Manipulating Google search results

Researcher Tom Anthony discovered a supercritical vulnerability in the Google search engine that could affect search results. The company “fixed” the vulnerability for half a year and paid only $ 1,337 for it.
A brief summary of the vulnerability is as follows: as part of ongoing research, the author recently discovered a problem with Google, which allows an attacker to send an XML sitemap to Google for a site for which he had not been authenticated. Since these files may contain indexing directives, such as hreflang , this allows an attacker to use these directives to help their own websites rank in Google search results.
Google allows you to submit an XML sitemap to help you find the URL to be crawled, but it can also be used for the hreflang directive to identify other international versions of the same page (for example, “hey, google, this American page, but I have a page in German, this URL ... "). It’s not known exactly how Google uses these directives (like everything related to Google’s search algorithms), but hreflang seems to allow a URL to“ borrow ”ranking and trust links of one url and use it to rank another URL (i.e. most people link to the US version of .com, and so the German version can “borrow” a trust for ranking in Google.de).
')
According to the documentation, the presentation of the XML file for Google can be performed via the Google Search Console, robots.txt, or a specialized “ping” URL.
You can add new XML Sitemaps through the ping mechanism, while Googlebot usually retrieves the file within 10-15 seconds after ping. It is important to note that Google also mentions a couple of times on the page that if you send a Sitemap through the ping mechanism, it will not appear inside your Search Console .
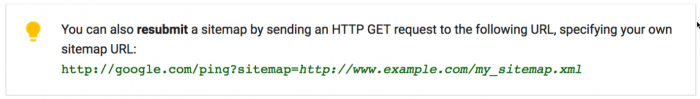
The practical application of the vulnerability is associated with the use of the redirection mechanism, which is quite common in modern web applications. An attacker can use direct forwarding in the context of different domains (if allowed):
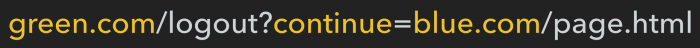
or mechanisms to bypass validation, for example, using a subdomain structure that repeats the URL of the site being attacked (for example, Tesco.com retailer, which earns more than 50 billion pounds sterling, more than 1 billion pounds sterling through its website):
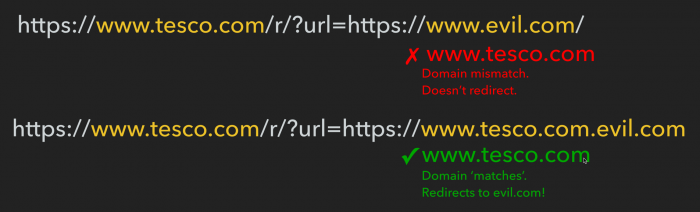
The ping service followed the full redirect path and validated the xml file for the first URL (but actually located on a different domain):
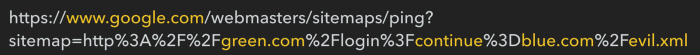
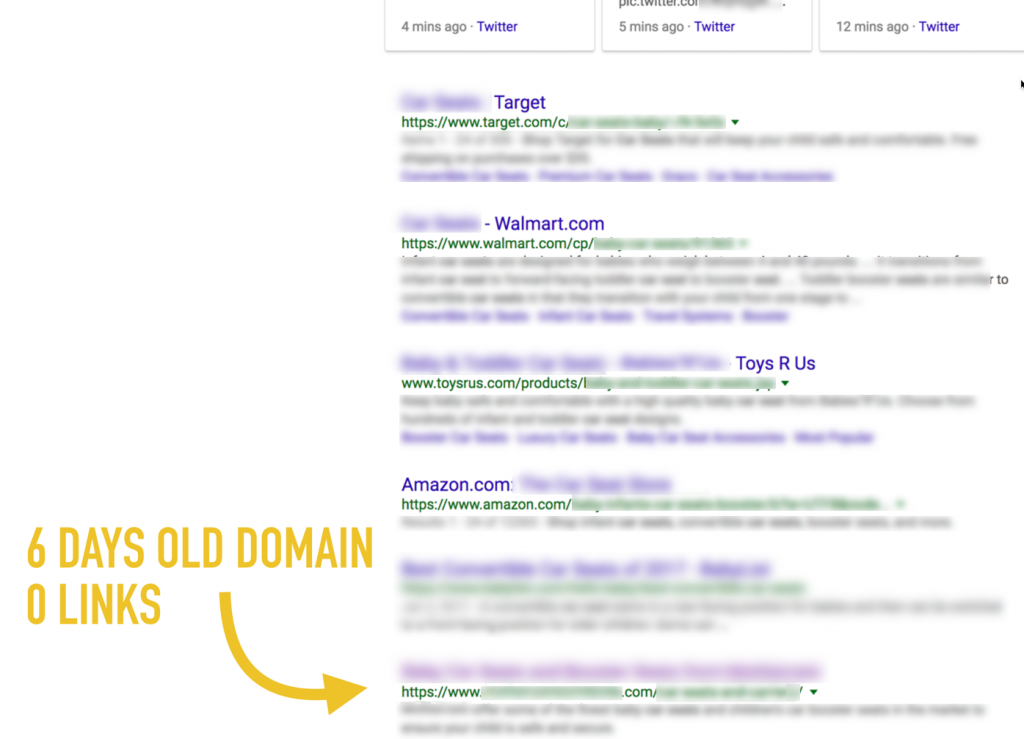
As a result of the experiment, the researcher received traffic to the “fake” domain, without a single backlink within 48 hours:

In addition, the new site began to appear on the first page of the issue of Google on highly competitive queries (again, without a single backlink to the new site):
Moreover, after these manipulations, the linking of websites began to be traced in the Google Search Console:

Timeline:
- September 23, 2017 - Initial Error Report.
- September 25, 2017 - Google answer - learning about the error.
- October 2, 2017 - sending details.
- October 9 - November 6 - some status updates.
- November 6, 2017 - Google continues to explore the issue of security.
- November 6, 2017 - the author's correction is related to following the redirects for pinged sitemaps.
- January 3, 2018 - status update.
- January 15, 2018 - Google’s response from that until all factors have been identified, given the legitimate use - they are asked to wait for an answer.
- February 15, 2018 - Google is vulnerable.
- March 6, 2018 - Google reports on the payment of remuneration in the amount of 1337 dollars.
- March 6, 2018, the author asks to publish the details of the vulnerability in the public domain.
- March 12, 2018 - Google asks to wait, because The fix has not yet been completed.
- March 25, 2018 - Google confirmed the publication of details of the vulnerability in the public domain.
Source: https://habr.com/ru/post/352976/
All Articles