SSL Data transfer security
How long have you tested your SSL? It's not enough just to buy an SSL certificate and install it, you need to configure it.
Why is it important. External security analysis (manual or automatic) usually begins with checking the SSL configuration. The SSL configuration usually indicates the overall security level of the entire data protection system. Therefore, advanced users are starting to send requests like “how can you protect my personal data if you have SSL v3 enabled”. Within the framework of the GDPR, a secure SSL setup is a technical measure to protect personal data.
SSL Configuration Testing
')
Problems with SSL protocol versions:
SSL 2.0, SSL 3.0, and TLS 1.0 are strongly recommended to be disabled, since most security standards have not supported them for a long time (for example, PCI DSS 3.1).
Recommended protocols TLS v1.1 and TLS v1.2 with current algorithms for encryption and removal of hashes.
SSL Configuration Analysis
There is a great tool SSLLabs Test Tool for testing SSL configuration reliability testing.
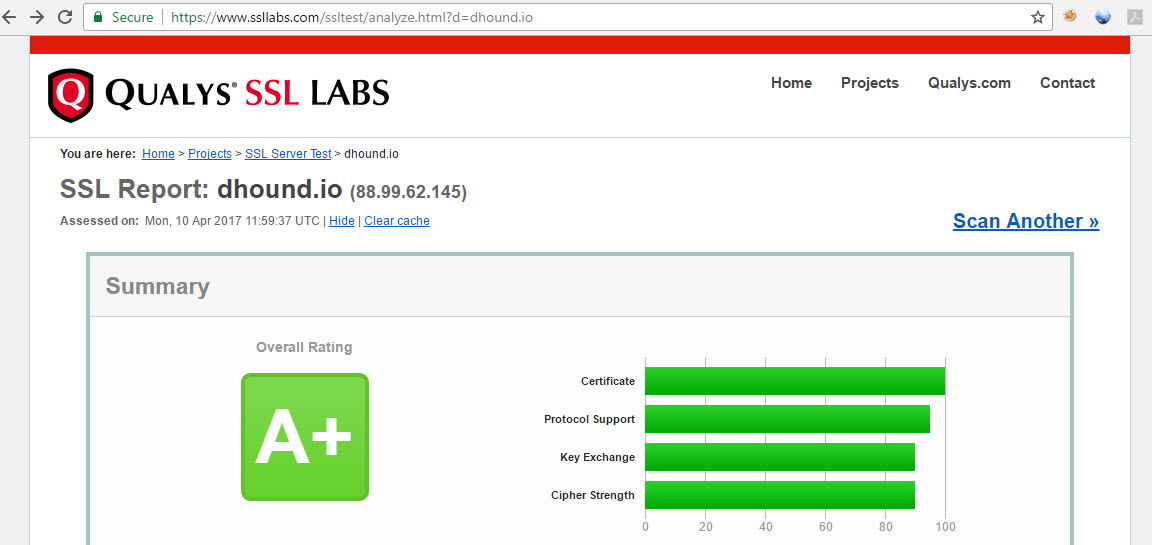
A + and A are the best SSL configuration metric. F - the worst level.
Sample SSL test for one of our product sites
Below is another example of how to quickly check the level of SSL configuration using the nmap tool:
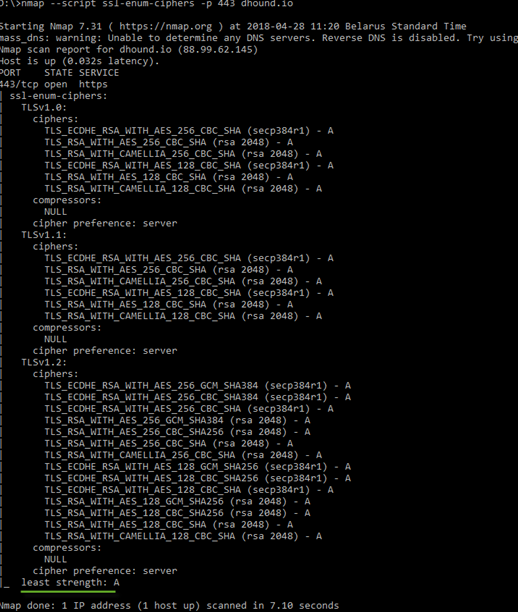
Strong ciphers
The low level of SSL configuration is in most cases associated with the use of outdated and weak encryption algorithms.
This resource provides information on how to set up good SSL algorithms on Apache, nginx, HAProxy, etc.
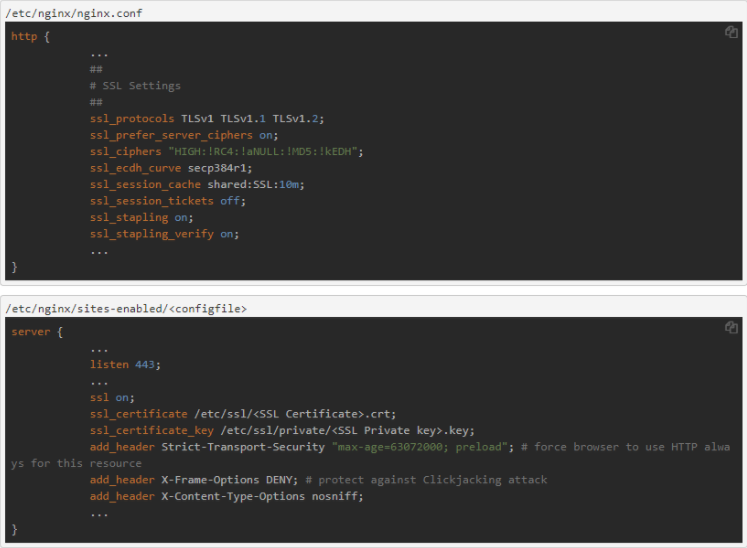
Configuration on Nginx
Below is an example of the configuration of web servers on nginx, which increased the SSL setting from level B to A + and increased system security:
Windows configuration
Windows Server 2016 and higher already have an SSL configuration that complies with current security policies (for example, SSL v2 and SSL v3 are disabled).
In earlier versions of Windows Servers (2008, 2012) SSL v3 is still enabled, i.e. you need to manually disable obsolete protocols. See Microsoft recommendations: how to disable PCT 1.0, SSL 2.0, SSL 3.0, or TLS 1.0
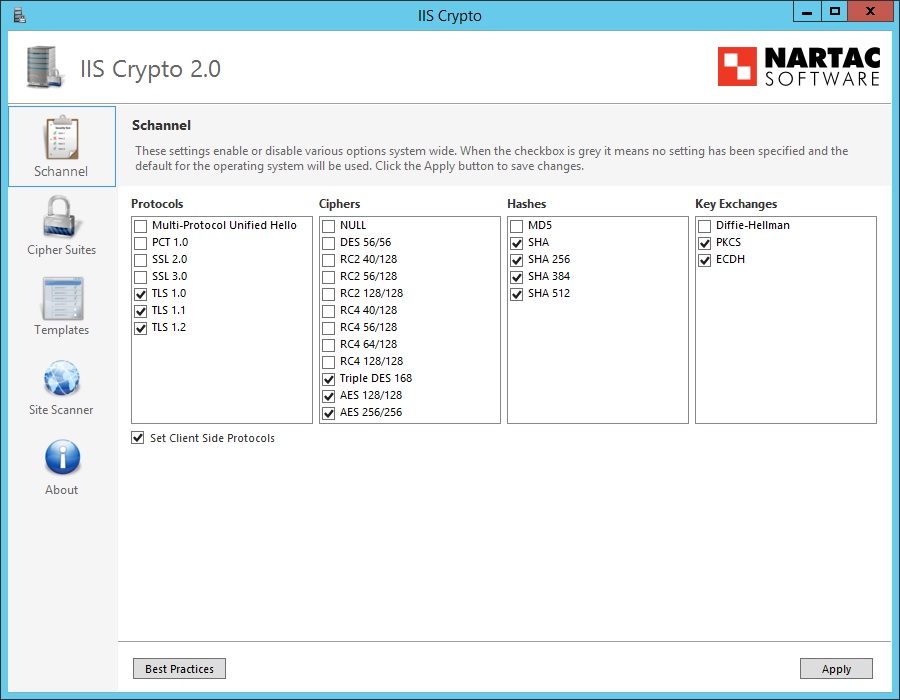
We use the IIS Crypto tool , which provides a graphical interface for disabling weak ciphers and outdated protocols. This avoids dangerous manual work with the Windows registry.
Using SSLLabs Test Tool , its tips and functionality allows you to quickly protect SSL / TLS on Windows.
The real SSL configuration example for Windows Server 2012 R2
The author - Denis Koloshko, CISSP
Why is it important. External security analysis (manual or automatic) usually begins with checking the SSL configuration. The SSL configuration usually indicates the overall security level of the entire data protection system. Therefore, advanced users are starting to send requests like “how can you protect my personal data if you have SSL v3 enabled”. Within the framework of the GDPR, a secure SSL setup is a technical measure to protect personal data.
SSL Configuration Testing
')
Problems with SSL protocol versions:
- SSL v2 is insecure, outdated and not recommended for use. See DROWN attack on this protocol.
- SSL v3 is unsafe and outdated tool. See POODLE attack.
- TLS v1.0 is also an outdated protocol, but in practice it is still necessary. His main weakness ( BEAST ) has been mitigated in modern browsers.
- TLS v1.1 and TLS v1.2 both do not have known security problems, but only v1.2 provides modern cryptographic algorithms.
SSL 2.0, SSL 3.0, and TLS 1.0 are strongly recommended to be disabled, since most security standards have not supported them for a long time (for example, PCI DSS 3.1).
Recommended protocols TLS v1.1 and TLS v1.2 with current algorithms for encryption and removal of hashes.
SSL Configuration Analysis
There is a great tool SSLLabs Test Tool for testing SSL configuration reliability testing.
A + and A are the best SSL configuration metric. F - the worst level.
Sample SSL test for one of our product sites

Below is another example of how to quickly check the level of SSL configuration using the nmap tool:

Strong ciphers
The low level of SSL configuration is in most cases associated with the use of outdated and weak encryption algorithms.
This resource provides information on how to set up good SSL algorithms on Apache, nginx, HAProxy, etc.
Configuration on Nginx
Below is an example of the configuration of web servers on nginx, which increased the SSL setting from level B to A + and increased system security:

Windows configuration
Windows Server 2016 and higher already have an SSL configuration that complies with current security policies (for example, SSL v2 and SSL v3 are disabled).
In earlier versions of Windows Servers (2008, 2012) SSL v3 is still enabled, i.e. you need to manually disable obsolete protocols. See Microsoft recommendations: how to disable PCT 1.0, SSL 2.0, SSL 3.0, or TLS 1.0
We use the IIS Crypto tool , which provides a graphical interface for disabling weak ciphers and outdated protocols. This avoids dangerous manual work with the Windows registry.
Using SSLLabs Test Tool , its tips and functionality allows you to quickly protect SSL / TLS on Windows.
The real SSL configuration example for Windows Server 2012 R2

The author - Denis Koloshko, CISSP
Source: https://habr.com/ru/post/354582/
All Articles