Simple, affordable and useful Wi-Fi lab. Do it yourself
If you are seriously involved in Wi-Fi, then you definitely have your laboratory equipment. Without him, in my opinion, can not do. If you are going to seriously engage in Wi-Fi, then sooner or later, you will need to get a laboratory. In this article I will tell you how to do this with minimal cost and for what tasks the laboratory may be necessary, using real examples.

More than 40% (according to statista.com) of corporate Wi-Fi is Cisco. You will probably need this particular iron. First you need to buy 2-3 access points of the second freshness. For example, AIR-CAP1702I-R-K9. These points support 802.11ac, but not so expensive as fresh. For some tasks even AIR-CAP1602I-R-K9 will do. Older do not recommend taking. Often, it requires the support of points with fresh software that needs to be tested, and the fresh software does not support old points. For example, at 8.6 already even 1602 will not start. If you have enough money, you can get fresh points with Mobility Express, such as 1852 or 2802. Then the controller may not need you the first time, but the functionality of the real controller will still be richer, and later it will come in handy. You can understand the difference by reading the config guide for both.
You can buy from a familiar distributor with a maximum discount, or at the NFR price, if you work at a partner integrator. Although the management of the integrator does not always like to approve the purchase of something “for himself”, even at the NFR price. If you need to find iron at the lowest price and for cash, then your choice is Avito or ebay. There are very interesting offers. The regulatory domain of the access point does not matter, since on the controller you will set the desired RU. When buying from us, in Russia, I advise you to record all the contacts of the seller, to make a screen of the announcement, as there is a small probability that the points were stolen by some evil installers, it is there. When we launched one large object, 10 out of 200 access points were stolen and found at a nearby pawnshop through Avito.
')
So, you have purchased access points. If you bought autonomous points, then transfer them to the controller ( CAPWAP ) mode (and vice versa) for ten minutes, skillfully. Googles by request type: Cisco 1702 lightweight to autonomous. If you already have free points, for example, from the ZIP kit, you are lucky. You can immediately go to the next stage - the controller.

Cisco has 2 main types of controllers, iron and virtual. Virtual works only in FlexConnect mode and this imposes a number of limitations, but in many cases it is sufficient. He has one indisputable advantage, it is shareware. More precisely, a full-featured demo license for almost 3 months is activated immediately after installation. 3 months is a sufficient period for testing. If you need to extend it, simply reinstall the controller (saving the config) or even easier, roll back to the previously created snapshot of the virtual machine;) again, not forgetting to save the config. The iron controller type 2504 can be bought cheaply in the same places as points. Now there are many of them on the market.
1. Server where the virtual machine will spin. For the tasks of a laboratory controller, any laptop with a 64-bit processor supporting VT-x will do. For example, I have this experienced Thinkpad X220 on i5. If you have access to a mighty blade with ESXi at work, of course it is appropriate to use its power. In general, choose from the available.
2. Virtualization software such as VMware Workstation (a bit paid) or VirtualBox (given for free). Which one to choose is up to you. In my experience, the OVA template with a virtual controller turned around and did not work on all versions of VirtualBox. Earned only on older, 5.0.16, and then not immediately. On 5.1.8 did not work. On 5.2.6, the specific OVA with the 8.5 version of the controller does not start. On VMware Workstation it started right away and worked like a clock, so I can recommend it.
3. OVA package with the archive of all necessary, including the image of the controller. Officially swings to cisco.com with access. For example, stable 8.0.152.0, is available for download just like that (if you are registered on cisco.com). If there is no access to the software of interest, but there is a partnership, then you can request it by friendship. If neither one nor the other, be smart.
I will not tell you in detail with pictures how to deploy OVA, this is done as usual. Open .ova, specify where to store the car and go ...
Then everything will go automatically and soon you will see that the controller is loading.
After the download, you will see the familiar dialog of the first controller setup, for which you of course prepared in advance. Just in case in the spoiler I will remind you the parameters that will be required. Values, of course, put their own, and the service port is important to put in another subnet.
After that, the controller will reboot and work.
In the VMware console there will be access to the console, through the browser at the specified Management Interface IP Address there will be https access to the WEB, which is more convenient. You can also ssh.

If there is no web access, you are likely to have attached a virtual one to the wrong network adapter.
Edit - Virtual Network Editor will resolve this issue.
Further, everything is as usual with the controller, except that the access points must be put into FlexConnect mode in order to make money. And do not forget to activate the license, otherwise you will wonder for a long time why the DTLS tunnel is not established!
Check custom solutions
For example, at one factory it was necessary to connect a number of network devices on a mobile crane, via Wi-Fi. The client used a Cisco 1532E access point in WGB offline mode. This mode is good because it allows you to flexibly configure roaming parameters, and devices connected via WGB are visible by their MAC in the network. The customer wanted to make sure that the roaming time was short in this mode.
I transferred one point to an autonomous WGB mode and, on a long cord, wore it in the office, moving between two controller points hanging on the ceiling. The laptop was connected to the point with the same cord, so in the logs, as the point moved, similar records appeared that clearly allowed to judge the roaming time.
In this example, 353-265 = 88ms was spent on scanning, selecting, and switching.
Different versions of the experiment showed the time to 200ms, which suited everyone.
Maybe for the analysis of roaming time it would be more correct to use packet sniffing, listen to the air from two adapters and analyze later, but at that time it seemed sufficient.
Checking fresh software for stability
There is a useful rule: the best is the enemy of the good. If your software is up-to-date, recommended as stable and you only need its capabilities, there is no need to change it. If you need new features, such as AVC on FlexConnect, you will probably have to update the software. If you are servicing a large network, with hundreds or thousands of TDs, then the risk that something will go wrong on a fresh software is there. For this it is useful to have a laboratory where you can run the necessary software for a week and try it out. How much is 1 hour of network downtime at your facility? How much is a set for labs? Compare these prices and decide for yourself.
Check idle time when using some commands
If you are setting up a live network, it is much more interesting, just need to be more careful and know in advance the result of your actions. If a simple live network creates problems, it is better to try commands that require reloading points in advance.
For example, there is such a handy thing as RF Profile, in which the data rate, the working MCS, the parameters of the automatic radio control, as well as some other useful parameters like RxSOP change. This profile is hung on a group of points, adjusting them at once. At the same time, it is necessary to remember that if you change an existing profile that is already in work, then no result will follow. No changes will be made. It is necessary to fasten another profile to the point group, the points will be overloaded, with its settings, then the original one that you changed to be screwed, and then, having reloaded, the points will work on the new settings. How long it will take you can find out by conducting an experiment in the office, then to coordinate with the customer a short break in communication.
Reason out intractable Wi-Fi neighbors
Suppose your office network is built on UniFi. The next room is leased by another company, and its administrator, not knowing that in the 2.4 GHz band, only three non-intersecting channels tuned the neighboring point to your 3rd channel, and even occupied 40 MHz! Or even this is not the admin did, and the firmware curve itself chose the 3rd channel. At the same time, people download torrents constantly through this third channel. Your colleagues began to complain that Wi-Fi works worse. What to do? Ideally, transfer all (equipment) and all (clients) to 5 GHz and forget about this terrible time when your spectrum analyzer showed these pictures
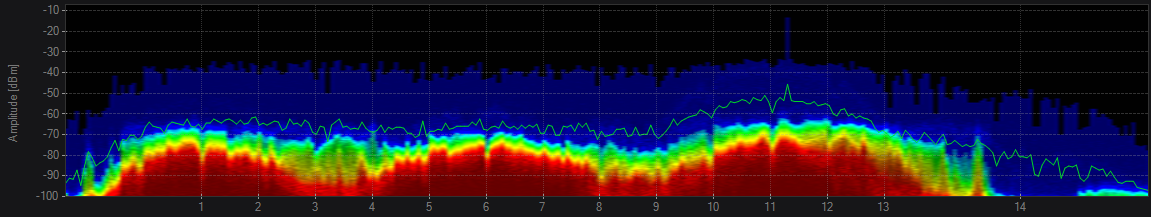
In real life, this is not yet possible. 2.4 GHz in the Russian Federation is still popular, thanks to manufacturers of low-end Chinese smartphones.
So, the transfer will not work, you need to communicate with the next office. Most likely, if you clearly explain why they need to change the settings, the question will be resolved quickly. If there is no help, or there are a lot of and neighboring offices that do not understand who is the source of your concern (although it can be detected by some free Wi-Fi Analyzer on your smartphone), then you can use heavy artillery. In the Monitor - Rogues section, find the point of interest to you and in the Update Status select the Contain.
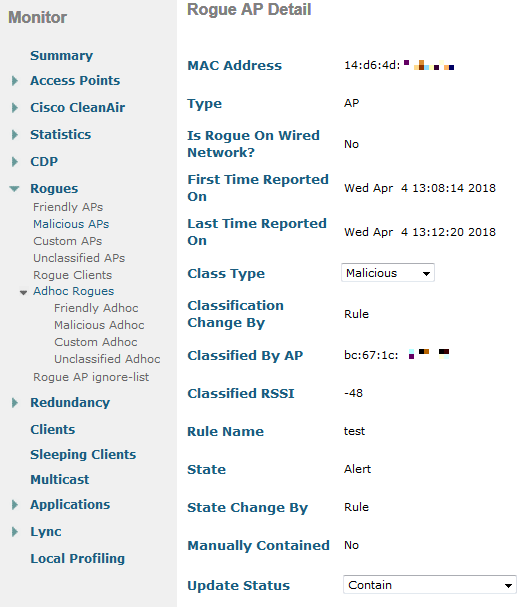
In this case, the controller will carefully warn you that this may be illegal. In fact, you initiate a DoS attack on your neighbor's network by sending de-authentication frames from your 802.11 points on behalf of the neighbor point to its clients. And that's all, if you hear this point at least at the level of -70dBm and press the Apply button, while selecting the maximum number of APs to contain the rogue, then all of its clients simply stop working.

People do not understand what is happening, because they physically chop off and it is impossible to connect. They are trying to change the settings, it does not help. If you also (after a couple of days) notice that the channel has been changed, and successfully, then the Contain status is removed and everyone is happy. If not, decide for yourself. In my experience, once a couple of weeks, it was discovered that people had set up a new access point, the SSID remained the same, but the channel was set up crooked again.
If anyone knows what legally it can threaten in the Russian Federation, I will be glad to your comments. It is also curious what evidence could be taken. To discover that you can be reached, but you need to have a serious infrastructure that will see that this happens and will say about it in a similar way: Warning: Our AP with Base Radio MAC f4: ea: 67: 00: 01: 08 is under attack (contained ) by another AP on radio type 802.11b / g.
If someone has such an infrastructure, it is extremely unlikely that he will make such gross mistakes in the configuration. If you have a software like Omnipeek for intercepting 802.11 frames and an adapter that can work in promiscuous mode, then it will help to detect such a problem. On your favorite Kali Linux, you already know how to catch frames and what to do. Thus, if suddenly people in your network stopped connecting to Wi-Fi, completely, look for software to intercept, and before that check whether you are interfering with your neighbors.
If you’re not sure whether to ask your bosses (or yourself) to allocate funds to buy three access points in order to build a very useful Wi-Fi lab, I hope your doubts are dispelled.

More than 40% (according to statista.com) of corporate Wi-Fi is Cisco. You will probably need this particular iron. First you need to buy 2-3 access points of the second freshness. For example, AIR-CAP1702I-R-K9. These points support 802.11ac, but not so expensive as fresh. For some tasks even AIR-CAP1602I-R-K9 will do. Older do not recommend taking. Often, it requires the support of points with fresh software that needs to be tested, and the fresh software does not support old points. For example, at 8.6 already even 1602 will not start. If you have enough money, you can get fresh points with Mobility Express, such as 1852 or 2802. Then the controller may not need you the first time, but the functionality of the real controller will still be richer, and later it will come in handy. You can understand the difference by reading the config guide for both.
Where can one buy?
You can buy from a familiar distributor with a maximum discount, or at the NFR price, if you work at a partner integrator. Although the management of the integrator does not always like to approve the purchase of something “for himself”, even at the NFR price. If you need to find iron at the lowest price and for cash, then your choice is Avito or ebay. There are very interesting offers. The regulatory domain of the access point does not matter, since on the controller you will set the desired RU. When buying from us, in Russia, I advise you to record all the contacts of the seller, to make a screen of the announcement, as there is a small probability that the points were stolen by some evil installers, it is there. When we launched one large object, 10 out of 200 access points were stolen and found at a nearby pawnshop through Avito.
')
So, you have purchased access points. If you bought autonomous points, then transfer them to the controller ( CAPWAP ) mode (and vice versa) for ten minutes, skillfully. Googles by request type: Cisco 1702 lightweight to autonomous. If you already have free points, for example, from the ZIP kit, you are lucky. You can immediately go to the next stage - the controller.

Cisco has 2 main types of controllers, iron and virtual. Virtual works only in FlexConnect mode and this imposes a number of limitations, but in many cases it is sufficient. He has one indisputable advantage, it is shareware. More precisely, a full-featured demo license for almost 3 months is activated immediately after installation. 3 months is a sufficient period for testing. If you need to extend it, simply reinstall the controller (saving the config) or even easier, roll back to the previously created snapshot of the virtual machine;) again, not forgetting to save the config. The iron controller type 2504 can be bought cheaply in the same places as points. Now there are many of them on the market.
To install a virtual controller, you will need:
1. Server where the virtual machine will spin. For the tasks of a laboratory controller, any laptop with a 64-bit processor supporting VT-x will do. For example, I have this experienced Thinkpad X220 on i5. If you have access to a mighty blade with ESXi at work, of course it is appropriate to use its power. In general, choose from the available.
2. Virtualization software such as VMware Workstation (a bit paid) or VirtualBox (given for free). Which one to choose is up to you. In my experience, the OVA template with a virtual controller turned around and did not work on all versions of VirtualBox. Earned only on older, 5.0.16, and then not immediately. On 5.1.8 did not work. On 5.2.6, the specific OVA with the 8.5 version of the controller does not start. On VMware Workstation it started right away and worked like a clock, so I can recommend it.
3. OVA package with the archive of all necessary, including the image of the controller. Officially swings to cisco.com with access. For example, stable 8.0.152.0, is available for download just like that (if you are registered on cisco.com). If there is no access to the software of interest, but there is a partnership, then you can request it by friendship. If neither one nor the other, be smart.

I will not tell you in detail with pictures how to deploy OVA, this is done as usual. Open .ova, specify where to store the car and go ...

Then everything will go automatically and soon you will see that the controller is loading.

After the download, you will see the familiar dialog of the first controller setup, for which you of course prepared in advance. Just in case in the spoiler I will remind you the parameters that will be required. Values, of course, put their own, and the service port is important to put in another subnet.
Options
System Name [Cisco_2c:4d:2f] (31 characters max): vWLC Enter Administrative User Name (24 characters max): wlcadmin Enter Administrative Password (3 to 24 characters): ******** Re-enter Administrative Password : ******** Service Interface IP Address Configuration [static][DHCP]: static 172.16.0.8 Management Interface IP Address: 10.8.8.2 Management Interface Netmask: 255.255.255.0 Management Interface Default Router: 10.8.8.1 Management Interface VLAN Identifier (0 = untagged): 0 Management Interface DHCP Server IP Address: 10.8.8.1 Enable HA [yes][NO]: NO Virtual Gateway IP Address: 198.51.100.108 Mobility/RF Group Name: LAB Network Name (SSID): TEST Configure DHCP Bridging Mode [yes][NO]: no Allow Static IP Addresses [YES][no]: no Configure a RADIUS Server now? [YES][no]: no Warning! The default WLAN security policy requires a RADIUS server. Please see documentation for more details. Enter Country Code list (enter 'help' for a list of countries) [RU]: RU Enable 802.11b Network [YES][no]: Enable 802.11a Network [YES][no]: Enable Auto-RF [YES][no]: yes Configure a NTP server now? [YES][no]: 10.8.8.1 Configure the system time now? [YES][no]: no Warning! No AP will come up unless the time is set. Please see documentation for more details. Configuration correct? If yes, system will save it and reset. [yes][NO]: yes Configuration saved! Resetting system with new configuration... After that, the controller will reboot and work.
In the VMware console there will be access to the console, through the browser at the specified Management Interface IP Address there will be https access to the WEB, which is more convenient. You can also ssh.

If there is no web access, you are likely to have attached a virtual one to the wrong network adapter.
Edit - Virtual Network Editor will resolve this issue.
Further, everything is as usual with the controller, except that the access points must be put into FlexConnect mode in order to make money. And do not forget to activate the license, otherwise you will wonder for a long time why the DTLS tunnel is not established!
A few examples of what the laboratory is useful for.
Check custom solutions
For example, at one factory it was necessary to connect a number of network devices on a mobile crane, via Wi-Fi. The client used a Cisco 1532E access point in WGB offline mode. This mode is good because it allows you to flexibly configure roaming parameters, and devices connected via WGB are visible by their MAC in the network. The customer wanted to make sure that the roaming time was short in this mode.
I transferred one point to an autonomous WGB mode and, on a long cord, wore it in the office, moving between two controller points hanging on the ceiling. The laptop was connected to the point with the same cord, so in the logs, as the point moved, similar records appeared that clearly allowed to judge the roaming time.
log
*Mar 1 01:39:34.265: %DOT11-4-UPLINK_DOWN: Interface Dot11Radio1, parent lost: Too many retries
*Mar 1 01:39:34.265: E76D58EB-1 Uplink: Lost AP, Too many retries
*Mar 1 01:39:34.265: E76D597D-1 Uplink: Setting No. of retries in channel scan to 2
*Mar 1 01:39:34.265: E76D5985-1 Uplink: Wait for driver to stop
*Mar 1 01:39:34.265: E76D5FBB-1 Uplink: Enabling active scan
*Mar 1 01:39:34.265: E76D5FCA-1 Uplink: Not busy, scan all channels
*Mar 1 01:39:34.265: E76D5FD2-1 Uplink: Scanning
*Mar 1 01:39:34.313: E76E2161-1 Uplink: Rcvd response from 003a.7db3.c54f channel 161 538
*Mar 1 01:39:34.325: E76E231F-1 Uplink: An AP responded, try to assoc to the best one
*Mar 1 01:39:34.341: E76E82D7-1 Uplink: dot11_uplink_scan_done: rsnie_accept returns 0x0 key_mgmt 0xFAC02 encrypt_type 0x200
*Mar 1 01:39:34.341: E76E82ED-1 Uplink: ssid GMXM-C auth open
*Mar 1 01:39:34.341: E76E82F4-1 Uplink: try 003a.7db3.c54f, enc 200 key 4, priv 1, eap 0
*Mar 1 01:39:34.341: E76E82FE-1 Uplink: Authenticating
*Mar 1 01:39:34.341: E76E855C-1 Uplink: Associating
*Mar 1 01:39:34.341: E76E8DEB-1 Uplink: EAP authenticating
*Mar 1 01:39:34.353: %DOT11-4-UPLINK_ESTABLISHED: Interface Dot11Radio1, Associated To AP GMXM-1702i-1 003a.7db3.c54f [None WPAv2 PSK]
*Mar 1 01:39:34.353: E76EB2C7-1 Uplink: DoneIn this example, 353-265 = 88ms was spent on scanning, selecting, and switching.
Different versions of the experiment showed the time to 200ms, which suited everyone.
Maybe for the analysis of roaming time it would be more correct to use packet sniffing, listen to the air from two adapters and analyze later, but at that time it seemed sufficient.
Checking fresh software for stability
There is a useful rule: the best is the enemy of the good. If your software is up-to-date, recommended as stable and you only need its capabilities, there is no need to change it. If you need new features, such as AVC on FlexConnect, you will probably have to update the software. If you are servicing a large network, with hundreds or thousands of TDs, then the risk that something will go wrong on a fresh software is there. For this it is useful to have a laboratory where you can run the necessary software for a week and try it out. How much is 1 hour of network downtime at your facility? How much is a set for labs? Compare these prices and decide for yourself.
Check idle time when using some commands
If you are setting up a live network, it is much more interesting, just need to be more careful and know in advance the result of your actions. If a simple live network creates problems, it is better to try commands that require reloading points in advance.
For example, there is such a handy thing as RF Profile, in which the data rate, the working MCS, the parameters of the automatic radio control, as well as some other useful parameters like RxSOP change. This profile is hung on a group of points, adjusting them at once. At the same time, it is necessary to remember that if you change an existing profile that is already in work, then no result will follow. No changes will be made. It is necessary to fasten another profile to the point group, the points will be overloaded, with its settings, then the original one that you changed to be screwed, and then, having reloaded, the points will work on the new settings. How long it will take you can find out by conducting an experiment in the office, then to coordinate with the customer a short break in communication.
Reason out intractable Wi-Fi neighbors
Suppose your office network is built on UniFi. The next room is leased by another company, and its administrator, not knowing that in the 2.4 GHz band, only three non-intersecting channels tuned the neighboring point to your 3rd channel, and even occupied 40 MHz! Or even this is not the admin did, and the firmware curve itself chose the 3rd channel. At the same time, people download torrents constantly through this third channel. Your colleagues began to complain that Wi-Fi works worse. What to do? Ideally, transfer all (equipment) and all (clients) to 5 GHz and forget about this terrible time when your spectrum analyzer showed these pictures

In real life, this is not yet possible. 2.4 GHz in the Russian Federation is still popular, thanks to manufacturers of low-end Chinese smartphones.
So, the transfer will not work, you need to communicate with the next office. Most likely, if you clearly explain why they need to change the settings, the question will be resolved quickly. If there is no help, or there are a lot of and neighboring offices that do not understand who is the source of your concern (although it can be detected by some free Wi-Fi Analyzer on your smartphone), then you can use heavy artillery. In the Monitor - Rogues section, find the point of interest to you and in the Update Status select the Contain.

In this case, the controller will carefully warn you that this may be illegal. In fact, you initiate a DoS attack on your neighbor's network by sending de-authentication frames from your 802.11 points on behalf of the neighbor point to its clients. And that's all, if you hear this point at least at the level of -70dBm and press the Apply button, while selecting the maximum number of APs to contain the rogue, then all of its clients simply stop working.

People do not understand what is happening, because they physically chop off and it is impossible to connect. They are trying to change the settings, it does not help. If you also (after a couple of days) notice that the channel has been changed, and successfully, then the Contain status is removed and everyone is happy. If not, decide for yourself. In my experience, once a couple of weeks, it was discovered that people had set up a new access point, the SSID remained the same, but the channel was set up crooked again.
If anyone knows what legally it can threaten in the Russian Federation, I will be glad to your comments. It is also curious what evidence could be taken. To discover that you can be reached, but you need to have a serious infrastructure that will see that this happens and will say about it in a similar way: Warning: Our AP with Base Radio MAC f4: ea: 67: 00: 01: 08 is under attack (contained ) by another AP on radio type 802.11b / g.
If someone has such an infrastructure, it is extremely unlikely that he will make such gross mistakes in the configuration. If you have a software like Omnipeek for intercepting 802.11 frames and an adapter that can work in promiscuous mode, then it will help to detect such a problem. On your favorite Kali Linux, you already know how to catch frames and what to do. Thus, if suddenly people in your network stopped connecting to Wi-Fi, completely, look for software to intercept, and before that check whether you are interfering with your neighbors.
If you’re not sure whether to ask your bosses (or yourself) to allocate funds to buy three access points in order to build a very useful Wi-Fi lab, I hope your doubts are dispelled.
Source: https://habr.com/ru/post/352864/
All Articles