if the 2005 update has not yet passed through this whole chain, then something is clearly wrong with this.
And now we will answer frequently asked questions:
Is it true that RomPager is so bad?
— , , , «», , .
, « » ?
– , .
?
– , !
, IP- ?
– 80 7547 ISP TR-069, , .
: IPv4, IP, .
, !
, .
Question:
— D-Link GSL 320, Linux, , ?
Answer:
— , , , , , , .
Question:
— , ZoneAlarm. , , ?
Answer:
— , , , , .
Question:
— , , , , , , ? , ISP.
Answer:
— DSL , , .
, , , , . – , , .
Question:
— gSOAP ?
Answer:
— SDK, , .
Question:
— , ?
Answer:
— , !
Question:
— , 7547?
Answer:
— - , , , IP, WAN. IP LAN, , . .
Question:
— , , , ACS ?
Answer:
— , , , , .
Question:
— ?
Answer:
— , .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/354760/
All Articles