Survey: more than half of e-banking systems contain critical vulnerabilities
Experts at Positive Technologies analyzed the level of security of remote banking services (RB) systems. The statistics collected for 2017 suggests that, despite the general improvement in the situation with the protection of RBS, financial institutions still have work to do - more than half of the systems contain critically dangerous vulnerabilities.
Security Trends of RBS Systems
Most of the RBS systems reviewed (68%) were developed by financial institutions themselves. In 2016, applications created by banks contained two times less vulnerabilities than systems deployed on ready-made platforms, but now they have changed: in applications built on boxed solutions, less critical vulnerabilities have been found. Vendors began to pay more attention to security issues, while banks still lacked experienced developers on the staff and a well-structured process of safe development.
')
On average, in 2017, each RB System accounted for 7 vulnerabilities, which is more than the 2016 figure, when each financial application had only 6 deficiencies.
Online banking security
At the same time, the number of high and medium risk vulnerabilities is reduced. For example, in a third of online banks there were no critical security bugs, and a year earlier, high-risk vulnerabilities were in all but one of the financial web applications.

The most common vulnerabilities of online banks in 2017 were “Cross-site scripting” (75% of systems) and “Insufficient protection against data interception attacks” (69%) that allow attacks on bank customers (for example, intercepting cookie values). or steal credentials). More than half of online banks (63%) contained a high level of risk “Insufficient authorization” vulnerability, which allows an attacker to gain unauthorized access to the functions of a web application not intended for this level of user. In addition, vulnerabilities in 94% of online banks could be used by cyber criminals to access customer information and personal information.
Thus, despite certain improvements in the security of online banks, they still contain vulnerabilities that can lead to extremely serious consequences.

Mobile Financial Security
Most of the RBS systems analyzed (61%) accounted for mobile applications, among which server-side parts of mobile applications and clients for Android and iOS mobile operating systems were approximately equally distributed.

Compared to the previous similar survey in 2016, the share of high vulnerabilities (29% instead of 32% in 2016) and the average risk level (56% instead of 60%) decreased. Accordingly, the proportion of low-risk vulnerabilities has increased; Companies seek to take action first to eliminate critical vulnerabilities.
Nevertheless, in half of the systems (48%) at least one critically dangerous vulnerability was detected. In 52% of mobile banks, vulnerabilities allowed to decrypt, intercept, pick up credentials for access to a mobile application or bypass the authentication process altogether. As a result, an attacker may be able to perform operations in a mobile bank on behalf of a legitimate user.
At the same time, iOS applications were again protected better than their counterparts for Android. The share of high-risk vulnerabilities in iOS applications was only 25%, while in Android applications it is 56%.
Not so bad
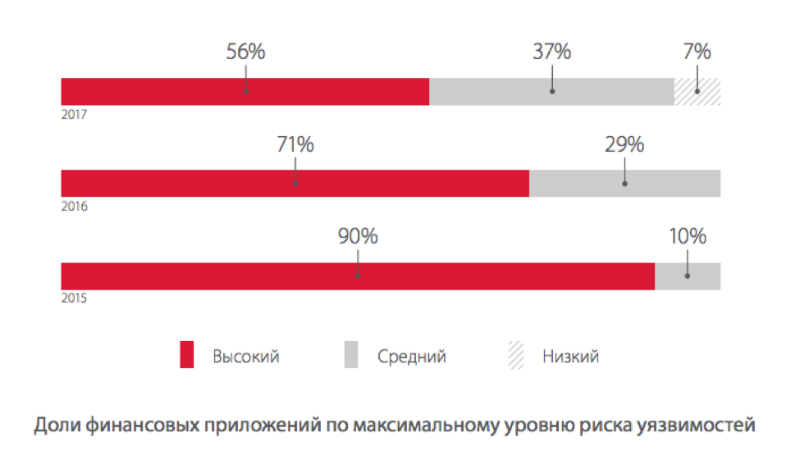
The proportion of RBS systems in which critical vulnerabilities are detected decreases every year. If in 2015, high-risk vulnerabilities were contained in 90% of the analyzed systems, and in 2016 in 71%, then in 2017, only in 56%. This is a positive moment.
At the same time, despite a noticeable increase in the level of security, the current flaws still pose serious threats to banks and their customers - 44% of mobile applications could compromise customers' banking information, and in 13% we encountered the “Execution of arbitrary code” vulnerability, which allows get full control over the DBO server, which is fraught with bank reputational and financial losses.
To reduce the likelihood of a successful attack, experts from Positive Technologies advise financial companies, in addition to analyzing application security, to pay attention to analyzing their source code of applications. Prior to the release of fixes for the identified vulnerabilities, it is recommended to use the web application firewall, and after removing them, check the effectiveness of the measures taken.
When creating financial applications on their own, banks should pay more attention to security issues at early stages, both at the design stage of applications and the preparation of technical tasks for programmers, and in the development process.
The full version of the RBS security study is available at the link (you will need to register to download the file).
Source: https://habr.com/ru/post/354540/
All Articles