Mikrotik RoS, useful things
The prevalence of Mikrotik equipment is growing every day, more and more devices, and hence RoS, appear not only in the corporate sector, but also among ordinary, home users.
Unfortunately, in spite of the quite normal default settings that can be done via Quick Set, on the Internet you can find a lot of tips to clear the configuration, and do something on a “special” basis, from “zero”. In this article, I want to share my experience and give recommendations on how to change the configuration from Quick Set to fit my needs, while maintaining an adequate level of security.
Quick Set is an automatic configuration wizard that helps you quickly, without plunging into the depths of fine-tuning RoS, configure a router and start using it. Depending on the device, you may have several templates available:
Next we will mainly configure the HomeAP \ WISP AP, but the tips will be useful in other configurations.
')
The default configuration does not allow to connect to the router from the external network, but protection is based only on the packet filter. Do not forget about setting a password for the user admin. Therefore, in addition to filtering and password, I do the following:
I disable services that are not needed in the home network (and not in all non-home networks), but I limit the rest to the scope by specifying addresses from which you can connect to these services.
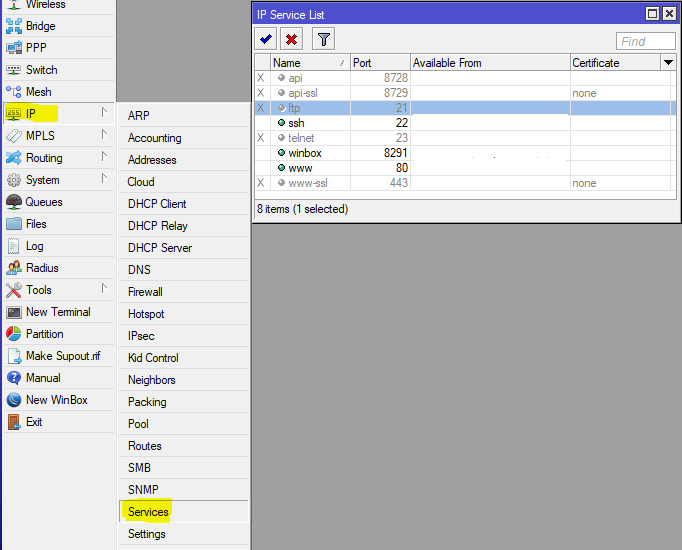
The next step is to limit the detection of the router by searching for neighbors. To do this, you should have a list of interfaces where this protocol can work, let's configure it:
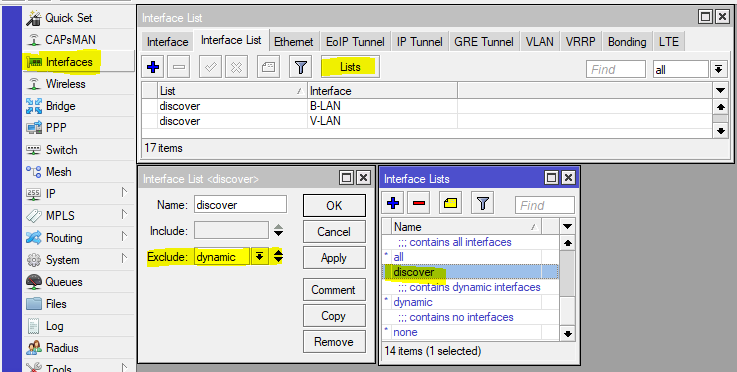
Let's add to the discovery list the interfaces on which we want the Neighbors Discovey protocol to work.
Now we configure the operation of the protocol, specifying the discovery list in its settings:

In a simple, home configuration, in the discovery list there may be interfaces on which the access protocol by MAC address can work, for situations when IP is not available, therefore we will configure this function:
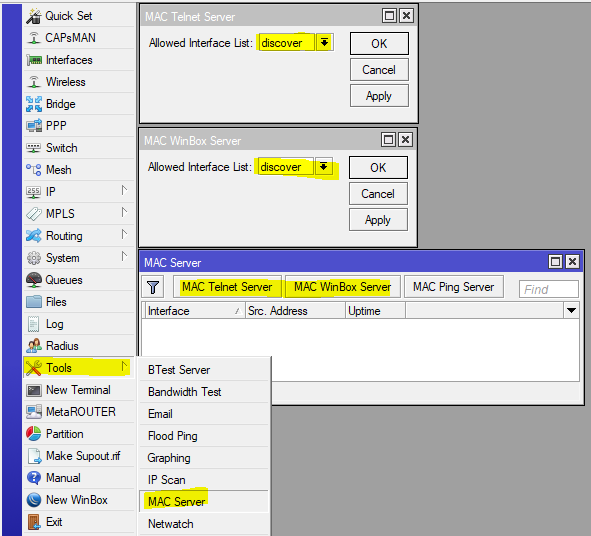
Now, the router will become “invisible” on the external interfaces, which will hide information about it (not all of course) from potential scanners, and even deprive the bad guys of easy access to control over the router.
Now, add some simple rules to the packet filter:
And put them after the defcon rule for the icmp protocol.
The result will be a ban for a day for those who are trying to open more than 15 new connections per second. There are many or fewer 15 connections, a moot point, here you have to choose a number yourself, I chose 50 for corporate use, and I have such bans 1-2 per day. The second group of rules is much tougher, blocks attempts to connect to the ssh port (22) and winbox (8291), 3 attempts per minute, and rest for a day;). If you need to put a DNS server on the Internet, then a similar rule can be cut off the attempts of DNS Amplification Attacks, but the solution is not perfect, and there are many false positives.
RFC 1918 describes the allocation of address spaces for globally non-routable networks. Therefore, it makes sense to block traffic from \ to such networks on the interface, which looks to the provider, except for situations where the provider gives you a "gray" address.
Put these rules closer to the beginning and do not forget to add to the list of WAN interface, looking in the direction of the provider.
But a set of marshuts in the "black hole"
This set of routes will send all traffic to RFC 1918 networks into a “black hole”, however, if there are routes with a smaller metric, then such traffic will go through these routes. Useful to ensure that private traffic does not leak into the external network.
Thanks for the advice we thank achekalin
Quite a controversial technology that allows applications to ask the router to forward ports through NAT, however, the protocol works without any authorization and control, it is simply not in the standard, and often is a point that reduces security. Customize at your discretion:
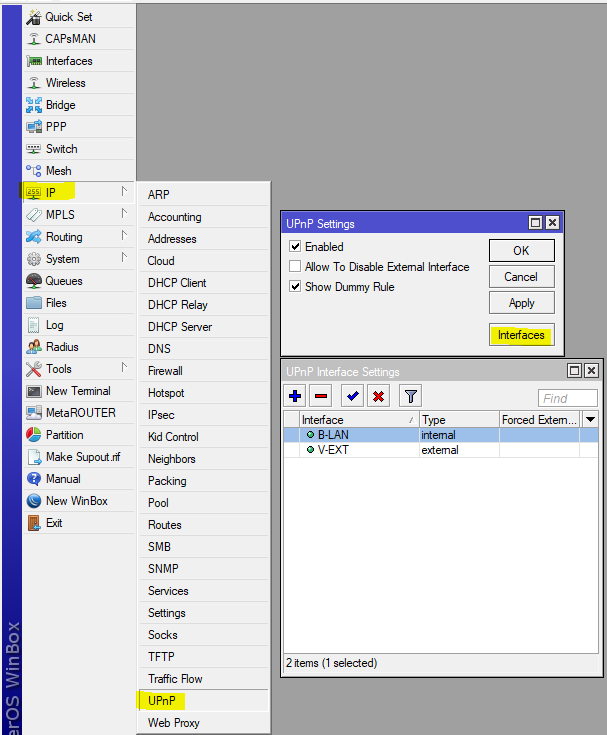
Among other things, it is worthwhile to disable the SIP conntrack module, which can cause inadequate VoIP operation, most modern SIP clients and servers do well without its help, and SIP TLS makes it completely useless.

If you are not using IPv6 or do not want Windows workstations to raise IPv6 tunnels without demand, then block the following traffic:
Thanks again for the advice of achekalin
This function appeared quite recently (from version 6.41), and it is very convenient. However, there is an unpleasant bug (I reported about it, but it has not been fixed yet), the point is that after the router is restarted, the firewall rules that use these lists do not work for the interfaces included in the child lists. Treated before adding child lists. Automation is simple:
In the Sheduler to the start event, we write a script (lists of interfaces for configuration with balancing):
In an urban environment, when the broadcast is extremely noisy, it makes sense to abandon channels in 40MGhz, this increases the power density of the signal on the channel, since the 40MGHz channel is essentially two channels of 20MGHz.
If your router distributes the Internet and gives clients the settings via DHCP, it makes sense to set the arp = reply-only option, and add-arp = yes in the DHCP Server
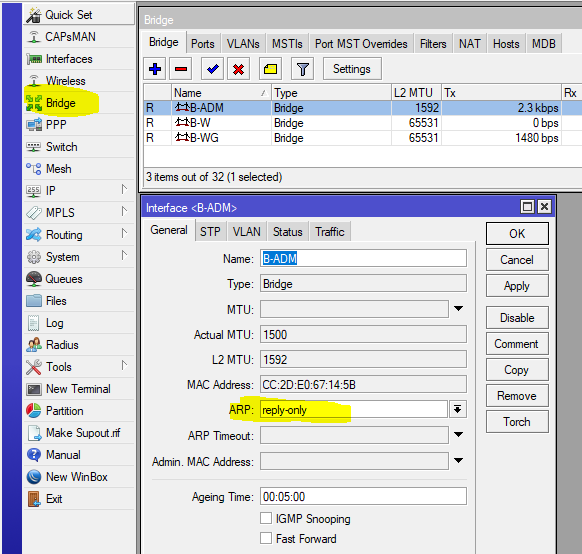
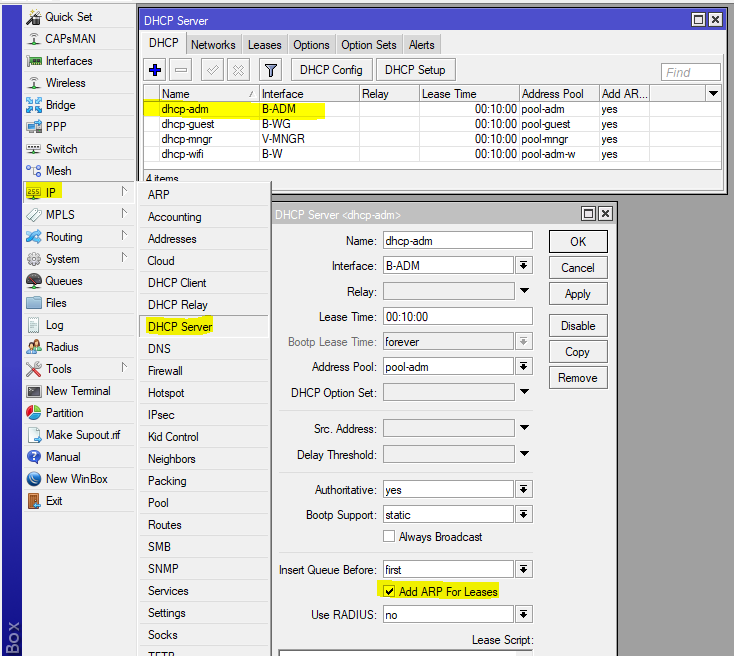
This setting will prevent you from manually setting the IP address, since the router will only agree to work with the MAC-IP pair that it issued itself.
For corporate use, I recommend getting lists of interfaces and addresses that personify access zones. Then, by creating such lists, you can configure the rules for traffic from one zone to another, as well as easily change the composition of zones. In general, more often use lists, rather than the interfaces themselves, this will facilitate the transfer of the configuration.
Unfortunately, in spite of the quite normal default settings that can be done via Quick Set, on the Internet you can find a lot of tips to clear the configuration, and do something on a “special” basis, from “zero”. In this article, I want to share my experience and give recommendations on how to change the configuration from Quick Set to fit my needs, while maintaining an adequate level of security.
What is Quick Set?
Quick Set is an automatic configuration wizard that helps you quickly, without plunging into the depths of fine-tuning RoS, configure a router and start using it. Depending on the device, you may have several templates available:
- CAP - Managed Access Point Mode, requires configured CAPsMAN
- CPE - WiFi client mode, when the Internet comes to you via WiFi
- HomeAP [dual] - Home access point mode, here the number of settings is reduced, and their names are close to the "home users" slang
- PTP Bridge AP \ CPE - Wireless bridge organization mode, one point is configured in the AP, the rest in the CPE
- WISP AP - Almost the same as HomeAP, but the settings are more and the names are more “professional”
- Basic AP - Almost empty configuration, suitable for deploying autonomously managed access points (without CAPsMAN)
Next we will mainly configure the HomeAP \ WISP AP, but the tips will be useful in other configurations.
')
Security
The default configuration does not allow to connect to the router from the external network, but protection is based only on the packet filter. Do not forget about setting a password for the user admin. Therefore, in addition to filtering and password, I do the following:
Accessibility on external interfaces
I disable services that are not needed in the home network (and not in all non-home networks), but I limit the rest to the scope by specifying addresses from which you can connect to these services.

The next step is to limit the detection of the router by searching for neighbors. To do this, you should have a list of interfaces where this protocol can work, let's configure it:
/interface list add exclude=dynamic name=discover 
Let's add to the discovery list the interfaces on which we want the Neighbors Discovey protocol to work.
Now we configure the operation of the protocol, specifying the discovery list in its settings:

In a simple, home configuration, in the discovery list there may be interfaces on which the access protocol by MAC address can work, for situations when IP is not available, therefore we will configure this function:

Now, the router will become “invisible” on the external interfaces, which will hide information about it (not all of course) from potential scanners, and even deprive the bad guys of easy access to control over the router.
DDoS protection
Now, add some simple rules to the packet filter:
/ip firewall filter add action=jump chain=forward connection-state=new in-interface-list=ISP jump-target=anti-DDoS add action=jump chain=input connection-state=new in-interface-list=ISP jump-target=anti-DDoS add action=drop chain=forward connection-state=new src-address-list=BAN-DDoS add action=return chain=anti-DDoS dst-limit=15,15,src-address/10s add action=add-src-to-address-list address-list=BAN-DDoS address-list-timeout=1d chain=anti-DDoS add action=jump chain=input connection-state=new dst-port=22,8291 in-interface-list=ISP jump-target=anti-BruteForce-3 protocol=tcp add action=drop chain=forward connection-state=new src-address-list=BAN-BruteForce-3 add action=return chain=anti-BruteForce-3 dst-limit=4/1m,1,src-address/1m40s add action=add-src-to-address-list address-list=BAN-BruteForce-3 address-list-timeout=1d chain=anti-BruteForce-3 And put them after the defcon rule for the icmp protocol.
The result will be a ban for a day for those who are trying to open more than 15 new connections per second. There are many or fewer 15 connections, a moot point, here you have to choose a number yourself, I chose 50 for corporate use, and I have such bans 1-2 per day. The second group of rules is much tougher, blocks attempts to connect to the ssh port (22) and winbox (8291), 3 attempts per minute, and rest for a day;). If you need to put a DNS server on the Internet, then a similar rule can be cut off the attempts of DNS Amplification Attacks, but the solution is not perfect, and there are many false positives.
RFC 1918
RFC 1918 describes the allocation of address spaces for globally non-routable networks. Therefore, it makes sense to block traffic from \ to such networks on the interface, which looks to the provider, except for situations where the provider gives you a "gray" address.
/ip firewall address-list add address=10.0.0.0/8 list="RFC 1918" add address=172.16.0.0/12 list="RFC 1918" add address=192.168.0.0/16 list="RFC 1918" /ip firewall filter add action=drop chain=input comment="Drop RFC 1918" in-interface-list=WAN src-address-list="RFC 1918" add action=drop chain=forward comment="Drop RFC 1918" dst-address-list="RFC 1918" out-interface-list=WAN add action=drop chain=output comment="Drop RFC 1918" dst-address-list="RFC 1918" out-interface-list=WAN Put these rules closer to the beginning and do not forget to add to the list of WAN interface, looking in the direction of the provider.
But a set of marshuts in the "black hole"
/ip route add comment="RFC 1918" distance=249 dst-address=10.0.0.0/8 type=blackhole add comment="RFC 1918" distance=249 dst-address=172.16.0.0/12 type=blackhole add comment="RFC 1918" distance=249 dst-address=192.168.0.0/16 type=blackhole This set of routes will send all traffic to RFC 1918 networks into a “black hole”, however, if there are routes with a smaller metric, then such traffic will go through these routes. Useful to ensure that private traffic does not leak into the external network.
Thanks for the advice we thank achekalin
UPnP
Quite a controversial technology that allows applications to ask the router to forward ports through NAT, however, the protocol works without any authorization and control, it is simply not in the standard, and often is a point that reduces security. Customize at your discretion:

SIP Conntrack
Among other things, it is worthwhile to disable the SIP conntrack module, which can cause inadequate VoIP operation, most modern SIP clients and servers do well without its help, and SIP TLS makes it completely useless.

IPv6 tunnels
If you are not using IPv6 or do not want Windows workstations to raise IPv6 tunnels without demand, then block the following traffic:
/ip firewall filter add action=drop chain=forward comment="Teredo TCP" dst-port=3544 protocol=tcp add action=drop chain=forward comment="Teredo UDP" dst-port=3544 protocol=udp add action=drop chain=forward comment=6to4 protocol=ipv6 Thanks again for the advice of achekalin
Dynamic and nested lists of interfaces
This function appeared quite recently (from version 6.41), and it is very convenient. However, there is an unpleasant bug (I reported about it, but it has not been fixed yet), the point is that after the router is restarted, the firewall rules that use these lists do not work for the interfaces included in the child lists. Treated before adding child lists. Automation is simple:
In the Sheduler to the start event, we write a script (lists of interfaces for configuration with balancing):
/interface list set ISP1TUN include="" set ISP include="" set TUN include="" :delay 2 set ISP1TUN include=ISP1,TUN1 set ISP include=ISP1 set TUN include=TUN1 WiFi
In an urban environment, when the broadcast is extremely noisy, it makes sense to abandon channels in 40MGhz, this increases the power density of the signal on the channel, since the 40MGHz channel is essentially two channels of 20MGHz.
Bridge & ARP
If your router distributes the Internet and gives clients the settings via DHCP, it makes sense to set the arp = reply-only option, and add-arp = yes in the DHCP Server


This setting will prevent you from manually setting the IP address, since the router will only agree to work with the MAC-IP pair that it issued itself.
Other
For corporate use, I recommend getting lists of interfaces and addresses that personify access zones. Then, by creating such lists, you can configure the rules for traffic from one zone to another, as well as easily change the composition of zones. In general, more often use lists, rather than the interfaces themselves, this will facilitate the transfer of the configuration.
Source: https://habr.com/ru/post/353730/
All Articles