Vulnerability found in Vesta CP hosting control panel
In some of our previous articles we have already talked about the free Vesta CP control panel. This morning we received disturbing information - there is a critical vulnerability in the panel that allows attackers to access the server and launch DDoS attacks from it or send spam, which often leads to traffic overspending. Details known at the moment, as well as tips on protecting a clean and cleaning a hacked server, under the cat.
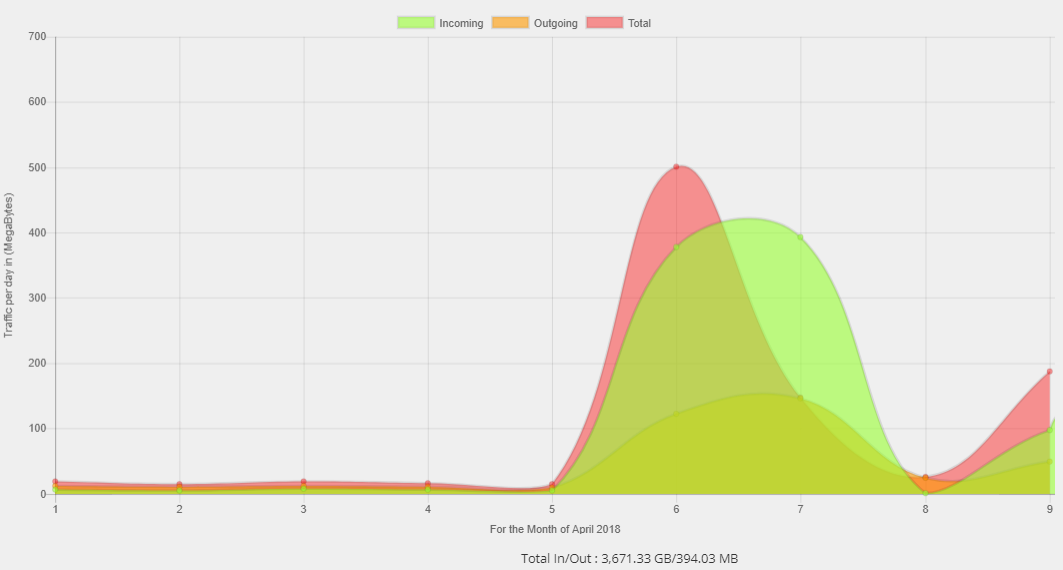
The first notifications about possible vulnerabilities in Vesta 0.9.8-19 appeared on April 7 in both the English and Russian branches of the forum panel . All symptoms were similar: a sharp increase in traffic and a parasitic load on the server. And according to the statements of people serving many client servers, they only had one thing in common - Vesta CP.
Soon, preventive measures were followed by individual providers - blocking the standard port of Vesta (8083) at the network level of the provider, disabling the guilty. In the meantime, the panel developers themselves tried to link the hacks with their product. And you can not say that successfully.
')
According to the developers themselves, they were unable to reliably establish and reproduce the vector of attack, but they released a hotfix covering some of the gaps that could have caused it. Namely, they corrected the authorization and made the password check more stringent. So far, no information has been received on the successful hacking of the updated Vesta 0.9.8-20, but the fact that the developers could not reliably establish the attack vector itself keeps users in a certain amount of tension. Below we provide some recommendations from the network to prevent hacking and to combat the consequences.
Most of the recommendations below apply not only to servers with Vesta CP, but also to any other Linux server.
Spots The consequences of this attack are eliminated rather uneasy, therefore, if you have such an opportunity, we advise you to use Vanish to merge backups (we reminded you of the need to do them more than once ) and reinstall the server. The difficulty lies in the fact that Trojan.DDoS_XOR-1 (also known as Chinese Chicken Multiplatform DoS botnets Trojan), which infected most of the compromised machines, is very self-repairing, and certain tambourine dances are needed to remove it (described below). Another difficulty is the banal server overload by parasitic processes, which will significantly complicate your work with the server outside of the rescue mode (which may not exist in principle if you use VPS).
If it’s not possible to just reinstall everything, try the following.
If you are a hoster or a sysadmin, and you need to leave proof for a client, you can leave the rest of the files unchecked. If not, delete all other frozen files. Also, if you are unable to identify malicious files yourself, use ClamAV or RKHunter and see their report.
If you have additional information about this problem, write in the comments. Subscribe to our channel and this topic, we will also monitor developments and publish important updates in this article.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

The first notifications about possible vulnerabilities in Vesta 0.9.8-19 appeared on April 7 in both the English and Russian branches of the forum panel . All symptoms were similar: a sharp increase in traffic and a parasitic load on the server. And according to the statements of people serving many client servers, they only had one thing in common - Vesta CP.
Soon, preventive measures were followed by individual providers - blocking the standard port of Vesta (8083) at the network level of the provider, disabling the guilty. In the meantime, the panel developers themselves tried to link the hacks with their product. And you can not say that successfully.
')
According to the developers themselves, they were unable to reliably establish and reproduce the vector of attack, but they released a hotfix covering some of the gaps that could have caused it. Namely, they corrected the authorization and made the password check more stringent. So far, no information has been received on the successful hacking of the updated Vesta 0.9.8-20, but the fact that the developers could not reliably establish the attack vector itself keeps users in a certain amount of tension. Below we provide some recommendations from the network to prevent hacking and to combat the consequences.
What to do if your server has not been hacked yet?
Most of the recommendations below apply not only to servers with Vesta CP, but also to any other Linux server.
- First of all, update the panel by running the command:
v-update-sys-vesta-all - Change in /usr/local/vesta/nginx/conf/nginx.conf the standard port 8083 to another one of your choice.
- Use a non-standard SSH port. Use the key entry if possible.
It is also advisable to disable root login from the world. - Download and run Linux Environment Security .
- Download and install Linux malware detect . After installation, run the primary system analysis for existing problems: maldet -a / (and analyze the report). If everything is in order, start monitoring: maldet - monitor / . Be sure to include your email to receive reports in /usr/local/maldet.conf .
- Another very useful tool to install is Config Server Firewall . Carefully read the configuration file and be sure to turn on tracking changes to directories and files.
- If you are not expecting users, customers or visitors from China - block it all at the firewall level.
- Install an application to monitor traffic. For example, ntopng .
And if you have already hacked?
If it’s not possible to just reinstall everything, try the following.
- Check for symptoms of infection with Trojan.DDoS_XOR. It appears in the output top as a file with a random name of the form H8wuaqwiu, S01wefiouh8, etc. or as a system command, sometimes not even assuming a long execution: ls, ifconfig, pwd, ping, awk, telnet ...
The second symptom is the presence of the .sh file in the hourly crown folder. You can check with the command ls -la /etc/cron.hourly/ . The file is often called gcc.sh , cron.sh , but other names are possible. - See the contents of the .sh file. For example, using the cat /etc/cron.hourly/gcc.sh command. The file has approximately the following content:
#! / bin / sh
PATH = / bin: / sbin: / usr / bin: / usr / sbin: / usr / local / bin: / usr / local / sbin: / usr / X11R6 / bin
for i in `cat / proc / net / dev | grep: | awk -F: {'print $ 1'} `; do ifconfig $ i up & done
cp /lib/libudev.so /lib/libudev.so.6
/lib/libudev.so.6 - Get in there? Do not rush to fuss, Trojan recovers its files faster than you can delete them all. But it will try to use the same file names, so the lock should help:
chmod 0 /etc/cron.hourly/gcc.sh; chattr +ia /etc/cron.hourly/gcc.sh; chattr + i /etc/crontab - And the process of completely killing is also useless, it is recommended to stop it first,
so that the trojan does not try to restart it. In the output of the top command, find the process that caused the suspicion (for example, S01wefiouh8) and execute:kill -STOP 16621 - Locate executables and block them. To search, use the command find / etc -name '* S01wefiouh8 *' . For found files, execute chmod 0 / name / file; chattr + ia / name / file .
- Remove the executable files found in / usr / bin (with ls -lt / usr / bin | head you can search for others that are suspicious):
rm -f /usr/bin/S01wefiouh8 - Now you can finish the stopped process:
pkill mtyxkeaofa - Finally, remove the body of the virus:
rm -f /lib/libudev*.so
If you are a hoster or a sysadmin, and you need to leave proof for a client, you can leave the rest of the files unchecked. If not, delete all other frozen files. Also, if you are unable to identify malicious files yourself, use ClamAV or RKHunter and see their report.
If you have additional information about this problem, write in the comments. Subscribe to our channel and this topic, we will also monitor developments and publish important updates in this article.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/353320/
All Articles