Own Goal We are testing DDoS protection.

The topic of DDoS attacks, their types and methods of protection has been repeatedly raised by our authors in the past . We are closely following the wishes of our readers and therefore today we will demonstrate the DDoS protection service with a live example. In this article we will analyze a similar task: we will make a test web application, organize a stress test simulating a DDoS attack, and compare network load statistics with and without protection.
Under the cut there are many images and gifs.
We already wrote about the types of DDoS attacks and how to protect against them in our previous article . In addition to basic solutions for monitoring and filtering network traffic, Selectel provides enhanced protection against DDoS attacks . This level of protection adds an extra step to the traffic cleaning complex in the form of a special proxy server configured for specific applications.
')
In this article, we consider the case of an attack aimed at bandwidth overload, and specifically we use the DrDOS (Distributed Reflection Denial of Service) method, which uses the technique of reflection requests. This method is interesting because it allows you to multiply the volume of the attack compared to the throughput of the infected machine, and was chosen because it clearly shows the scale of the possible attack.
Action plan
We will conduct a demonstration of the DDoS protection service with the help of an experiment, the purpose of which will be to compare the performance of a web server under a DDoS attack with a connected service and without it. To do this, we will organize two stress tests with the same attack parameters on a previously prepared web server in the VPC via a secure and direct IP address. We will evaluate the degree of influence of the DDoS protection services on the filtering of unwanted traffic using the processor and network device utilization metrics. In addition, we use the service monitoring tool to determine the availability of a web server in different locations.
Web server :
- A simple Wordpress site deployed with a standard LAMP stack;
- Virtual server in VPC with 1 vCPU and 1 GB of RAM on Ubuntu.
Monitoring tools:
- Netdata utility for viewing real-time system information;
- Monitoring the availability of services, in which we use a simple GET request to conduct a test.
Tool for stress test :
- IP Stresser , which provides the ability to create a test with an attack volume of up to 3 Gbps.
As a result of the tests, it is expected that with the connected service for protection against DDoS attacks, the service will not be interrupted. In the next part we will look at creating and configuring an application in a VPC and the process of activating the service. Then we will conduct stress tests and compare the readings of the metrics.
Setting up the application and connection services for protection from DDoS
As a medium for hosting a web server, we chose a virtual private cloud for the ability to quickly create a virtual machine and connect a public subnet:

We also included a public subnetwork in the allocated resources - a floating IP address is not suitable for working with the DDoS protection service:

Next, we will create a server within the project, using the ready image of Ubuntu 16.04 as a source for installing the system. In the network settings section, you need to select a connection through a previously reserved public subnet, as well as select and record the public IP address: we will need it later.

After installing the server, we will configure Wordpress using the standard LAMP stack :

Making sure that the application is working, we proceed to ordering the DDoS protection service.
Service activation Basic DDoS protection
Service ordering is carried out in the Networks and Services section in the Selectel personal account:
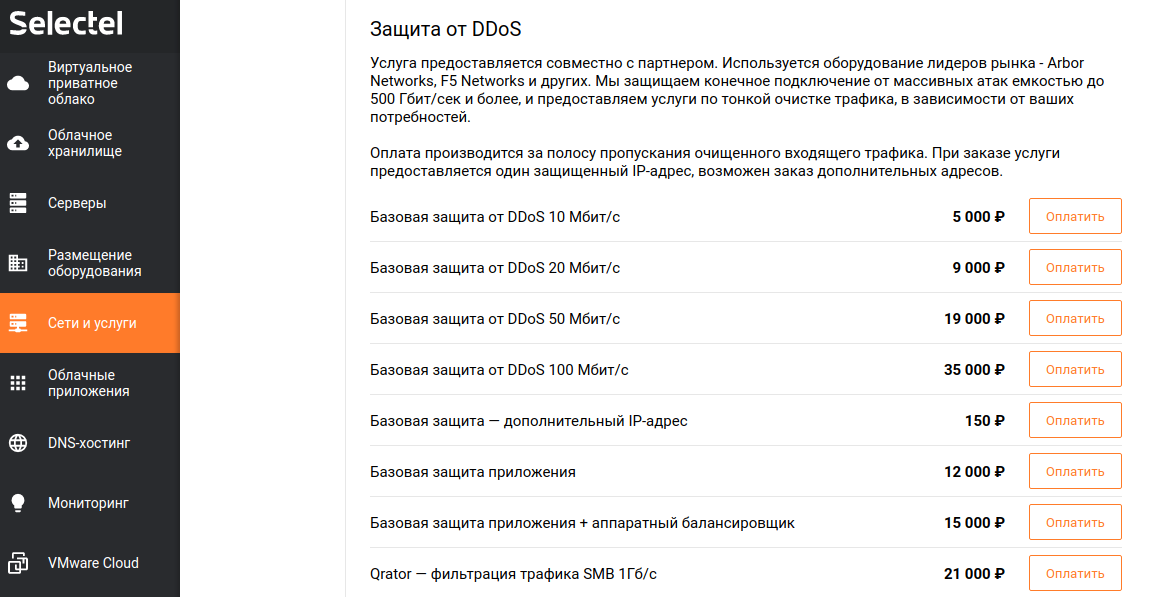
Select the item Basic DDoS protection 10 Mbit / s and make the payment for the service:

After the service is activated, a ticket will be created for technical support to configure protection for your application. The support employee needs to provide the IP address and type of application. After receiving all the necessary information, the protection will be configured. Additional information about connected protection and services will be in the support message in reply:

We were allocated a secure IP address, which we will configure later, and also provide information for access to the attack statistics service. In addition, as can be seen from the message, you need to configure the application to work with the new dedicated protected IP address, since the traffic arriving at the initial IP address will not be filtered.
Setting aliases is slightly different in different systems, in our example we use Ubuntu, where this is done by the following command:
$ sudo ifconfig eth0:0 95.213.255.18 up At this stage, it remains to test the operation and availability of the service through a secure IP address:

Stress test for unprotected IP address
Let us proceed to the stress test of the system on an unprotected IP address with the following attack settings:

The target host is an address that, when using the service in real time, will need to be hidden - the traffic going to it will not be filtered and will lead to a system crash.
Let's start the first stress test:
It can be seen that the processor is overloaded almost instantly and the volume of received traffic tends to 3Gb / s:
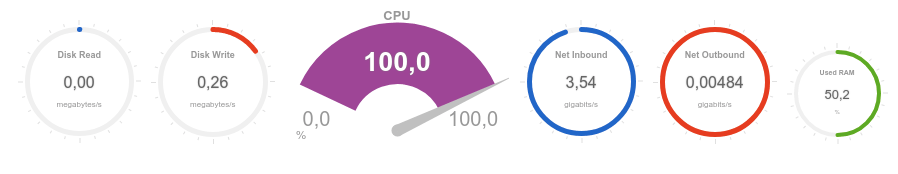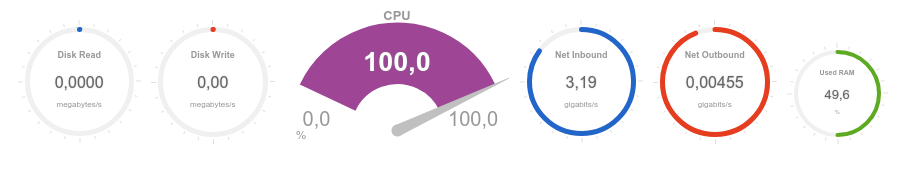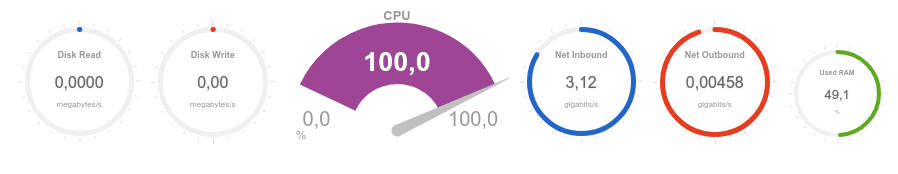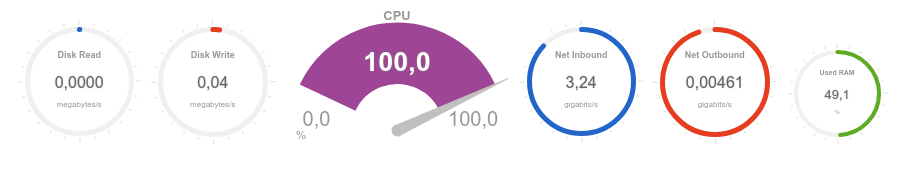
Now we estimate the availability and response time of the service in different geographical locations:
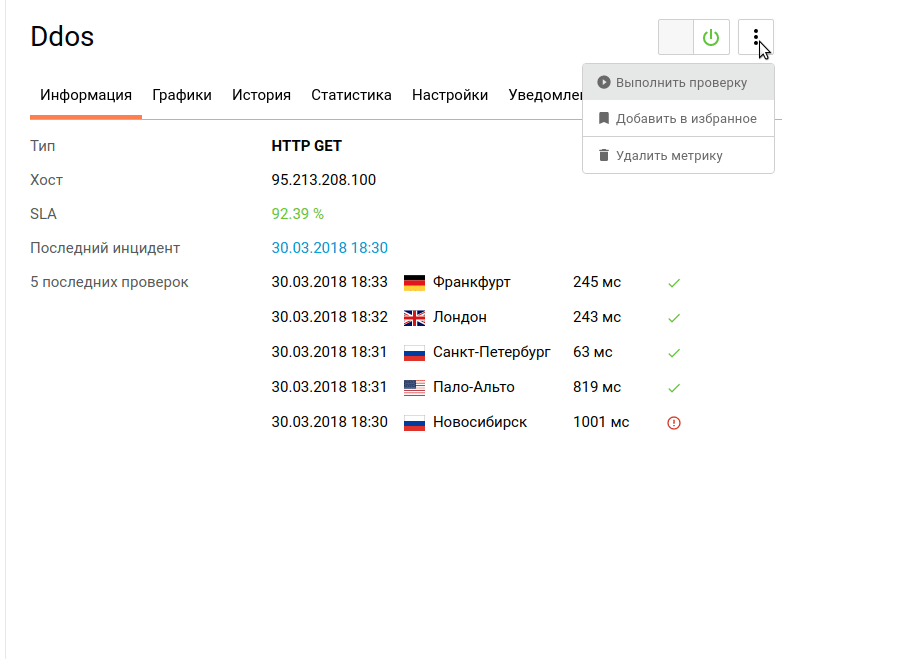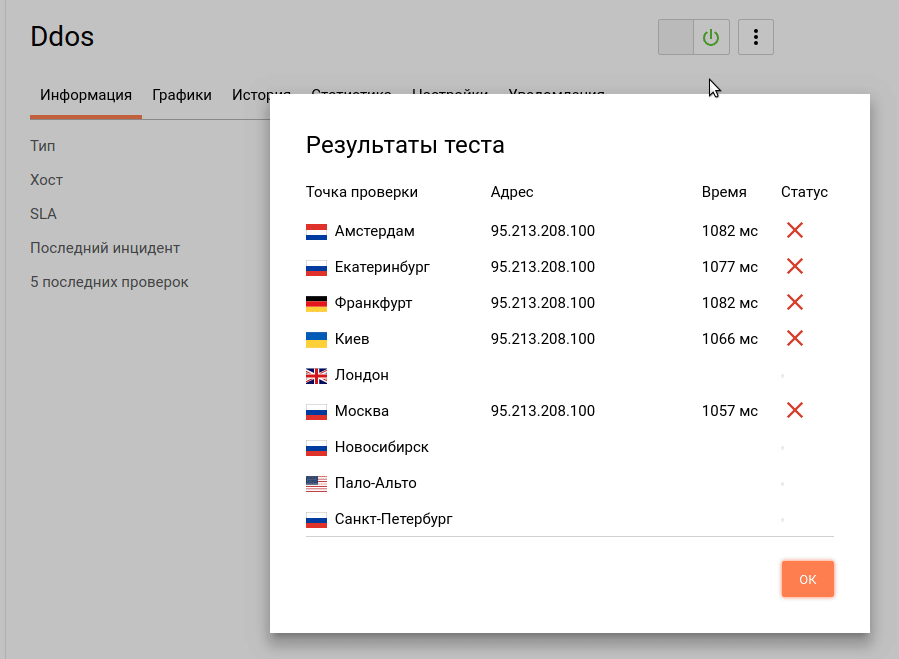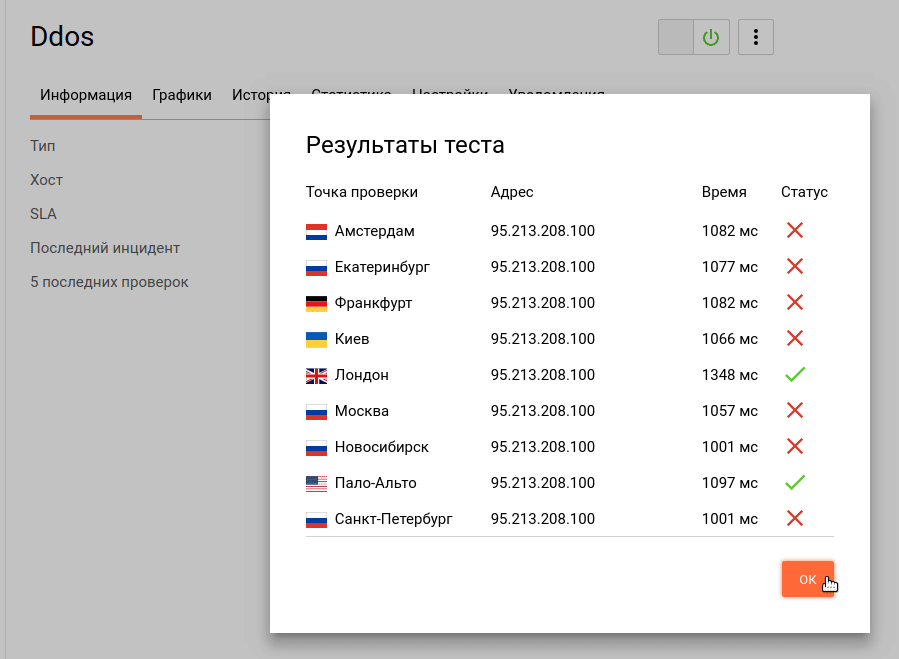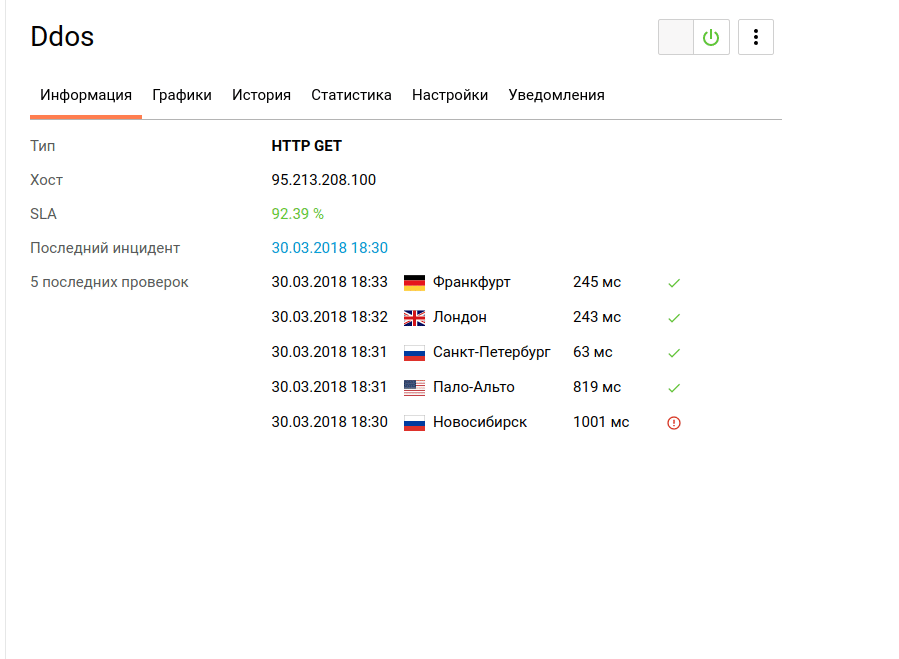
Most of the test points showed the inaccessibility of the specified service and a long response time, which indicates successful stress testing and the vulnerability of the current configuration to the transport level DDoS attacks.
Summarizing the results, it is obvious that the web server fully took over the entire volume of the test attack, and in case of an increase in the load, the application would fail. Next, we will test the availability of a web server with a connected service for protection against DDoS attacks, however in real systems it is highly desirable to take additional measures to ensure the security of the application at the program level.
Stress test for secure IP address
Using completely similar parameters for an attack other than an IP address, we will launch a stress test:
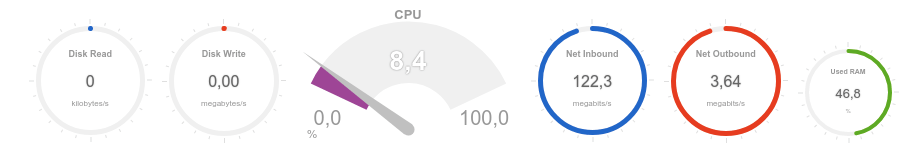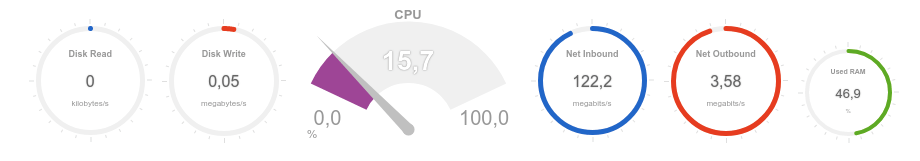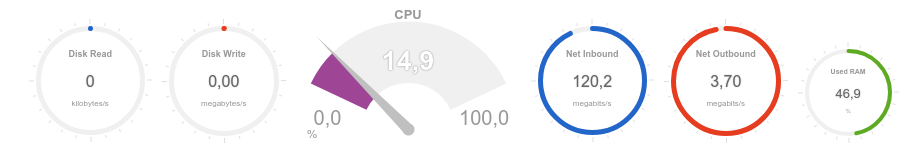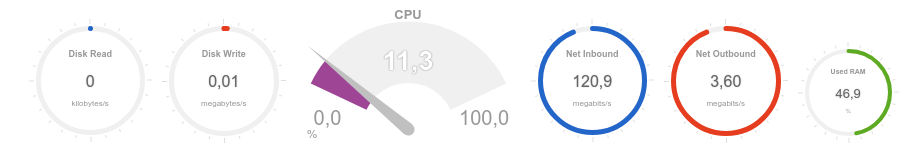
It can be seen that the recorded volume of incoming traffic is about 120 Mbps, and the processor load is about 20%:
We now turn to testing the availability and response time of the web server through the monitoring tool:
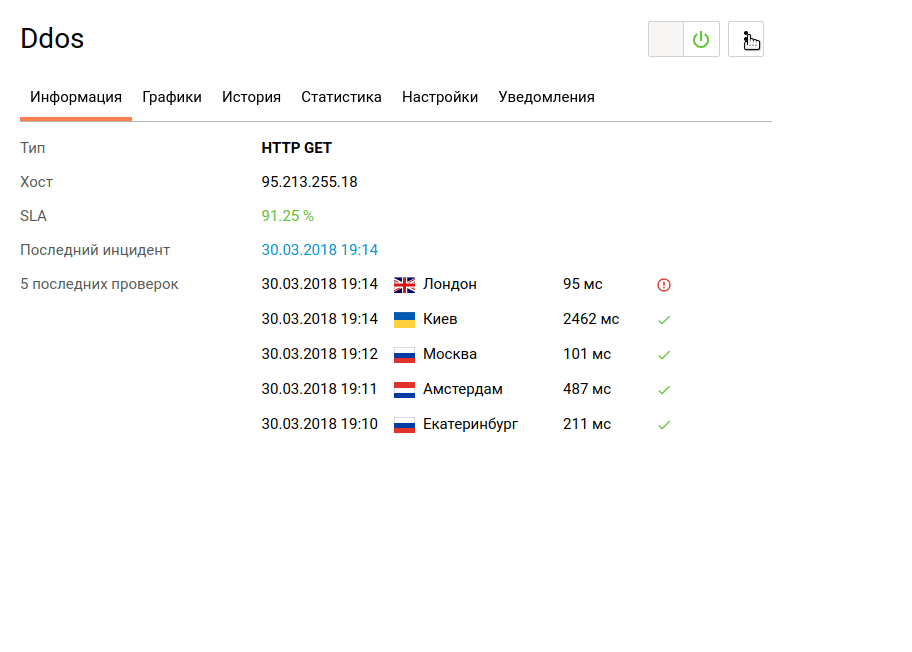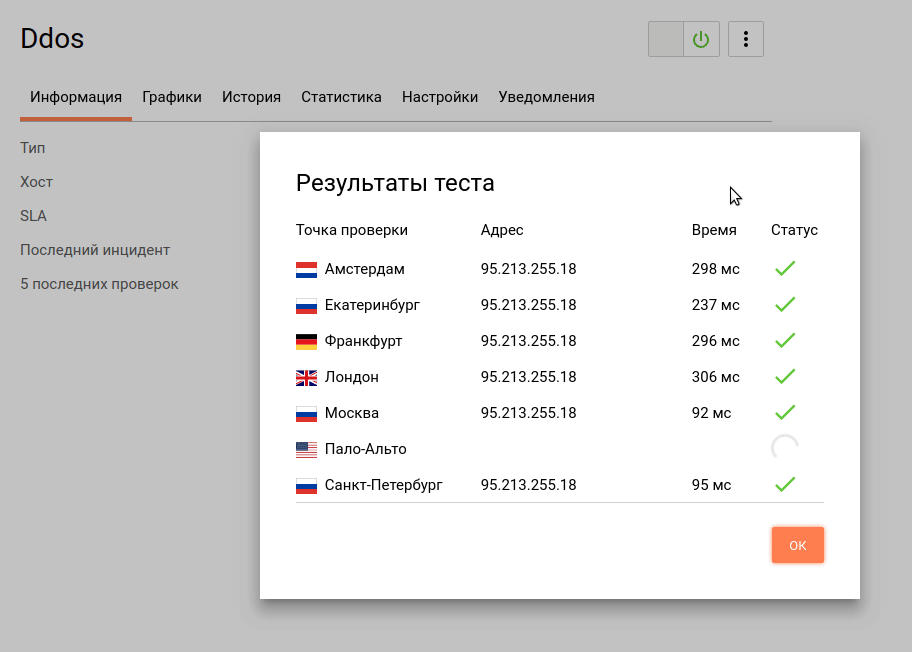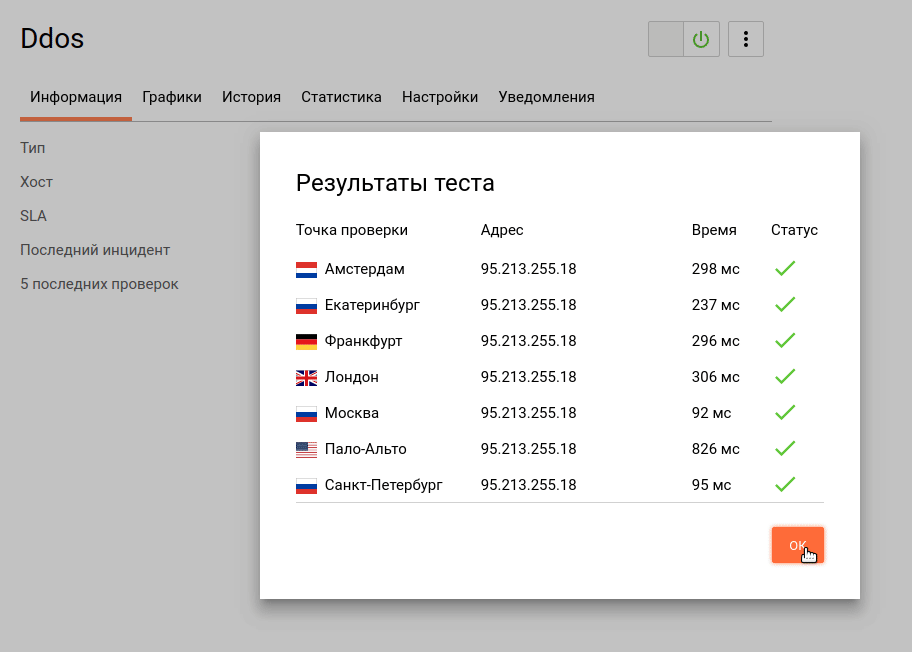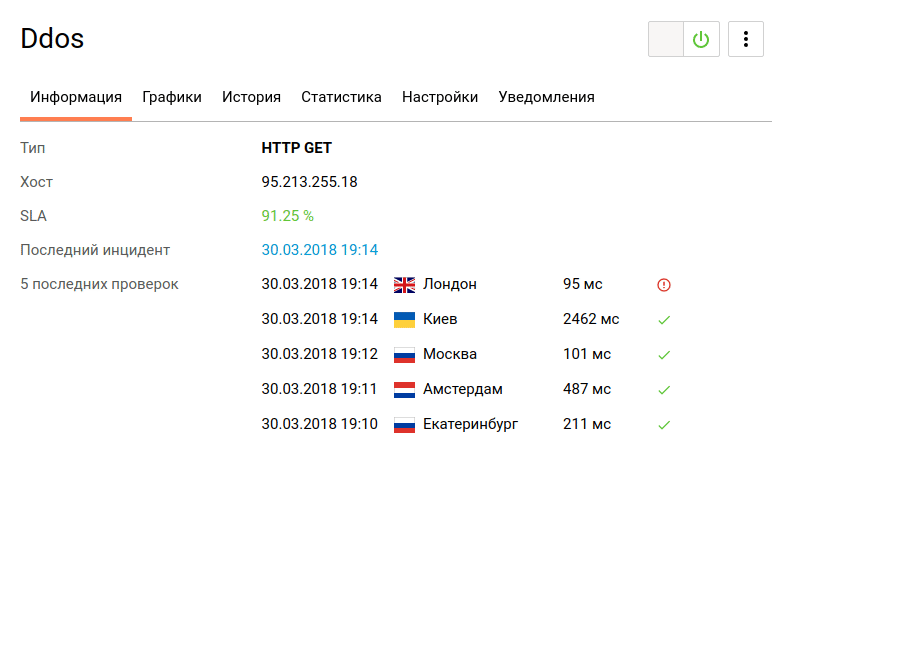
Already we can say that the use of such services to protect against DDoS-attacks provides a certain level of web server security.
Attack Monitoring and Statistics
As soon as the attack on the protected address begins, the client is notified of this event by email:

The following web interface is available for viewing real-time attack information:
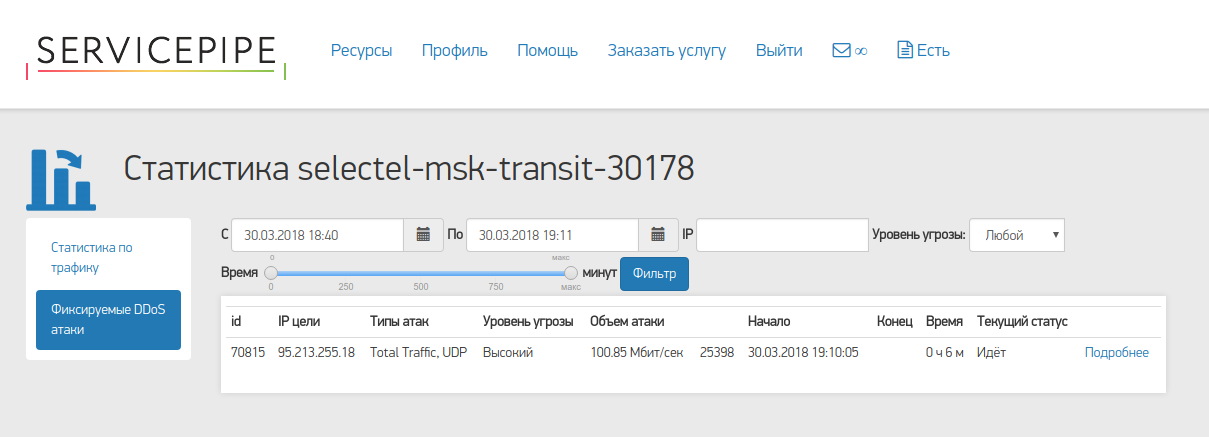
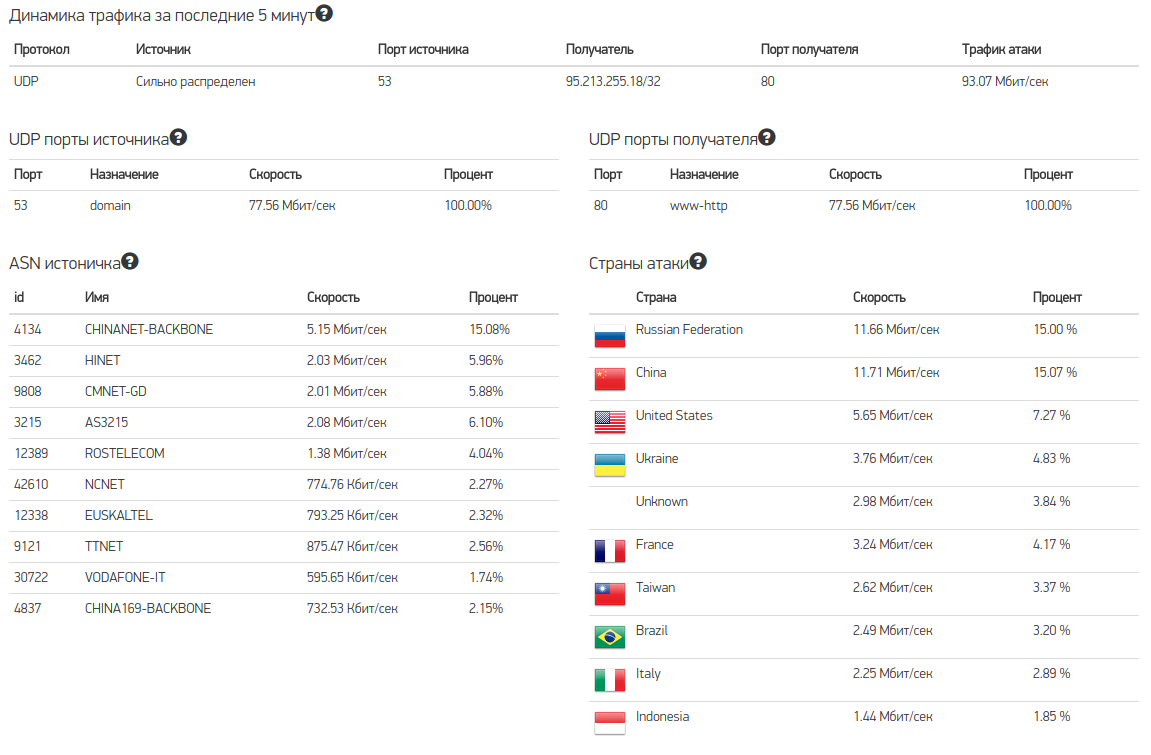
It contains more detailed information about incoming traffic:
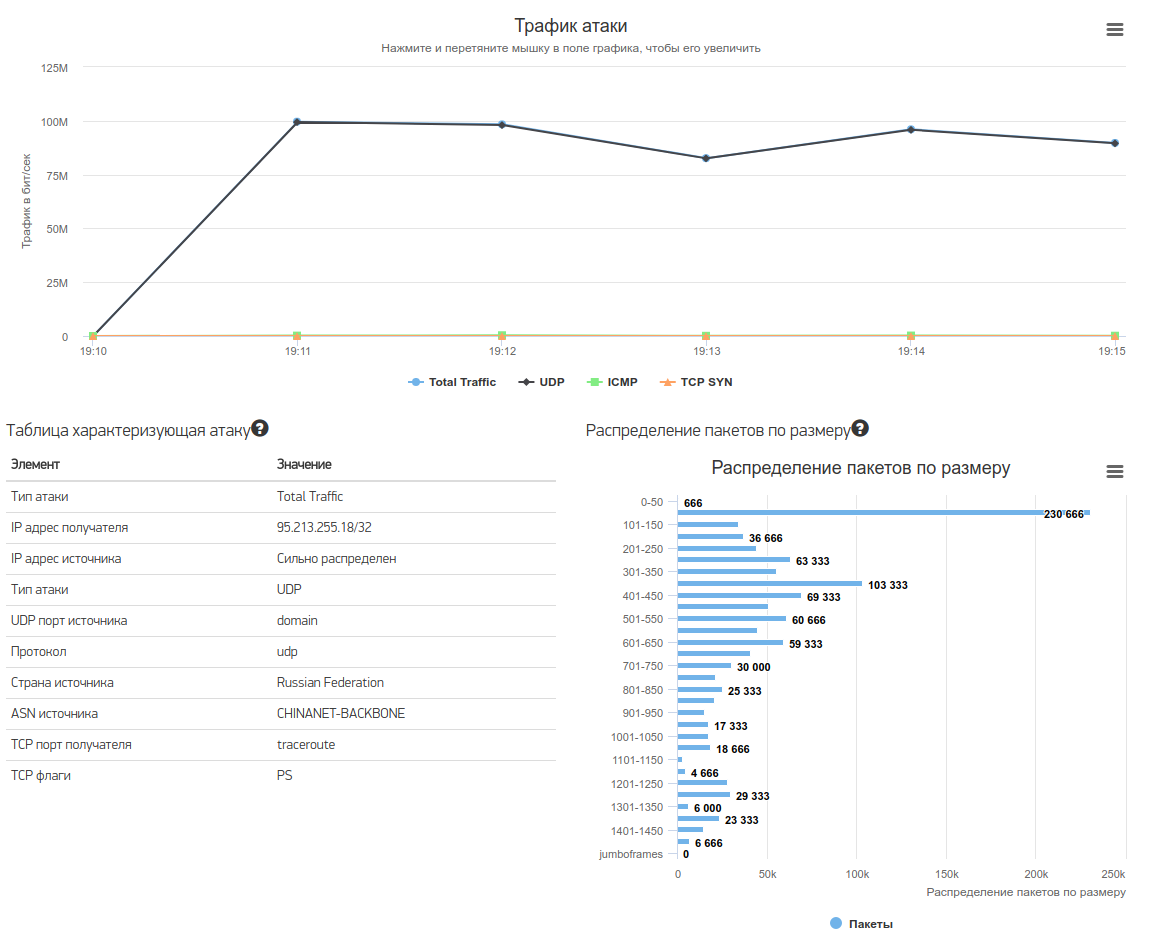
You can also see the sources of traffic by country:
Conclusion
The experience showed the preservation of the health of the web server under a test DDoS-attack when the service is connected to protect against DDoS. In addition, the use of our service allows you to track incoming DDoS attacks in real time without additional settings of the working systems and promptly respond to them.
In the space for further research, you can include the creation of more complex stress tests and the use of not only basic protection, but also enhanced with more advanced traffic filtering tools.
You can get acquainted with the types of protection and successful experience of our clients on the service page .
Source: https://habr.com/ru/post/354112/
All Articles