ESET: Lazarus Cyber Group Switches to Central America
Lazarus Group gained fame after a cyber attack on Sony Pictures Entertainment in 2014. In 2017, the group remains active using a wide range of malicious tools, including the KillDisk wiper.
Our study showed that Lazarus is most likely behind the attack on online casinos in Central America and some other goals at the end of 2017. In these incidents, the attackers used the same tools, including KillDisk, which was run on compromised devices.

Lazarus hackers were first identified in a Novetta Operation Blockbuster report in February 2016; US CERT and FBI called this cyber group Hidden Cobra . The band gained wide popularity after the attack on Sony Pictures Entertainment .
')
Subsequent attacks related to Lazarus attracted the attention of information security specialists who relied on Novetta materials and other research — hundreds of pages of descriptions of attackers' tools: attacks on Polish and Mexican banks , the WannaCry epidemic , phishing attacks on US Department of Defense contractors , etc. All of these studies allow Lazarus to be identified as a source of attack.
Please note that the list of Lazarus tools (all the files that information security specialists associate with the activity of the group) is quite wide, and we believe that there are many subfamilies of them. Unlike the toolboxes used by other cybergroups, the source code of the Lazarus tools has never been revealed as a result of a public leak.
In addition to special programs, Lazarus use projects that are available on GitHub or provided on a commercial basis.
In this section, we will look at some of the tools found on the servers and workstations of the online casino network in Central America, and explain how their relationship with Lazarus was established. ESET antivirus products detect malware groups like Win32 / NukeSped and Win64 / NukeSped. They were used in combination with samples of destructive KillDisk software.
Almost all of these tools are designed to run as a Windows service. Administrator rights are required for this, which means that attackers must have these rights during development or compilation.
TCP backdoor
Win64 / NukeSped.W is a console application installed in the system as a service. One of the first stages of execution is the dynamic loading of the required DLL names onto the stack:

Similarly, procedure names for the Windows API are built dynamically. In this particular sample, they are visible as plaintext; in other past samples that we analyzed, they were encoded in base64, encrypted or placed on the stack character-by-character:
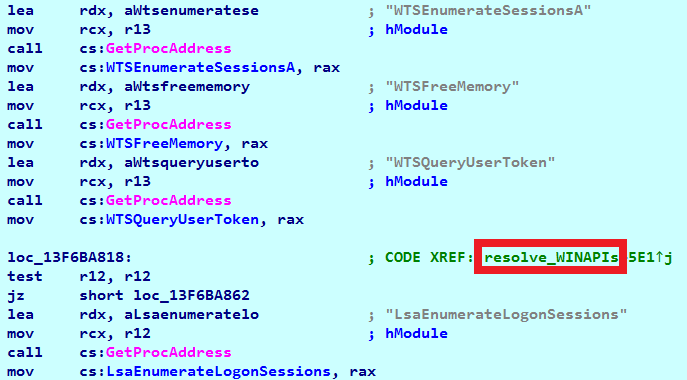
These signs are typical Lazarus malware traits. Another typical feature of the Lazarus backdoor is also visible in this backdoor: it listens on a specific port, which is an indicator of firewall blocking:
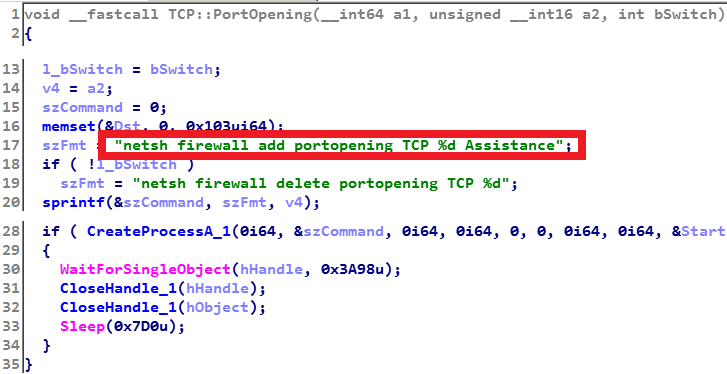
The backdoor supports 20 commands, the functionality of which is similar to the previously analyzed Lazarus samples (note that the command names are not set by the attackers, but were created by the ESET virus analyst):
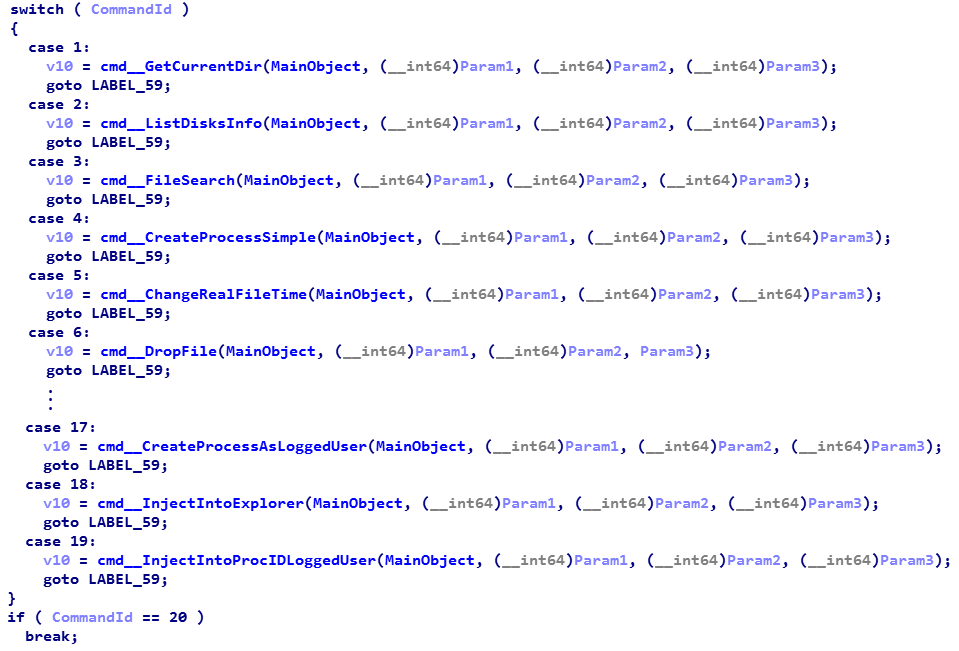
The backdoor creates several files in the file system. The listening port is stored in a text file named
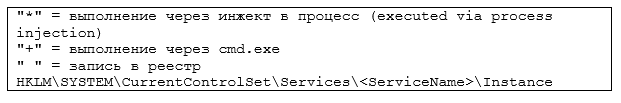
In the case of the “+” option, the output
Session hacker
The Win64 / NukeSped.AB console application creates a process on behalf of another user currently logged on the victim's system (similar to command number 17 from the TCP backdoor previously described).
This is a protected version of Themida described by Kaspersky Lab. In our case, it was installed as
The static view shows the same file properties in both of these selections: the same PE compilation timestamp, identical Rich Header linker data (pointing to the Visual Studio 2010 linker (10.00)), and some of the version information for resources matches:

Although the PE timestamp and resources were stolen from the legitimate Microsoft
Our consistent dynamic analysis confirmed that this file, found in the compromised online casino network, is associated with a session hacker used in attacks against Polish and Mexican sites.
Bootloader / Installer
This is a simple command line tool that takes several parameters. It is designed to work with processes (injection / deletion of a process using a PID or name), services (shutting down / reinstalling a service) or files (reset / deletion). Functionality is determined by the parameters.
KillDisk is the common name by which ESET products detect destructive malware with the erase disk function — damage the boot sectors and overwrite and then delete (system) files, followed by a reboot, to make the device unusable.
Although all versions of KillDisk have similar functions, the sample code base does not always match. KillDisk has many subfamilies, whose names are distinguished by suffixes (in our case, Win32 / KillDisk.NBO). Variants of subfamilies with common code fragments are sometimes used in different cyber campaigns, which may indicate a common source of attacks, as in this case.
Other versions of KillDisk were used in targeted attacks on Ukrainian sites in December 2015 and December 2016 , but these samples belong to other subfamilies and, most likely, are not related to new attacks.
Studying the incident in Central America, we found two Win32 / KillDisk.NBO variants in the compromised network. Malicious software has infected more than a hundred machines in the organization. There are several possible explanations for his appearance: the attackers could hide the traces after the attack, or use KillDisk for extortion or cyber sabotage. In any case, this is a large-scale infection within the same organization.
The data of our telemetry, as well as the simultaneous use of versions of Win32 / KillDisk.NBO and other well-known Lazarus tools in a compromised network indicate that it was Lazarus hackers who deployed KillDisk, and not any other cyber group.
Analysis of the two samples showed that they have many common code fragments. In addition, they are almost identical to the KillDisk version, which was used in attacks on financial institutions in Latin America studied by Trend Micro .
The KillDisk samples found on the online casino network use the following path:
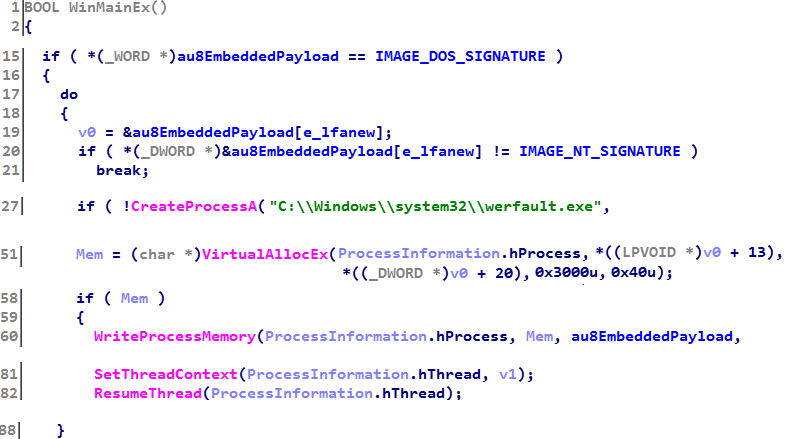
The actual built-in payload is injected into the
One of the options is protected by a third-generation commercial VMProtect, which makes unpacking difficult. Most likely, the attackers did not buy the VMProtect license, but used the available pirated or leaked copies of the Internet. The use of software protection tools is characteristic of the Lazarus group: in attacks on Polish and Mexican banks in February 2017, they used Enigma Protector; Some of the Operation Blockbuster samples reported by Palo Alto Networks used an older version of VMProtect.
Typical Lazarus String Format
Among the numerous characteristics that allow us to attribute the authorship of the samples and the origin of the attacks to the Lazarus group, it is necessary to note the format of the lines. The table below shows the formatted strings found in the above samples, as well as other TCP backdoors associated with Lazarus:

By itself, this fact cannot be proof, but, looking for similar string formatting in all malware samples collected by ESET, we found them only in samples supposedly related to Lazarus. Therefore, we can assume that the presence of these lines indicates the authorship of Lazarus.
There are at least two tools available that attackers have used.
Browser Password Dump
This tool is designed to recover passwords from popular web browsers. Since December 2014, he has been using old, well-known methods. It can be used in the latest versions of Google Chrome (64.0.3282.186), Chromium (67.0.3364.0), Microsoft Edge (41.16299.15.0) and Microsoft Internet Explorer (11.0.9600.17843). It is not compatible with the latest versions of Firefox or Opera.
Mimikatz
The attackers also used a modified version of the Mimikatz tool designed to extract Windows credentials. It takes one parameter - the name of the file to store the output. If the parameter is not specified, the output file named
Most of the tools described above were downloaded and installed on workstations using malicious droppers and loaders used in the initial stage of the attack. In addition, we have seen indicators that indicate the use of remote access tools, including Radmin 3 and LogMeIn, to monitor target devices.
A recent attack on online casinos in Central America suggests that Lazarus hackers will recompile tools before each new campaign (we did not see identical samples anywhere else). It was a complex multi-step attack, in which dozens of secure tools were used, which, being autonomous, hardly showed such a dynamic.
The use of KillDisk most likely served one of two purposes: the attackers hid their tracks after the espionage operation, or used destructive software for extortion or sabotage. In any case, the detection of malware on more than 100 workstations and servers of the organization indicates considerable resources spent by the attackers.
Our study showed that Lazarus is most likely behind the attack on online casinos in Central America and some other goals at the end of 2017. In these incidents, the attackers used the same tools, including KillDisk, which was run on compromised devices.

Lazarus Tools
Lazarus hackers were first identified in a Novetta Operation Blockbuster report in February 2016; US CERT and FBI called this cyber group Hidden Cobra . The band gained wide popularity after the attack on Sony Pictures Entertainment .
')
Subsequent attacks related to Lazarus attracted the attention of information security specialists who relied on Novetta materials and other research — hundreds of pages of descriptions of attackers' tools: attacks on Polish and Mexican banks , the WannaCry epidemic , phishing attacks on US Department of Defense contractors , etc. All of these studies allow Lazarus to be identified as a source of attack.
Please note that the list of Lazarus tools (all the files that information security specialists associate with the activity of the group) is quite wide, and we believe that there are many subfamilies of them. Unlike the toolboxes used by other cybergroups, the source code of the Lazarus tools has never been revealed as a result of a public leak.
In addition to special programs, Lazarus use projects that are available on GitHub or provided on a commercial basis.
Lazarus tools for attacking online casinos
In this section, we will look at some of the tools found on the servers and workstations of the online casino network in Central America, and explain how their relationship with Lazarus was established. ESET antivirus products detect malware groups like Win32 / NukeSped and Win64 / NukeSped. They were used in combination with samples of destructive KillDisk software.
Almost all of these tools are designed to run as a Windows service. Administrator rights are required for this, which means that attackers must have these rights during development or compilation.
TCP backdoor
Win64 / NukeSped.W is a console application installed in the system as a service. One of the first stages of execution is the dynamic loading of the required DLL names onto the stack:

Similarly, procedure names for the Windows API are built dynamically. In this particular sample, they are visible as plaintext; in other past samples that we analyzed, they were encoded in base64, encrypted or placed on the stack character-by-character:

These signs are typical Lazarus malware traits. Another typical feature of the Lazarus backdoor is also visible in this backdoor: it listens on a specific port, which is an indicator of firewall blocking:

The backdoor supports 20 commands, the functionality of which is similar to the previously analyzed Lazarus samples (note that the command names are not set by the attackers, but were created by the ESET virus analyst):

The backdoor creates several files in the file system. The listening port is stored in a text file named
%WINDOWS%\Temp\p . The %WINDOWS%\Temp\perflog.evt contains a list of paths for binary files intended for injection, execution, or writing to the registry, depending on the starting character of the line:
In the case of the “+” option, the output
cmd.exe / c «% s 2 »% s» (or cmd.exe / c «% s »% s 2> 1» ) is written to % WINDOWS% \ Temp \ perflog.dat .Session hacker
The Win64 / NukeSped.AB console application creates a process on behalf of another user currently logged on the victim's system (similar to command number 17 from the TCP backdoor previously described).
This is a protected version of Themida described by Kaspersky Lab. In our case, it was installed as
C:\ Users\public\ps.exe . It has three parameters.The static view shows the same file properties in both of these selections: the same PE compilation timestamp, identical Rich Header linker data (pointing to the Visual Studio 2010 linker (10.00)), and some of the version information for resources matches:

Although the PE timestamp and resources were stolen from the legitimate Microsoft
PREVHOST.EXE file from Windows 7 SP1, there is no PREVHOST.EXE data available: the Microsoft source file was compiled and linked to Visual Studio 2008 (9.00).Our consistent dynamic analysis confirmed that this file, found in the compromised online casino network, is associated with a session hacker used in attacks against Polish and Mexican sites.
Bootloader / Installer
This is a simple command line tool that takes several parameters. It is designed to work with processes (injection / deletion of a process using a PID or name), services (shutting down / reinstalling a service) or files (reset / deletion). Functionality is determined by the parameters.
KillDisk Versions
KillDisk is the common name by which ESET products detect destructive malware with the erase disk function — damage the boot sectors and overwrite and then delete (system) files, followed by a reboot, to make the device unusable.
Although all versions of KillDisk have similar functions, the sample code base does not always match. KillDisk has many subfamilies, whose names are distinguished by suffixes (in our case, Win32 / KillDisk.NBO). Variants of subfamilies with common code fragments are sometimes used in different cyber campaigns, which may indicate a common source of attacks, as in this case.
Other versions of KillDisk were used in targeted attacks on Ukrainian sites in December 2015 and December 2016 , but these samples belong to other subfamilies and, most likely, are not related to new attacks.
Studying the incident in Central America, we found two Win32 / KillDisk.NBO variants in the compromised network. Malicious software has infected more than a hundred machines in the organization. There are several possible explanations for his appearance: the attackers could hide the traces after the attack, or use KillDisk for extortion or cyber sabotage. In any case, this is a large-scale infection within the same organization.
The data of our telemetry, as well as the simultaneous use of versions of Win32 / KillDisk.NBO and other well-known Lazarus tools in a compromised network indicate that it was Lazarus hackers who deployed KillDisk, and not any other cyber group.
Analysis of the two samples showed that they have many common code fragments. In addition, they are almost identical to the KillDisk version, which was used in attacks on financial institutions in Latin America studied by Trend Micro .
The KillDisk samples found on the online casino network use the following path:
C:\Windows\Temp\dimens.exeThe actual built-in payload is injected into the
werfault.exe system process:
One of the options is protected by a third-generation commercial VMProtect, which makes unpacking difficult. Most likely, the attackers did not buy the VMProtect license, but used the available pirated or leaked copies of the Internet. The use of software protection tools is characteristic of the Lazarus group: in attacks on Polish and Mexican banks in February 2017, they used Enigma Protector; Some of the Operation Blockbuster samples reported by Palo Alto Networks used an older version of VMProtect.
Typical Lazarus String Format
Among the numerous characteristics that allow us to attribute the authorship of the samples and the origin of the attacks to the Lazarus group, it is necessary to note the format of the lines. The table below shows the formatted strings found in the above samples, as well as other TCP backdoors associated with Lazarus:

By itself, this fact cannot be proof, but, looking for similar string formatting in all malware samples collected by ESET, we found them only in samples supposedly related to Lazarus. Therefore, we can assume that the presence of these lines indicates the authorship of Lazarus.
Additional tools
There are at least two tools available that attackers have used.
Browser Password Dump
This tool is designed to recover passwords from popular web browsers. Since December 2014, he has been using old, well-known methods. It can be used in the latest versions of Google Chrome (64.0.3282.186), Chromium (67.0.3364.0), Microsoft Edge (41.16299.15.0) and Microsoft Internet Explorer (11.0.9600.17843). It is not compatible with the latest versions of Firefox or Opera.

Mimikatz
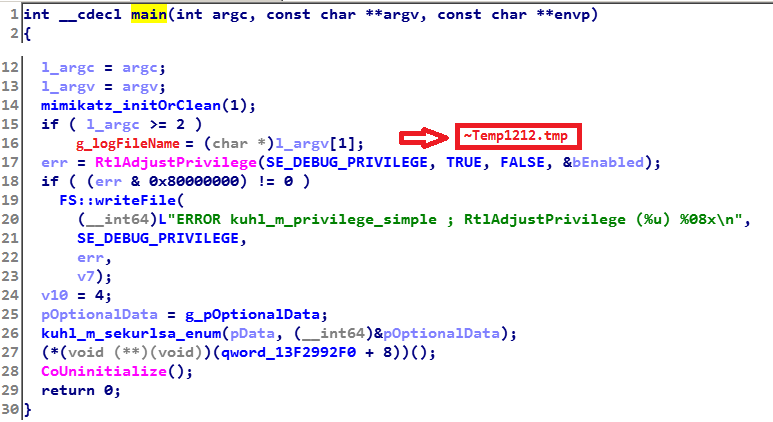
The attackers also used a modified version of the Mimikatz tool designed to extract Windows credentials. It takes one parameter - the name of the file to store the output. If the parameter is not specified, the output file named
~Temp1212.tmp is stored in the same directory as Mimikatz. The output contains hashes of Windows credentials of authorized users. The tool is often used in targeted attacks, in particular by the Telebots group in the Petya epidemic , as well as in Operation Buhtrap .
Infection vector
Most of the tools described above were downloaded and installed on workstations using malicious droppers and loaders used in the initial stage of the attack. In addition, we have seen indicators that indicate the use of remote access tools, including Radmin 3 and LogMeIn, to monitor target devices.
findings
A recent attack on online casinos in Central America suggests that Lazarus hackers will recompile tools before each new campaign (we did not see identical samples anywhere else). It was a complex multi-step attack, in which dozens of secure tools were used, which, being autonomous, hardly showed such a dynamic.
The use of KillDisk most likely served one of two purposes: the attackers hid their tracks after the espionage operation, or used destructive software for extortion or sabotage. In any case, the detection of malware on more than 100 workstations and servers of the organization indicates considerable resources spent by the attackers.
Samples
429B750D7B1E3B8DFC2264B8143E97E5C32803FF Win32/KillDisk.NBO
7DFE5F779E46855B32612D168B9CC5334F25B5F6 Win32/KillDisk.NBO
5042C16076AE6346AF8CF2B40553EEEEA98D5321 Win64/NukeSped.W trojan (VMProtect-ed)
7C55572E8573D08F3A69FB15B7FEF10DF1A8CB33 Win64/NukeSped.W trojan (Themida-protected)
E7FDEAB60AA4203EA0FF24506B3FC666FBFF759F Win64/NukeSped.Z trojan (Themida-protected)
18EA298684308E50E3AE6BB66D7321A5CE664C8E Win64/NukeSped.Z trojan (VMProtect-ed)
8826D4EDBB00F0A45C23567B16BEED2CE18B1B6A Win64/NukeSped.AB trojan (Themida-protected)
325E27077B4A71E6946735D32224CA0421140EF4 Win64/Riskware.Mimikatz.A application
D39311C74DEB60C736982C1AB74D6684DD1E1264 Win32/SecurityXploded.T (VMProtect-ed)
E4B763B4E74DE3EF24DB6F19108E70C494CD18C9 Win32/SecurityXploded.T (Themida-protected)
Source: https://habr.com/ru/post/354286/
All Articles