Conference BLACK HAT USA. “How the feds caught the Russian mega-carder Roman Seleznev”
A year ago, this topic was actively discussed at Giktatimes:
Russian carder Roman Seleznev, the son of a deputy, was sentenced to 27 years in prison in the US

')
Karder and the son of the deputy Roman Seleznev said that since 2008 he worked under the protection of the FSB
In today's translation, we will reveal the details of how the feds caught the Russian mega-carder Roman Seleznev.
Good afternoon, my name is Norman Barbosa, I am the prosecutor in the computer crimes investigation of the US Attorney's Office in Seattle, here is my second assistant, Harold Chen, a former judicial prosecutor from the General Directorate of Justice of Washington, DC, who now works for Google. He received a lot of money after we won this case, and now he is happy to be here with me.
I want to thank our friend who is here for giving me the laptop. Yesterday, when I came here, my computer began to "squeak" and immediately issued a critical error. I thought it could be "these" guys or the FSB. I’m not sure, but I know that many of you are playing the Fissure Hack. When we were engaged in the Seleznev case, among other things, we also played a game of “find an FSB agent,” so if you see him, let us know.

Our presentation does not serve the purpose of finding the password for your hacker empire, because it still does not work. It's just a real opportunity for us, for the justice department, to talk in detail about how we are investigating computer crime cases so that our accusations sound convincing to the jury. We have to prove to 12 jurors that this man was sitting at the computer, and present detailed evidence, which is why he was tried.
There was a situation when we were forced to present all our evidence in such detail that far exceeds the amount of information available to the public. And then, there are cases that are resolved if the accused admits his guilt or simply does not come to court.
We were very lucky that we got the case - Harold, me and another prosecutor from my office, Seth Wilkinson. It was a long investigation, and we participated in it from the very beginning; this was done by another assistant district attorney, who retired before Romana was arrested. Her name was Catherine Warman, she was my management tutor and was well versed in computer crimes. She worked on this case together with agent David Dunn, who also left the government service before Seleznev’s arrest.
I am sure many of you have heard of him here this week, this is an excellent investigator who returned to the service specifically to participate in court sessions.
So today I’m going to tell you about the progress of the investigation, and then Harold will tell you about the evidence we received as a result of Roman’s arrest, the process’s difficulties caused by the results of the accused’s forensic examination and how we had to deal with them.
Here is a small description of Roman Seleznyov: he was one of the world's largest abductors of credit card data, was accused by three Federal courts in different states, a Russian, who owns real estate in Vladivostok and in Bali in Indonesia.
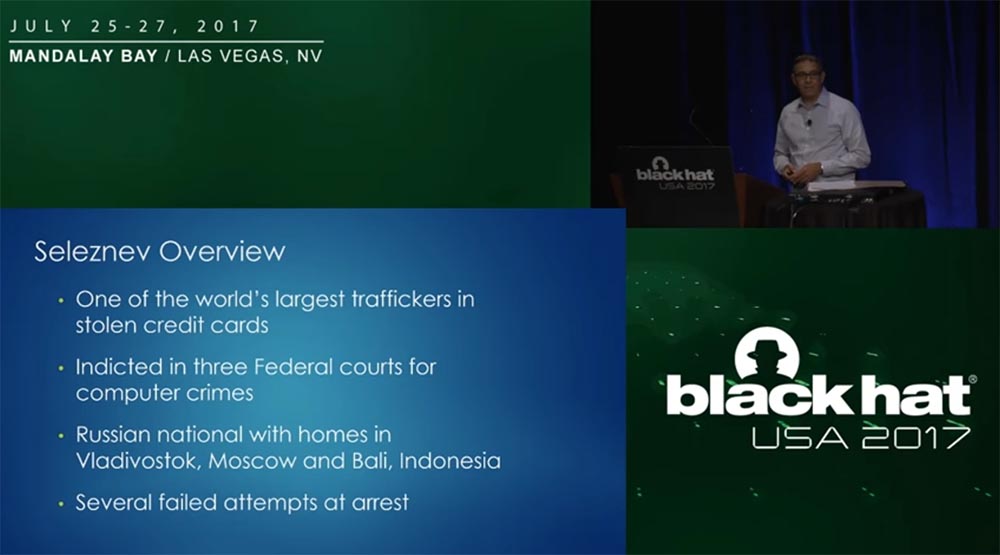
He has been stealing bank card data since about 2005 before we were able to arrest him and present him in court in 2014. From 2011 to 2014, we made several attempts to arrest him, which were unsuccessful.
The position of his father in the Russian government was of great importance, which the court could not ignore (Valery Seleznev is a State Duma deputy from the LDPR party). There was tension between our government and the Russian government after Roman was detained in the Maldives in 2014, which resulted in me and other participants in the process being blacklisted by the Russian government and banned from entering Russia. Fortunately, this tension subsided, and again I can go to Moscow, where I studied Russian. But at that time, none of us could go there.
Thanks to his criminal scheme, Seleznyov stole a lot of money, so he hoped to break the lawsuit with their help. He had a very monetary "support team" that provided his protection.
Seleznev hacked card services using three different “nicknames”: nCux, Track2 and 2Pac, connected with three periods of his hacking activity.

He was the first to use on the carders forums, where he had sold stolen card data since 2002, then he began to use the “nickname” of Track2 and used the nickname of 2Pac before his arrest.
The nCux identification took place at the beginning of 2009, when it was lit up on many carders forums, on this slide you see his message about the sale of these cards: “Dear customers, do not miss your chance - all AMEX cards for $ 1 each, VISA, MC , DISCOVER - $ 5 piece. The “Great Sale” is related to the fact that in May 2009 Roman declared that he would retire and stop hacking. His activity in this field has been monitored since 2002, when he began selling cards with all the data, including his name, password, date of birth and Social Security number. In 2005, he took into account that the stolen credit card data enjoyed great popularity and purchasing power, and developed vigorous activity. Because of this, he came to the attention of the Washington division of the Secret Service of Cybernetic Intelligence. They began to monitor his activity on the Internet and realized that this was a “big player” and began to try to find out who exactly was hiding behind the “nickname” nCux. In fact, the transliteration of this “nickname” in Russian meant “psycho” - this was the nickname awarded to Roman for his “explosive” character.
During the surveillance period from 2005 to 2009, the CIS Secret Service obtained quite a lot of information based on the “excavations” of open Internet trolling - a good “old-fashioned” investigative work.

In May 2009, they, together with the FBI, met in Moscow with the FSB and reached agreements on information exchange, after which it was literally a month, and Seleznyov disappeared from the Internet, destroying all the known FBI accounts. He posted this post in May, and disappeared in June.
This threw the Secret Service back and forced her to rethink how to conduct an international investigation and exchange information in this particular case.
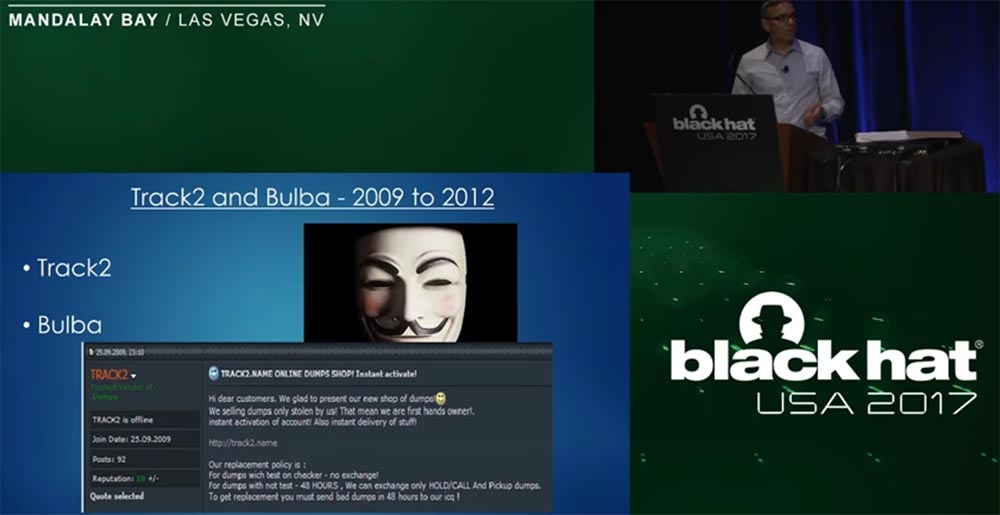
Naturally, Seleznyov was not going to retire - he just changed his “nickname” and used Track2 and Bulba nicknames throughout 2009-2012. This slide shows the new post of Seleznev, who began to re-create his empire on the site carder.su, the most authoritative resource of carders, where Roman already had a reputation as a solid seller. This is evidenced by the mark in the upper left part of the message under the “nickname” This prompted the Secret Service that it was not just some new hacker who got a little stolen card from his “stash”, he had weight and fame among the users of this resource. The site administration even provided him with a monopoly in this matter, throwing out the smaller competitors of Seleznev, who offered similar goods.
CIS came to the conclusion that this is indeed a major player, and they immediately marked it on their “radar” and in May 2010 began an investigation. At about the same time, a local employee of our office, David Dunn, took part in a SWAT operation in Idaho, in the city of Ker-D'Alene, which was held at Shlotsky's Deli, a fast-food chain restaurant, about the leakage of visitors' credit card data. He inspected computer equipment there and confiscated RAM, where he unexpectedly discovered that Shlotsky's Deli was connected to the network via a Russian IP address. David took note of this fact, and after a few weeks or a month, a lot of stolen credit cards surfaced on the network, which could be traced to the data breach, and the Shlotsky restaurant’s computer turned out to be this point. After this, CIS invited Dunn to participate in the episode of the investigation of the case related to the equipment found in this restaurant.
Detective Dunn examined the computer of the suspect who had been confiscated in a restaurant, and found that the guy was looking at these two sites: Track2.name and Bulba.cc and chatted with a man named Track2.

He told him that his website Track2.name was covered, but a restaurant employee could sell card numbers on another site, Bulba.cc. The detective began to investigate both these sites to find out whether one hacker is hiding under these two "nicknames". He investigated the domain registration and found out the e-mail box from which the registration occurred, examined other mailboxes located in the USA, also associated with these accounts. Eastern Virginia supported the investigation of this case together with CIS, and in October 2010 they began to collect warrants for information. Detective Dunn had been expecting information for several weeks, because this is not the kind of thing that can be done overnight. In addition, some orders were returned, as there were cases when postal registrars refused to provide information.
And while he was waiting, on October 21, 2010, the second hacking took place - this time at one of the oldest Broadway Grill restaurants on Capitol Hill in Washington.

Detective Dunn arrived in Washington and, together with a local detective, began to study point-of-sale computers. They found out that the computers were set up very poorly with regard to ensuring the security of visitor information, since they stored data of 32 thousand credit bank cards in the form of simple text files. And this information went to the same IP address that was used in Shlotsky's Deli restaurant computers in Idaho. Here, the detective was able to advance a little further, as he managed to find out that someone had placed malicious software on Broadway Grill computers, which redirected the data to the malicious server while manually typing the address associated with the same IP address as Shlotsky's Deli.
Detective Dunn realized that now he had the opportunity to investigate the crime at home, so there is no longer any need to travel to Virginia or Idaho and you can bring a case here in the western district of Washington.
Then the matter began to rapidly unwind. During November 2010 - February 2011, the detective found out who registered the sites of the carding. He found Yahoo's mailboxes that led to the HopOne server in McLean, Virginia. Here he found out that from the IP addresses of computers in Shlotsky the card numbers were sent to a server in Russia.

When researching Yahoo accounts, he found out who bought HopOne server at McLean. For this, he conducted a legal penetration testing on the Yahoo server in order to track incoming and outgoing connections. This did not allow to explore the content, but gave him the IP addresses of incoming and outgoing connections, the numbers of some ports, the amount of data transferred. In addition, he saw that this server was connected to hundreds of computers throughout the United States, many of which were installed in restaurants. When he began to check their IP addresses, he learned that almost all of these computers were connected to the HopOne server, and found dozens of victims across the country who used points of sale in these restaurants.
The next slide shows evidence of malicious interference with computers that made credit card payments in many restaurants and cafes.
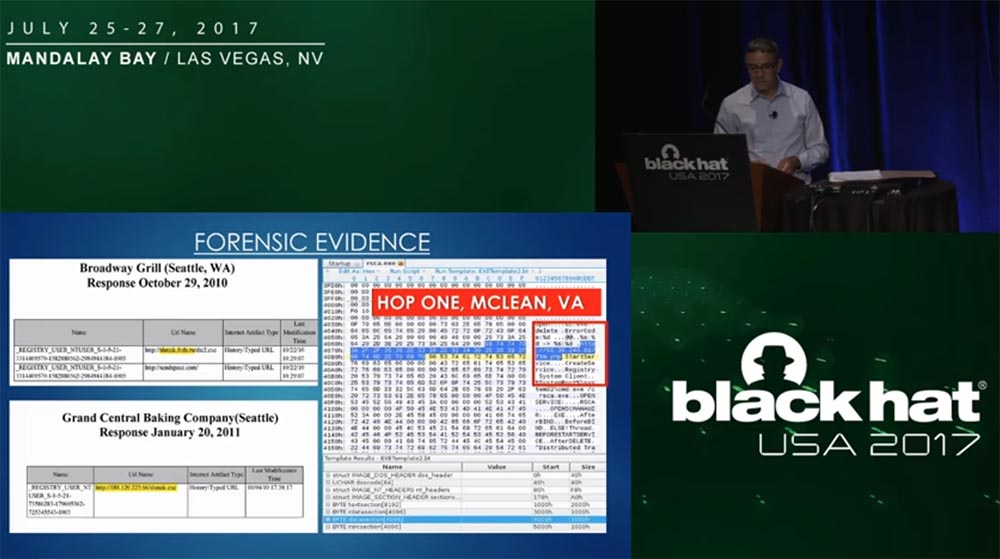
Shows the IP devices with which this malware was connected and sent the card data to the same HopOne server.
The following shows the infrastructure of this criminal scheme. There is nothing special here - this is a regular botnet network using several levels of data transfer.

Roman's computer is shown in the upper left corner. Detective Dunn discovered many hacking tools on the HopOne server that allowed him to recreate the Seleznev scheme. The Russian hacker scanned the ports of the payment terminal of the victim to find open RDP connections. As soon as he found such a connection, he hacked it with the help of a Brute-force attack with password selection and downloaded the card data to the user's server under the Shmak / Smaus nicknames with the IP address 188.120.255.66, the HopOne server with IP 66.36.240.69, and the Ukrainian server with IP 188.95.159.20. From there, the data came to the sites of carders - sellers under the nicknames of Track2 and Bulba.
On the left, you see the Yahoo mailbox that was used to register the Shmak / Smaus server, on the right, the Yahoo mailbox for Track2 and Bulba. In this case, the middle mailbox associated with Track2 was also connected to the HopOne server. A study of the HopOne server led to the discovery of hundreds of files that contained almost 400,000 credit card numbers. All of them were stored very conveniently for us, since they contained the IP addresses of the victims. This allowed us to quickly identify all the victims and gather more evidence.
As for the email addresses, they allowed us to identify Seleznev. He used one of the addresses of the Yahoo email service, which received various notifications. In the rubensamvelich@yahoo.com box, we found a letter about the successful registration of Roman Seleznev on PayPal on September 19, 2009. This was one of the strongest evidence against Roman, which was discovered by Detective Dunn. The previous slide shows that the rubensamvelich account led to the sites of stolen card sellers, so using this PayPal sign-up box was the biggest mistake Roman had made.
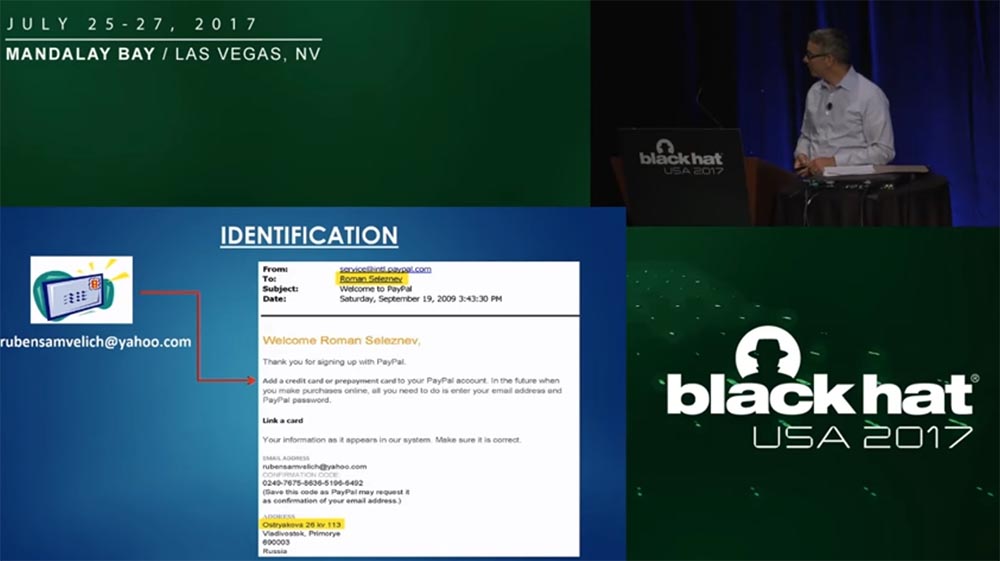
He did not think that the basis of American payment systems is to keep copies of such messages about the user's registration, where all his identification data is available. Here is the address of his registration in Vladivostok, which served as the identification of the person during the passport check during the arrest.
The second account, boookscafe@yahoo.com, which we found was used by Roman for many years. This was another mistake Seleznev, since he used this box back in 2006.
.

The boookscafe box did not help in investigating Seleznev’s hacker network infrastructure, but it helped to establish his connection with the user, known by his nickname nCux. We traced many related things, including ordering a bouquet of flowers for his wife. A postcard was attached to it with the words that “you are the most beautiful, but Eve is still more beautiful than you”! Eva is the name of his daughter, which was also inscribed on his passport, and was another proof of identification during the arrest. We also found his order for a Russian online store, with a home address in Vladivostok, placed with the help of this mailbox.
In the end, we found the most significant evidence on the HopOne server, where he kept all his hacking tools for hacking and the numbers of stolen credit cards. Seleznyov used this server to book a flight for an Indonesia-Singapore flight, and his personal data and the number of a Russian passport were indicated on the reservation form. The coincidence of the data of this order with the data of the passport served as another proof during his arrest. In Indonesia, his second home was located.

The Secret Service put all this evidence together, and together with Detective Dunn began to look for possible evidence of Seleznev’s involvement in other carder frauds. The next slide shows evidence that all such cases are somehow connected with each other, and carders have been working with each other for a long time and are connected with one another with common interests.
This 2007 chat is from an investigation conducted by the Department of the Eastern District of New York. If you remember, the investigation began in 2002-2003. It concerned the hacker community Carder Planet and was very successful for the New York government. Mr. Carranza was one of the detainees in this case, and a chat between him and a certain nCux 111 was discovered on his computer. He told him his real data - his first name, last name, home address in Vladivostok, two mailboxes, among which was indicated and boookscafe@yahoo.com. These data were required by Karranze for the deal with Seleznyov.

After gathering all this evidence, Detective Dunn and a representative of the prosecutor's office appealed to the Grand Jury in 2011 and received an indictment that imputed Roman Seleznev, known under 9 hacker nicknames, committing computer crimes, fraud with bank cards, using funds to hack traffic and etc.

Unfortunately, shortly thereafter, Roman, being in Morocco, was seriously injured by the explosion of a cafe in Mogadishu on April 28, 2011 during a terrorist attack. He and his wife were sitting on the 2nd floor of the restaurant, which was heavily destroyed by a bomb. He was taken to Moscow, where he spent several months in a coma and underwent several operations. Detective Dunn went to the bulba.cc website several times to check the activity of his administrator, however, they didn’t use this seller-administrator account, only messages from users appeared on the site who knew that an accident had happened to the “boss” and wished him a speedy recovery . Finally, in January 2012, this store of stolen cards was closed.
2011-2013 , . , , , . , .
, , , . , , .
, , , . , .
– 2pack.cc, 2013 2014. , . , CIS. , , , - Home Depot Neiman Marcus Target . , .
, , – , . , , , . .
, - – . 2014 , , . , , : « »!, : « »?
20 DOJ, -. , – , .

6 4 , . 1 , 3 5 , 3 . 3 . .
, .

, , , – , iPhone, , . , , «» nCux, Smaus, Ochko123. , – smaus, shmac, ochko. , . Ochko123! , «» – « » (butthole ).
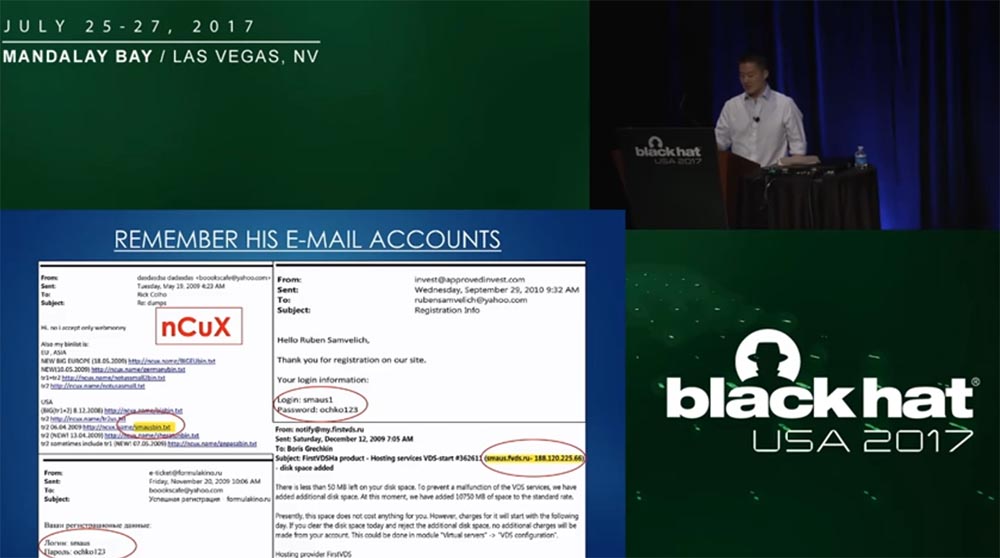
– , . 1,7 , , 1,7 . .
-, , , , , , . , , , , , , . , MSR 206, , , , , .. .
, ? PACER – , , , . – , , «» - , , Bulba.
, , , ?
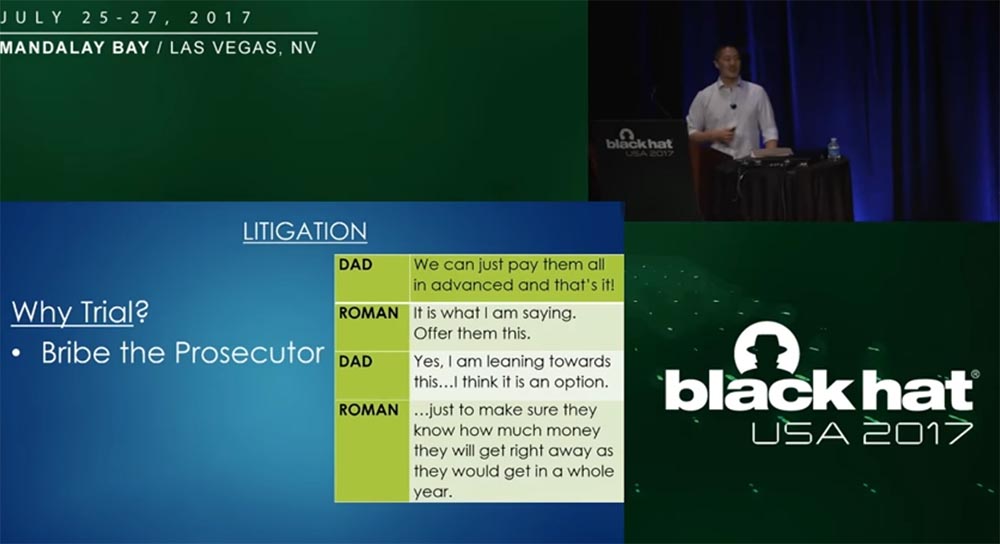
, 2 . , « » . , , . : « , »! : « , ». : «, … , ».
, 10 . , , .
, , « », « », « », « » . , . , - , Black Hat, .

, , - , , . , - , , , , . , , , . Windows 8, , .
, , , . , , , , .
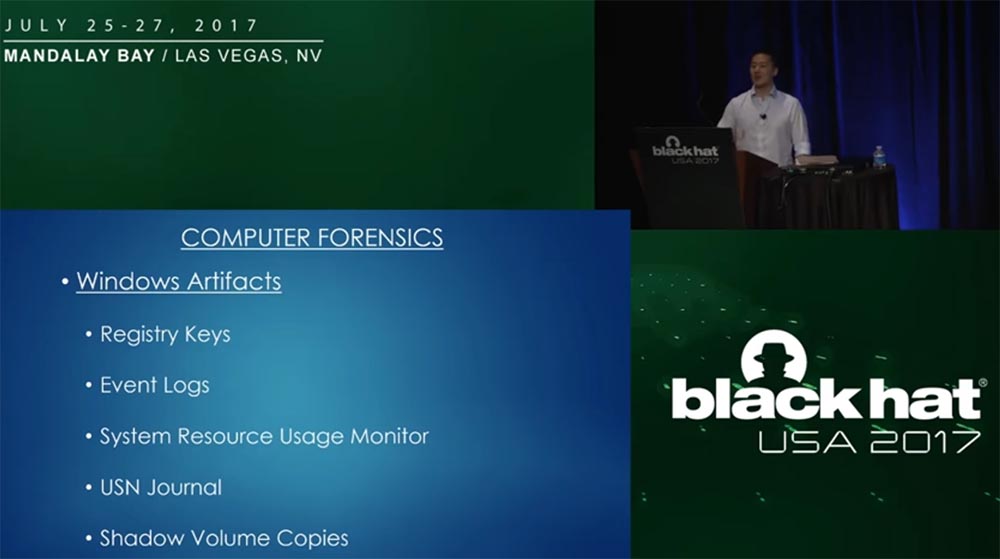
«» Windows, , , , USN . , , . , 21 3- , KANIFUSHI. «» , . , , 20 . SIM-, , «». , «».
. , , , , - , . smaus, , .
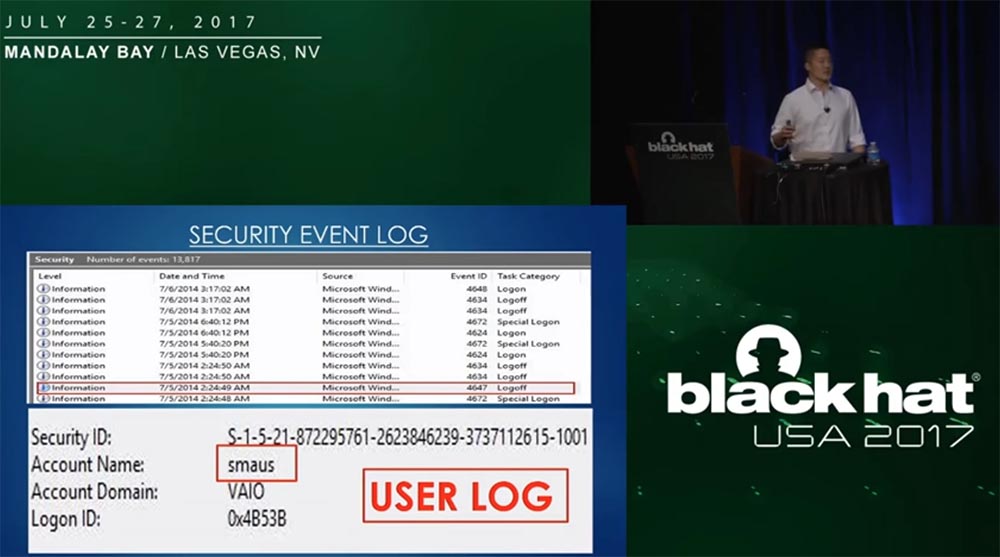
SRAM , , , TOR. , , .
, slack space, . , , . , «» , . , 8 . 38 27 .

.
:
— , , , . , , , .
Question:
— - , ?
:
— , .
Question:
— - , ?
:
— , , - , , .
Question:
— , , ?
:
— , . , , , .
Question:
— 2011 2014 ?
Answer:
— , , , , .
Question:
— , , « ». , ?
Answer:
— , , , , .
Question:
— , ?
Answer:
— , 27 , , , 169 . , , , . , . , , . 400 , , , , .
Question:
— , ?
Answer:
— , , .
Question:
— iPhone ?
Answer:
— Apple , , .
Question:
— ?
Answer:
— 3700 .
Question:
— , 2009 ?
Answer:
— , .
Question:
— , , POS ?
Answer:
— , , , 32 , .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Russian carder Roman Seleznev, the son of a deputy, was sentenced to 27 years in prison in the US

')
Karder and the son of the deputy Roman Seleznev said that since 2008 he worked under the protection of the FSB
In today's translation, we will reveal the details of how the feds caught the Russian mega-carder Roman Seleznev.
Good afternoon, my name is Norman Barbosa, I am the prosecutor in the computer crimes investigation of the US Attorney's Office in Seattle, here is my second assistant, Harold Chen, a former judicial prosecutor from the General Directorate of Justice of Washington, DC, who now works for Google. He received a lot of money after we won this case, and now he is happy to be here with me.
I want to thank our friend who is here for giving me the laptop. Yesterday, when I came here, my computer began to "squeak" and immediately issued a critical error. I thought it could be "these" guys or the FSB. I’m not sure, but I know that many of you are playing the Fissure Hack. When we were engaged in the Seleznev case, among other things, we also played a game of “find an FSB agent,” so if you see him, let us know.

Our presentation does not serve the purpose of finding the password for your hacker empire, because it still does not work. It's just a real opportunity for us, for the justice department, to talk in detail about how we are investigating computer crime cases so that our accusations sound convincing to the jury. We have to prove to 12 jurors that this man was sitting at the computer, and present detailed evidence, which is why he was tried.
There was a situation when we were forced to present all our evidence in such detail that far exceeds the amount of information available to the public. And then, there are cases that are resolved if the accused admits his guilt or simply does not come to court.
We were very lucky that we got the case - Harold, me and another prosecutor from my office, Seth Wilkinson. It was a long investigation, and we participated in it from the very beginning; this was done by another assistant district attorney, who retired before Romana was arrested. Her name was Catherine Warman, she was my management tutor and was well versed in computer crimes. She worked on this case together with agent David Dunn, who also left the government service before Seleznev’s arrest.
I am sure many of you have heard of him here this week, this is an excellent investigator who returned to the service specifically to participate in court sessions.
So today I’m going to tell you about the progress of the investigation, and then Harold will tell you about the evidence we received as a result of Roman’s arrest, the process’s difficulties caused by the results of the accused’s forensic examination and how we had to deal with them.
Here is a small description of Roman Seleznyov: he was one of the world's largest abductors of credit card data, was accused by three Federal courts in different states, a Russian, who owns real estate in Vladivostok and in Bali in Indonesia.

He has been stealing bank card data since about 2005 before we were able to arrest him and present him in court in 2014. From 2011 to 2014, we made several attempts to arrest him, which were unsuccessful.
The position of his father in the Russian government was of great importance, which the court could not ignore (Valery Seleznev is a State Duma deputy from the LDPR party). There was tension between our government and the Russian government after Roman was detained in the Maldives in 2014, which resulted in me and other participants in the process being blacklisted by the Russian government and banned from entering Russia. Fortunately, this tension subsided, and again I can go to Moscow, where I studied Russian. But at that time, none of us could go there.
Thanks to his criminal scheme, Seleznyov stole a lot of money, so he hoped to break the lawsuit with their help. He had a very monetary "support team" that provided his protection.
Seleznev hacked card services using three different “nicknames”: nCux, Track2 and 2Pac, connected with three periods of his hacking activity.

He was the first to use on the carders forums, where he had sold stolen card data since 2002, then he began to use the “nickname” of Track2 and used the nickname of 2Pac before his arrest.
The nCux identification took place at the beginning of 2009, when it was lit up on many carders forums, on this slide you see his message about the sale of these cards: “Dear customers, do not miss your chance - all AMEX cards for $ 1 each, VISA, MC , DISCOVER - $ 5 piece. The “Great Sale” is related to the fact that in May 2009 Roman declared that he would retire and stop hacking. His activity in this field has been monitored since 2002, when he began selling cards with all the data, including his name, password, date of birth and Social Security number. In 2005, he took into account that the stolen credit card data enjoyed great popularity and purchasing power, and developed vigorous activity. Because of this, he came to the attention of the Washington division of the Secret Service of Cybernetic Intelligence. They began to monitor his activity on the Internet and realized that this was a “big player” and began to try to find out who exactly was hiding behind the “nickname” nCux. In fact, the transliteration of this “nickname” in Russian meant “psycho” - this was the nickname awarded to Roman for his “explosive” character.
During the surveillance period from 2005 to 2009, the CIS Secret Service obtained quite a lot of information based on the “excavations” of open Internet trolling - a good “old-fashioned” investigative work.

In May 2009, they, together with the FBI, met in Moscow with the FSB and reached agreements on information exchange, after which it was literally a month, and Seleznyov disappeared from the Internet, destroying all the known FBI accounts. He posted this post in May, and disappeared in June.
This threw the Secret Service back and forced her to rethink how to conduct an international investigation and exchange information in this particular case.

Naturally, Seleznyov was not going to retire - he just changed his “nickname” and used Track2 and Bulba nicknames throughout 2009-2012. This slide shows the new post of Seleznev, who began to re-create his empire on the site carder.su, the most authoritative resource of carders, where Roman already had a reputation as a solid seller. This is evidenced by the mark in the upper left part of the message under the “nickname” This prompted the Secret Service that it was not just some new hacker who got a little stolen card from his “stash”, he had weight and fame among the users of this resource. The site administration even provided him with a monopoly in this matter, throwing out the smaller competitors of Seleznev, who offered similar goods.
CIS came to the conclusion that this is indeed a major player, and they immediately marked it on their “radar” and in May 2010 began an investigation. At about the same time, a local employee of our office, David Dunn, took part in a SWAT operation in Idaho, in the city of Ker-D'Alene, which was held at Shlotsky's Deli, a fast-food chain restaurant, about the leakage of visitors' credit card data. He inspected computer equipment there and confiscated RAM, where he unexpectedly discovered that Shlotsky's Deli was connected to the network via a Russian IP address. David took note of this fact, and after a few weeks or a month, a lot of stolen credit cards surfaced on the network, which could be traced to the data breach, and the Shlotsky restaurant’s computer turned out to be this point. After this, CIS invited Dunn to participate in the episode of the investigation of the case related to the equipment found in this restaurant.
Detective Dunn examined the computer of the suspect who had been confiscated in a restaurant, and found that the guy was looking at these two sites: Track2.name and Bulba.cc and chatted with a man named Track2.

He told him that his website Track2.name was covered, but a restaurant employee could sell card numbers on another site, Bulba.cc. The detective began to investigate both these sites to find out whether one hacker is hiding under these two "nicknames". He investigated the domain registration and found out the e-mail box from which the registration occurred, examined other mailboxes located in the USA, also associated with these accounts. Eastern Virginia supported the investigation of this case together with CIS, and in October 2010 they began to collect warrants for information. Detective Dunn had been expecting information for several weeks, because this is not the kind of thing that can be done overnight. In addition, some orders were returned, as there were cases when postal registrars refused to provide information.
And while he was waiting, on October 21, 2010, the second hacking took place - this time at one of the oldest Broadway Grill restaurants on Capitol Hill in Washington.

Detective Dunn arrived in Washington and, together with a local detective, began to study point-of-sale computers. They found out that the computers were set up very poorly with regard to ensuring the security of visitor information, since they stored data of 32 thousand credit bank cards in the form of simple text files. And this information went to the same IP address that was used in Shlotsky's Deli restaurant computers in Idaho. Here, the detective was able to advance a little further, as he managed to find out that someone had placed malicious software on Broadway Grill computers, which redirected the data to the malicious server while manually typing the address associated with the same IP address as Shlotsky's Deli.
Detective Dunn realized that now he had the opportunity to investigate the crime at home, so there is no longer any need to travel to Virginia or Idaho and you can bring a case here in the western district of Washington.
Then the matter began to rapidly unwind. During November 2010 - February 2011, the detective found out who registered the sites of the carding. He found Yahoo's mailboxes that led to the HopOne server in McLean, Virginia. Here he found out that from the IP addresses of computers in Shlotsky the card numbers were sent to a server in Russia.

When researching Yahoo accounts, he found out who bought HopOne server at McLean. For this, he conducted a legal penetration testing on the Yahoo server in order to track incoming and outgoing connections. This did not allow to explore the content, but gave him the IP addresses of incoming and outgoing connections, the numbers of some ports, the amount of data transferred. In addition, he saw that this server was connected to hundreds of computers throughout the United States, many of which were installed in restaurants. When he began to check their IP addresses, he learned that almost all of these computers were connected to the HopOne server, and found dozens of victims across the country who used points of sale in these restaurants.
The next slide shows evidence of malicious interference with computers that made credit card payments in many restaurants and cafes.

Shows the IP devices with which this malware was connected and sent the card data to the same HopOne server.
The following shows the infrastructure of this criminal scheme. There is nothing special here - this is a regular botnet network using several levels of data transfer.

Roman's computer is shown in the upper left corner. Detective Dunn discovered many hacking tools on the HopOne server that allowed him to recreate the Seleznev scheme. The Russian hacker scanned the ports of the payment terminal of the victim to find open RDP connections. As soon as he found such a connection, he hacked it with the help of a Brute-force attack with password selection and downloaded the card data to the user's server under the Shmak / Smaus nicknames with the IP address 188.120.255.66, the HopOne server with IP 66.36.240.69, and the Ukrainian server with IP 188.95.159.20. From there, the data came to the sites of carders - sellers under the nicknames of Track2 and Bulba.
On the left, you see the Yahoo mailbox that was used to register the Shmak / Smaus server, on the right, the Yahoo mailbox for Track2 and Bulba. In this case, the middle mailbox associated with Track2 was also connected to the HopOne server. A study of the HopOne server led to the discovery of hundreds of files that contained almost 400,000 credit card numbers. All of them were stored very conveniently for us, since they contained the IP addresses of the victims. This allowed us to quickly identify all the victims and gather more evidence.
As for the email addresses, they allowed us to identify Seleznev. He used one of the addresses of the Yahoo email service, which received various notifications. In the rubensamvelich@yahoo.com box, we found a letter about the successful registration of Roman Seleznev on PayPal on September 19, 2009. This was one of the strongest evidence against Roman, which was discovered by Detective Dunn. The previous slide shows that the rubensamvelich account led to the sites of stolen card sellers, so using this PayPal sign-up box was the biggest mistake Roman had made.

He did not think that the basis of American payment systems is to keep copies of such messages about the user's registration, where all his identification data is available. Here is the address of his registration in Vladivostok, which served as the identification of the person during the passport check during the arrest.
The second account, boookscafe@yahoo.com, which we found was used by Roman for many years. This was another mistake Seleznev, since he used this box back in 2006.
.

The boookscafe box did not help in investigating Seleznev’s hacker network infrastructure, but it helped to establish his connection with the user, known by his nickname nCux. We traced many related things, including ordering a bouquet of flowers for his wife. A postcard was attached to it with the words that “you are the most beautiful, but Eve is still more beautiful than you”! Eva is the name of his daughter, which was also inscribed on his passport, and was another proof of identification during the arrest. We also found his order for a Russian online store, with a home address in Vladivostok, placed with the help of this mailbox.
In the end, we found the most significant evidence on the HopOne server, where he kept all his hacking tools for hacking and the numbers of stolen credit cards. Seleznyov used this server to book a flight for an Indonesia-Singapore flight, and his personal data and the number of a Russian passport were indicated on the reservation form. The coincidence of the data of this order with the data of the passport served as another proof during his arrest. In Indonesia, his second home was located.

The Secret Service put all this evidence together, and together with Detective Dunn began to look for possible evidence of Seleznev’s involvement in other carder frauds. The next slide shows evidence that all such cases are somehow connected with each other, and carders have been working with each other for a long time and are connected with one another with common interests.
This 2007 chat is from an investigation conducted by the Department of the Eastern District of New York. If you remember, the investigation began in 2002-2003. It concerned the hacker community Carder Planet and was very successful for the New York government. Mr. Carranza was one of the detainees in this case, and a chat between him and a certain nCux 111 was discovered on his computer. He told him his real data - his first name, last name, home address in Vladivostok, two mailboxes, among which was indicated and boookscafe@yahoo.com. These data were required by Karranze for the deal with Seleznyov.

After gathering all this evidence, Detective Dunn and a representative of the prosecutor's office appealed to the Grand Jury in 2011 and received an indictment that imputed Roman Seleznev, known under 9 hacker nicknames, committing computer crimes, fraud with bank cards, using funds to hack traffic and etc.

Unfortunately, shortly thereafter, Roman, being in Morocco, was seriously injured by the explosion of a cafe in Mogadishu on April 28, 2011 during a terrorist attack. He and his wife were sitting on the 2nd floor of the restaurant, which was heavily destroyed by a bomb. He was taken to Moscow, where he spent several months in a coma and underwent several operations. Detective Dunn went to the bulba.cc website several times to check the activity of his administrator, however, they didn’t use this seller-administrator account, only messages from users appeared on the site who knew that an accident had happened to the “boss” and wished him a speedy recovery . Finally, in January 2012, this store of stolen cards was closed.
2011-2013 , . , , , . , .
, , , . , , .
, , , . , .
– 2pack.cc, 2013 2014. , . , CIS. , , , - Home Depot Neiman Marcus Target . , .
, , – , . , , , . .
, - – . 2014 , , . , , : « »!, : « »?
20 DOJ, -. , – , .

6 4 , . 1 , 3 5 , 3 . 3 . .
, .

, , , – , iPhone, , . , , «» nCux, Smaus, Ochko123. , – smaus, shmac, ochko. , . Ochko123! , «» – « » (butthole ).

– , . 1,7 , , 1,7 . .
-, , , , , , . , , , , , , . , MSR 206, , , , , .. .
, ? PACER – , , , . – , , «» - , , Bulba.
, , , ?
, 2 . , « » . , , . : « , »! : « , ». : «, … , ».

, 10 . , , .
, , « », « », « », « » . , . , - , Black Hat, .

, , - , , . , - , , , , . , , , . Windows 8, , .
, , , . , , , , .

«» Windows, , , , USN . , , . , 21 3- , KANIFUSHI. «» , . , , 20 . SIM-, , «». , «».
. , , , , - , . smaus, , .

SRAM , , , TOR. , , .
, slack space, . , , . , «» , . , 8 . 38 27 .

.
:
— , , , . , , , .
Question:
— - , ?
:
— , .
Question:
— - , ?
:
— , , - , , .
Question:
— , , ?
:
— , . , , , .
Question:
— 2011 2014 ?
Answer:
— , , , , .
Question:
— , , « ». , ?
Answer:
— , , , , .
Question:
— , ?
Answer:
— , 27 , , , 169 . , , , . , . , , . 400 , , , , .
Question:
— , ?
Answer:
— , , .
Question:
— iPhone ?
Answer:
— Apple , , .
Question:
— ?
Answer:
— 3700 .
Question:
— , 2009 ?
Answer:
— , .
Question:
— , , POS ?
Answer:
— , , , 32 , .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/354560/
All Articles