How is information security operational management center (SOC-center) built today?
In large companies, there are people who are engaged only in controlling the state of information security and waiting for problems to begin. This is not about security guards in front of monitors, but about selected people (at least one in a shift) in the information security department.

Most of the time the operator of the SOC center works with the SIEMs. SIEM systems collect data from various sources throughout the network and, together with other solutions, compare events and assess the threat, both individually for each user and service, and in general for groups of users and network nodes. As soon as someone starts to behave too suspiciously, the operator of the SOC-center receives a notification. If the level of suspicion is overwhelming, the suspicious process or workplace is first isolated, and then a notification comes. Next begins the investigation of the incident.
')
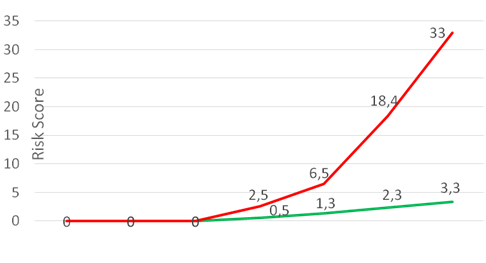
Very simplifying, for each suspicious action the user receives penalty points. If the action is characteristic of him or his colleagues - there are few points. If the action is not typical - there are a lot of points.
For UBA systems (User Behavior Analytics), the sequence of actions also matters. Separately, a sharp jump in traffic, connecting to a new IP or copying data from a file server happens from time to time. But if the user first opened the letter, then he had an appeal to the newly registered domain, and then he began to search the neighboring machines and send strange encrypted traffic to the Internet - this is already a suspicion of an attack.
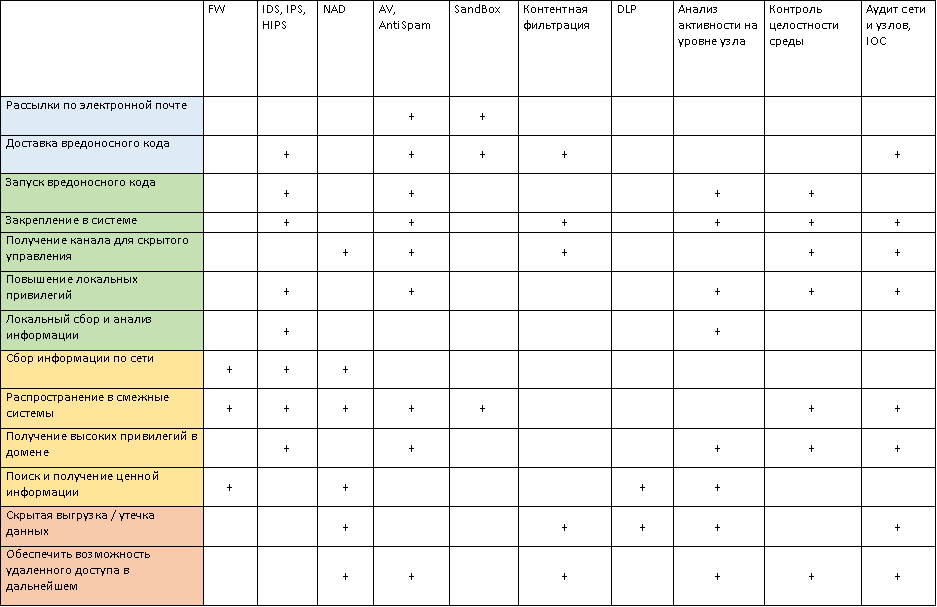
Typically, at an average level of development of the information security department, a typical company has a set of protection systems - firewalls (often NGFW), streaming antiviruses, DDoS protection systems, a DLP system with agents at workstations, and so on. But all this is rarely linked in a single information network, which compares events and finds unobvious correlations.
"Still inexperienced" differ from "already experienced" lined up processes of work with the constantly changing infrastructure of the company. That is, the system is dynamic, and the entire infrastructure is considered as a living organism, growing and continuously developing. Based on this paradigm, all the rules of work, procedures and interaction rules within the existing ecosystem are set.
If there is no such approach, even though the data is somehow collected, and the incidents are somehow recorded, we often see that those responsible do not know how to respond to certain situations. I know you are ready to not believe me now. But recently there was a vivid example. When replacing the equipment, the state company did not have time to roll in the correct configs and caught the encryption virus. They call and ask: “What should I do right now?” IT wants to block completely, clean up the network segment, reinstall all the operating systems, IB says that there is critical data and it’s not clear how the virus has reached - and doesn’t give permission to touch anything. Time is running out.
We advised to isolate the segment on the firewall, to make a complete snapshot of all the workstations of the segment and transfer it to us forignics. While the analysis is being carried out, for encrypted stations, reinstall the OS from scratch, for the rest, check for a rootkit by running an antivirus from the LiveCD. Then return the stations to the network, but continue to closely monitor the traffic on the proxy and NGFW for the spread of infection and conduct a security audit for key systems.
As a result, the customer revised the IS risks and redid all protection to normal, with centralized control of the settings of workstations, servers and network equipment, centralized control system of applications being run, control of the integrity of key systems and more stringent settings on information protection tools.
Well, first of all, the fact that SIEM-systems are reactive in nature. They have a key advantage - they connect and unite a bunch of systems of different vendors. That is, it is not necessary to change and redo the entire infrastructure from scratch - take your existing protection components and put a SIEM system on top of them. The problem is that the SIEM system starts working only when the attacker has already penetrated the infrastructure. Therefore, for an effective SOC-center, classic SIEM systems need to be supplemented with UBA class systems and Threat Intelligence data, which allow an attacker to be detected even at the early stages of an attack, ideally, at the stage of preparation for hacking.
After a few weeks of learning the UBA-system, what is the incident, and what is the usual repetitive routine, there are about a dozen basic alarms a day. Suppose, eight of them require quick analysis, but they end up banal - these are bugs, iron malfunctions, atypical, but allowed user activity. Another is the situation when the script kiddie tries to break through the defense. And the last - a real data leakage or targeted attack. Such cases require a more detailed investigation, including a retrospective analysis of a large amount of data to a depth of about several months. Here SOC-centers are well helped by data analysis systems built on the basis of technologies of the Big Data class.

Figure 1. Typical APT attack scenario
SIEM and UBA look at who did what, what changed and how, in order to understand whether a node or an employee has been compromised.
Secondly, we need people who are engaged in the detection and investigation of security incidents. That is, their task is not to support the infrastructure, but to actively participate in the rapid response to IS incidents. A day at a large retail network is quite possible hundreds of potential security incidents. Most of them are automatic attacks on web resources or unrecorded interactions with external systems, but some of them are quite real external APT attacks and internal fraud.
Third, the regulations and procedures for the interaction of various units at the time of the attack, the so-called Play Book, according to which the IS incident is located and investigated, must be worked out. In many situations, SOC employees must have high authority. For example, they should have the right to immediately suspend the work of production if there is a massive data leak. In the bank to cut food in such a situation - the limit of courage. But if you think over everything in advance and fix the action plan in the regulations, you can choose the lesser evil in each specific situation. All this is done in order to detect the incident as early as possible and minimize potential damage.
We have implemented our SOC-center, to which we have connected both our infrastructure and a number of our customers. It is based on the SIEM-system, which we supplemented with our own development based on Big Data with machine learning for the detection of anomalies and APT attacks. On the first line, we have a dedicated Helpdesk group - “universal soldiers”, who will conduct basic troubleshooting and simple incidents can be closed. The second line is analysts, information security specialists, who are involved in the investigation of complex incidents and deep forsensics. And there is also a team of pentesters, which from time to time checks the perimeter of the network for strength. All teams communicate with each other through HPSM for convenience and to support a single knowledge base.
One of the most important pieces of behavioral analysis systems that are deployed within SOC-centers is training and calibration. That is, those very assessments of the actions of users and nodes on a scale of potential danger generated in real time. If a user's workstation is compromised, then its behavior in the system will be quite different from colleagues.
It is important to localize on the basis of type behavior. For example, if a person works as a networker in a large company and launches a bunch of weird tools, SIEM will see that he has five other people working next to him - that means all the rules. But if the accountant begins to do something similar to the engineer frills - the alarm will be immediately.
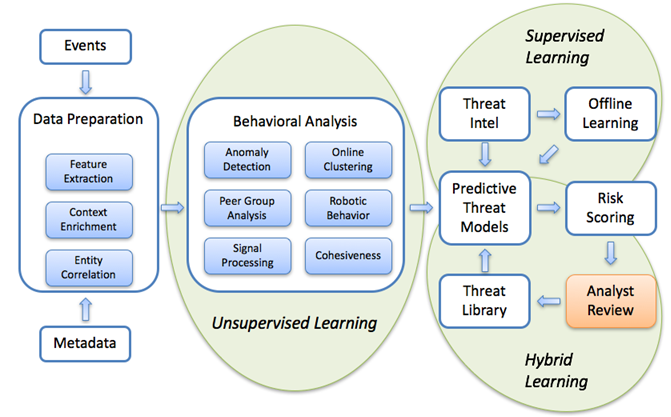
Figure 2. Machine learning models for detecting abnormal network activity
In practice, during implementations during calibrations, we found:
A very good thing is to evaluate the model and roll up a heap of incidents to the root cause. For example, uplink failure between data centers is one big problem, not hundreds of mini-failures of workstations, servers and network equipment. Operators must understand, so it’s done most often like this:

Figure 3. Formation of the resource-service model
A very good thing - the union of disparate incidents in a single killchain. There are a number of stages through which a hacker goes through hacking infrastructure, ranging from preparing for scanning to ending with data theft and destroying logs. Signs of such activity can be monitored for months and recorded in the user's “card”, which allows operators to quickly identify a “zero patient”.

Figure 4. Example of killchain
In the end, it looks like this:
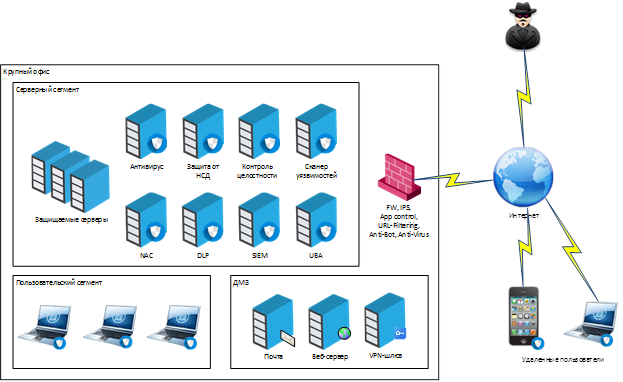
And this is an example of a set of security systems that are interconnected within the SOC and exchange data via the SIEM:
By the way, if you are a novice specialist and have long wanted to work in the field of information security, we have something for you. We are looking for a junior manager to promote information security solutions. It will be necessary to understand both current solutions and vendors and their products. Communicate with customers, make commercial offers and so on. In general, it will not be boring. For details, write me an email.

Most of the time the operator of the SOC center works with the SIEMs. SIEM systems collect data from various sources throughout the network and, together with other solutions, compare events and assess the threat, both individually for each user and service, and in general for groups of users and network nodes. As soon as someone starts to behave too suspiciously, the operator of the SOC-center receives a notification. If the level of suspicion is overwhelming, the suspicious process or workplace is first isolated, and then a notification comes. Next begins the investigation of the incident.
')

Very simplifying, for each suspicious action the user receives penalty points. If the action is characteristic of him or his colleagues - there are few points. If the action is not typical - there are a lot of points.
For UBA systems (User Behavior Analytics), the sequence of actions also matters. Separately, a sharp jump in traffic, connecting to a new IP or copying data from a file server happens from time to time. But if the user first opened the letter, then he had an appeal to the newly registered domain, and then he began to search the neighboring machines and send strange encrypted traffic to the Internet - this is already a suspicion of an attack.
How do they usually work with information security?
Typically, at an average level of development of the information security department, a typical company has a set of protection systems - firewalls (often NGFW), streaming antiviruses, DDoS protection systems, a DLP system with agents at workstations, and so on. But all this is rarely linked in a single information network, which compares events and finds unobvious correlations.
"Still inexperienced" differ from "already experienced" lined up processes of work with the constantly changing infrastructure of the company. That is, the system is dynamic, and the entire infrastructure is considered as a living organism, growing and continuously developing. Based on this paradigm, all the rules of work, procedures and interaction rules within the existing ecosystem are set.
If there is no such approach, even though the data is somehow collected, and the incidents are somehow recorded, we often see that those responsible do not know how to respond to certain situations. I know you are ready to not believe me now. But recently there was a vivid example. When replacing the equipment, the state company did not have time to roll in the correct configs and caught the encryption virus. They call and ask: “What should I do right now?” IT wants to block completely, clean up the network segment, reinstall all the operating systems, IB says that there is critical data and it’s not clear how the virus has reached - and doesn’t give permission to touch anything. Time is running out.
We advised to isolate the segment on the firewall, to make a complete snapshot of all the workstations of the segment and transfer it to us forignics. While the analysis is being carried out, for encrypted stations, reinstall the OS from scratch, for the rest, check for a rootkit by running an antivirus from the LiveCD. Then return the stations to the network, but continue to closely monitor the traffic on the proxy and NGFW for the spread of infection and conduct a security audit for key systems.
As a result, the customer revised the IS risks and redid all protection to normal, with centralized control of the settings of workstations, servers and network equipment, centralized control system of applications being run, control of the integrity of key systems and more stringent settings on information protection tools.
How does building a SOC-center differ from the introduction of a SIEM system?
Well, first of all, the fact that SIEM-systems are reactive in nature. They have a key advantage - they connect and unite a bunch of systems of different vendors. That is, it is not necessary to change and redo the entire infrastructure from scratch - take your existing protection components and put a SIEM system on top of them. The problem is that the SIEM system starts working only when the attacker has already penetrated the infrastructure. Therefore, for an effective SOC-center, classic SIEM systems need to be supplemented with UBA class systems and Threat Intelligence data, which allow an attacker to be detected even at the early stages of an attack, ideally, at the stage of preparation for hacking.
After a few weeks of learning the UBA-system, what is the incident, and what is the usual repetitive routine, there are about a dozen basic alarms a day. Suppose, eight of them require quick analysis, but they end up banal - these are bugs, iron malfunctions, atypical, but allowed user activity. Another is the situation when the script kiddie tries to break through the defense. And the last - a real data leakage or targeted attack. Such cases require a more detailed investigation, including a retrospective analysis of a large amount of data to a depth of about several months. Here SOC-centers are well helped by data analysis systems built on the basis of technologies of the Big Data class.

Figure 1. Typical APT attack scenario
SIEM and UBA look at who did what, what changed and how, in order to understand whether a node or an employee has been compromised.
Secondly, we need people who are engaged in the detection and investigation of security incidents. That is, their task is not to support the infrastructure, but to actively participate in the rapid response to IS incidents. A day at a large retail network is quite possible hundreds of potential security incidents. Most of them are automatic attacks on web resources or unrecorded interactions with external systems, but some of them are quite real external APT attacks and internal fraud.
Third, the regulations and procedures for the interaction of various units at the time of the attack, the so-called Play Book, according to which the IS incident is located and investigated, must be worked out. In many situations, SOC employees must have high authority. For example, they should have the right to immediately suspend the work of production if there is a massive data leak. In the bank to cut food in such a situation - the limit of courage. But if you think over everything in advance and fix the action plan in the regulations, you can choose the lesser evil in each specific situation. All this is done in order to detect the incident as early as possible and minimize potential damage.
Practice
We have implemented our SOC-center, to which we have connected both our infrastructure and a number of our customers. It is based on the SIEM-system, which we supplemented with our own development based on Big Data with machine learning for the detection of anomalies and APT attacks. On the first line, we have a dedicated Helpdesk group - “universal soldiers”, who will conduct basic troubleshooting and simple incidents can be closed. The second line is analysts, information security specialists, who are involved in the investigation of complex incidents and deep forsensics. And there is also a team of pentesters, which from time to time checks the perimeter of the network for strength. All teams communicate with each other through HPSM for convenience and to support a single knowledge base.
One of the most important pieces of behavioral analysis systems that are deployed within SOC-centers is training and calibration. That is, those very assessments of the actions of users and nodes on a scale of potential danger generated in real time. If a user's workstation is compromised, then its behavior in the system will be quite different from colleagues.
It is important to localize on the basis of type behavior. For example, if a person works as a networker in a large company and launches a bunch of weird tools, SIEM will see that he has five other people working next to him - that means all the rules. But if the accountant begins to do something similar to the engineer frills - the alarm will be immediately.

Figure 2. Machine learning models for detecting abnormal network activity
In practice, during implementations during calibrations, we found:
- Those who decided to remember cryptocurrency.
- Found an innumerable number of people who send files to their personal mail. Set up auto-blocking filters - if there are many such files, mail is blocked.
- We caught a couple of people on a potential report leak, but it’s just that the bookkeeping was set in motion entirely and the system didn’t have time to learn.
- The customer somehow burned the first “combat” alarm - the https traffic wrapped through some strange IP. It turned out that the financial department worked with bank clients who redirected the page to an external resource to assess browser compromise, and from there the traffic went to banking itself. It looked really strange, but talked to the bank, this is the norm.
- In one of the branches of a large company, they found an admin who installed the “left” software on his workstation, disabling half of the information security systems. And they burned him on the fact that he downloaded another crack with a virus and managed to start distributing it across the internal network segment. The customer isolated the segment, and we did the forensics.
- Caught a couple of comrades who use their colleagues' accounts for their business. A colleague in Irkutsk, and then hop - from the office working on his car. Disorder. Or, the account suddenly generated 10 thousand login attempts in a couple of minutes - some wrote a robot, but when changing passwords I forgot to feed him a new account.
- Well, we spotted several attacks. The model looks like this: first, a letter came with a high suspicion of spam. Then the user turned to the website with a fresh domain registration. Next pause, everything is calm. After 2 weeks at night, someone remotely connected and started downloading data from a file server. At this point, an incident was created for manual processing, after 4 minutes filtering was turned on only on the “white sheet”, then in the morning a full debriefing was done. Full automation was not used - it requires caution, because if there is a system that blocks everything, then the attack itself can go for it.
Another pair of chips
A very good thing is to evaluate the model and roll up a heap of incidents to the root cause. For example, uplink failure between data centers is one big problem, not hundreds of mini-failures of workstations, servers and network equipment. Operators must understand, so it’s done most often like this:
- pre-determined key business processes;
- a catalog of IT services is created that support the work of business processes;
- for each IT service, its main components are determined: servers, network equipment, a set of application software;
- a resource-service model is built, which is a hierarchical graph, the nodes of which are the key components, and the edges are the connections between them.

Figure 3. Formation of the resource-service model
A very good thing - the union of disparate incidents in a single killchain. There are a number of stages through which a hacker goes through hacking infrastructure, ranging from preparing for scanning to ending with data theft and destroying logs. Signs of such activity can be monitored for months and recorded in the user's “card”, which allows operators to quickly identify a “zero patient”.

Figure 4. Example of killchain
Evolution of the protection system


In the end, it looks like this:

And this is an example of a set of security systems that are interconnected within the SOC and exchange data via the SIEM:

By the way, if you are a novice specialist and have long wanted to work in the field of information security, we have something for you. We are looking for a junior manager to promote information security solutions. It will be necessary to understand both current solutions and vendors and their products. Communicate with customers, make commercial offers and so on. In general, it will not be boring. For details, write me an email.
Links
- We found a large company that has not been engaged in information security for 5 years and is still alive
- Safety of football stadiums: some implicit features
- Network microsegmentation in examples: how this cleverly twisted thing reacts to different attacks
- Directed IT attacks in the sphere of large business: how it happens in Russia
- My mail is dberezin@croc.ru
Source: https://habr.com/ru/post/353324/
All Articles