Operation Orangeworm: hackers infect medical equipment around the world using the Kwampirs Trojan

Symantec experts have published a report on the activity of the Orangeworm hacker group, which has created malicious software that attacks medical institutions in different countries. The target of the attacks is the theft of confidential information.
What is the problem
According to the researchers, the attackers have been at least since the beginning of 2015. Orangeworm victims include medical facilities in the USA, Europe and Asia. Most often, computers that control the operation of X-ray machines and MRI scanners are attacked.
For infection, the Kwampirs Trojan is used. After entering the network of the medical institution, the malware begins to collect data about the system and sends it to a remote server. After that, if the computer contains potentially interesting information for hackers, it is stolen.
')
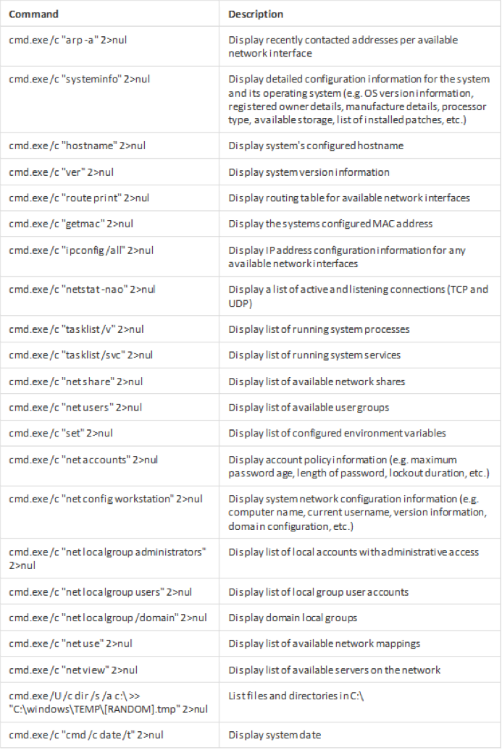
Kwampirs command set
What hackers need
The Orangeworm grouping attacked not only organizations from the healthcare sector, their attention was also attracted by companies from the IT sector, manufacturing, and even logistics.
According to researchers, this is due to the fact that the main purpose of the attackers was the theft of confidential data related to medicine - for example, patents for development in this area, which can be resold on the black market. Therefore, not only end users of such products were attacked, but also companies that worked on them on a contract basis.
Why the attack lasted three years
The developers of Kwampirs did not implement serious means of disguise, while the Trojan was actively copying itself to the available devices. Such a long-term activity of the Orangeworm grouping became possible due to the generally unsatisfactory level of information security in the healthcare sector. In particular, medical institutions often use outdated hardware and software, do not install antiviruses and updates. All this leads to the fact that for hackers it is easy to penetrate into the network of the organization and gain a foothold there for a long time.
For the timely detection of vulnerabilities and similar attacks, experts at Positive Technologies recommend using specialized information security tools. For example, Orangeworm could have been prevented if health facilities used cybersecurity incident management systems (for example, PT ISIM ) and security and compliance control tools (for example, MaxPatrol ).
Source: https://habr.com/ru/post/354304/
All Articles