Why put up a management interface or attack on a Cisco Smart Install on the Internet
Cisco recently learned about some hacker groupings that targeted Cisco switches as their target, using the issue of protocol misuse in the Cisco Smart Install Client. Several incidents in different countries, including some involving critical infrastructure, have been associated with the misuse of the Smart Install protocol. Some experts believe that a number of these attacks are associated with hackers in the service of the state. As a result, we take a proactive stance and encourage customers, again, to assess risks and apply available methods to neutralize risks.
On February 14, 2017 (yes, there is no error, this is about 2017), the Cisco Product Security Incident Response Team (PSIRT) published a bulletin describing the results of active scans associated with Cisco Smart Install Clients. The Cisco Smart Install Client software is an outdated utility designed for remote configuration of new Cisco equipment, in particular Cisco switches. In continuation, Cisco Talos posted a blog post and released an open source tool that scans devices using the Cisco Smart Install protocol. In addition to the above, a signature was issued for the Snort attack detection system (SID: 41722-41725), which allows to detect any attempts to use this technology.
The Cisco Smart Install protocol can be abused to change the TFTP server setting, export configuration files via TFTP, change the configuration files, replace the image of the network IOS operating system, and set up accounts that allow you to run IOS commands. Although this is not a vulnerability in the classical sense, the misuse of this protocol can serve as an attack vector that should be immediately neutralized. During late 2017 and early 2018, Talos watched as attackers attempted to scan clients using this vulnerability. Recent information has increased the relevance of this problem and we decided to return to it again.
')
Although we only observed attacks related to the problem of misusing the Cisco Smart Install protocol, another vulnerability was recently discovered and fixed in the Cisco Smart Install Client. This vulnerability has been discussed publicly, and a code has been released showing evidence of the possibility of exploiting the vulnerability (PoC). To fix the problem of misuse of the protocol, clients should also eliminate this vulnerability by installing the appropriate update.
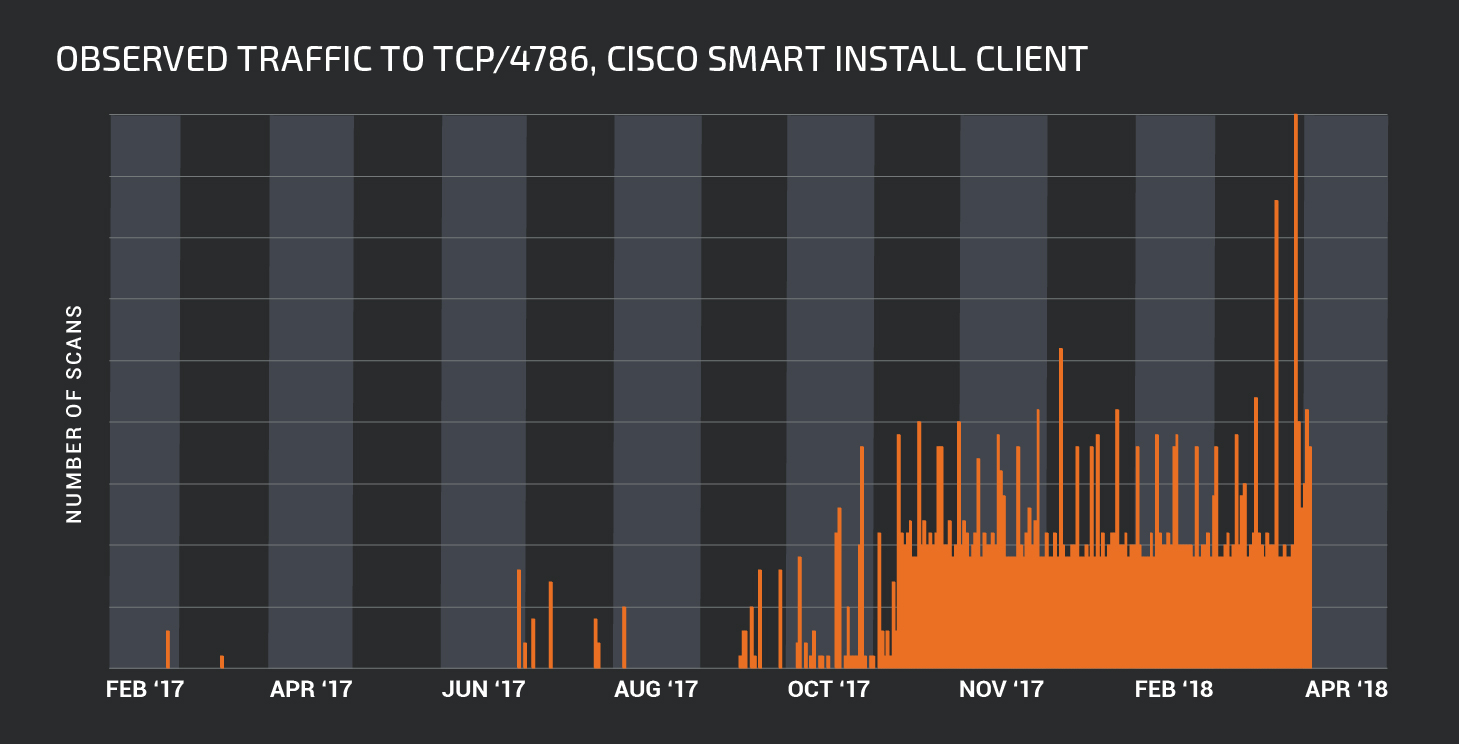
As part of the Cisco Talos study, we began to explore how many devices are potentially vulnerable to this attack. The results were extremely disturbing. Using Shodan, Talos was able to determine that more than 168,000 systems could potentially be detected via the Cisco Smart Install Client “open to the Internet”. This is better than the results of 2016, when a Tenable employee reported 251,000 vulnerable Cisco Smart Install Clients “visible” from the Internet. There may be differences in the Cisco Talos and Tenable scanning methodology, but we assume a significant reduction in the number of devices available to attack. In addition, despite the fact that since our initial bulletin, there has been a drop in scan volumes, Talos observed a sharp increase in scanning attempts for the Cisco Smart Install Client around November 9, 2017.
You can determine if you have a device “raised” on the Cisco Smart Install Client software switch. Running the show vstack config command will allow you to determine if the Smart Install Client is active. Below is an example of such a command with a response to it:
Additional features of the active Cisco Smart Install Client may be present if level 6 (informational) or higher registration is enabled. These event logs may include, but are not limited to, TFTP write operations, command execution, and device reloads.
The easiest way to counteract this problem is to run the no vstack command on a vulnerable device. If for any reason this option is not available to the client, the best option would be to restrict access via an access control list (ACL) for the interface, an example of which is shown below:
This type of ACL only allows the nodes shown above to access the Smart Install Client, which significantly limits the ability to launch an attack. In addition, there are signatures in our Intrusion Prevention Systems (IPS) to determine if Smart Install Client is affected or not.
For this and other issues, it is important to remember Cisco’s commitment to supporting affected customers. All customers, regardless of the status of the support contract, receive free incident response assistance, as well as assistance offered to contract customers for any incident involving known or reasonably suspicious security vulnerabilities in a Cisco product. If you encounter a Cisco product incident, contact the Cisco Technical Assistance Center (TAC):
For more information, see the Cisco Vulnerability Security Policy .
To ensure perimeter security and control, network administrators need to be especially vigilant. It is easy to “install and forget” network devices, as they are usually very stable and rarely change. Suffice it to recall the results of our annual cybersecurity annual report, in which we demonstrated the results of our study proving that the average non-elimination time for clients of vulnerabilities in network and server hardware and software is on average about five years. Combine this with the advantages that an attacker has when gaining access and intercepting control of a network device and you will realize that routers and switches become very attractive targets for intruders. Especially if we are talking about devices standing on the perimeter of the organization or carrier.
Watching attackers actively using this vector, Cisco strongly recommends that all customers review their architecture, use the Talos tools to scan their network, and remove the Cisco Smart Install Client from all devices where it is not used.
On February 14, 2017 (yes, there is no error, this is about 2017), the Cisco Product Security Incident Response Team (PSIRT) published a bulletin describing the results of active scans associated with Cisco Smart Install Clients. The Cisco Smart Install Client software is an outdated utility designed for remote configuration of new Cisco equipment, in particular Cisco switches. In continuation, Cisco Talos posted a blog post and released an open source tool that scans devices using the Cisco Smart Install protocol. In addition to the above, a signature was issued for the Snort attack detection system (SID: 41722-41725), which allows to detect any attempts to use this technology.
The Cisco Smart Install protocol can be abused to change the TFTP server setting, export configuration files via TFTP, change the configuration files, replace the image of the network IOS operating system, and set up accounts that allow you to run IOS commands. Although this is not a vulnerability in the classical sense, the misuse of this protocol can serve as an attack vector that should be immediately neutralized. During late 2017 and early 2018, Talos watched as attackers attempted to scan clients using this vulnerability. Recent information has increased the relevance of this problem and we decided to return to it again.
')
Although we only observed attacks related to the problem of misusing the Cisco Smart Install protocol, another vulnerability was recently discovered and fixed in the Cisco Smart Install Client. This vulnerability has been discussed publicly, and a code has been released showing evidence of the possibility of exploiting the vulnerability (PoC). To fix the problem of misuse of the protocol, clients should also eliminate this vulnerability by installing the appropriate update.
Scope
As part of the Cisco Talos study, we began to explore how many devices are potentially vulnerable to this attack. The results were extremely disturbing. Using Shodan, Talos was able to determine that more than 168,000 systems could potentially be detected via the Cisco Smart Install Client “open to the Internet”. This is better than the results of 2016, when a Tenable employee reported 251,000 vulnerable Cisco Smart Install Clients “visible” from the Internet. There may be differences in the Cisco Talos and Tenable scanning methodology, but we assume a significant reduction in the number of devices available to attack. In addition, despite the fact that since our initial bulletin, there has been a drop in scan volumes, Talos observed a sharp increase in scanning attempts for the Cisco Smart Install Client around November 9, 2017.

Neutralization
You can determine if you have a device “raised” on the Cisco Smart Install Client software switch. Running the show vstack config command will allow you to determine if the Smart Install Client is active. Below is an example of such a command with a response to it:
switch # show vstack config | inc Role Role: Client (SmartInstall enabled) Additional features of the active Cisco Smart Install Client may be present if level 6 (informational) or higher registration is enabled. These event logs may include, but are not limited to, TFTP write operations, command execution, and device reloads.
The easiest way to counteract this problem is to run the no vstack command on a vulnerable device. If for any reason this option is not available to the client, the best option would be to restrict access via an access control list (ACL) for the interface, an example of which is shown below:
ip access-list extended SMI_HARDENING_LIST permit tcp host 10.10.10.1 host 10.10.10.200 eq 4786 deny tcp any any eq 4786 permit ip any any This type of ACL only allows the nodes shown above to access the Smart Install Client, which significantly limits the ability to launch an attack. In addition, there are signatures in our Intrusion Prevention Systems (IPS) to determine if Smart Install Client is affected or not.
Support
For this and other issues, it is important to remember Cisco’s commitment to supporting affected customers. All customers, regardless of the status of the support contract, receive free incident response assistance, as well as assistance offered to contract customers for any incident involving known or reasonably suspicious security vulnerabilities in a Cisco product. If you encounter a Cisco product incident, contact the Cisco Technical Assistance Center (TAC):
- In Moscow: +7 495 961 13 82
- In St. Petersburg: +7 812 363-3328
- Free call within Russia: 8 800 700 05 22
- In Armenia: 800-721-7549
- In Belarus: 8 800 101, then 800 721 7549
- In Ukraine (main): 0800 301 2090 (toll free number)
- In Ukraine (alternative): +380 44 390 2400
- In Azerbaijan: 088 9999999
- In Kazakhstan: 8 ^ 800-121-4321 (dial 8, wait for the 2nd signal and then dial the remaining numbers). Then dial the PIN, 800-721-7549
- In Tajikistan: + 992 44 600 60 40
- In Uzbekistan: 800-721-7549
For more information, see the Cisco Vulnerability Security Policy .
findings
To ensure perimeter security and control, network administrators need to be especially vigilant. It is easy to “install and forget” network devices, as they are usually very stable and rarely change. Suffice it to recall the results of our annual cybersecurity annual report, in which we demonstrated the results of our study proving that the average non-elimination time for clients of vulnerabilities in network and server hardware and software is on average about five years. Combine this with the advantages that an attacker has when gaining access and intercepting control of a network device and you will realize that routers and switches become very attractive targets for intruders. Especially if we are talking about devices standing on the perimeter of the organization or carrier.
Watching attackers actively using this vector, Cisco strongly recommends that all customers review their architecture, use the Talos tools to scan their network, and remove the Cisco Smart Install Client from all devices where it is not used.
Additional Information
- Cisco bulletin about incorrect use of Cisco Smart Install protocol
- Cisco Newsletter on Smart Install RCE Vulnerability
- Cisco bulletin about DDoS vulnerabilities in the implementation of the Smart Install feature
- A note on the Cisco Talos blog about incorrectly using the Smart Install protocol
- Cisco Talos Smart Install Client Scanner
- This is the original Talos blog post.
- Cisco Cisco IOS and IOS XE Security Enhancement Guide
Source: https://habr.com/ru/post/352996/
All Articles